This post is also available in: 日本語 (Japanese)
Executive Summary
With more and more companies choosing to allow for flexible (hybrid/remote) work environments post-pandemic, we investigated the unique cyberthreats employees working from home face.
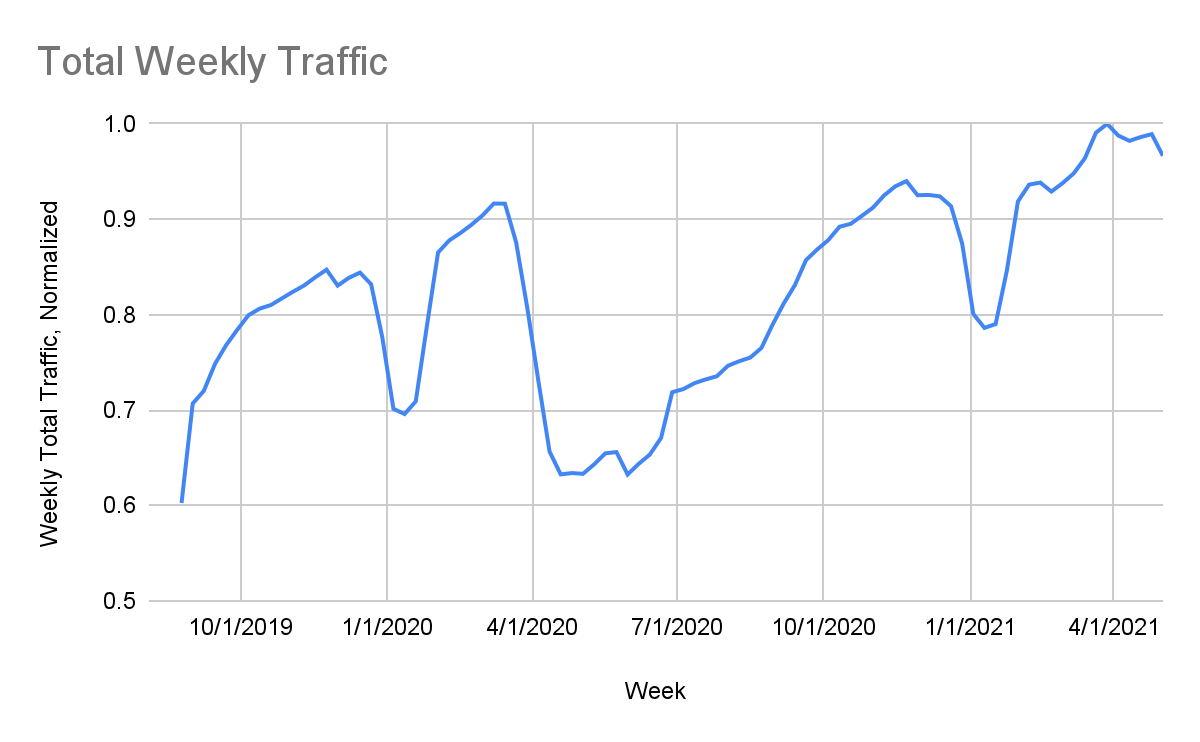
Our analysis focused primarily on trends in our firewall traffic and phishing pages detected by our URL Filtering service from September 2019 to April 2021. We found that in early 2020, when employees were making the shift to working from home, there was a significant drop in traffic coming through our URL Filtering service, coinciding with a significant increase in the number of new phishing pages per week. This suggests that at the peak of remote work, right when the smallest percentage of end-user traffic was being protected by corporate firewalls, threat actors were putting out more phishing attacks than ever.
By comparing the rate of phishing traffic coming from our on-prem firewalls versus our cloud-delivered security platform, Prisma Access, we discovered that remote employees might be especially vulnerable to a wide variety of phishing attacks. Specifically, we saw that the percentage of traffic coming from phishing pages was more than 2.4 times greater in Prisma Access traffic than in on-prem firewall traffic. This emphasizes the need to have the proper defenses in place for employees who are either fully remote or working from home.
