Executive Summary
We have uncovered three vulnerabilities in the firmware of the TOTOLINK X6000R router, version V9.4.0cu.1360_B20241207, released on March 28, 2025:
| CVE | Rating | Score | Description |
| CVE-2025-52905 | High | CVSS-B 7.0 | An argument injection flaw that attackers can use to trigger a denial of service (DoS), crashing the router or overwhelming remote servers. |
| CVE-2025-52906 | Critical | CVSS-B 9.3 | An unauthenticated command injection vulnerability that allows attackers to remotely execute arbitrary commands on the device. |
| CVE-2025-52907 | High | CVSS-B 7.3 | A security bypass that attackers can exploit to corrupt system files, cause a persistent denial-of-service, or achieve arbitrary file writes. Chaining attacks could lead to remote code execution (RCE). |
TOTOLINK is a manufacturer of networking products, including routers and other Internet of Things (IoT) devices used by consumers worldwide. The widespread adoption of these products makes their security a critical area of focus.
We worked with TOTOLINK to address this issue, and they have released an updated firmware version to resolve it. Users are advised to install the latest firmware to secure their devices.
This article provides a detailed technical analysis of these vulnerabilities. We will analyze the root cause and demonstrate the impacts.
Palo Alto Networks customers are better protected from the threats described through the following products and services:
- The Next-Generation Firewall with a Threat Prevention or Advanced Threat Prevention security subscription can help block attacks.
- Palo Alto Networks Device Security solution provides immediate visibility, risk assessment, and risk mitigation across the entire device landscape.
- Cortex Xpanse and the ASM add-on for XSIAM allow for detection of internet exposed TOTOLINK router devices which may be inadvertently accessible.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | IoT Vulnerability |
Vulnerability Analysis
The TOTOLINK X6000R router's web interface relies heavily on the /cgi-bin/cstecgi.cgi endpoint for its core functionality. This endpoint acts as a central processing hub, receiving user requests and determining the appropriate action to take. When the web interface sends a request to cstecgi.cgi, it includes a topicurl parameter. The HTTP server within the router uses the value of topicurl to determine which internal function to call, effectively making it a routing mechanism for controlling the router's configuration and operations.
We discovered multiple vulnerabilities within the functions handled by this /cgi-bin/cstecgi.cgi endpoint, potentially allowing unauthenticated attackers to exploit the router's web interface. We will now proceed with a technical deep-dive into each vulnerability, starting with an argument injection vulnerability.
CVE-2025-52905: Argument Injection
Firmware version V9.4.0cu.1360_B20241207 includes an input sanitization function designed to prevent command injection, shown in Figure 1.
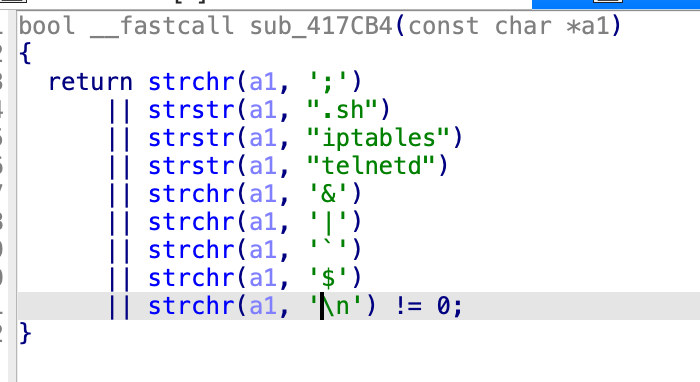
This function's blocklist fails to filter the hyphen character (-), creating a High argument injection vulnerability across multiple components.
CVE-2025-52906: Unauthenticated Command Injection
The setEasyMeshAgentCfg function, responsible for configuring EasyMesh agent settings, is vulnerable to unauthenticated command injection. This vulnerability arises because the function fails to properly validate and sanitize the user-supplied input for the agentName parameter. As a result, an attacker can inject arbitrary commands that the router will execute with the privileges of the web server process.
This vulnerability does not require authentication, meaning any attacker who can reach the router's web interface can exploit it.
This type of vulnerability represents a failure of input validation. Gaining root access allows an attacker to:
- Intercept traffic
- Pivot to other devices on the network
- Install persistent malware
CVE-2025-52907: Security Bypass
As established in the previous section, the firmware's sanitization function is implemented across multiple components but relies on an incomplete character blocklist. This allows an unauthenticated attacker to bypass the check and achieve arbitrary file manipulation.
