Executive Summary
Since the creation of the internet, email attacks have been the predominant attack vector for spreading malware and gaining initial access to systems and endpoints. One example of an effective email compromise technique is a homograph attack. Attackers use this content manipulation tactic to evade content analysis and trick users by replacing Latin characters with similar-looking characters from other Unicode blocks.
This article provides rare insights into real homograph attacks, and demonstrates the full chain of events that can potentially lead to exploitation of targets. We outline three cases that we detected in the wild. In each scenario, threat actors used homograph attacks in different contexts within email messages, to avoid natural language detections and reach target inboxes.
Attackers can make homograph manipulations to domain names or within an email’s content and headers, as part of a larger attack scheme that aims to establish initial access to a target. The presence of homographs in multiple fields within an email can make it appear more legitimate, while evading analysis and alerts on these fields.
To get their message across, threat actors craft email content that appears to be legitimate. This increases the likelihood that targets will interact with malicious content. As the success of this attack relies almost completely on the recipient’s impression of and interaction with the message, it is important to intercept and prevent such communication from reaching potential victims.
Palo Alto Networks customers are better protected from homograph attacks by Palo Alto Networks Cortex Advanced Email Security, which analyzes email content, headers and communication patterns. This can be combined with Cortex XSOAR, which quarantines and removes mails for all recipients, blocks malicious and compromised senders, and disables affected user accounts.
The Attack Surface Management add-on for Cortex XSIAM also includes new Digital Risk Protection, which has the ability to detect potentially risky services, including those that use homographs.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | Phishing |
What is a Homograph Attack?
To the human eye, the title of this article seems completely normal. But in fact, the word Ηоmоgraph in the title is not exactly the same as the word Homograph.
The differences are small, and hard to recognize. Ηоmоgraph actually includes several letters that are not Latin characters. In this case we’ve substituted the letter H with the Greek homoglyph Η and the letter o with the Cyrillic homoglyph о. Automated defenses that analyze the word will not recognize it as the word it appears to be and therefore might consider it to be valid or skip the manipulated word during analysis.
A homograph attack incorporates non-Latin characters that visually resemble Latin characters to create words. These words might look the same as their genuine counterparts to the human eye, but to a large language model (LLM) — or any computer system — they are actually different.
This attack essentially exploits the appearance of characters from different scripts — such as Cyrillic, Greek and others — that resemble the standard Latin characters that English speakers generally use when working on a computer.
A malicious actor who replaces Latin characters with lookalike non-Latin characters could evade detection and analysis, crafting malicious emails that can lead to credential theft, malware infection or other forms of exploitation. For example, substituting the Latin letter a with the Cyrillic а in the fictional brand “Airplаnes R Us” can make a fraudulent email from an attacker seem like a completely authentic email from Airplanes R Us to the human eye.
The rise of AI-driven phishing makes this an even more dangerous vector. AI can be used to generate highly convincing emails, making it easier for threat actors to create legitimate-looking emails en masse and harder to distinguish real and malicious emails from each other.
Threat actors usually incorporate homograph attacks into a larger attack scheme to lure targets to engage with malicious content. By manipulating various fields within the email using homograph characters, threat actors aim to:
- Deceive users: Visual similarities can trick recipients into trusting fraudulent emails.
- Bypass security filters: Conventional security solutions might not detect these character substitutions and would categorize the emails as legitimate.
- Impersonate trusted entities: Accurate mimicry of brands and roles increases the likelihood of recipient engagement.
Theory of Detection
While manipulated words may appear to be identical (or very similar) to the human eye, homograph characters can be detected by examining their Unicode values. The Unicode standard assigns a unique numerical value to each character, allowing computers to represent text from different languages and character scripts.
Each character set (e.g., Latin, Cyrillic, Greek) is assigned a specific range of numerical values. The Unicode organization's website provides a comprehensive list of these character sets and their corresponding values.
