Introduction
Our latest Unit 42 Attack Surface Threat Report explores the attack surface landscape of 265 global organizations worldwide. The report is based on our observable data on exposures and vulnerabilities that are publicly accessible over the internet, collected over a one-year period. It also offers recommendations on how organizations should approach active attack surface management (ASM). Here we summarize key findings from the report and recommendations from the report, providing a high-level overview of today’s attack surface landscape.
Key Findings on the Attack Surface Landscape
Change in attack surfaces inevitably leads to exposure. We observed that attack surfaces across industries are always in a state of flux. Our research indicates that, on average, an organization’s attack surface has over 300 new services every month. These additions alone account for nearly 32% of new high or critical exposures for organizations.
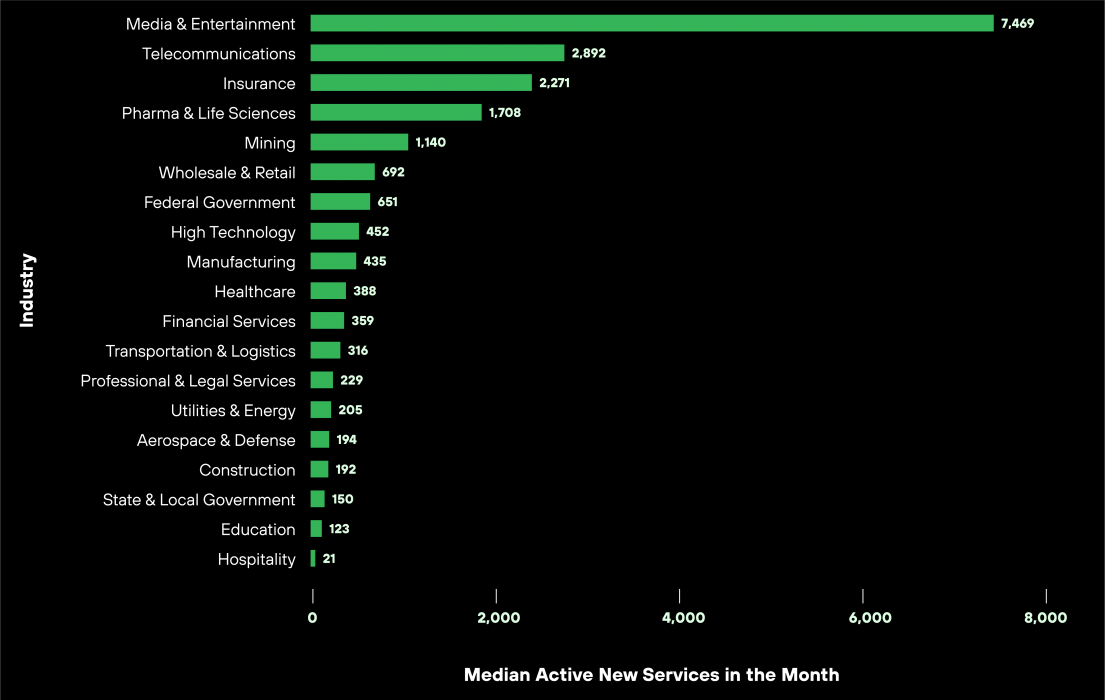
The media and entertainment industry experienced the highest rate of new services added, exceeding 7,000 per month.
Figure 1 shows that all industries consistently add new services to their growing attack surface. Sectors like telecommunications, insurance, pharma and life sciences add over 1,000 new services every month. Critical industries like financial services, healthcare and manufacturing add over 200 new services monthly.
For the past three years, the Unit 42 Incident Response Report has identified the most commonly targeted industries, which are also the top industries Unit 42 has provided incident response services to. In 2024, the top six industries identified were professional and legal services, high technology, manufacturing, healthcare, finance and wholesale and retail. Together, these industries accounted for 63% of cases.
While these statistics show which industries ask us for expert incident response help, other industries are at risk too.
Critical IT and security services are dangerously exposed to the internet.
Figure 2 shows that over 23% of exposures among the organizations we studied involve critical IT and security infrastructure, which opens the door to opportunistic attacks.