With phishing attacks continuing to rise globally, it’s more important now than ever that all employees are able to safely and securely browse the web, regardless of whether they are working in the office or from home. Tools like Prisma Access and GlobalProtect can help shield remote and/or hybrid employees from these cyberthreats by ensuring that they have access to the same security services afforded by Palo Alto Networks Next-Generation Firewalls.
Firewall Traffic Trends
We began our analysis by investigating trends in our URL Filtering traffic from before the pandemic, starting in September 2019. We observed a sudden and significant drop in traffic from March-April 2020, just as COVID was beginning its initial spread throughout the U.S., forcing organizations to shift to remote work.
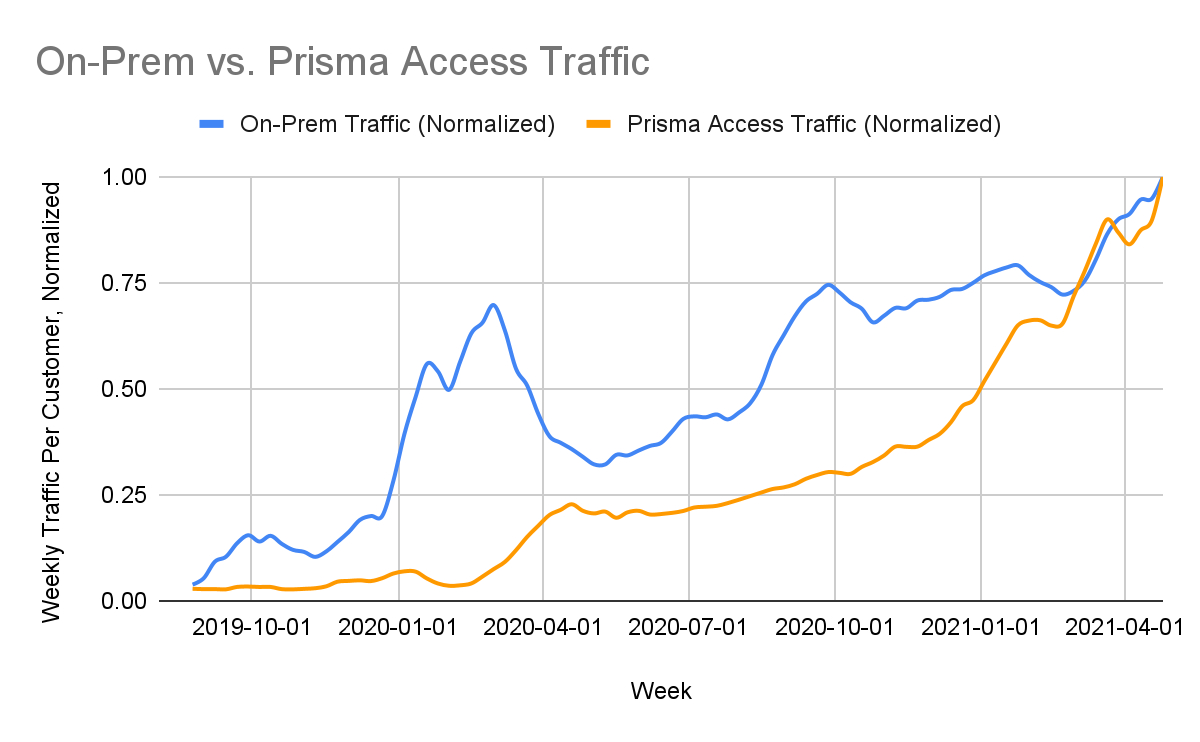
We then investigated how changes in customer traffic differed between our on-prem Next-Generation Firewalls and our cloud-delivered security platform, Prisma Access. We saw that weekly traffic from our on-prem firewalls (blue in Figure 2 below) dropped quite significantly – by about 45% – from March-April 2020. In contrast, weekly traffic from Prisma Access (orange in Figure 2) increased by more than 200% as employees suddenly shifted to working remotely. (The dips in December 2020 and December 2021 correspond to holiday breaks.)
