Executive Summary
Many illicit network services, including phishing campaigns and online gambling platforms, exploit traffic distribution systems (TDS) to redirect network traffic. A TDS acts as a central hub, redirecting victims through an often complex network of servers to obfuscate the final destination and hinder detection of these operations. This infrastructure also facilitates the management of multiple malicious endpoints simultaneously.
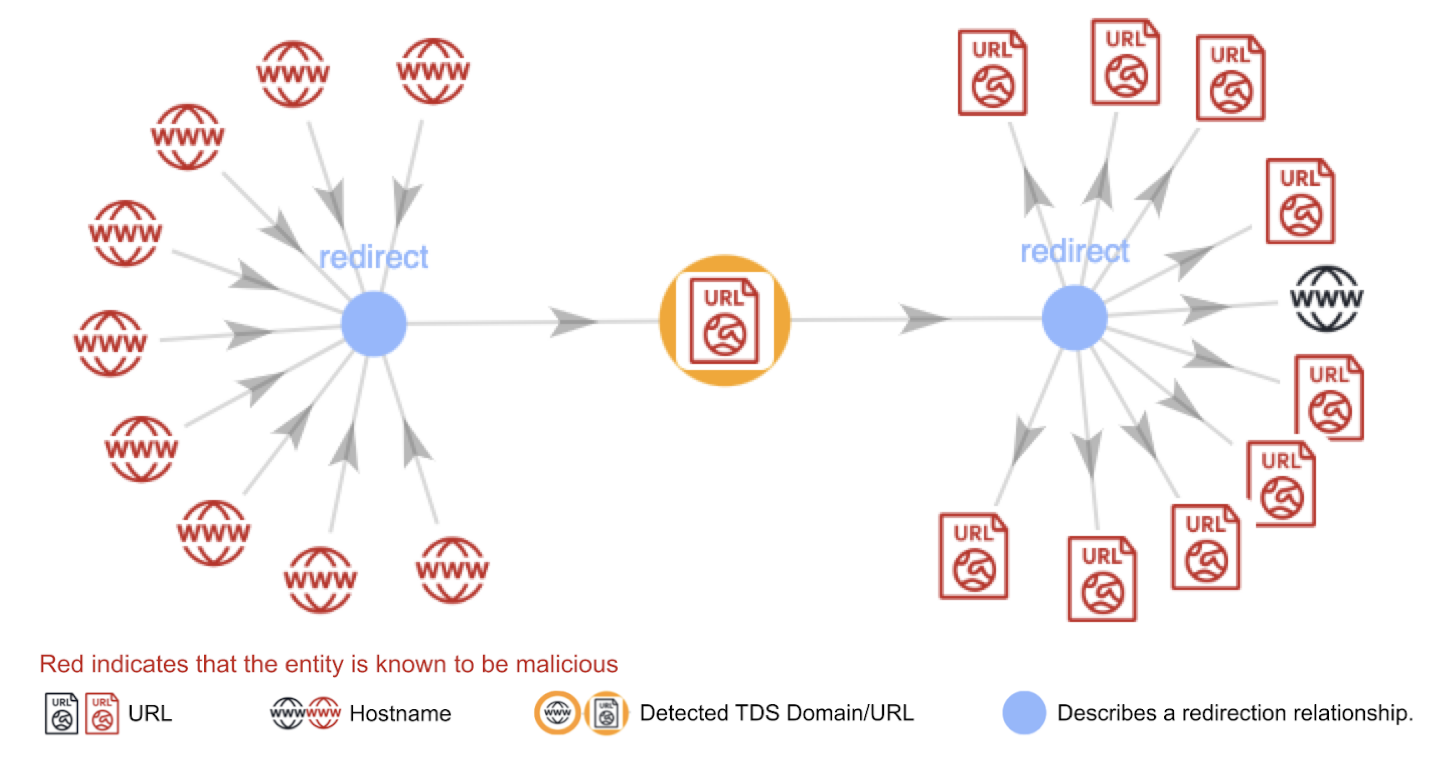
Analyzing the resolution and redirection traffic allows us to construct relationship networks among different URLs and identify TDS infrastructure. We have found that malicious TDS traffic exhibits significant topological characteristics compared to benign redirection networks. For example, malicious TDS infrastructure typically presents more URLs and a higher number of connections than benign TDS networks.
We combined the topological insights about malicious TDS infrastructure and comprehensive threat intelligence to build a machine learning (ML) powered malicious TDS detection system. Our detection system can capture various malicious TDS infrastructure hosting different types of cyberthreats or suspicious activities including malvertising, phishing and gambling services.