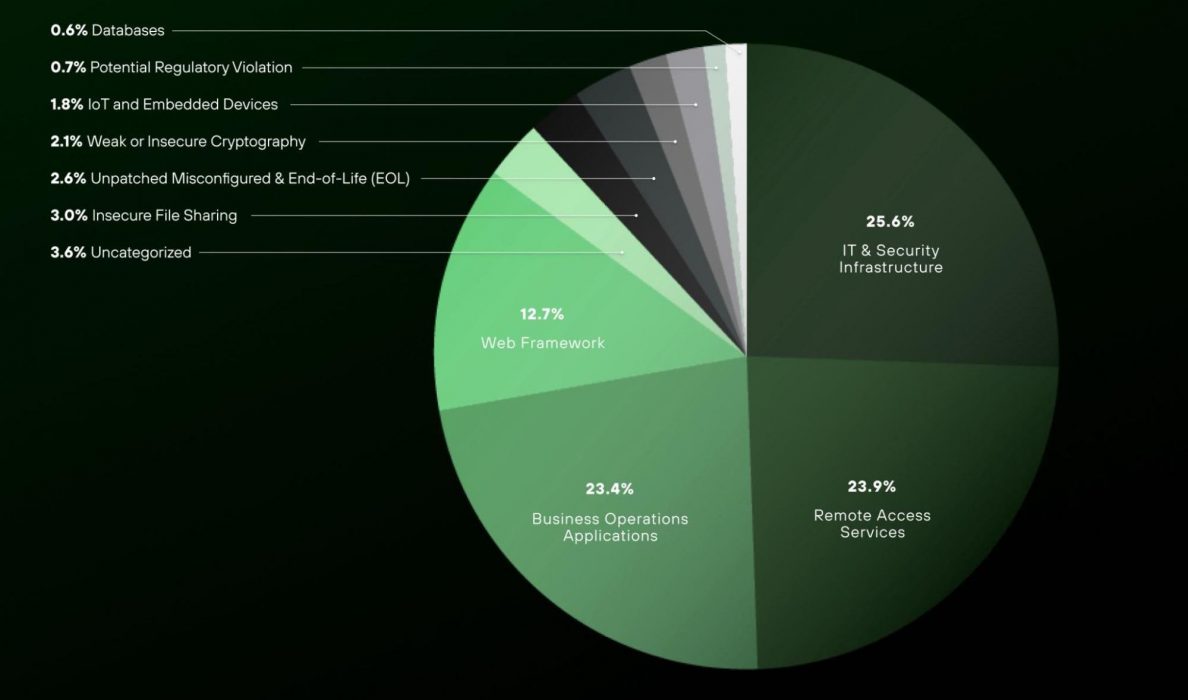
These exposures include vulnerabilities in the following application-layer protocols:
- SNMP
- NetBIOS
- PPTP
It also includes vulnerabilities in internet-accessible administrative login pages of the following products:
- Routers
- Firewalls
- VPNs
- Other core networking and security appliances
Recommendations For Actively Managing Your Attack Surface
A critical challenge for most organizations is tracking and protecting all assets. The 2024 Unit 42 Incident Response report reveals that in the past year, attackers most often gained initial access through software vulnerabilities, with the largest attack campaigns exploiting internet-facing systems.
To protect against these attack surface vulnerabilities, organizations should:
- Maintain persistent, comprehensive visibility
Identifying and responding to attack surface risks starts with continuous, comprehensive scans of your organization's ports, services and devices. - Monitor for unsanctioned services or shadow IT
Regularly check perimeter resources to distinguish between expected assets and unknown or out-of-scope ones, ensuring adherence to security baselines. Deviations from these baselines are often the most vulnerable to compromise, making them prime targets for attackers. - Remediate critical exposure risks in real time
Detection is only half of the battle. It is crucial to have processes and technology to assist security teams in identifying, communicating, tracking and automating remediation where possible.
How Palo Alto Networks Can Help
Get the full 2024 Unit 42 Attack Surface Threat Report for more global attack surface insights, trends and recommendations for best practices.
If ASM is new to your organization, or you’d like help with improving your program, Cortex Xpanse and Unit 42 Attack Surface Assessment can jump-start your journey. This assessment service gives you better visibility into your on-premises and cloud-based internet-connected assets and recommendations on prioritized actions to help you defend your organization.
Additionally, adding the ASM Module to your XSIAM deployment provides context on internet-exposed assets to enhance threat prevention, detection and response with AI and machine intelligence.
Additional Resources
- CISO’s Guide to Attack Surface Management — Palo Alto Networks
- Video: Top Attack Surface Use Cases — Palo Alto Networks
- Unit 42 Attack Surface Assessment- Palo Alto Networks










 Get updates from Unit 42
Get updates from Unit 42