Introduction
CTB-Locker is a well-known ransomware Trojan used by crimeware groups to encrypt files on the victim's endpoints and demand ransom payment to decrypt the files back to their original state, but most antiviruses detect it by mistake as CryptoLocker (only one vendor correctly detects it as CTB-Locker). The attack vector is very basic and repeats itself: It begins with a spear phishing email sent with SCR attachments (double zipped). Once executed by the user the first stage malware downloads and executes the ransomware from a fixed hardcoded server list.
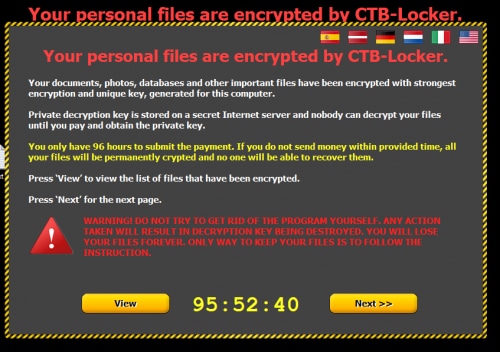
The Origins
The first known campaign was launched by Crimeware on November 2014. The first stage downloaded the ransomware from these sites:
- pubbliemme.com (5.134.122.150)
- agatecom.fr (213.186.33.19)
- n23.fr (213.186.33.4)
- baselineproduction.fr (213.186.33.4)
The Attack: A Legacy Nightmare
A very serious campaign was launched between January 19, 2015 and January 20, 2015, and Palo Alto Networks Enterprise Security Platform has discovered more than 1000 unique attacks since. The attacker used a polymorphic malware builder to generate malware with a unique hash for each victim, preventing signature-based solutions from detecting the new attacks before it was too late for the victim. This tactic is a nightmare for legacy security products that are based on legacy techniques such as bytes signatures, since they can only detect attacks after the damage is done instead of preventing it as a true solution should. Palo Alto Networks Enterprise Security Platform offers multilayer protection to prevent this attack along with other attacks without the need for prior knowledge of the specific attack.
Some IOCs and statistics
- breteau-photographe.com (213.186.33.150)
- voigt-its.de (188.93.8.7)
- maisondessources.com (213.186.33.19)
- jbmsystem.fr (213.186.33.3)
- pleiade.asso.fr (213.186.33.19)
- scolapedia.org (213.186.33.19)
We can see here that server hostnames were changed but they didn’t change the server IP address – see the attached file with results for files from last week’s campaign from VirusTotal. Most legacy security programs could not detect this malware at the time it was posted. If you re-test these hashes again from last week you can see an average of 49/57 engines that detect last week’s threat – but that’s too little, too late for anyone who already lost data.
The new (currently ongoing) campaign
This campaign started earlier today, and the malware uses the same techniques and even the same IOCs:
- same mutex name: wuqntwklyxwhac
- same job name: cderkbm.job
And only added two new hostnames:
- joefel.com (64.71.33.177)
- m-a-metare.fr (213.186.33.4) – same IP as before.
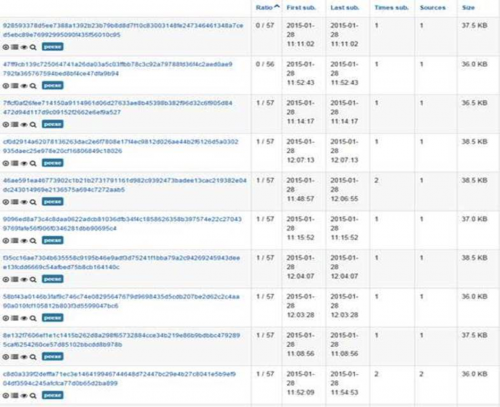
By now you shouldn’t be surprised that one of them is on the same known malicious IP address. We found 147 new unique pieces of malware today alone, two of them fully undetectable by the legacy security solutions in VirusTotal and most of them barely detected by one vendor (few have 4/57 detection rate).
See below:
So basically you have two choices:
- Update hashes every week and pray … (see hash list section, we’re happy to help those still trapped using legacy solutions)
- Implement next generation security products that can actually prevent this from happening.
IOCs for the latest campaign
The most surprising fact about this campaign is that almost all the IOCs haven’t been changed:
- Same mutex name: wuqntwklyxwhac
- Same job name: cderkbm.job .
- New IOC: additional mutex name - 87281673
For those still using legacy solutions we’ve attached two lists of SHA256 hashes in a text file format for reference. One list shows the new campaign, which continues to progress. The other list is of last week’s campaign by the same attackers (exhaustive or close to it).
Conclusion
Palo Alto Networks Enterprise Security Platform would have stopped this ransomware attack campaign thanks to the platform’s unique integration between the network, endpoint and the cloud to maximize security. Attacks aren't getting any less sophisticated, so it is time to leave legacy security solutions behind and upgrade to real, prevention-based security.












 Get updates from Unit 42
Get updates from Unit 42