Our Advanced DNS Security and Advanced URL Filtering services continuously monitor and scan the traffic in our customers’ networks to hunt for malicious indicators.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | DNS, Phishing |
Malicious Traffic Distribution Systems
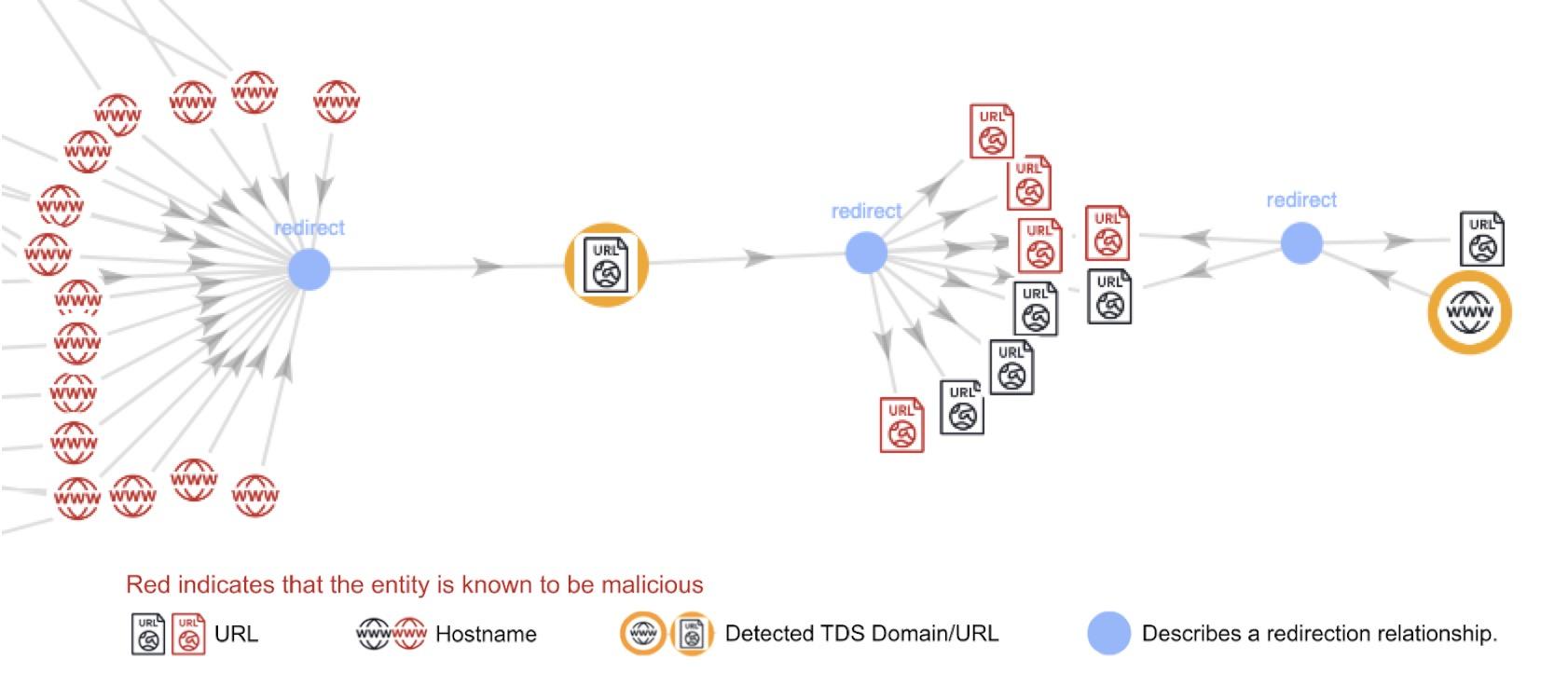
A TDS is a traffic redirection network containing multiple sources, intermediates and landing nodes. Attackers often employ social engineering tactics, such as phishing emails with malicious links disguised as invoices, to lure victims into malicious redirection chains via entry point webpages.
These entry points lead to a series of intermediate domains that obfuscate the origin of the attacks. The intermediate domains then take victims to final landing pages, which deliver the actual network threats, such as malware download links or fake login pages that steal the victims’ credentials.
Threat actors have several motivations to develop network attacks using TDS infrastructure.
- Resilience against takedown efforts: Attackers can swiftly change TDS entry and landing points whenever these are blocked, making them hard to take down fully
- Obfuscation and cloaking: By randomly redirecting visitors to legitimate websites, a TDS can evade the detection and analysis of automated crawling services
- Traffic monetization: The dynamic nature of TDS redirection logic allows attackers to provide content delivery service for different shady websites or help the attackers to monetize their traffic
Legitimate organizations also use TDS infrastructure to make their services more reliable and flexible. For example, marketing return-on-investment (ROI) tracking services often leverage TDS infrastructure to manage and improve their traffic flow. These tracking services require customers to follow outgoing links to the tracking TDS, which dynamically redirects traffic to different landing pages based on visitor parameters such as geolocation, device type and referrer.
We continuously crawl and analyze millions of websites daily. Based on the results, we constructed graphs that illustrate redirection flows between network endpoints and identify TDS indicators among the data. To gain deeper insights into the behavior of both malicious and legitimate TDS traffic, we conduct a large-scale topological analysis on these redirection graphs.
