SolarStorm Response With Next-Generation Firewall
It is possible to identify SolarWinds systems in a network using NGFW traffic monitoring. This section provides details of multiple queries and examples of their outputs. It is imperative for customers to employ the best practices for Palo Alto Networks products in order to ensure their appliances are configured in a manner best suited for their protection.
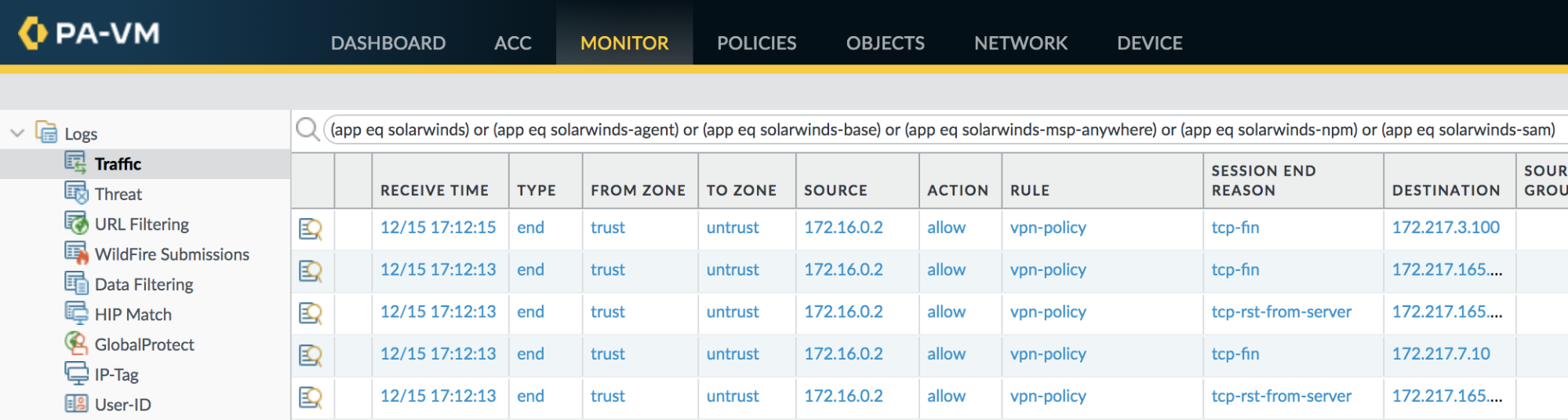
The following query filter will identify hosts contacting a server using the SolarWinds App-ID.
