This post is also available in: 日本語 (Japanese)
Executive Summary
Unit 42 researchers have observed a surge of malware written for the Android platform that is attempting to impersonate the popular ChatGPT application. These malware variants emerged along with the release by OpenAI of GPT-3.5, followed by GPT-4, infecting victims interested in using the ChatGPT tool.
Here, we provide an in-depth analysis of two types of currently active malware clusters. The first cluster is a Meterpreter Trojan disguised as a "SuperGPT" app. The second is a "ChatGPT" app that sends short-text messages to premium-rate numbers in Thailand, resulting in charges for the victim that are pocketed by the threat actor.
Android users can download applications written for the Android platform from a variety of places. The Google Play store is the official source, but users are also free to obtain applications from other sources such as websites or links in emails. This means there is potential for users to obtain applications that have not been vetted by Google.
The files described here have been sent to Google and will be blocked from the Google Play store. Google Play Protect also protects users from apps known to contain this malware on Android devices with Google Play Services, even when those apps come from other sources. This underscores the need for users to be aware of the risks when obtaining applications for mobile devices outside of official channels. It is still possible that users could encounter malicious applications for download elsewhere on the internet.
Palo Alto Networks customers with Cortex XDR, the Next-Generation Firewall and Advanced URL Filtering benefit from protections against the ChatGPT-themed attacks discussed in this article. Additionally, the malicious indicators (domains, URLs and hashes) can be prevented with our DNS Security and WildFire services.
| Related Unit 42 Topics | ChatGPT, Meterpreter, Scams |
Introduction
OpenAI created a tool known as Chat "Generative Pre-trained Transformer," or ChatGPT for short. This tool is powered by a large language model (LLM) and is currently in its fourth version.
ChatGPT first became publicly available on Nov. 30, 2022. It quickly went viral, since it demonstrated remarkable question-answering ability, though not necessarily in an accurate manner.
Threat actors are always seeking to distribute their wares via effective attack vectors, and impersonating prevalent applications according to the current global trend is among the most effective means to accomplish this objective. For instance, attackers commonly leveraged the COVID-19 pandemic to spread their own malicious versions of “Health and Wellness” category applications written for the Android platform.
Past reports on malware masquerading as a ChatGPT-related tool, as well as our earlier publication "ChatGPT-Themed Scam Attacks on the Rise," found that scammers were taking advantage of ChatGPT's popularity to launch attacks. Threat actors are using similarly worded domain names to trick victims into giving away personal information or downloading malware.
Here, we continue to report on this trend, sharing our findings on some malicious Android applications we've recently discovered in our telemetry. Specifically, we found two types of active malware. One is a Meterpreter Trojan disguised as a "SuperGPT" app, and the other is a "ChatGPT" app that sends messages to premium-rate numbers in Thailand.
Meterpreter Trojan
Our team uncovered a malicious Android Package Kit (APK) sample, which turned out to be a Trojanized version of a legitimate application. The legitimate application is an AI assistant based on the latest version of ChatGPT. The malicious version of this application enables the actor to establish remote access to an Android device if exploitation is successful.
Table 1 describes the legitimate application and Table 2 shows the malicious application.
| Application name | SuperGPT - AI with GPT-4 |
| Description (summarized from the official listing) | A GPT-4 powered AI assistant, able to perform tasks such as:
Also comes equipped with the following capabilities:
|
| Package name | com.dominapp.supergpt |
| Version name (code) | 1.2 (8) |
| SHA-256 hash | d7ef8929b236a43917f351c39963916c1dd3a9c0580499443322750435245f9f |
| File size | 10.85 MB (11,378,336 bytes) |
Table 1. Metadata of the legitimate application.