Our topological analysis studies the structure and relationships between connected elements in a network to understand its characteristics. We found three interesting insights about the difference between malicious and benign TDS traffic:
- Malicious TDS traffic has longer redirection chains than benign traffic
- Malicious TDS traffic contains more distinct URLs than benign traffic
- Malicious TDS traffic demonstrates a higher connectivity level among URLs
By examining the topological features of both malicious and legitimate TDS infrastructure, we observed significant differences that reveal distinct usage patterns. Using the results, we can develop a highly accurate detector to identify malicious TDS activity.
Malicious TDS traffic tends to have longer redirection chains compared to benign traffic. Figure 1 presents the cumulative distribution function (CDF) of the maximum redirection chain length for both. A CDF shows the probability that a random variable will be less than or equal to a certain value.
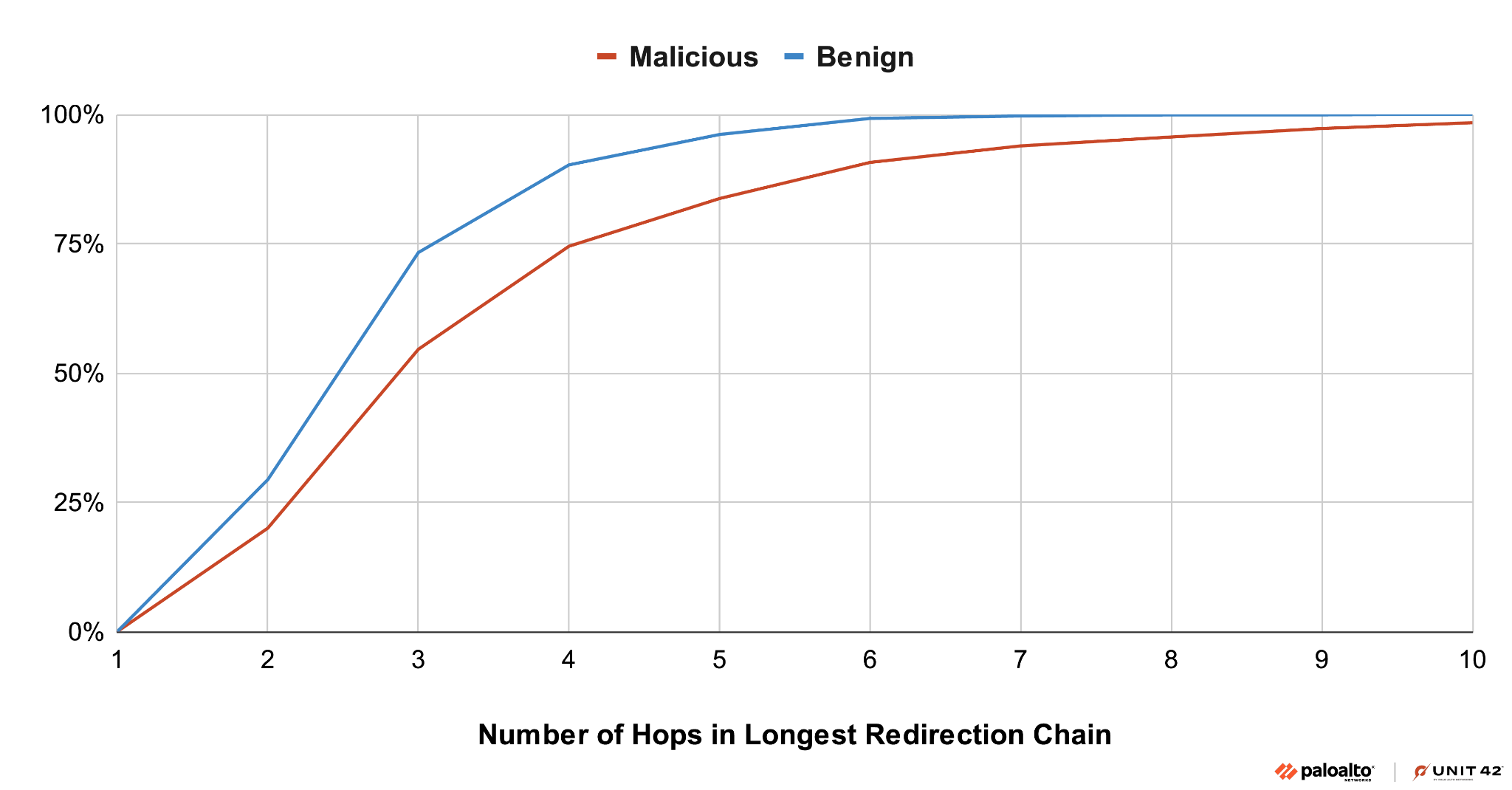
Figure 1 shows that approximately 25% of malicious TDS activity has its longest redirection chains at more than four hops (100% minus 75%). For benign TDS, this percentage is only approximately 10% (100% minus 90%).
These statistics highlight malicious redirection behaviors used for cloaking and obfuscation purposes. By using longer redirection chains, they can obscure the final malicious landing pages with multiple intermediate cloaking nodes to evade detection.
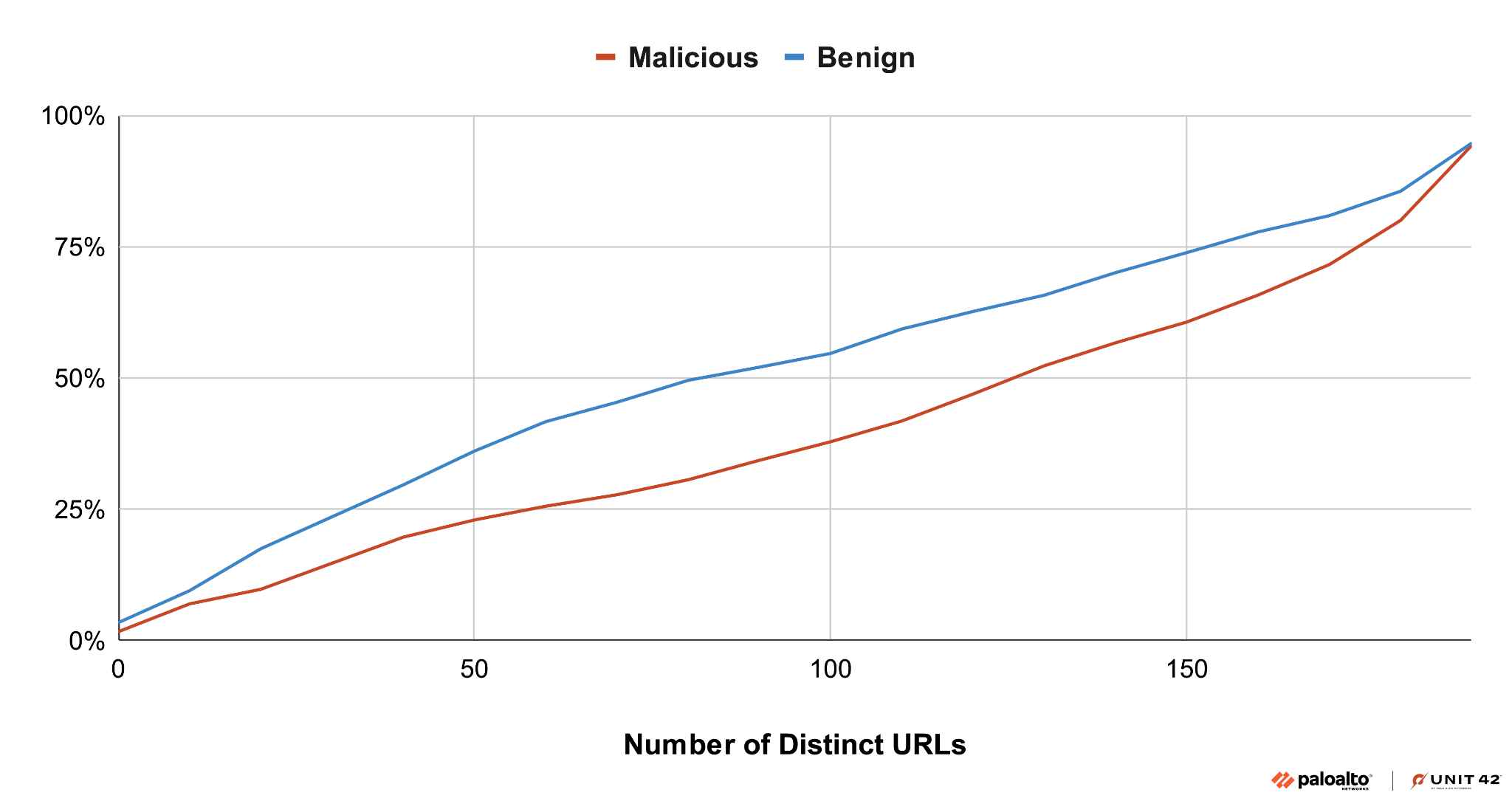
Malicious TDS graphs are also characterized by their larger size and higher connectivity among nodes. We discovered this feature by analyzing the CDFs of TDS URLs and subgraphs numbers. Figure 2 shows that malicious TDS traffic involves more URLs compared to benign traffic, represented by the red line for malicious TDS data being lower than the line for benign. Specifically, the median number of URLs in malicious TDS is 126, compared to 80 in benign TDS.