Each character set is assigned a specific range of Unicode values, with each value corresponding to a character (e.g., letter, number, symbol) within that script. Analyzing the characters’ values reveals which script it actually belongs to, enabling the detection of characters from other scripts that are hiding among characters from another script.
Observations of Homograph Technique Used in Phishing Attacks
Our analysis of email messages containing homograph attacks highlights key techniques including:
- Well-known brand impersonation
- Impersonation of services (e.g., document-sharing platforms, IT personnel)
Attackers manipulate characters in the display names of emails to resemble legitimate entities to make it challenging for recipients to detect fraudulent messages. These messages are likely to include homograph characters in other headers as well, to make the emails pass as legitimate.
The following case studies, which we have seen in the wild, demonstrate using homographs in different email headers and fields, emphasizing the threat. These case studies relate to different email homograph attack scenarios that follow similar patterns.
Case Study 1: File Sharing on Google Drive
In this attack scenario, attackers shared a file on Google Drive. They used an email account that had a display name and Google account logo mimicking those of a well-known, multi-national American company that offers financial services such as online banking.
The email address itself had nothing to do with the impersonated company, but the account name included homograph characters to imitate the appearance of the company’s name. We have obfuscated this information to protect the privacy of the impersonated organization.
Built-in security filters failed to detect this as an impersonation attempt or to categorize the content as malicious. Figure 1 shows a redacted version of the email.
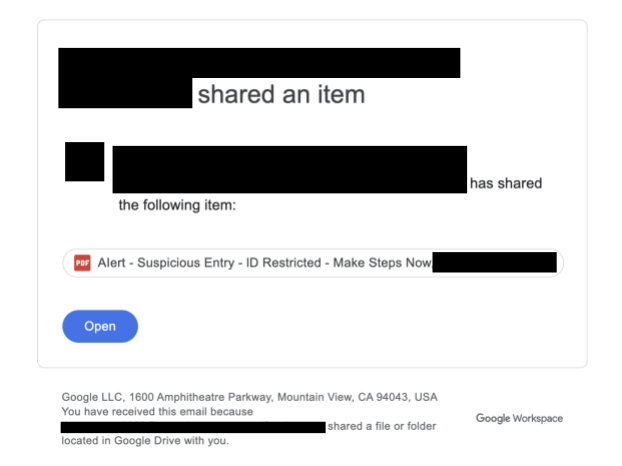
The attackers shared documents that discussed “suspicious entries” to the target’s account, suggesting they take action by clicking the VERIFY button provided in the file, as Figure 2 shows.

Although the website (messageconnection.blob.core[.]windows[.]net) was not operational at the time of our investigation, it’s likely the attacker would have used it to steal credentials, or potentially even to exploit the workstation of a target that accessed it.
Case Study 2: Links to Documents for Review and E-Signing
In another attack scenario that we investigated, threat actors used homograph substitutes to impersonate e-document sharing platforms. These platforms are used to electronically sign contracts, agreements and other documentation.
In this case, the attackers shared links, supposedly to documents ready for signing. This document prompted potential victims to click a link that redirected them to an attacker-controlled website. Although the attacker sent the mail from an address unrelated to any legitimate platform, both the display name and the subject of this email contained words with non-Latin homograph characters (marked in bold):
- Display name: Included the words Сonfidеntiаl and Ꭲiꮯkеt
- Subject: Included the words Finаnꮯiаl and Տtаtеmеnt
While it might be easier to spot these irregularities in this case, some programs render such characters to look like Latin letters, making it harder to distinguish them from Latin characters.
The subject also included a homograph manipulation of the target’s company name meant to create an impression that this email originated from the target’s company. As a result, the malicious email evaded detection and filters. Ultimately, the mail platform categorized the message as a valid email that reached the target’s inbox.
Attackers crafted the various buttons and URLs in the email and interfaces to lead the target to a fake login page. They customized the URL of the login page to the target’s organization and added a custom-made CAPTCHA to filter out bots and crawlers.