The MainActivity class of the malware sample contains a String variable reference to the official ChatGPT URL https://chat.openai.com/chat. Package-Class named v3.v is a custom WebViewClient class implementation (WebView is Android's built-in implementation to embed web browser functionality in apps made for its operating system). As such, this Java class is able to extend or override the default functionality. It does so by adding the following redirect rules:
- Redirect to https://chat.openai.com/chat, if URL contains https://openai.com/blog/chatgpt/
- Redirect to https://chat.openai.com/chat after a 1,000 millisecond delay, if URL contains beta.openai.com/
| Application icon | Screenshot | |
|
|
|
|
| Application name | SuperGPT | |
| SHA-256 hash | af19ca9213a20263c30584a2bf260dcdb3b4eafa4f43af10824af781573a2314 | |
| File size | 12.39 MB (12,994,395 bytes) | |
| Programming language | Kotlin | |
| Version name (code) | 1.2 (8) | |
| Package name | com.dominapp.supergpt | |
| Main activity | com.dominapp.supergpt.activities.MainActivity | |
| Android version | Minimum: | API level 23 (Android 6) |
| Target: | API level 32 (Android 12L) | |
Table 2. Metadata of the malicious APK sample.
According to VirusTotal (VT), this sample was first submitted through VT's web interface from Nicaragua (NI), on 2023-03-16 02:06:04 UTC, as filename 2021id.apk.
Payload Implantation
Comparing the differences between the legitimate and malicious APK samples, it is clear that the critical Trojanizing addition to the file is the following line of Smali language code (shown in Figure 1).
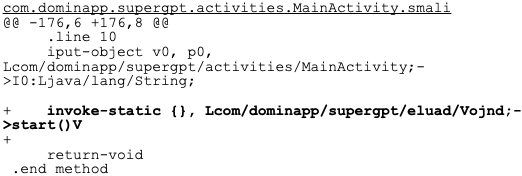
The core threat in this malware sample is known as "Meterpreter." It is created using the Metasploit framework.
The source code of the initial Java-based Android Meterpreter stager can be found on Rapid7's GitHub repository. The main functionality is implemented within the Payload class. The Payload class' start method is invoked by the MainService class. The MainService class, in turn, can be either:
- Started by the MainActivity class
- Started by the MainBroadcastReceiver class automatically upon completion of the device boot sequence
The Payload class' main method is responsible for performing the following sequence of actions:
- Parse the hard-coded exploit configuration stored in the configBytes byte array (shown in Figure 2).
- Note: This is not obfuscated in any way (e.g., the TCP or HTTP remote host address and port are clearly visible)
- Ensure the Android device's central processing unit (CPU) remains on via the Power Manager system service's partial wake lock functionality.
- Hide the icon’s application if requested.
- Establish a socket connection to the author-managed remote host.
- Download a secondary payload upon successful connection, implementing the full range of capabilities (e.g., the dump_sms command).
In the case of the APK malware sample in question, the following sequence of operations triggers this Meterpreter payload:
- The service named com.dominapp.supergpt.eluad.Vojnd starts upon the BOOT_COMPLETED action, as declared in the AndroidManifest.xml file.
- The thread named com.dominapp.supergpt.eluad.C2094e spawns and runs.
- The main method of the package class named com.dominapp.supergpt.eluad.Dapjs is invoked.

The Meterpreter payload is configured to connect to the remote endpoint tcp[://]Gwdidkfkf-47070[.]portmap[.]io:47070. Portmap.io is a service that performs port forwarding free of charge.
