This post is also available in: 日本語 (Japanese)
Threat Assessment: DoppelPaymer Ransomware
Executive Summary
DoppelPaymer is a ransomware family and threat actor group that first debuted publicly in June 2019. While attacks definitively tied to both the group and the fully mature version of the malware began in June 2019, earlier, less mature versions of the malware were obtained by security researchers several months prior, though without any definitive group affiliation. This may indicate that the actors were either testing functionality prior to employing the malware in an actual attack, or that they adjusted their approach over time in dealing with their victims.
DoppelPaymer Malware Overview

DoppelPaymer is considered part of a family of ransomware called BitPaymer. The actors behind DoppelPaymer share some overlap with an actor group known as Indrik Spider. The DoppelPaymer actors, like many other ransomware threat actor groups, maintain a public site and social media presence typically including lists of victims and their leaked data.
Since DoppelPaymer’s inception, the malware family has typically utilized two file extensions on victim endpoints – .locked and .doppeled. Outside of the two file extensions employed by DoppelPaymer, this ransomware employs an interesting technique to terminate processes and services: It leverages ProcessHacker. ProcessHacker is a legitimate open-source administration application that is bundled with many DoppelPaymer samples and is used to terminate processes and services on the infected endpoint.
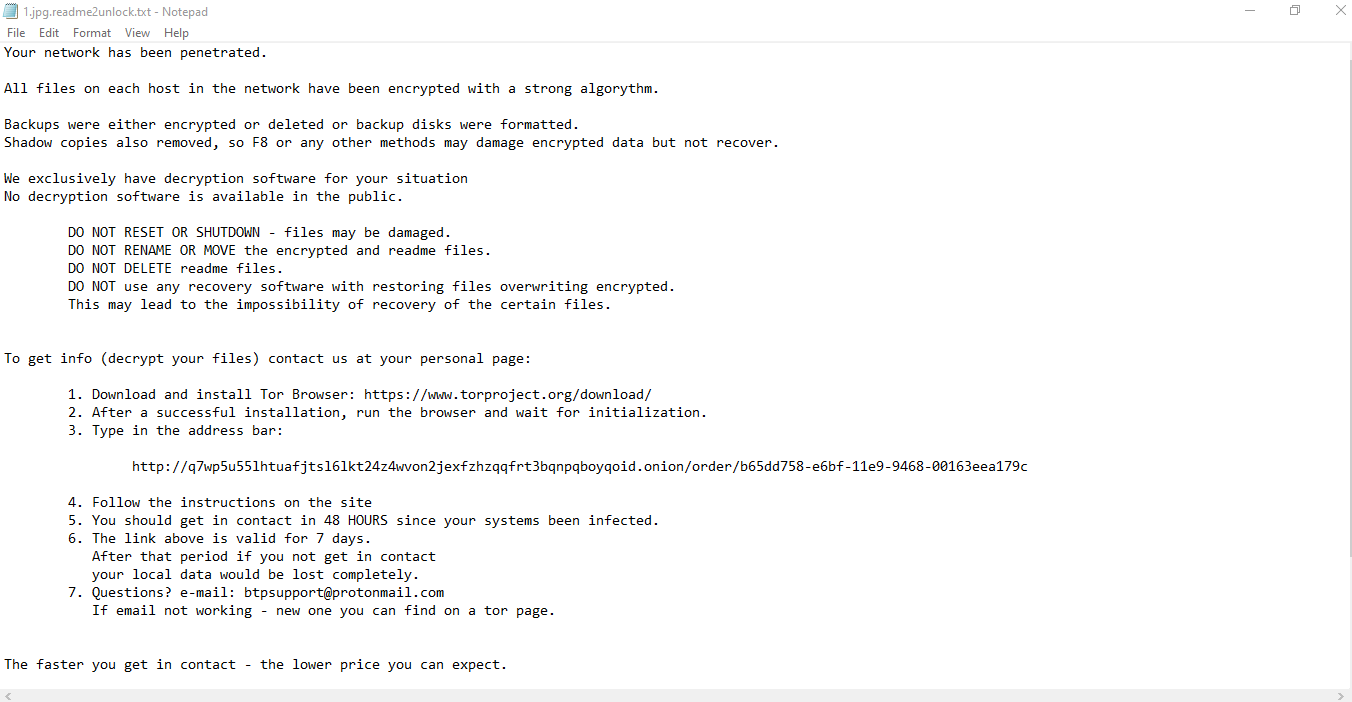
The ransomware note displayed by DoppelPaymer closely resembles the ransomware note dropped by BitPaymer in 2018. The ransom note doesn’t include the ransom amount, but it does include a .onion domain that’s a portal for payment and contacting the actors behind the attack. Like the ransom note, DoppelPaymer’s payment portal is nearly a clone of the original BitPaymer payment portal.