This same vulnerability extends to other components, including the setWizardCfg function (Figure 2).
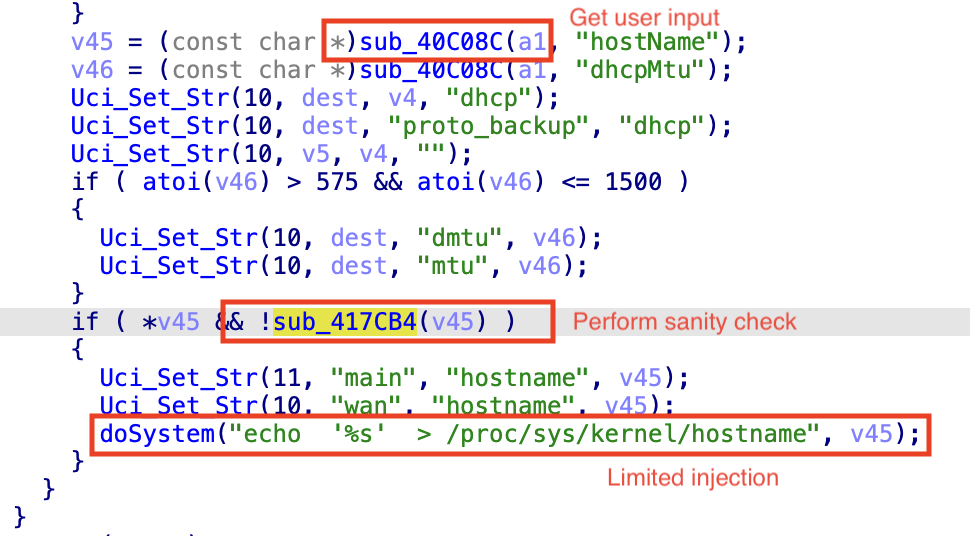
This vulnerability allows for an arbitrary file write by bypassing the same user-input confidence check, enabling an unauthenticated attacker to escalate their attack. This includes creating or modifying critical system files such as /etc/passwd to add new users, or altering boot scripts to achieve persistent RCE.
Conclusion and Recommendations
Home routers are the digital front door to the internet for millions of users. They serve as a key defense for personal data, smart home devices and corporate assets accessed via remote work.
Unauthenticated attackers could exploit these vulnerabilities to disrupt network services, gain unauthorized access to devices and potentially execute arbitrary code. Timely firmware updates are crucial for mitigating these risks. These vulnerabilities underscore the importance of robust security practices in IoT devices and the shared responsibility of vendors, security researchers and users in maintaining a secure digital ecosystem.
To protect against these threats, users should immediately upgrade their TOTOLINK X6000R router to the latest available firmware (V9.4.0cu.1498_B20250826).
For customers of Palo Alto Networks, our products deliver proactive protection against these vulnerabilities through the following services:
- Next-Generation Firewall with a Threat Prevention or Advanced Threat Prevention security subscription can help block attacks with best practices via Threat Prevention signature 95097 and 96495.
- The Palo Alto Networks Device Security security platform can leverage network traffic information to identify the vendor, model and firmware version of a device and identify specific devices that are affected by known vulnerabilities, and enforce risk-adaptive policies on these devices.
- Cortex Xpanse and the ASM add-on for XSIAM allow for detection of internet exposed TOTOLINK router devices which may be inadvertently accessible.
Disclosure Timeline
- June 13, 2025: The vulnerabilities were reported to TOTOLINK by Palo Alto Networks.
- June 19, 2025: TOTOLINK provided a fixed firmware build (V9.4.0cu.1454_B20250619) for Palo Alto Networks to verify.
- June 20, 2025: Palo Alto Networks initiated the process to assign CVEs to the vulnerabilities.
- June 25, 2025: TOTOLINK made the updated firmware publicly available.
- Sept. 23, 2025: The CVEs are published on the Palo Alto Networks GitHub.
Additional Resources
- X6000R Latest Firmware – TOTOLINK
- New Vulnerability in QNAP QTS Firmware: CVE-2023-50358 – Unit 42, Palo Alto Networks
- PANW-2025-0001 – Palo Alto Networks Vulnerability Disclosures GitHub
- PANW-2025-0002 – Palo Alto Networks Vulnerability Disclosures GitHub
- PANW-2025-0003 – Palo Alto Networks Vulnerability Disclosures GitHub











 Get updates from Unit 42
Get updates from Unit 42