|
1 |
(app eq solarwinds) or (app eq solarwinds-agent) or (app eq solarwinds-base) or (app eq solarwinds-msp-anywhere) or (app eq solarwinds-npm) or (app eq solarwinds-sam) |
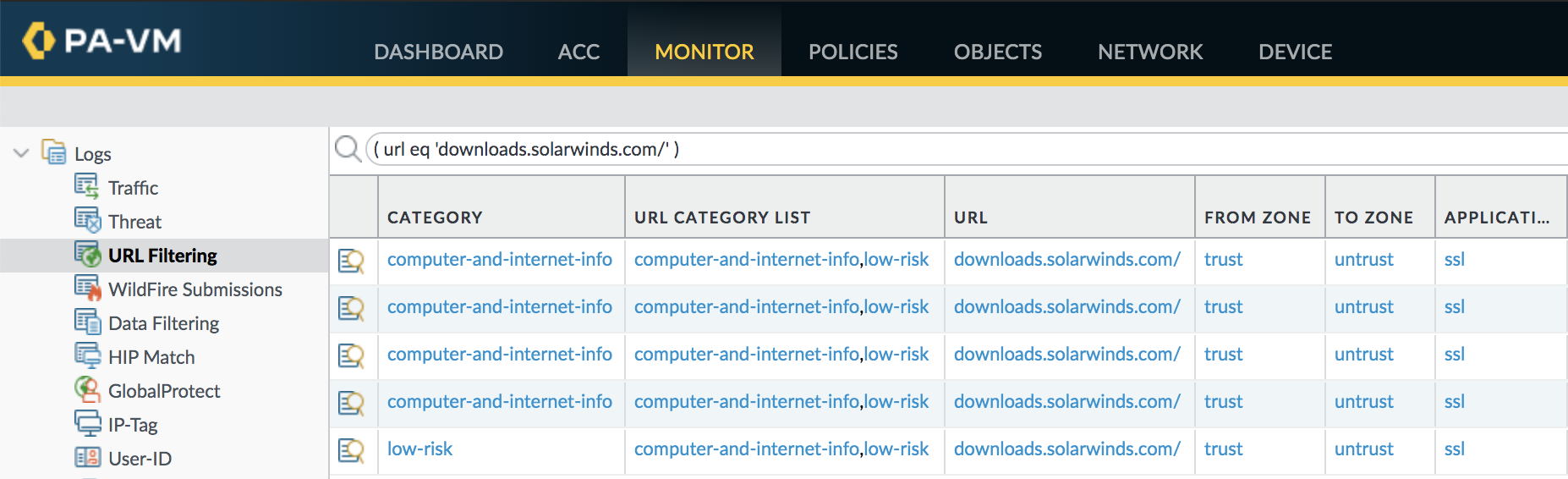
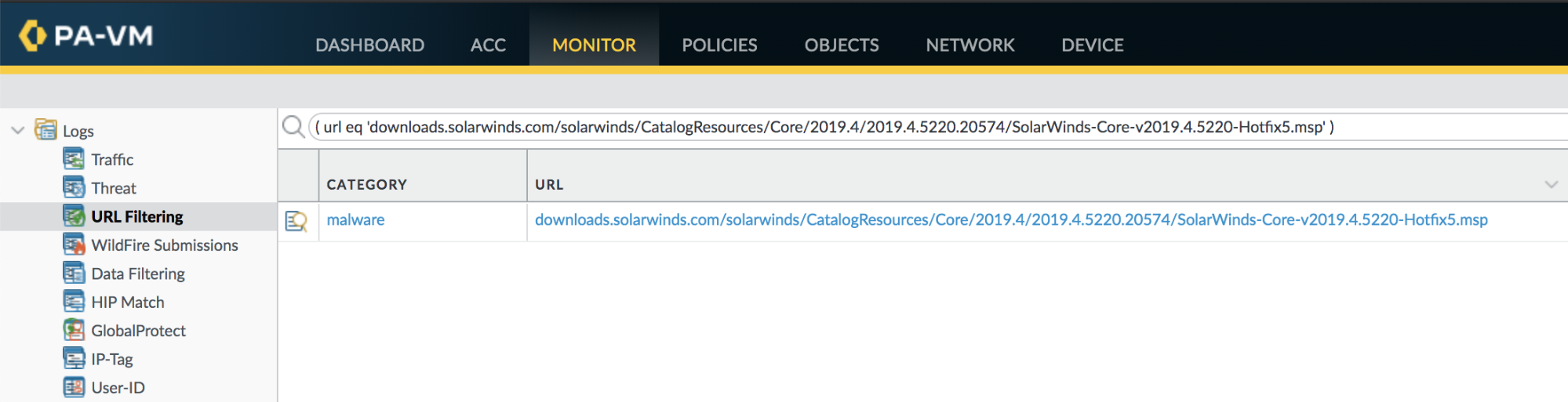
URL Filtering can also help identify compromised servers. This query filter will identify systems connecting to the SolarWinds download server and specifically downloading the SUNBURST plugin update.