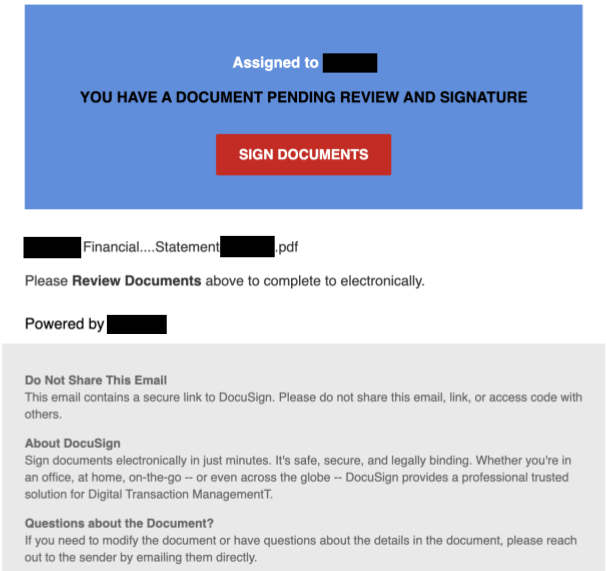
In this specific example, the target’s name appeared in the “Assigned to” section, making the email look like it was crafted specifically for that person. The email content itself displayed the company name in the PDF filename and in the “Powered by” section. The threat actor also added DocuSign branding and information to the content of the mail.
All of these aspects of the email strengthened the impression that an employee of the target’s company sent this communication through a genuine document sharing service. Figure 3 shows the email that was disguised to look like a message from DocuSign.
Clicking the SIGN DOCUMENTS button in the email shown above redirects the victim to a website that looks legitimate, and is even hosted by a legitimate .com top-level domain (TLD): bestseoservices[.]com. Figure 4 shows the interface message, which prompts the victim to click another button to verify their identity. This additional step is potentially intended to prevent crawlers from interacting with the site and detecting its malicious nature.

Clicking the “Verify it's you” button initiates a series of redirects designed to further lull the target into a false sense of security. First, the victim is redirected to the /templates directory of a legitimate website belonging to a municipality in the Middle East. This likely serves to mask the malicious intent of the attack.
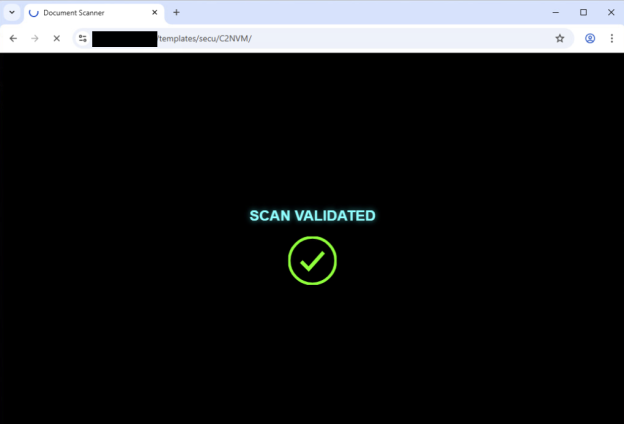
The website displays a message stating that it is performing an identity scan. Figure 5 shows that the screen then presents a SCAN VALIDATED message, further reinforcing the illusion of legitimacy. Finally, after this elaborate charade, the target is redirected to a domain under the .ru TLD (kig.skyvaulyt[.]ru), which was not active at the time of our investigation.
