This post is also available in: 日本語 (Japanese)
Executive Summary
Discovered in 2014, Emotet is one of the most prolific malware families, infecting computer systems globally through its mass campaigns of spam email that delivers malware (AKA malspam). These campaigns have been widely documented by many organizations, including how Emotet evolved from being a banking Trojan, to a malware loader with modular functionalities. The modular functionality of the malware allows the Emotet operators to install additional malware onto machines that are part of the Emotet botnet. The Emotet operators also provide their botnet as “Malware-as-a-Service” to other cyber-criminal gangs, who install their own malware of choice to the infected systems. For example, Emotet was recently used to deliver the Trickbot Trojan, which was then used to deliver the Ryuk ransomware.
Given Emotet’s destructive capability, incidents within enterprises have cost hundreds and thousands of dollars in recovery costs. The threat of an Emotet infection is significant and it is imperative to understand the Emotet operators’ modus operandi to better defend against it.
Our new research below reveals that despite the Emotet malspam campaigns going dark towards the end of May, a large number of vulnerable servers of small and mid-size enterprises (SMEs) across APAC (primarily Vietnam, India, Indonesia, Australia, China and Japan) are now being exploited by Emotet actors to distribute Emotet variants, primarily due to lack of updating and patching their web servers. Additionally, we found that the majority of these compromised domains are running the WordPress blogging software.
As we continue to notice SME’s websites being exploited at a high rate across APAC (also observed in other campaigns), and being leveraged as malware distribution servers, we were interested to look at the APAC regional numbers specifically for Emotet distribution. Narrowing down per regional country also helps in response efforts with associated national CERTs.
Emotet Campaign Overview
An important aspect to the overall Emotet campaign modus operandi, is the use of compromised legitimate domains to host and distribute the Emotet delivery docs and executables. Looking at the compromised domains, we note that the majority of the domains are SMEs with legitimate businesses. SME organizations often don’t update or patch their web servers, likely due to their limited resources. This allows cyber-criminals, like the Emotet actors, to exploit the server-side vulnerabilities and host the malicious Emotet variants that are then delivered via http links, embedded in the malspam campaigns.
Figure 1 below gives a high-level overview of how Emotet campaigns infect victim machines. The actors first scan the internet for vulnerable web-servers, which are then exploited and used to host the malicious Emotet variants. The actors then proceed with their email spam campaigns with legitimate-looking themes to lure victims to click on the attached URL that downloads the Emotet delivery document or executable from the compromised domain hosting the malware. In the case of Emotet delivery documents, it typically includes a macro that then downloads and executes the Emotet payload, infecting the victim’s machine. Whereas in other cases, Emotet executables are downloaded directly from the compromised domains and infect the victim’s machine to join the wider Emotet botnet.
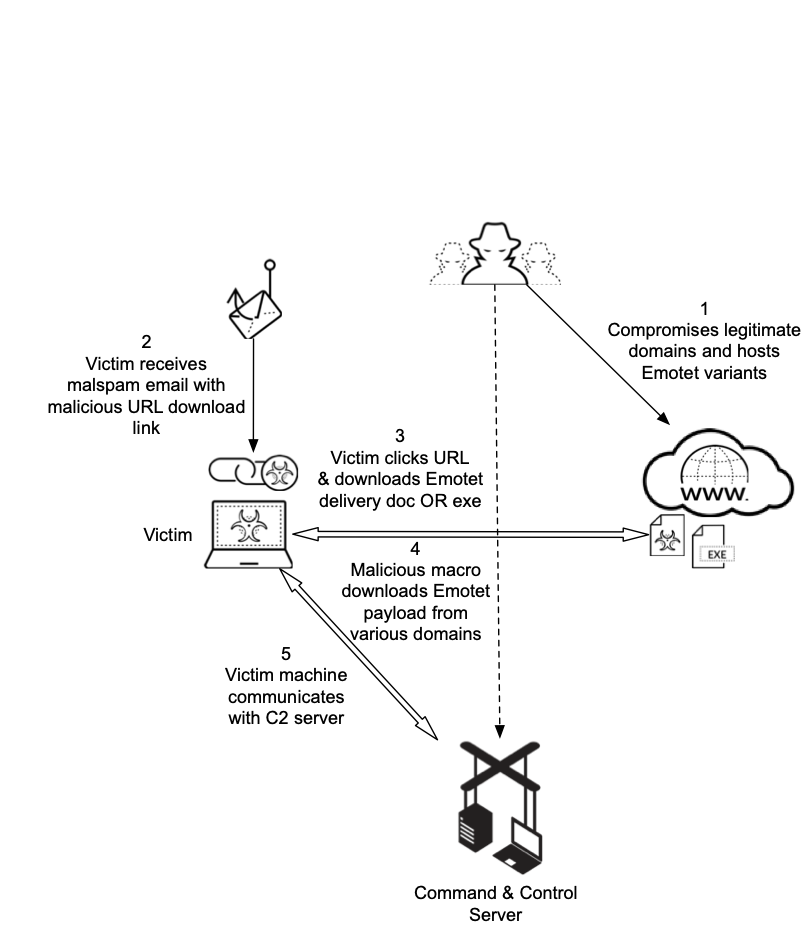
Figure 1. Current depiction of Emotet delivery using distribution servers.