This suggests that organizations relying solely on on-prem firewalls, without adjusting to increased remote work by deploying cloud-delivered security services, were far more vulnerable to a variety of cyberattacks since their now-remote employees were able to browse the web unprotected.
To further investigate this point, we looked into which industries experienced the greatest drops in total URL Filtering traffic from March-April 2020. We noticed that the education and high tech industries experienced especially large decreases in traffic during this period: education (~46% decrease), presumably due to school closures, and high tech (~35% decrease), presumably due to employers’ willingness to let employees work remotely given the industry’s inherently digital nature. All in all, nearly every industry we studied experienced a significant drop in URL Filtering traffic of roughly 30% or more during this time.
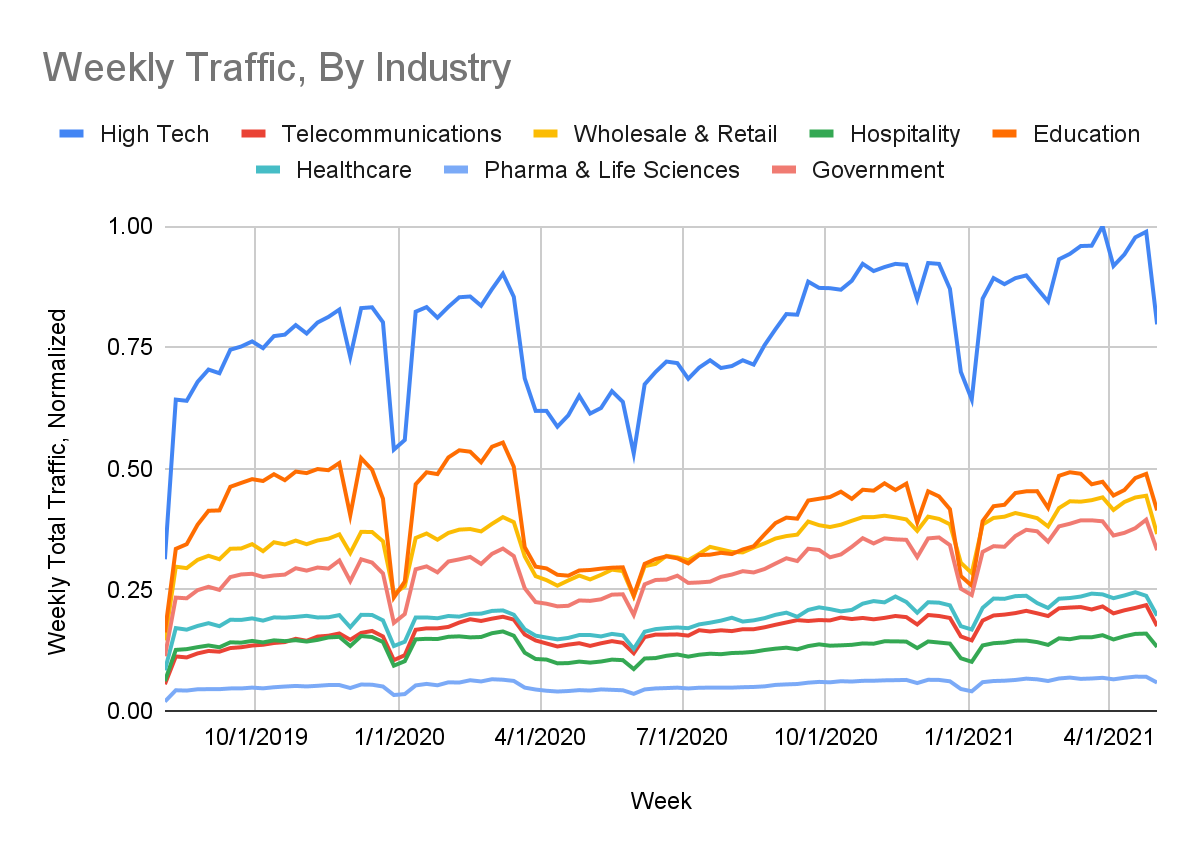
These significant drops in observed URL Filtering traffic stress the importance of having access to security services regardless of where your employees or end users are physically located. Although our observed URL Filtering traffic dropped at the start of the pandemic, internet usage as a whole went up by ~25% in mid-March, according to the Wall Street Journal. (Total internet usage then dipped slightly in May, but still stayed higher than pre-pandemic levels). This suggests that despite the drop in traffic, people were not necessarily using the internet any less than before. Rather, people were on average using the internet even more than before, with a larger proportion of that internet traffic being unprotected by enterprise-grade firewalls, leaving end users more vulnerable than ever to a wide variety of cyberthreats.
