In late October, we began examination of a VBA-initiated Infostealer campaign. This blog post follows up on additional information we gathered on related malware and associated actors.
Pivot On Initial Predator Pain Sample C2
In our previous post, we identified two Command and Control (C2) fully qualified domain names (FQDNs) for the initial Predator Pain sample analyzed: mail.rivardxteriaspte.co[.]uk and ftp.rivardxteriaspte.co[.]uk. We were interested in seeing whether any other malware samples had been observed communicating with these FQDNs and, if so, to which malware family they belonged.
Leveraging the Palo Alto Networks WildFire platform, we found an additional 14 samples that communicated with one or both of these C2 FQDNs between December 27, 2013, and August 1, 2014 (Table 1).
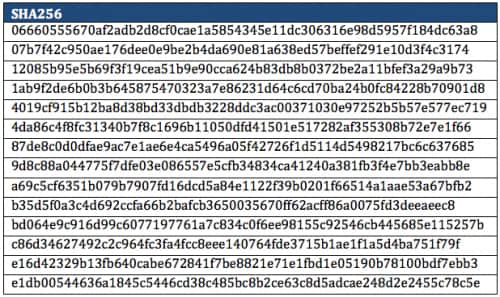
While anti-virus (AV) detections varied widely, all of these samples belong to the Predator Pain keylogger malware family. Additionally, a number of samples were also packaged with the Limitless keylogger, most likely for its exfiltration capabilities. Although Limitless is easily modified, one clear indication that it is employed is a default POST request over TCP/80 to the following URL:
www.limitlessproducts[.]org/Limitless/Login/submit_log.php
Both of these keylogger packages are available in the cybercrime underground for less than $40 USD, with cracked versions available for free (albeit with potentially unwanted “features”). The samples observed had the following capabilities (ordered by prevalence):
- Collection of system information
- Web browser password extraction
- E-mail password extraction
- Screenshot capture
- Logging of web browser activity
- Logging of e-mail activity
- Logging of chat activity
- Internet Download Manager password extraction
Figure 1 presents a malware-centric view of identified samples, categorized under the dominant malware family of Predator Pain.
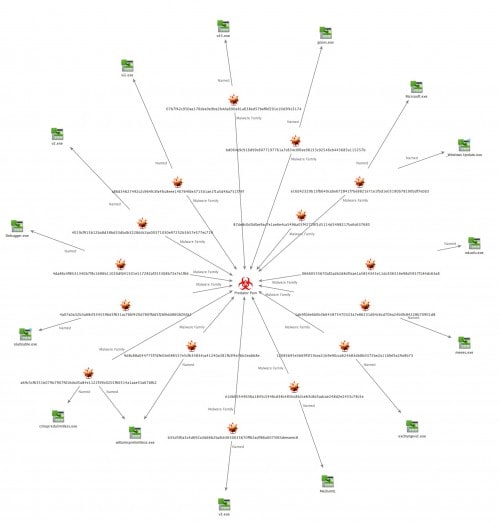
The newly identified samples were almost exclusively downloaded from one domain, nova.co[.]in, which resolved for some time to the same IP as the download domain for the initially analyzed Predator Pain sample, 209.160.24.197. Sometime between mid-March and the first of August, the nova.co[.]in IP resolution shifted to 209.160.26.174. The download domain view of those samples for which data was available can be found in Figure 2.
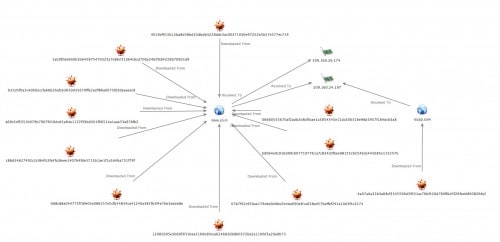
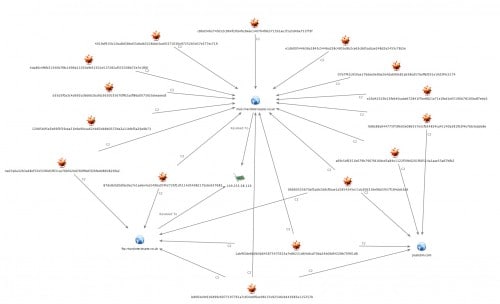
The broader set of malware also revealed five samples that reached out to Pastebin, as an additional C2-oriented request. Associated Pastebin pages were no longer active when checked in November 2014. Figure 3 depicts the C2 communications for samples.
Additional Actor Analysis
In our last post for this campaign, we attributed the focal Predator Pain sample to an actor that goes by the handle “Skozzy”. The profile for the related malware enumerated above further supports this attribution, given the shared C2 infrastructure and dominance of two malware packages favored by this actor.
In an attempt to gain further insight into this actor, we also performed a pivot on WHOIS registrant information for the initial Predator Pain sample’s C2 domain. This revealed a “Josh Frank” (sometimes “Josh Franks”, “Franks Josh” or “Josh Frank Kelvin”) persona, which in turn was confirmed as associated with both 419 and dating scams, under at least the following e-mail addresses:
- frankjosh61[at]yahoo.com
- frankjosh60[at]yahoo.com
- joshfrank615[at]yahoo.com (potential)
Additionally, this persona is known to register domains under two organizations, “Xteria pte” and “Amorex”, and has been observed using registrant contact information and/or social engineering references from Malaysia or the United Kingdom. Correlated domains lean towards financial (e.g., banking, brokerage) and dating themes, with registrar activity observed for associated domains as late as October 2014. A sampling of domains linked to this persona follows:
- maybnk2u-malaysia[.]net
- lexusmalaysia[.]com
- attaccq[.]com
- ahaldarazi[.]com
- tegbet[.]com
- acemovement[.]com
While it cannot be said with certainty that “Skozzy” and “Josh Frank” refer to the same individual, it is clear that there is a tie between the two in terms of motivations and objectives: financial gain through personal and/or business fraud.
Expanding on Actor Motivations and Objectives
As noted in the previous blog post on this topic, “roles across nation state, cybercrime, hacktivist and ankle-biter/script kiddies are not mutually exclusive and – in fact – continue to become fuzzier over time.” Actors using tools such as Predator Pain and Limitless have a myriad of options at their disposal for information collection. This extends into an equally broad range of potential malicious uses for that information. It also further blurs the lines between malicious actor categories, translating into increased challenges in characterization/qualification and attribution for cyber attacks.
Opportunism further extends within each of these malicious actor categories – especially with greater availability and a lower cost of entry for increasingly sophisticated and effective tools. One example is the shift by some cybercrime actors away from information theft from individuals and instead scaling up towards higher-yield attacks against companies and organizations. Clever application of insider, sensitive information gleaned from such tools can serve as a multiplier to the perceived legitimacy and potential impact of more precise second-stage social engineering and/or malware attacks.
With the demonstrated success of such tools and techniques to date, we anticipate continued growth in the number of these types of attacks in the future. The Palo Alto Networks Enterprise Security Platform can prevent, address and minimize the risk of these and other associated threats. Learn more about the platform here.











 Get updates from Unit 42
Get updates from Unit 42