In October, we called out a series of attacks installing the Dridex Trojan using macros in Microsoft Word documents. Those attacks continued over the last few months and in first two weeks of the new calendar year we’ve seen another new campaign.
To refresh your memory, Dridex is the latest version of the Bugat/Feodo/Cridex banking Trojan. Its core functionality is to steal credentials of online banking websites and allow a criminal to use those credentials to initiate transfers and steal funds. Dridex is currently being distributed through an e-mail campaign that carries a Word Document attachment, which uses built-in macro code to download and execute a copy of the Trojan.
While Dridex targets banks from all over the world, in October the majority of the e-mails we tracked were destined for the United States, with the United Kingdom coming in at a distant second place. This time around the UK comes out on top, with over one third of all attacks observed there.
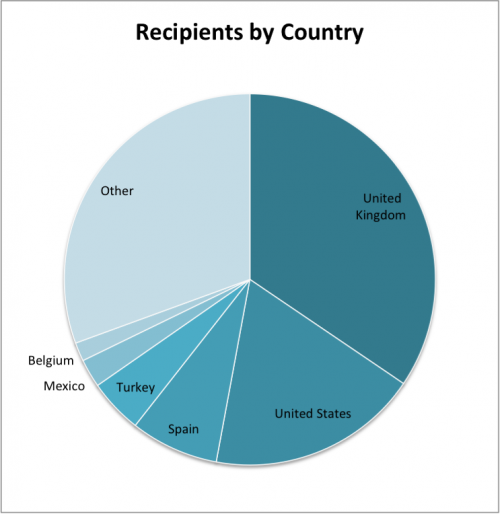
This change in targeting is also clear in the themes used in each of the attacks. Many of the most-common attachment names refer to the BACS, or Bankers' Automated Clearing Services, which is used for bank transfers in the UK. Another group of e-mails claimed to be an invoice from the Les Mills UK, a fitness organization. This campaign is likely preying on individuals who have made New Year’s resolutions to get fit in the UK.
In October we had identified just six URLs used by the Word documents to download the Dridex Trojan. In the past two weeks we’ve detected files using 43 different download locations.
- 108.59.252.116/mops/pops.php
- 111.125.170.132/doc/8.exe
- 159.253.19.113/ord/1.exe
- 178.77.79.224/mops/pops.php
- 188.241.116.63/mops/pops.php
- 192.157.233.28/ord/1.exe
- 192.227.167.32/mops/pops.php
- 193.136.19.160/mans/pops.php
- 194.28.139.100/mans/pops.php
- 206.72.192.15/mans/pops.php
- 213.174.162.126/mans/pops.php
- 213.9.95.58/mans/pops.php
- 87.106.165.232/mans/pops.php
- aircraftpolish.com/js/bin.exe
- betterinnovation.net/modules/mod_arateiclws/cr_7_2711_2.exe
- cerovski1.net.amis.hr/js/bin.exe
- curie-hennebont.fr/js/bin.exe
- dollarbrasil.com.br/444
- ecovoyage.hi2.ro/js/bin.exe
- elsy.pwp.blueyonder.co.uk/444
- fachonet.com/js/bin.exe
- gofoto.dk/js/bin.exe
- gv-roth.de/js/bin.exe
- interativaonline.com/444
- jasoncurtis.co.uk/js/bin.exe
- lapiden.com/wp-content/themes/twentytwelve/mss20.exe
- lapiden.com/wp-content/themes/twentytwelve/mss22.exe
- lichtblick-tiere.de/js/bin.exe
- media.mystudio.net/js/bin.exe
- microinvent.com/js/bin.exe
- nestorausqui.com/444
- ngrbook.com/cp/images/digits/blushdw/cr_7_2711_2.exe
- nubsjackbox.oboroduki.com/js/bin.exe
- obuwiehurt.com.pl/js/bin.exe
- paulmartinseo.com/wp-content/themes/twentyten/cr_7_2711_13.exe
- phaluzan.net.amis.hr/js/bin.exe
- riccis.homepage.t-online.de/Testseite/js/bin.exe
- sardiniarealestate.info/js/bin.exe
- ticklestootsies.com/js/bin.exe
- walkdesign.com/wp-content/themes/willow/cr7_2711_1.exe
- weme-systems.de/modules/mod_arateiclws/mss3.exe
- www.isolectra.com.sg/tmp/rk2n1.exe
- zusso.jp/444
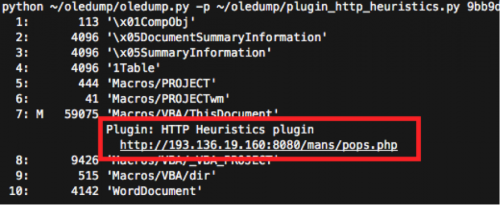
Many of these URLs are hosted on compromised websites, but there is no clear pattern to indicate how they are taking control of the websites. However, there are clear groupings of patterns for the download URLs. One group relies on the path “/js/bin.exe” while another uses “mops/pops.php”. These URLs are encoded within the macros included in each file. If you are interested in extracting them, Rodel Mendrez from SpiderLabs wrote a short guide using Python. If you want to take the simpler route, Didier Steven’s OLE Dump tool has a plug-in that will automatically decode and extract these URLs, as shown below.
Palo Alto Networks WildFire detects all of these macro-based attacks using our sandbox technology. Others can protect themselves by disabling macros in Microsoft Word. Macro-based malware has been around for over well over a decade. Most organizations should disable them by default, enabling macros only for trusted files.












 Get updates from Unit 42
Get updates from Unit 42