Since the hybrid work model is likely here to stay post-pandemic (according to The Work Trend Index, a report published by Microsoft, over 70 percent of employees across a variety of industries want flexible remote work options to continue), organizations must rethink how to protect their workforces moving forward, which starts by making digital security an integral part of their hybrid and/or remote work plans.
Phishing-Related Trends
To study how attackers may have responded to this increase in remote work, we investigated the number of phishing URLs detected by our ML-powered URL Filtering service from September 2019-April 2021.
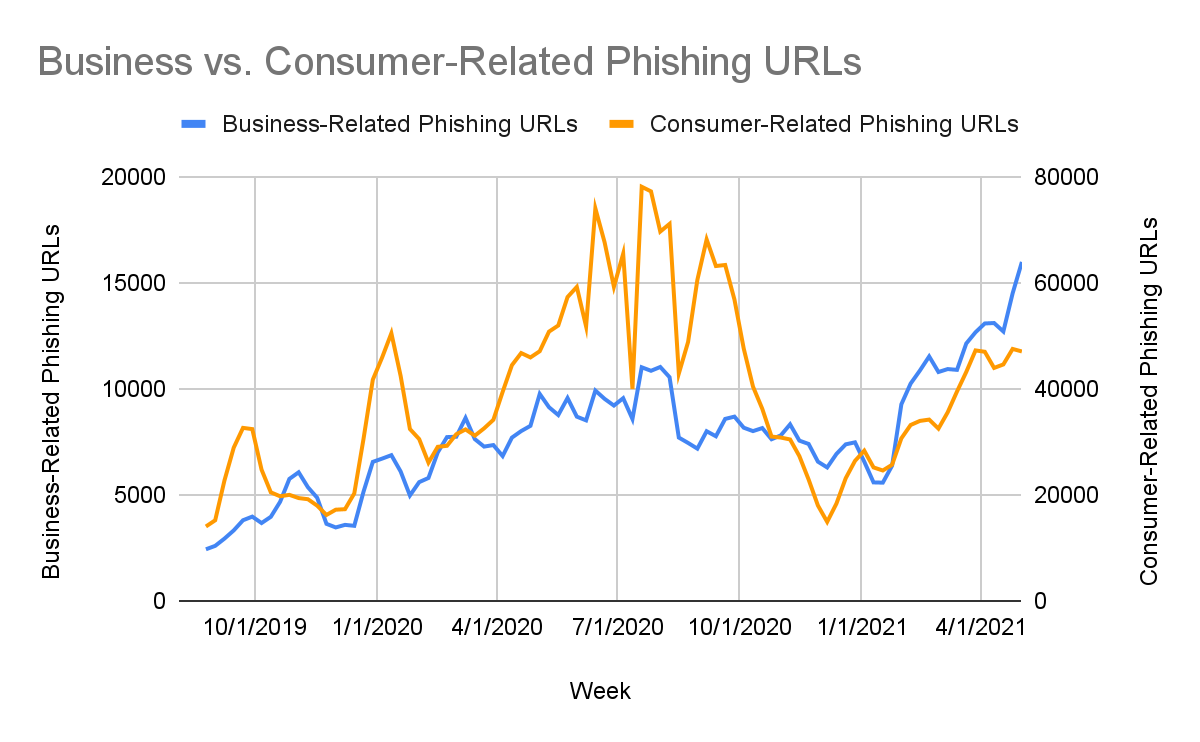
We observed an initial upward trend in new phishing URLs starting around February 2020, peaking around June 2020. Looking at Figure 4, we can see that the largest number of new phishing pages (orange) was observed just as URL Filtering traffic (blue) was at its lowest point (May-June 2020). This suggests that the high prevalence of remote work at this time coincided with a high rate of attempted phishing attacks.