Unit 42 has observed Doppelpaymer being used against firms in the wholesale and retail, manufacturing, finance, insurance, transportation and logistics, high tech, hospitality, and real estate industries. From a regional perspective, the threat actors behind DoppelPaymer have targeted victims in the U.S., Canada, Mexico, South Africa, Belgium, Italy, Norway, and Germany.
DoppelPaymer propagates via remote human operators using compromised Domain Admin credentials to spread across an organization’s network. The ransom amount the operators behind DoppelPaymer have typically demanded is between $25,000 and $17 million. The average ransom paid in 2020, typically in Bitcoin, reached $276,587.41.
More information on DoppelPaymer victimology can be found in the 2021 Unit 42 Ransomware Threat Report.
Courses of Action
This section documents relevant tactics, techniques and procedures (TTPs) used with DoppelPaymer and maps them directly to Palo Alto Networks product(s) and service(s). It also further instructs customers on how to ensure their devices are configured correctly.
| Product / Service | Course of Action |
| Initial Access, Defense Evasion, Persistence, Privilege Escalation | |
| Domain Accounts [T1078.002] | |
| NGFW | Ensure that User-ID is only enabled for internal trusted interfaces |
| Ensure that 'Include/Exclude Networks' is used if User-ID is enabled | |
| Ensure that the User-ID Agent has minimal permissions if User-ID is enabled | |
| Ensure that the User-ID service account does not have interactive logon rights | |
| Ensure remote access capabilities for the User-ID service account are forbidden. | |
| Threat Prevention† | Ensure that antivirus profiles are set to block on all decoders except 'imap' and 'pop3' |
| Ensure a secure antivirus profile is applied to all relevant security policies | |
| Ensure that all zones have Zone Protection Profiles with all Reconnaissance Protection settings enabled, tuned and set to appropriate actions | |
| Cortex XSOAR | Deploy XSOAR Playbook - Access Investigation Playbook |
| Deploy XSOAR Playbook - Impossible Traveler | |
| Exfiltration, Collection, Discovery, Impact | |
| Automated Exfiltration [T1020], Data from Local System [T1059.003], System Network Configuration Discovery [T1016], Inhibit System Recovery [T1490], Data Encrypted for Impact [T1486] | |
| Cortex XDR | Enable Anti-Exploit Protection |
| Enable Anti-Malware Protection | |
| Cortex XSOAR | Deploy XSOAR Playbook - Block IP |
| Deploy XSOAR Playbook - Block URL | |
| Deploy XSOAR Playbook - Hunting and Threat Detection Playbook | |
| Deploy XSOAR Playbook - PAN-OS Query Logs for Indicators | |
| Deploy XSOAR Playbook - Palo Alto Networks Endpoint Malware Investigation | |
| Deploy XSOAR Playbook - Ransomware Manual for incident response. | |
Table 1. Courses of Action for DoppelPaymer ransomware.
†These capabilities are part of the NGFW security subscriptions service.
Conclusion
Unfortunately, the similarities between BitPaymer, DoppelPaymer and other ransomware families suggests ransomware actors are borrowing from each other’s playbooks on a regular basis. Like other ransomware actors, the actors behind DoppelPaymer maintain an active social media presence and leak site, while also seeking increasing ransom amounts from victims, much the same way ransomware threat actor groups in the past have done.
Palo Alto Networks detects and prevents DoppelPaymer in the following ways:
- WildFire: All known samples are identified as malware.
- Cortex XDR with:
- Indicators for DoppelPaymer.
- Anti-Ransomware Module to detect DoppelPaymer encryption behaviors.
- Local Analysis detection to detect DoppelPaymer binaries.
- Next-Generation Firewalls: DNS Signatures detect the known command and control (C2) domains, which are also categorized as malware in URL Filtering.
- AutoFocus: Tracking related activity using the BitPaymerFamily tag.
Additionally, Indicators of Compromise (IoCs) associated with DoppelPaymer are available on GitHub, and have been published to the Unit 42 TAXII feed.
Additional Resources
- BitPaymer Source Code Fork: Meet DoppelPaymer Ransomware and Dridex 2.0
- BitPaymer Malware Information
Continue Reading: Phobos











 Get updates from Unit 42
Get updates from Unit 42