A TDS consists of multiple redirection chains that involve the same set of domains. However, not all URLs are fully connected, resulting in isolated subgraphs within a TDS redirection graph.
Figure 3 shows that malicious TDS graphs have fewer isolated subgraphs, since the line representing malicious TDS activity in the CDF graph is above the blue line representing the benign TDS data. About 40% of malicious TDS activity consists of a single subgraph, meaning all their URLs are interconnected. In contrast, only 20% of benign TDS activity has just one subgraph.
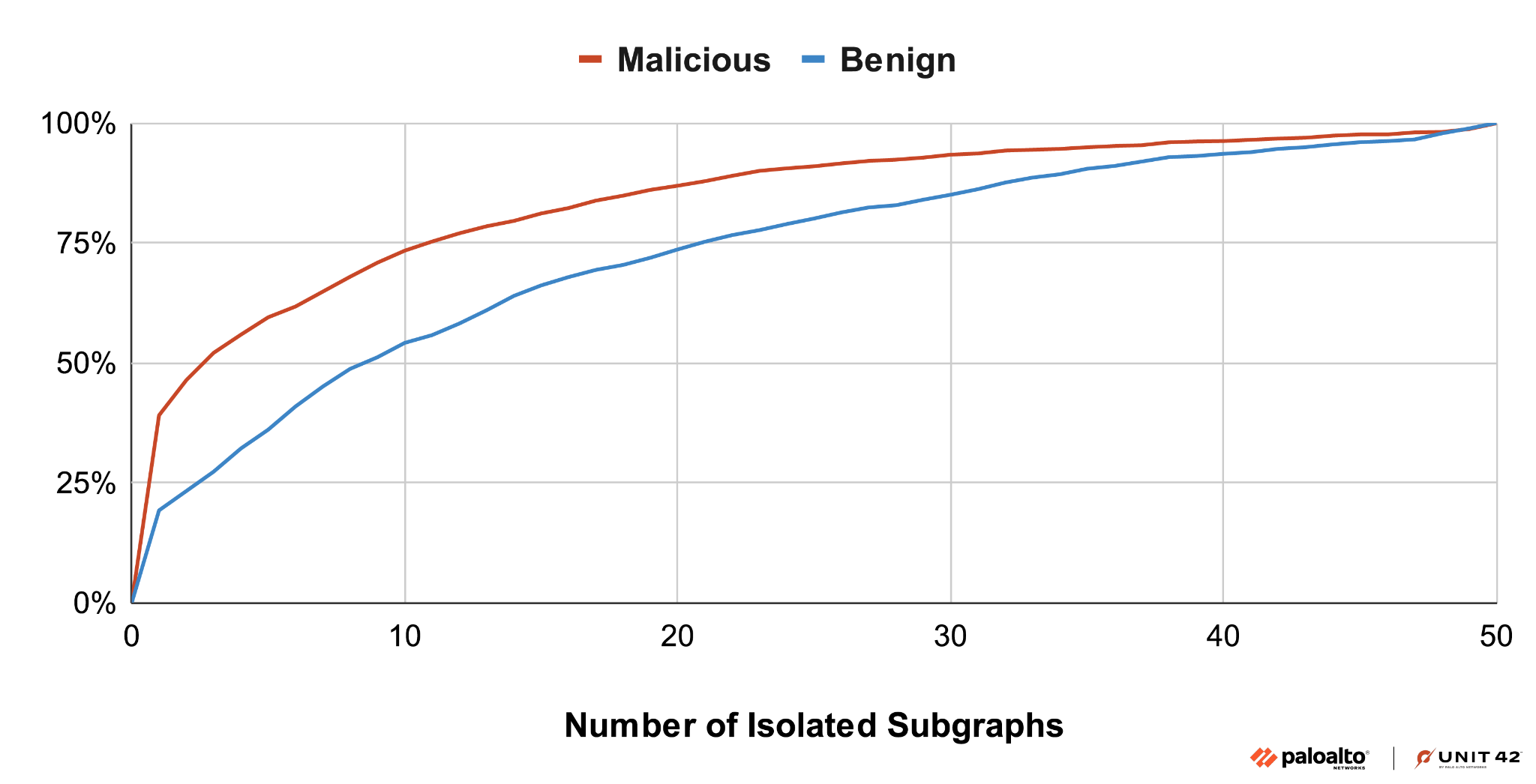
These two observations indicate that malicious TDS activity has greater overall connectivity among URLs, suggesting that attackers are more likely to exploit the dynamic redirection capabilities of a TDS. In contrast, benign TDS activity, such as tracking services, tends to set up dedicated URLs for specific entry and landing nodes.
Case Study
This section examines various examples of malicious TDS infrastructure use and how attackers exploit it for network abuse.
TDS for Phishing
TDS infrastructure is widely abused to deliver malicious web content, especially phishing websites. One of the phishing TDS campaigns we analyzed was a fraudulent cryptocurrency giveaway mimicking a decentralized app store.