Certificate Attribution
The digital code-signing certificate used to sign this sample belongs to the attacker with the following characteristics:
- Email address – lkpandey950@gmail[.]com
- Organization Common Name (CN) – Hax4Us
- Located in Shahdara, Delhi, India
- The certificate is valid from 2020-07-17 11:08:41 UTC to 2047-12-02 11:08:41 UTC
- Serial number – 1a505d53b1c75046a81acb021fdb5f99936b75db
- SHA-1 thumbprint – 65094A64233F818AEF5A4EDE90AC1D0C5A569A8B
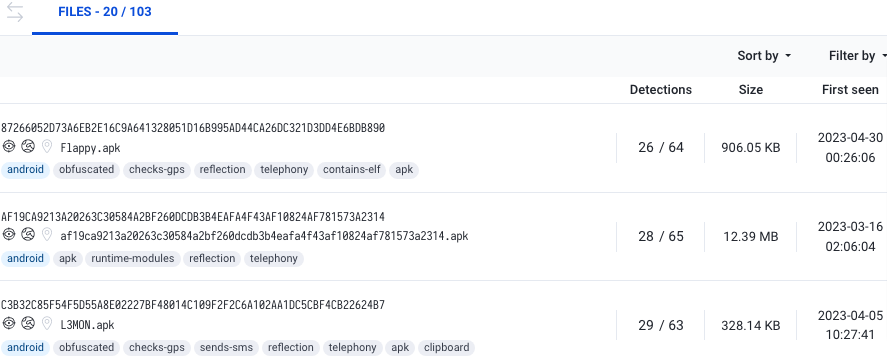
This certificate is attached to over a hundred other publicly shared malware samples on VT (as shown in Figure 3).
SMS to Premium-Rate Numbers
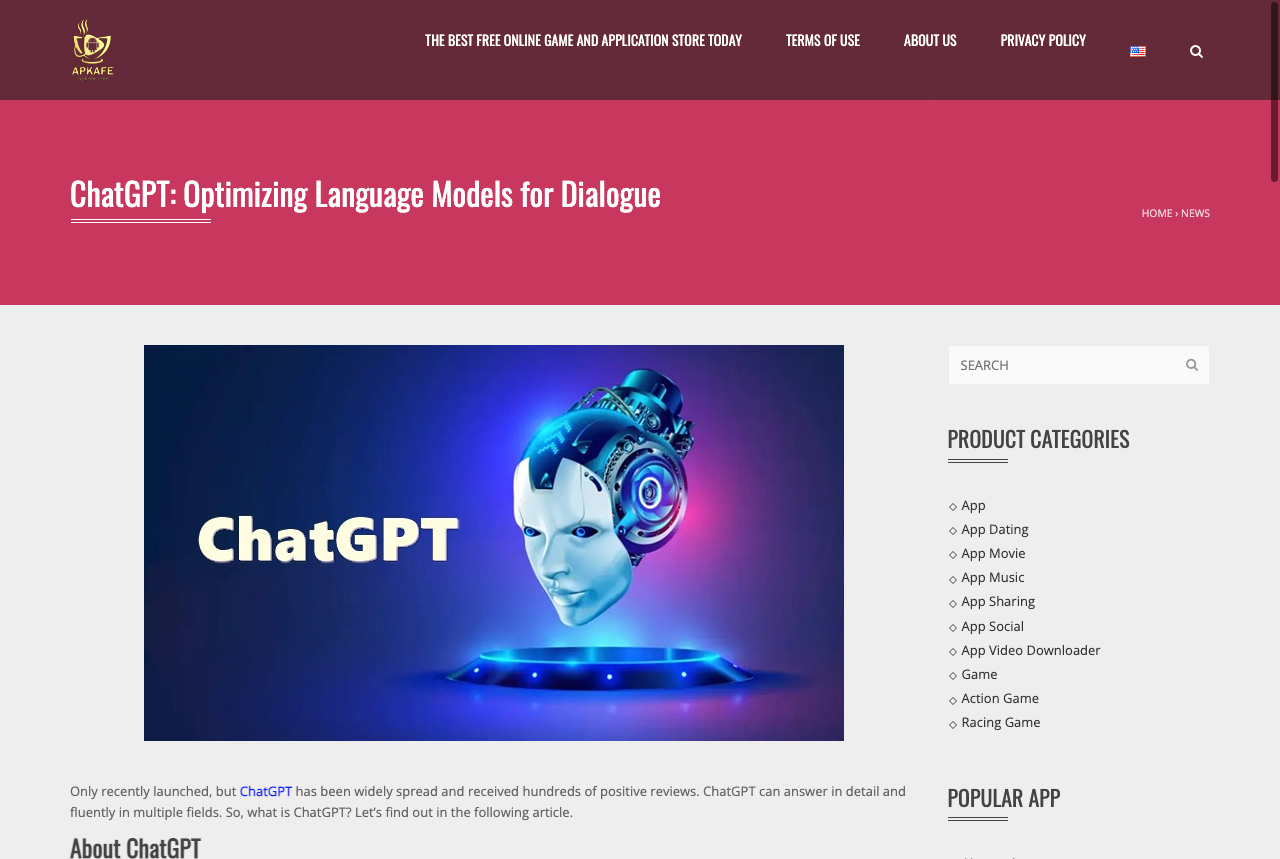
We've also uncovered another cluster of APK malware samples. On the surface, the malware seems to be presenting the following webpage (shown in Figure 4) containing a description of ChatGPT. But in fact, this threat conceals a sinister intent underneath.

