At 06:47 PST on May 20 Palo Alto Networks WildFire detected the start of the latest Kuluoz spam campaign. The total number of e-mails detected quickly rose to over 30,000 per hour around noon PST and had not begun to slow down as of 1:30PM PST.
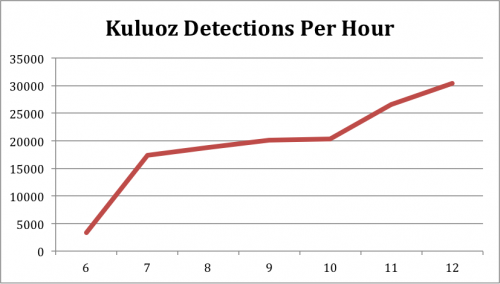
Kuluoz is a descendant of the Asprox malware and spreads by sending copies of itself as an e-mail attachment. As the malware infects more systems, the systems begin sending more e-mails which leads to more infections. Kuluoz makes money for its owner by installing other malware, such as crimeware or fake antivirus programs.
Kuluoz e-mails often trick the reader into thinking they are delivery notifications (such as UPS or Fedex), or notices from airlines or payment processors. In this case the e-mails claim to contain a document about a court case.
Subject: Hearing of your case in Court
From: Notice of Appearance
Pretrial Notice,
Please, download the copy of the court notice attached herewith to read the details.
Note: The case may be heard by the judge in your absence if you do not come.
Truly yours,
Clerk to the Court.
Olivia Smith
Each e-mail carries one of the following attachments:
- Court_Notice_May-20_Date_IN-FN_2014.exe
- Court_Notice_May-20_Date_EN-RM_2014.exe
- DC_Court_Notice_ER_NSER[4 Random Numbers].zip
These attachments are different versions of the malware that has been packed to evade antivirus engines. Twelve of the 53 scanners on virustotal.com now detect the first variant of the malware, but only three detect the latest version.
To determine where the highest number of infected nodes are, we mapped the sending IP address for each of the attach e-mails to their rough geographic location. While there are infected systems around the world, the largest concentration is in North America, particularly the United Stats and Canada.
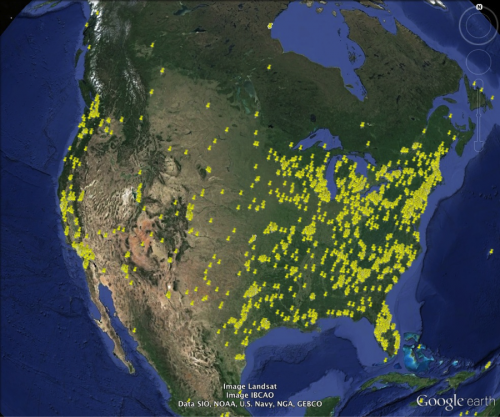
Geographic Distribution of Koluoz Spam Nodes in North America
Thus far we’ve detected the following command and control servers in use.
- 192.69.192. 178:443
- 59.106.185. 11:443
- 173.203.113. 94:443
- 69.60.8. 88:8080
- 205.186.156. 218:8080
The network traffic generated by each Trojan uses the HTTP protocol, and despite its use of port 443, is not encrypted with SSL.
As with most fast-spreading malware, antivirus engines will typically begin detecting the files a day or two after the spread has begun. While we haven’t seen any indication that the spam volume has begun to slow down, we do expect the campaign to wind down in the next 24 hours, but a new campaign will probably be close behind. WildFire users can rest assured that they’ll be protected from whatever Kuluoz has in-store next.











 Get updates from Unit 42
Get updates from Unit 42