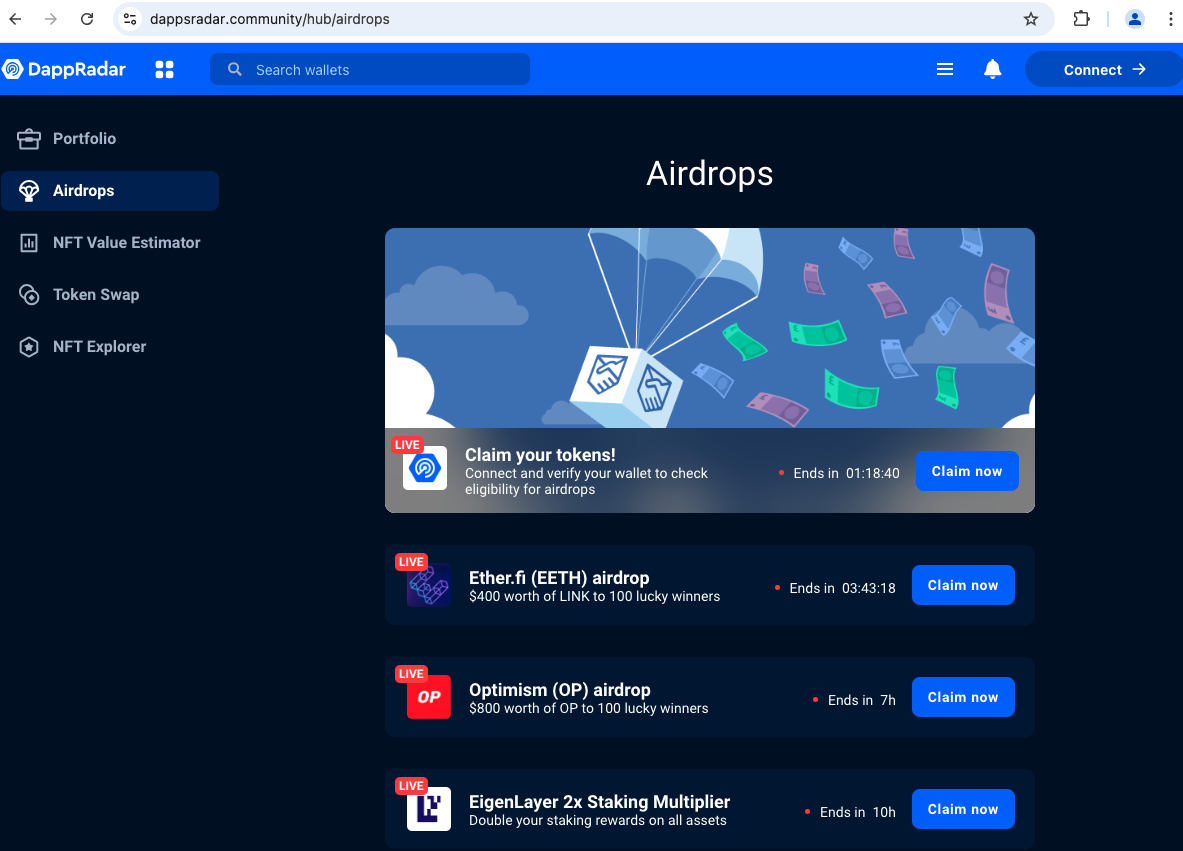
Figure 4 illustrates part of this TDS structure. It contains many squatting domains including dapparadar[.]app, dappadar[.]community and dappadar[.]bio.
These squatting domains all redirect to the same landing page, which is a phishing page that mimics a cryptocurrency airdrop system, as shown in Figure 5.
TDS for Malvertising
Malvertising TDS campaigns redirect visitors to different shady advertising pages. TDS operators can sell this redirected traffic to malicious services. A TDS serves as a platform that makes the network infrastructure more scalable and flexible, allowing for the easy addition or removal of landing pages.
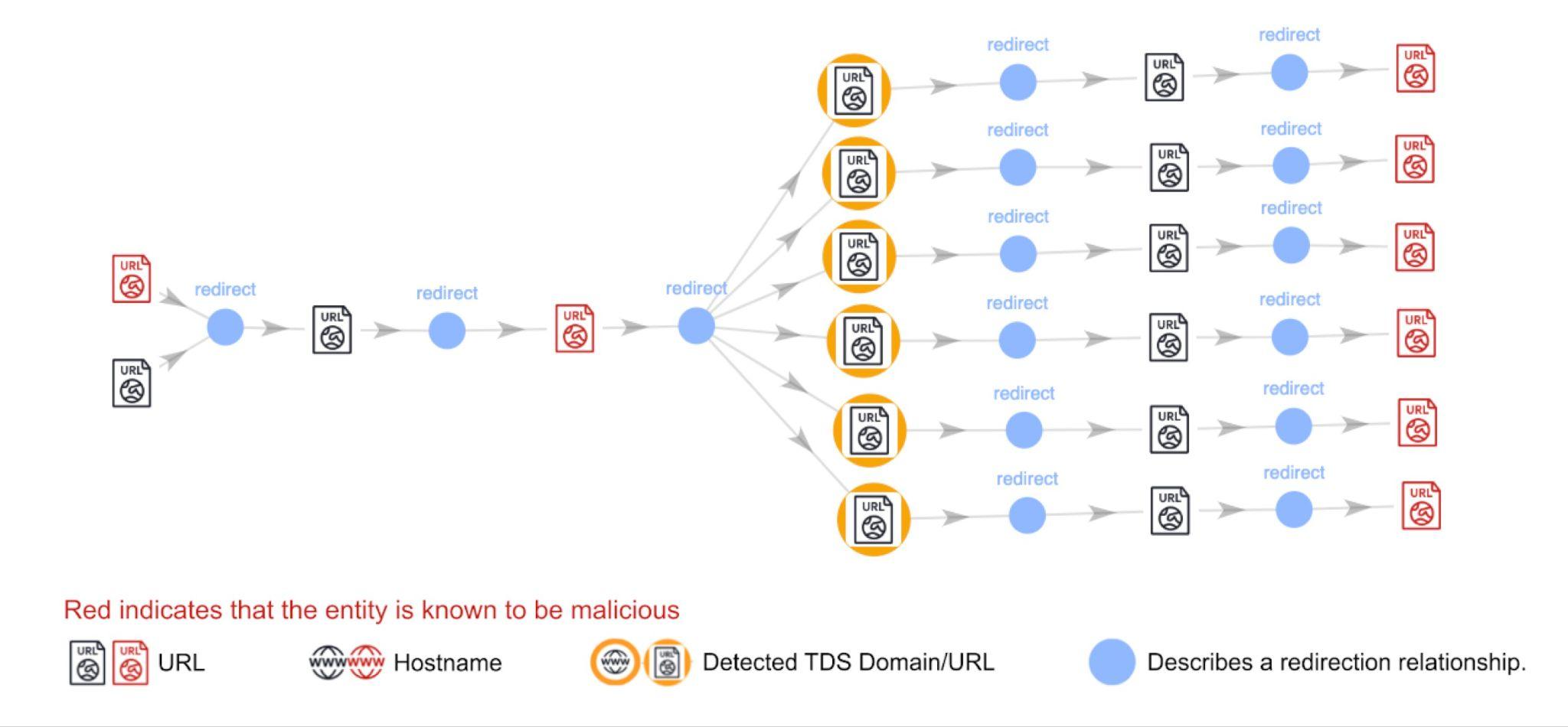
Figure 6 is part of the redirection graph for a malvertising TDS campaign. Visitors from the same entry website are redirected to different URLs under vkmarketing2[.]com, then to various shady landing pages.