Moreover, all these APK samples share the OpenAI logo often associated with ChatGPT (shown in Figure 5) as their application icon, adding to the deceptive narrative that this application is related to the ChatGPT AI tool.
These APK malware samples are capable of sending SMS messages to premium-rate numbers in Thailand (TH). Premium-rate numbers cost more than calls to normal phone numbers, in exchange for rendering some sort of service (e.g., users providing information). The business behind it collects the earnings, but this can also be abused to conduct scams and fraudulent activity. For reference, the official Android Open Source Project (AOSP) codebase contains a list of premium-rate numbers by country.
The Android permission to send SMS text messages, android.permission.SEND_SMS, is requested by the application, and a reference to the "country":"thailand" is passed as a ContentValue. The samples also make use of OneSignal, a service that enables apps to send messages via push notifications, including by email, SMS and within the app itself.
For instance, the configuration obtained from the URL hxxps[://]api[.]onesignal[.]com/apps/af63b434-ec50-46a0-9374-d57a383f2e03/android_params[.]js is reproduced below:
(The OneSignal app ID is af63b434-ec50-46a0-9374-d57a383f2e03)
{
"awl_list": {},
"android_sender_id": "660194064544",
"chnl_lst": [],
"outcomes": {
"direct": {
"enabled": false
},
"indirect": {
"notification_attribution": {
"minutes_since_displayed": 60,
"limit": 10
},
"enabled": false
},
"unattributed": {
"enabled": false
}
},
"receive_receipts_enable": false
}
The formatted phone number in the android_sender_id field value is +661-9406-4544.
These APK samples are digitally signed with a generic certificate. As for other key attributes, their values are depicted in Table 3 below.
| Validity | From 2008-02-29 01:33:46 UTC
To 2035-07-17 01:33:46 UTC |
| Serial number | 936eacbe07f201df |
| Thumbprint (SHA-1) | 61ED377E85D386A8DFEE6B864BD85B0BFAA5AF81 |
Table 3. Code-signing certificate attributes for Type II APK samples.
This cluster of samples can be subdivided into two smaller batches, each sharing some common characteristics. APK samples in the first batch send an SMS text message to one hard-coded, premium-rate Thai number and make use of the OneSignal service. APK samples in the second batch send different SMS text messages to two other hard-coded, premium-rate Thai numbers, and they do not obtain configuration from an external OneSignal endpoint.
The APK samples belonging to the first batch have a lower version compared to those from the second. This suggests that the first batch could be an earlier iteration of malware development than the second. This theory is supported by the earlier "first submission" timestamp of these APK samples on VT: batch one (February 2023), followed by batch two (March 2023).