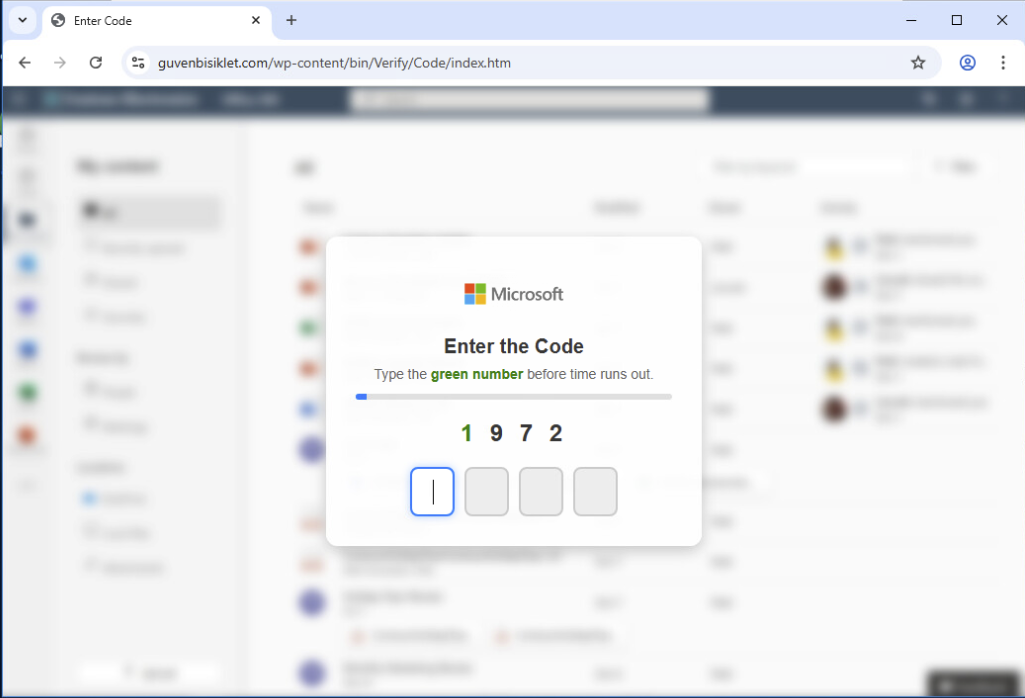
In a separate email, threat actors used a similar method in the initial attack stages. In this case, after clicking a button from a different document sharing email, the victim is redirected to the page shown in Figure 6. The attacker designed this page to filter out bots and crawlers by forcing the victim to insert a one-time password (OTP) that changes every time they type a green number, as shown in Figures 6 and 7.
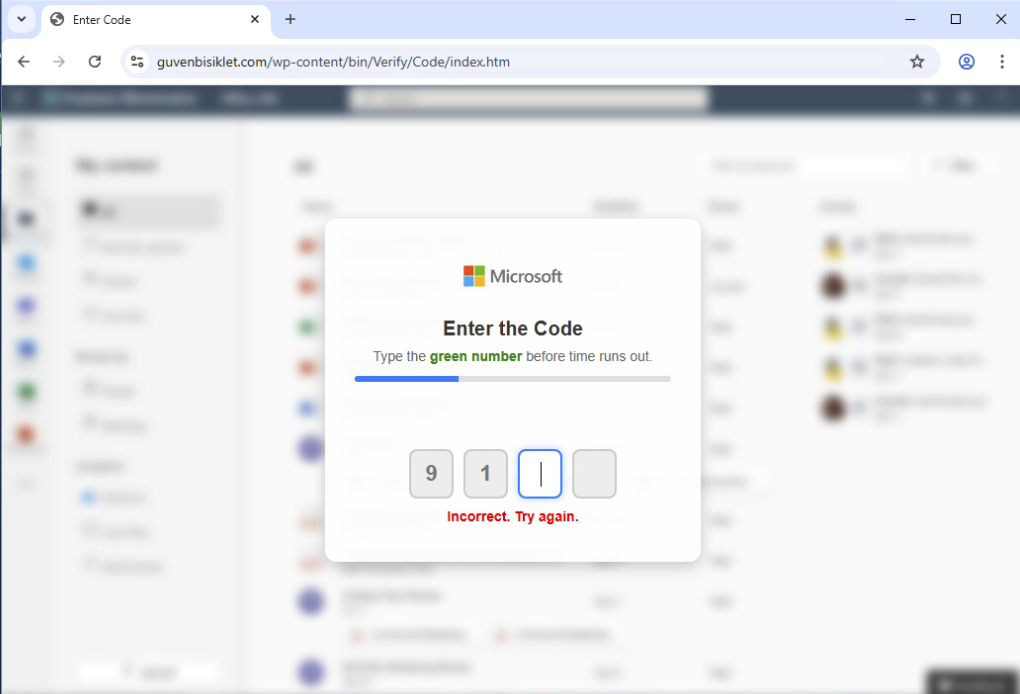
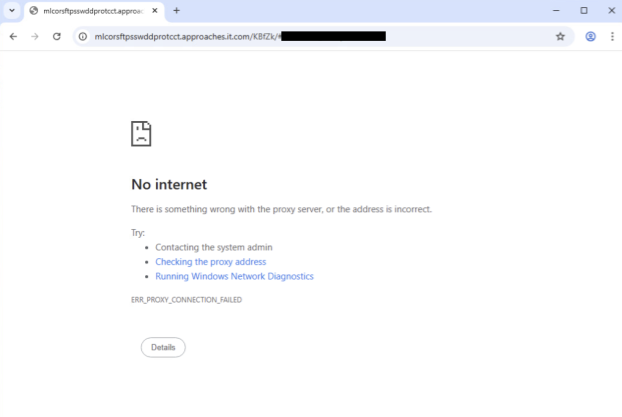
After inserting the OTP code successfully, a page that mimics a Microsoft domain is presented: mlcorsftpsswddprotcct.approaches.it[.]com. The obfuscated URL parameters shown in Figure 8 display the target mailbox.
We suspect that the threat actors customized the site to be accessible only to targeted users, effectively filtering out other access attempts. This website was not active at the time of our investigation.