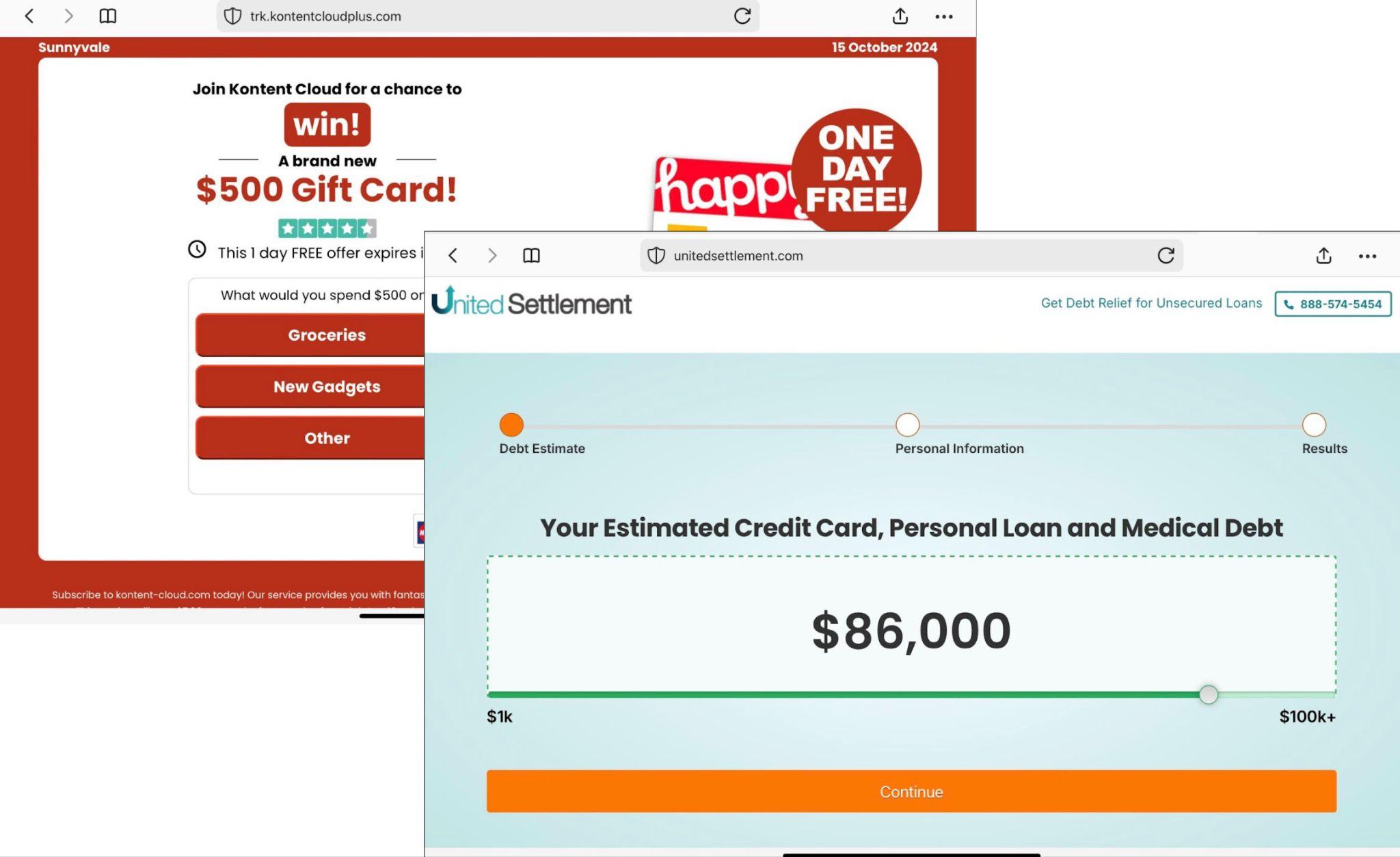
After two or more hops, the TDS infrastructure directs visitors to shady advertisement pages offering things like gift card rewards and loans (Figure 7).
TDS for Darknet or Illicit Services
Besides acting as a shared traffic distribution platform, a TDS can be abused for darknet services. Although these services are not inherently malicious, they are often subject to strict internet censorship, particularly in areas such as gambling and adult websites. We discovered a campaign that built a large TDS using a large number of domain generation algorithm (DGA) based .lol domains as intermediate redirection nodes.