Batch One
These are the SHA-256 hashes of samples in this batch:
- 2980329fa5eaed0f5625e961572f7ae8136ca7df30cca9e9c8783c827627b692
- 391e8f394af425f1e7edff6aea1605aa89f2fb0233c44e70cff265fc60ec3b1b
- d1844bf3865c7d2e4745baa2496297937821171d7a3ad4412b0a4e767bc32b5e
- d1b1813f7975b7117931477571a2476decff41f124b84cc7a2074dd00b5eba7c
Table 4 below summarizes the static attributes of samples in this batch.
| Package names |
|
|
| Main activities |
|
|
| Version name (code) | chatgpt (183) | |
| Android version | Minimum: API level 18 (Android 4.3) | |
| Target: API level 30 (Android 11) | ||
| Tags |
|
|
| First submission timestamps on VT (UTC) | Between 2023-02-02 08:37:23 and 2023-02-07 03:08:33 | |
|
OneSignal configuration |
||
| App ID | af63b434-ec50-46a0-9374-d57a383f2e03 | |
| Android sender ID | +661-9406-4544 | |
Table 4. Static attributes of batch one APK samples.
Batch Two
These are the SHA-256 hashes of samples in this batch:
- b787d5ef4a0c350a9f62f55907c8ef6d92bf7699b8544fabff5a263e52a2d0d1
- be757541584cc2dc2e7adacf7a5186be07d474f06c8698a938589f86ce56ea34
- e9bb6d04d796eb147b9d73a7df91fb9e6a99e0be8a41a61329d600a9dfe8b1ae
Table 5 below summarizes the static attributes of samples in this batch.
| File size | 1.249 MB (1,309,619 bytes) | |
| Package name | com.chatgpt.ggmmtlan | |
| Main activity | ggtlan.sub.MainActivity | |
| Version name (code) | chatgpt (200) | |
| Android version | Minimum: API level 22 (Android 5.1) | |
| Target: API level 30 (Android 11) | ||
| First submission timestamp on VT (UTC) | SHA-256 hash | |
| 2023-03-08 22:16:21 | be757541584cc2dc2e7adacf7a5186be07d474f06c8698a938589f86ce56ea34 | |
| 2023-03-10 12:00:23 | e9bb6d04d796eb147b9d73a7df91fb9e6a99e0be8a41a61329d600a9dfe8b1ae | |
| 2023-03-17 10:19:14 | b787d5ef4a0c350a9f62f55907c8ef6d92bf7699b8544fabff5a263e52a2d0d1 | |
Table 5. Static attributes of Batch 2 APK samples.
Conclusion
The emergence of ChatGPT-themed APK malware poses a severe threat to the security and privacy of mobile devices. These types of malware can potentially steal sensitive information, spy on user activities and cause significant financial losses for unsuspecting victims.
To protect themselves against this type of malware, mobile users should take proactive measures, such as installing reputable antivirus software, being cautious when downloading apps from third-party sources and keeping their devices up to date with the latest security patches.
Overall, the threat of mobile malware highlights the critical importance of mobile device security. By remaining vigilant and taking proactive steps to safeguard our devices, we can help prevent the spread of this dangerous malware and protect ourselves from potential harm.
Palo Alto Networks customers with Cortex XDR, the Next-Generation Firewall and WildFire benefit from protections against the attacks discussed in this article. Additionally, the malicious indicators (domains, URLs and hashes) can be prevented with our DNS Security and Advanced URL Filtering services.
If you think you might have been impacted or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: +1.866.486.4842 (+1.866.4.UNIT42)
- UK: +44.20.3743.3660
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Indicators of Compromise
| Category | SHA-256 hashes |
| APK malware samples Type I |
|
| APK malware samples Type II |
Batch One
|
|
Batch Two
|
|
| URL |
|
| Certificate Thumbprint (SHA-1) |
|
MITRE ATT&CK TTPs
| ID | Technique | Description |
| T1582 | SMS Control | APK malware samples are capable of sending SMS to Premium-rate Numbers in Thailand. |
| T1623 | Command and Scripting Interpreter | APK malware samples are capable of providing Meterpreter shell access. |
Additional Resources
- ChatGPT Malware: A New Threat in Cybersecurity, Sangfor Technologies
- Into Android Meterpreter and how the malware launches it — part 2, Medium
- ChatGPT-Themed Scam Attacks Are on the Rise, Unit 42, Palo Alto Networks












 Get updates from Unit 42
Get updates from Unit 42