|
1 |
( url contains downloads.solarwinds.com ) or ( url eq 'downloads.solarwinds.com/solarwinds/CatalogResources/Core/2019.4/2019.4.5220.20574/SolarWinds-Core-v2019.4.5220-Hotfix5.msp' ) |
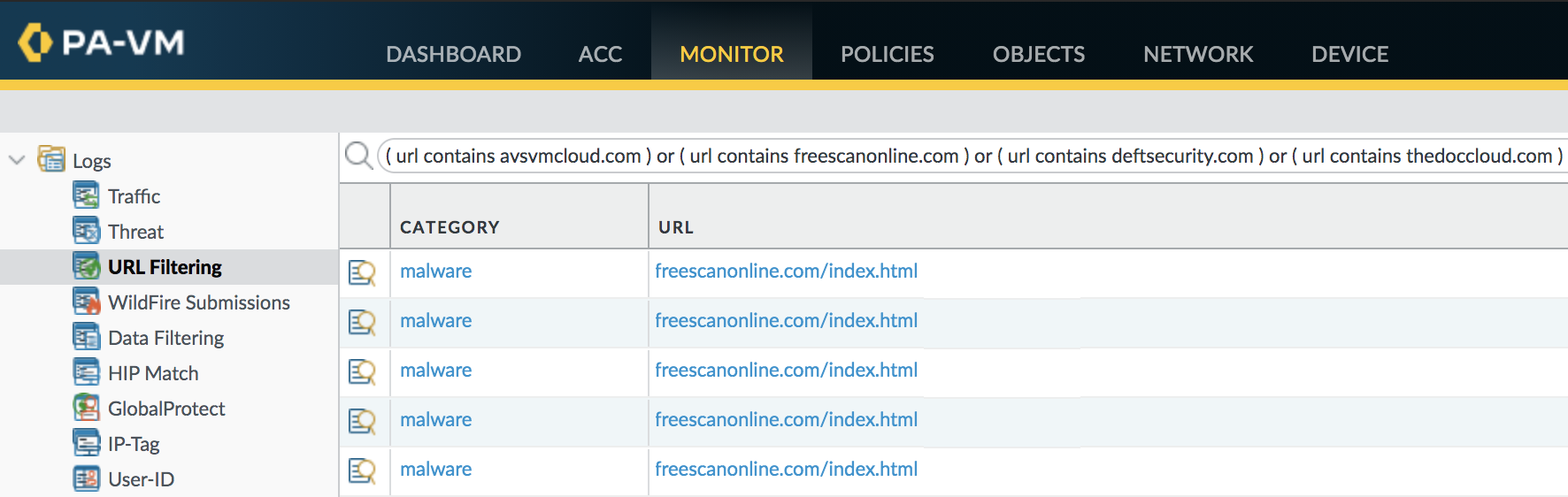
The following URL Filtering query will identify traffic to the known SUNBURST command and control domains:
|
1 |
( url contains avsvmcloud.com ) or ( url contains freescanonline.com ) or ( url contains deftsecurity.com ) or ( url contains thedoccloud.com ) or ( url contains websitetheme.com ) or ( url contains highdatabase.com ) or ( url contains incomeupdate.com ) or ( url contains databasegalore.com ) or ( url contains panhardware.com ) or ( url contains zupertech.com ) or ( url contains virtualdataserver.com ) or ( url contains digitalcollege.org) |
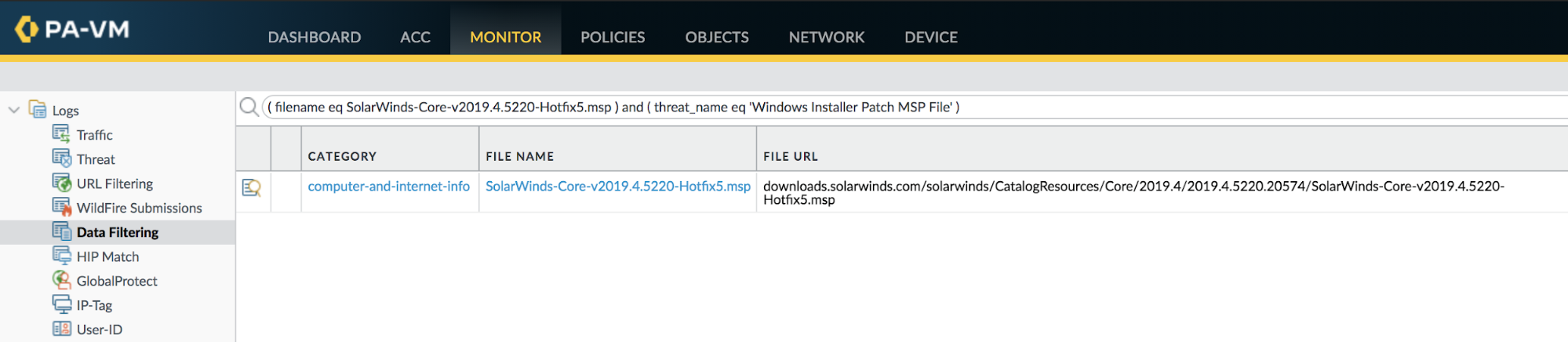
File Blocking will identify hosts that have downloaded the known filenames associated with the SUNBURST plugin update.