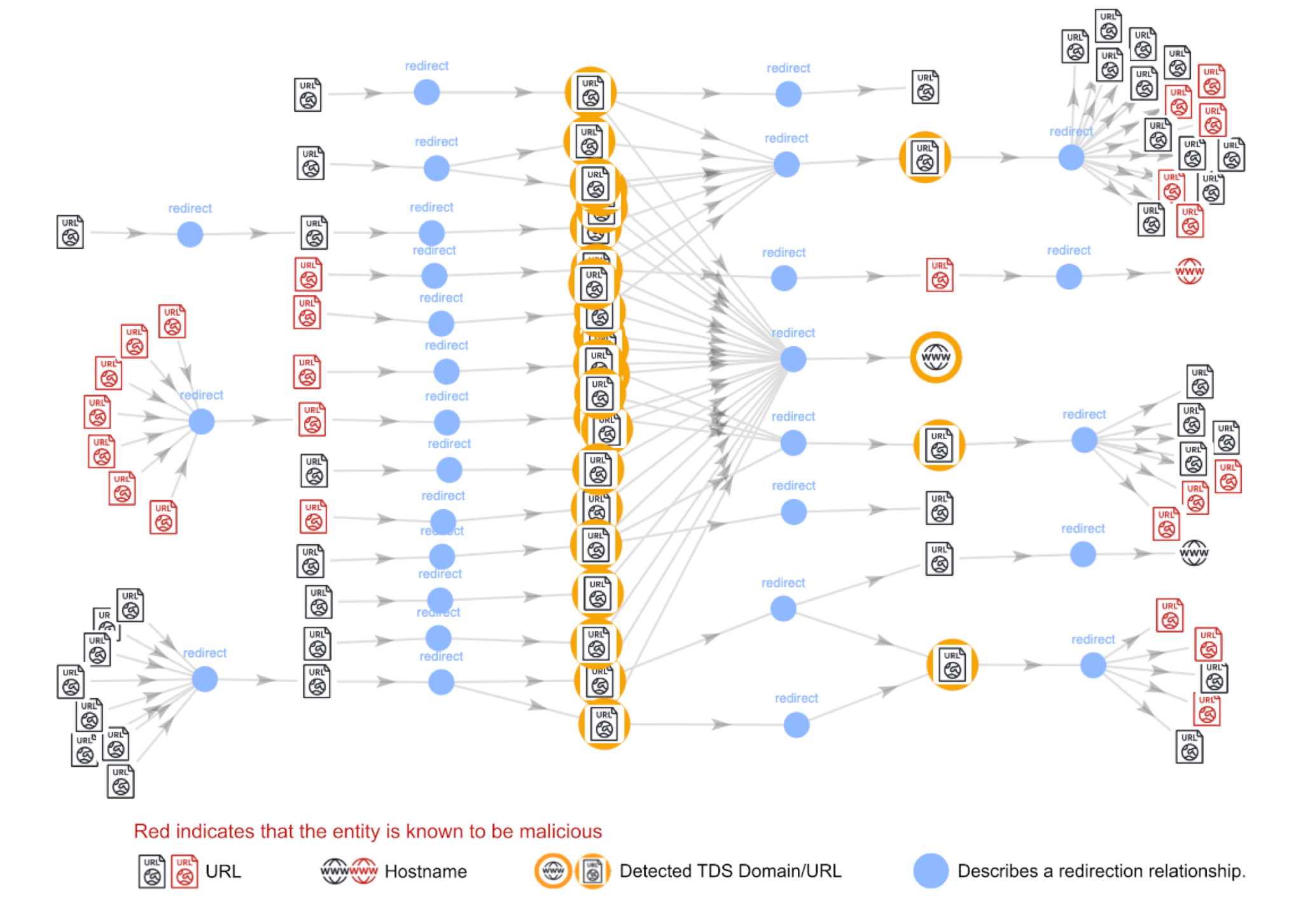
Figure 8 shows part of the redirection network hosting this illicit service. All redirection chains are centered around different DGA .lol domains and their randomly generated subdomains.
We identified 139 .lol malicious domains actively serving this campaign from May-October 2024. We also observed that the adversaries registered many DGA domains in bulk and integrated them into the service shortly after the registration. For example, xd2kdw[.]lol, ba3e7q[.]lol and 7eh3gj[.]lol were created on August 22, 2024, and began carrying malicious traffic in mid-September.
This structure, with all TDS domains connected to the same entry and landing nodes, makes the dark market service resilient to takedowns. Even if one domain is taken down, the others remain functional.
Since May 2024, we observed emerging DGA domains serving this campaign, with increased registrations and traffic by August and September. We also identified entry and landing domains using uncommon TLDs like .xyz, .mom and .pics.
Figure 9 shows the campaign’s landing page, which is a portal to Chinese gambling and adult content.
TDS for Cloaking
Threat actors can abuse TDS infrastructure to conceal malicious content by redirecting the visitor to legitimate websites. We identified a recent example using mobesti[.]com for a phishing campaign.
Figure 10 shows how this campaign directed visitors from various entry domains to phishing websites. To obscure the malicious activities, this type of TDS campaign occasionally redirects to legitimate sites including the Google Play download page for TikTok or the Yahoo homepage. This tactic can mislead automated crawlers into viewing the TDS infrastructure as a legitimate redirection service, resulting in a benign verdict.
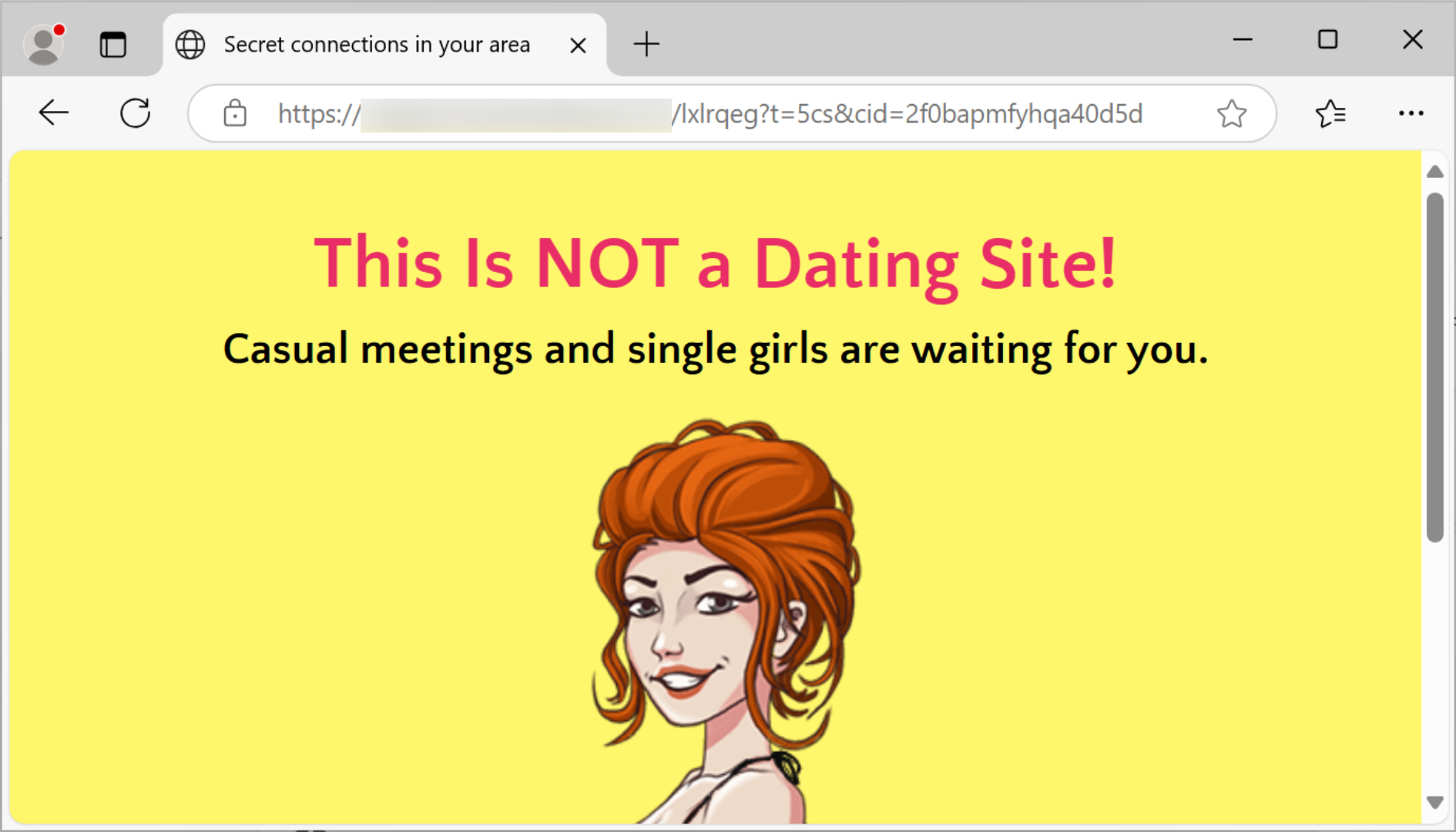
This phishing campaign attracts victims’ attention with an adult-themed phishing site shown in Figure 11. The threat actor used dating-related keywords to create phishing domains such as 3adating[.]com and meetyoursoulmate[.]life.