Case Study 3: Spotify Impersonation Attempt
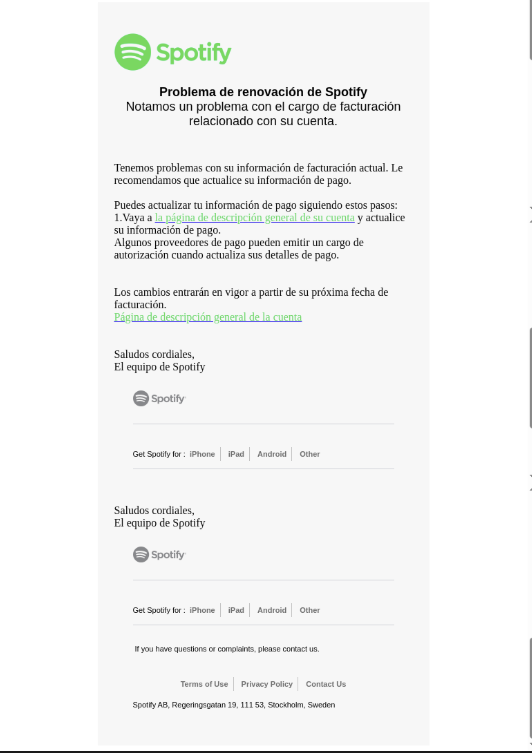
The third case that we investigated involved an impersonation of Spotify — a streaming music and podcast provider. An attacker sent an email purporting to be from Sρօtifу, using a sender address that contained non-Latin homograph characters, making it difficult to visually distinguish from a legitimate Spotify email.
Figure 9 shows the email, which stated that the recipient’s Spotify payment had not gone through and that they must update their payment details in the provided link. This link redirected the target to the legitimate redirects[.]ca URL shortening service, likely to mask the final destination and evade detection. We assume this shortened link would have led to an attacker-controlled website that the attackers could have used for credential theft or other malicious purposes.
By the time we investigated this scenario, the link was not active.