Return of Emotet
Our data indicates malspam and command and control (C2) activity for Emotet has been active as of September 16, 2019 after a three-and-a-half-month break. This has been confirmed by media reports through several other sources. While most of the reports published on Emotet’s malspam campaign gives a good understanding on the possible number of victims or victim geolocation, we would like to focus on the use of compromised legitimate domains. These are used as distribution servers for Emotet’s initial malicious document variants and try and give an understanding on which countries within APAC are largely impacted.
APAC Distribution Servers
Various criminal groups often use compromised servers from legitimate domains to distribute malware. This is a common tactic, because most networks from legitimate domains are less likely to be blocked by a targeted organization. Therefore, these Emotet Word documents and executable files are far more likely to reach a victim's host.
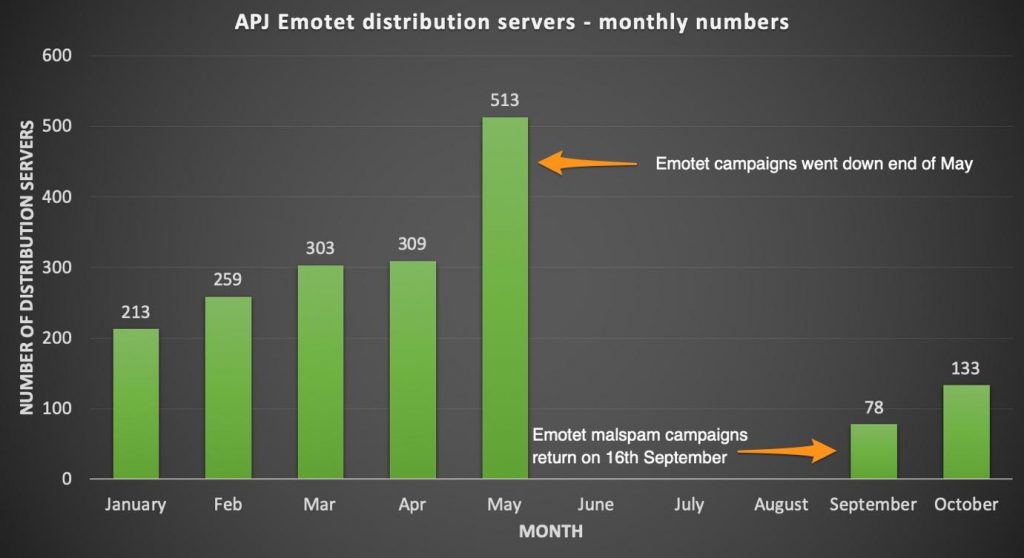
Looking at our datasets and extracting all APAC related domains involved in the spreading of Emotet malware since January 2019, we can see a clear increase in distribution servers used by the Emotet actors since early 2019. As mentioned above, the Emotet malspam campaigns went dark towards the end of May, but it is important to note from Figure 2 that the number of distribution servers used during the month of May was significantly higher than previous months, which may imply that the actors intended to grow their botnet and also possibly profit as much as possible before they took a break.