|
1 |
( filename eq SolarWinds-Core-v2019.4.5220-Hotfix5.msp ) and ( threat_name eq 'Windows Installer Patch MSP File' ) |
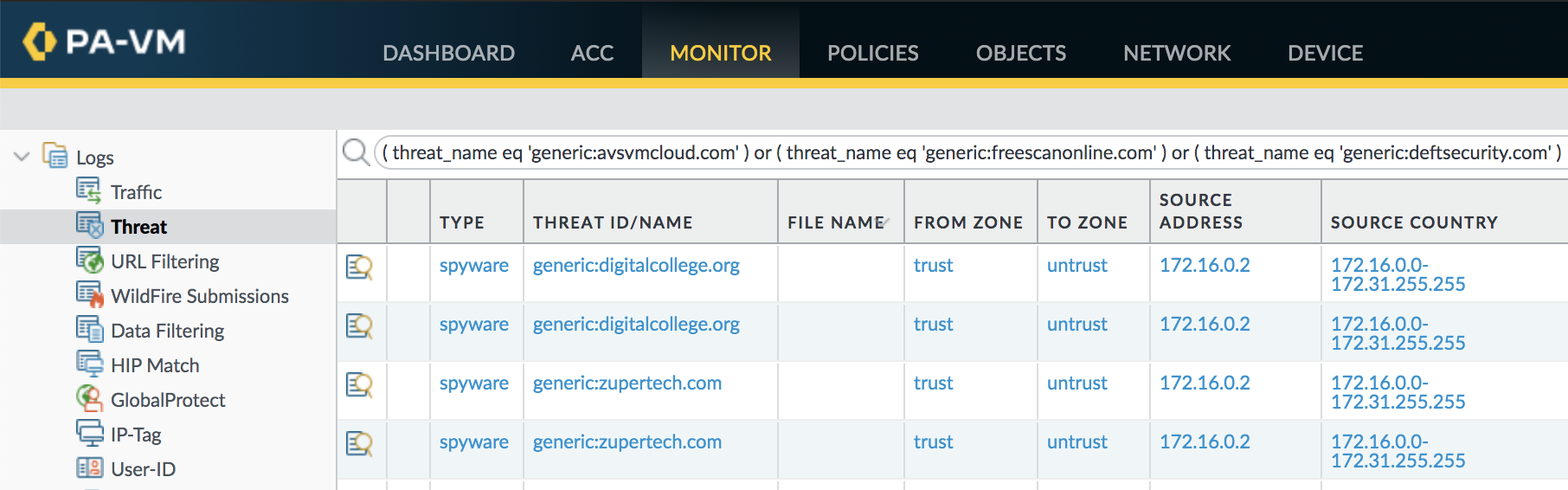
Threat logs can expose DNS queries that indicate SUNBURST command and control traffic. The following filter identifies known domain names used by the backdoor.