Conclusion
Adversaries widely abuse TDS infrastructure to build dynamic and resilient network infrastructure for malicious web services. These redirection networks enhance resilience against takedowns and enable scaling and cloaking of malicious content.
Machine Learning Based Detection
By dynamically analyzing malicious websites and associated redirection chains, we gained insights into the characteristics of this type of malicious network infrastructure, enabling more comprehensive blocking of attacking network entities. Based on the topologic and threat-related features, we developed an aggregated ML model to detect malicious TDS activity automatically.
We extracted 20 features from TDS graphs to detect malicious traffic distributors. Figure 12 shows the most important features.
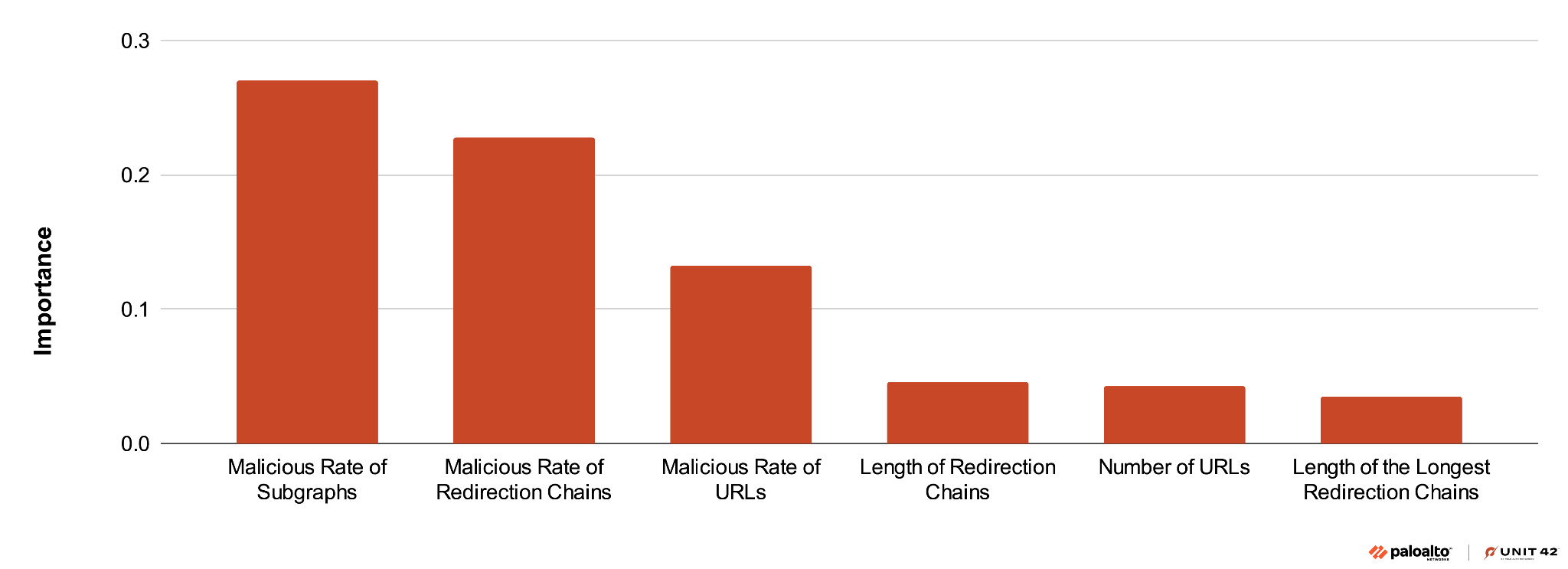
The top three features are the malicious rates across three categories with importance increasing with scope size (i.e., URL, redirection chain and subgraph). Key topological characteristics include redirection chain length and the number of URLs, which quantify TDS connectivity.
We trained multiple ML models to detect malicious TDS activity based on topologic and threat-related features. We selected thresholds for each model based on precision to ensure the detection quality. The overall detector aggregate results from multiple models to achieve 93% precision with a 0.4% false positive rate.
Palo Alto Networks Next-Generation Firewall customers are better protected against malicious domains mentioned in this article and more emerging malicious TDS activity. This includes protection through our detector via Advanced DNS Security and Advanced URL Filtering subscription services.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
The following malicious or shady domains are referenced in this article:
- 3adating[.]com
- 7eh3gj[.]lol
- ba3e7q[.]lol
- dappadar[.]bio
- dappadar[.]community
- dapparadar[.]app
- meetyoursoulmate[.]life
- mobesti[.]com
- vkmarketing2[.]com
- xd2kdw[.]lol









 Get updates from Unit 42
Get updates from Unit 42