Figure 2 Emotet monthly distribution servers since January 2019
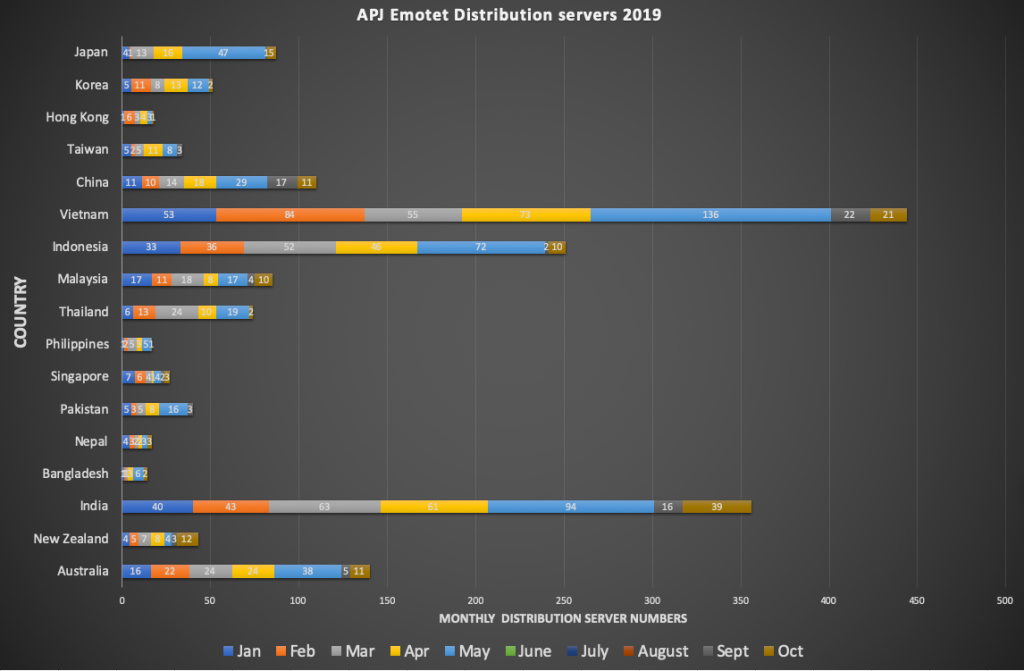
Drilling down to country-specific domains, we can discern some interesting insights into the most affected countries. As seen in Figure 3 below, the top affected countries are Vietnam, India, Indonesia, Australia, China and Japan, followed by several ASEAN nations.
Our data below reveals a large number of vulnerable servers across APAC are exploited by Emotet actors to distribute Emotet variants. This data also indicates that a large number of SME’s fail to perform best practices, like patching their systems on a regular basis, resulting in them being exploited and becoming a critical part of the overall success of the Emotet campaign.
Figure 3 Distribution servers by Country
It is important to note that the majority of the compromised domains are running the WordPress blogging software. A quick search for WordPress vulnerabilities on vulnerability tracker sites, like “CVE Details”, shows the high number of vulnerabilities that have been disclosed for WordPress. A similar search on “Exploit-DB” also shows the high number of exploits being published every month in the public domain, allowing anyone to reuse the exploits published. While the understanding of Emotet actors exploiting vulnerable WordPress sites is not new to the security community, it is important to stress and highlight this again to raise the awareness for organizations to patch their web applications as soon as possible and deter threat actors like the Emotet gang to take advantage of the vulnerabilities and avoid a more devastating impact.
Conclusion
While Emotet has been active for a number of years, their ongoing campaign numbers, modular platform, disruptive capability, related incidents and the associated recovery costs for organizations show that this is one of the most significant cyber threats of the current era. Our emphasis on the distribution servers across the APAC region on this blog was to gain visibility on regional, in-country numbers and also to streamline remediation efforts and raise awareness on how cybercriminals are taking advantage of vulnerable SME’s. We also set out to illustrate why it is imperative for SME’s to improve their cyber-hygiene on patching their respective web-servers and applications. We are concurrently working with respective, in-country national CERT teams to share the details on the affected compromised domains for possible remediation.
Palo Alto Networks customers are protected from this threat. Our threat prevention platform detects Emotet malware, with Wildfire while and simultaneously updating the ‘malware’ category within the PAN-DB URL filtering solution for compromised domains it has identified.
AutoFocus users can track this activity using the Emotet tag.
IOCs:
https://github.com/pan-unit42/iocs/tree/master/emotet/sha256-hashes











 Get updates from Unit 42
Get updates from Unit 42