|
1 |
( threat_name eq 'generic:avsvmcloud.com' ) or ( threat_name eq 'generic:freescanonline.com' ) or ( threat_name eq 'generic:deftsecurity.com' ) or ( threat_name eq 'generic:thedoccloud.com' ) or ( threat_name eq 'generic:websitetheme.com' ) or ( threat_name eq 'generic:highdatabase.com') or ( threat_name eq 'generic:incomeupdate.com' ) or ( threat_name eq 'generic:databasegalore.com' ) or ( threat_name eq 'generic:panhardware.com' ) or ( threat_name eq 'generic:zupertech.com' ) or ( threat_name eq 'generic:virtualdataserver.com' ) or ( threat_name eq 'generic:digitalcollege.org' ) |
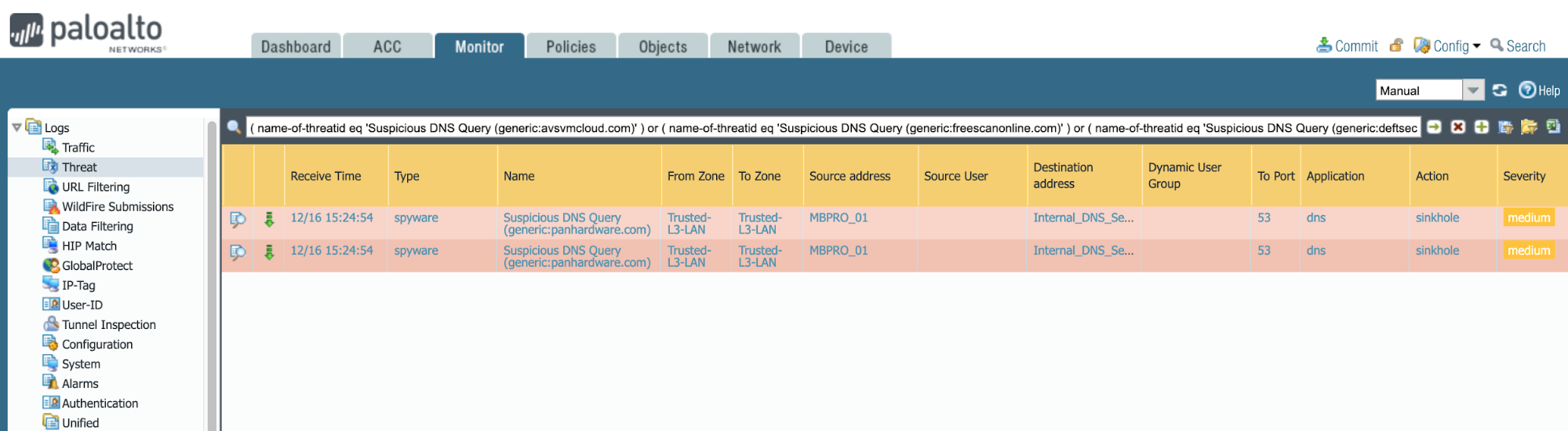
The following v9.x query can also be used to expose relative DNS queries:
|
1 |
( url eq 'Suspicious DNS Query (generic:avsvmcloud.com)' ) or ( url eq 'Suspicious DNS Query (generic:freescanonline.com)' ) or ( url eq 'Suspicious DNS Query (generic:deftsecurity.com)' ) or ( url eq 'Suspicious DNS Query (generic:thedoccloud.com)' ) or ( url eq 'Suspicious DNS Query (generic:websitetheme.com)' ) or ( url eq 'Suspicious DNS Query (generic:highdatabase.com)' ) or ( url eq 'Suspicious DNS Query (generic:incomeupdate.com)' ) or ( url eq 'Suspicious DNS Query (generic:databasegalore.com)' ) or ( url eq 'Suspicious DNS Query (generic:panhardware.com)' ) or ( url eq 'Suspicious DNS Query (generic:zupertech.com)' ) or ( url eq 'Suspicious DNS Query (generic:virtualdataserver.com)' ) or ( url eq 'Suspicious DNS Query (generic:digitalcollege.org)' ) or ( url eq 'Suspicious DNS Query (generic:solartrackingsystem.net)' ) or ( url eq 'Suspicious DNS Query (generic:webcodez.com)' ) or ( url eq 'Suspicious DNS Query (generic:seobundlekit.com)' ) or ( url eq 'Suspicious DNS Query (generic:virtualwebdata.com)' ) or ( url eq 'Suspicious DNS Query (generic:lcomputers.com)' ) or ( url eq 'Suspicious DNS Query (generic:mobilenweb.com)' ) or ( url eq 'Suspicious DNS Query (generic:kubecloud.com)' ) |
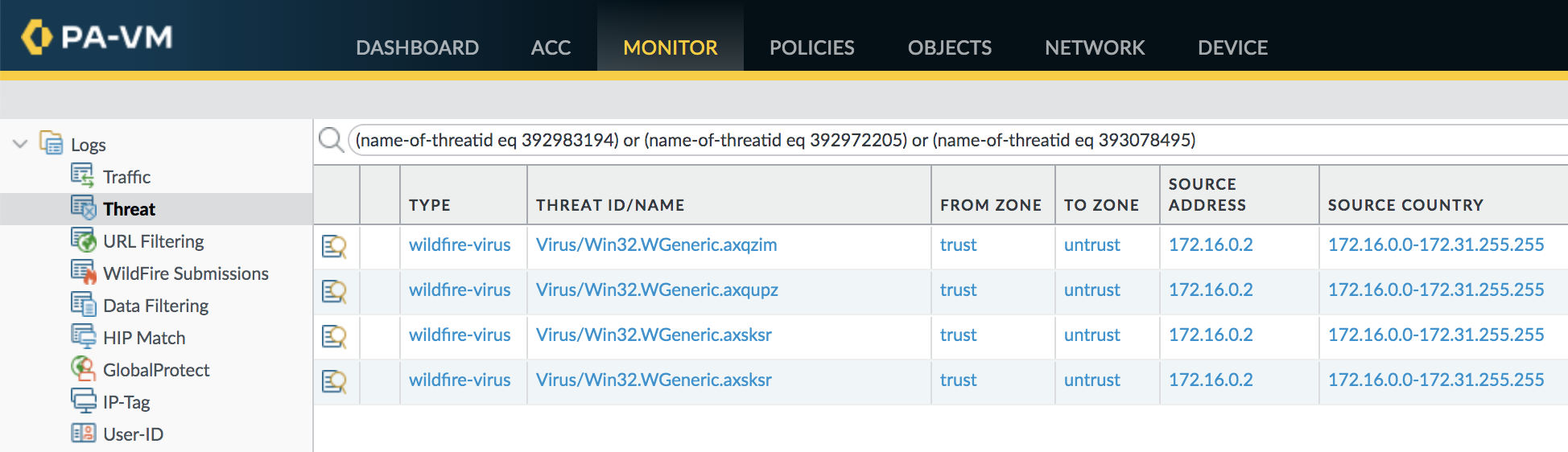
WildFire and Threat Prevention identify the known SUNBURST backdoor files. The following filter will identify the specific threats associated with SUNBURST in the Threat log.
|
1 |
(name-of-threatid eq 392983194) or (name-of-threatid eq 392972205) or (name-of-threatid eq 393078495) |
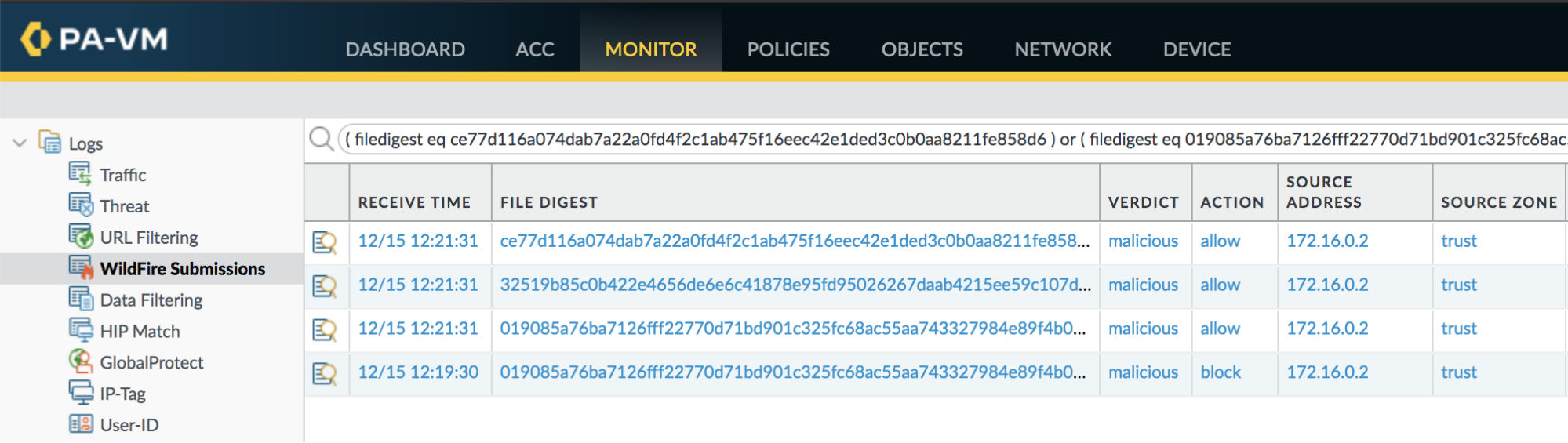
The following filter will identify known SUNBURST and TEARDROP files submitted to WildFire in the WildFire submissions log:
|
1 |
( filedigest eq ce77d116a074dab7a22a0fd4f2c1ab475f16eec42e1ded3c0b0aa8211fe858d6 ) or ( filedigest eq 019085a76ba7126fff22770d71bd901c325fc68ac55aa743327984e89f4b0134 ) or ( filedigest eq 32519b85c0b422e4656de6e6c41878e95fd95026267daab4215ee59c107d6c77 ) or ( filedigest eq 118189f90da3788362fe85eafa555298423e21ec37f147f3bf88c61d4cd46c51 ) |
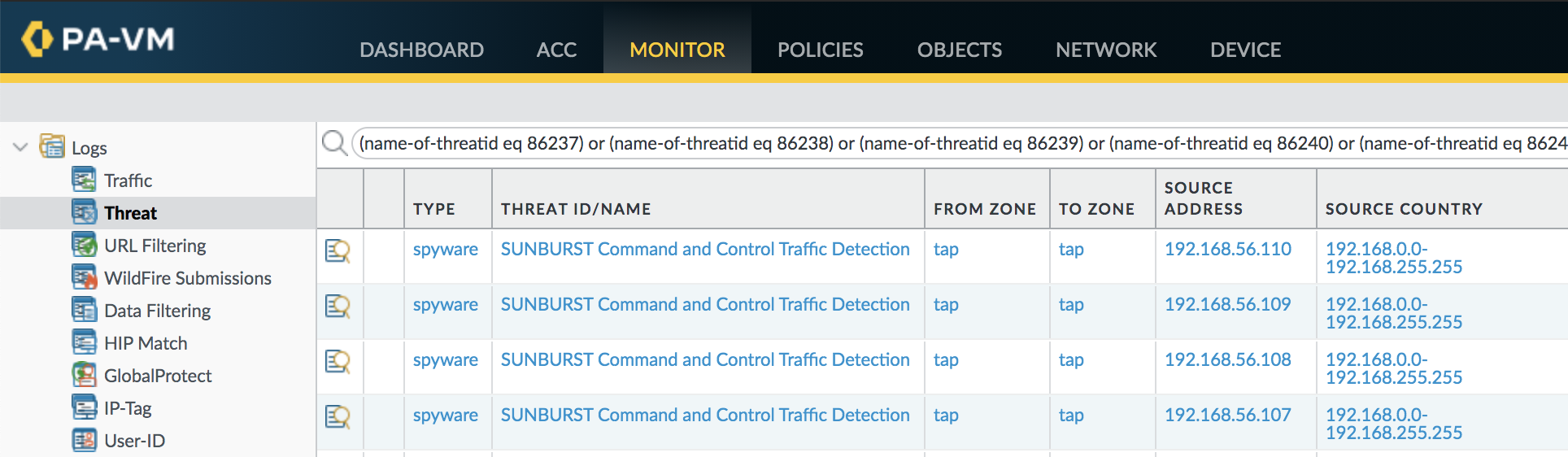
Threat Prevention can detect command and control traffic from SUNBURST as well as the Cobalt Strike Beacon used by SolarStorm. The following filter will identify this command and control traffic in the Threat log.
|
1 |
(name-of-threatid eq 86237) or (name-of-threatid eq 86238) or (name-of-threatid eq 86239) or (name-of-threatid eq 86240) or (name-of-threatid eq 86242) or (name-of-threatid eq 86243) or (name-of-threatid eq 86244) or (name-of-threatid eq 86245) or (name-of-threatid eq 86246) or (name-of-threatid eq 86247) or (name-of-threatid eq 86248) or (name-of-threatid eq 86249) or (name-of-threatid eq 86250) or (name-of-threatid eq 86251) |
Continue reading: SolarStorm Response With Cortex XDR and/or Cortex XSOAR












 Get updates from Unit 42
Get updates from Unit 42