These case studies clearly demonstrate threat actors crafting highly targeted and convincing emails that are difficult to distinguish from legitimate communications. Without robust detection and prevention mechanisms, organizations and individuals are vulnerable to these attacks and will struggle to discern that these are malicious links and action buttons embedded in these emails.
Conclusion
The increased adoption of new AI models enables attackers to create more convincing and personalized emails. This makes it easier to deceive recipients into engaging with malicious content and harder to distinguish authentic content from fraudulent. Homograph attacks present an additional challenge to common detection methods, as standard defense mechanisms do not recognize or automatically inspect manipulated text.
An email security module that checks for the presence of words that should trigger alerts will not recognize the words pаssword, սrgent and ActᎥoո reɋuired as being problematic, because they contain homographs. As such, the module might not detect or prevent communication and sites that attackers crafted for malicious purposes. This could result in manipulated input being processed in unexpected ways.
People across the globe use computing technology in a variety of languages. It can be difficult to differentiate between potentially malicious emails and those that make reasonable and justifiable use of non-Latin characters. Even when email messages appear legitimate, there are still important factors to consider before categorizing such communication as safe:
- Check the address of the sender: Is it related to the display name or the mail’s content? For example, does the domain name match the company being impersonated? Does it look like the usual domains that are associated with this company?
- Is this address well known in your organization? Or is it a first-time sender? Be wary of emails from unknown senders, especially if they are asking for sensitive information or directing you to external links or attachments.
- Examine the content of the mail: Do some letters look a bit off? They might actually not be Latin characters. You can use a character inspection tool to check the Unicode values of suspicious characters.
- Never engage with attachments or URLs sent by unknown addresses, or that lead to addresses that seem different from the ones you are familiar with. They could be harmful. Always verify the legitimacy of links before clicking on them.
As with all email-related attacks, two of the keys to prevention are awareness and training. Treat every email that reaches your inbox with caution and follow the suggestions above whenever you encounter a suspicious email. An email with a legitimate appearance doesn’t necessarily mean that it is actually legitimate.
Palo Alto Networks Product Protections for Homograph Attacks
Palo Alto Networks Cortex Advanced Email Security is designed to help protect against modern email-based threats, featuring comprehensive detection and defense methods, including against homograph attacks. The module performs deep email analysis of email metadata, content and behavioral patterns to identify malicious intents and sophisticated impersonation attempts — even those that AI generates. Emails and alerts are assigned risk scores based on this analysis, which helps analysts reduce alert fatigue by prioritizing events with higher risk levels.
This module can be combined with Cortex XSOAR, which quarantines and removes mails for all recipients, blocks malicious and compromised senders, and disables affected user accounts.
The Attack Surface Management add-on for Cortex XSIAM also includes new Digital Risk Protection capabilities which have the ability to detect potentially risky services using permutations of customer domains, such as homographs.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
Email addresses that shared files on Google Drive:
- tioranpycon1999@attention.processverification[.]com
- perlapersdoc1998@supportmanager.fullrecoveryaccount[.]agency
Case study 1 URLs:
- messageconnection.blob.core[.]windows[.]net
Email addresses that sent the document-sharing emails:
- cfa@agroparistechl[.]fr
- brantlawassoc@bellnet[.]ca
Case study 2 URLs:
- bestseoservices[.]com
- kig[.]skyvaulyt[.]ru
- hxxps://guvenbisiklet[.]com/wp-content/bin/Verify/Code/index.htm(?/1.AYWNjb3VudHNAY29vbHBvb2xsdGQuY29t)
- microsftpsswddprotcct.approaches.it[.]com
Email address that sent the Spotify email:
- info47198@ha01s003[.]org-dns[.]com
Note: This article makes plentiful use of special characters. Depending on the languages supported on your individual device, a PDF version of this article may not contain all the characters used.












 Get updates from Unit 42
Get updates from Unit 42