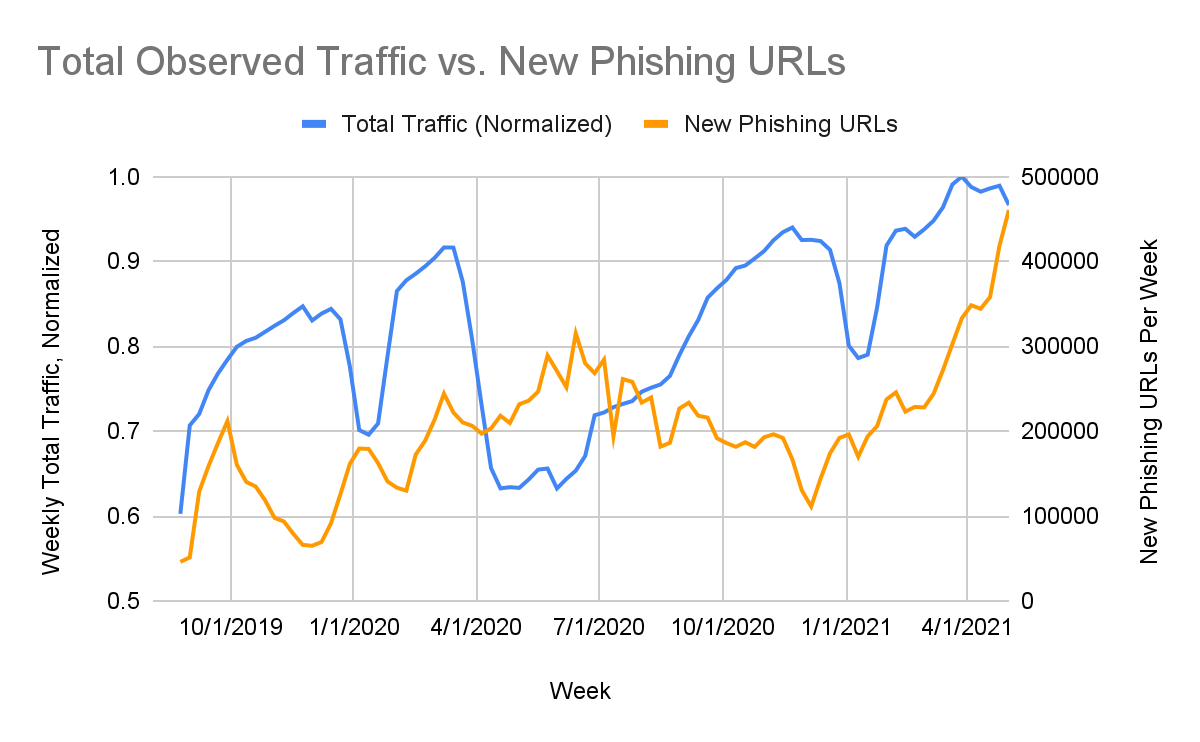
Next, we used keyword matching to determine which URLs were business-related (targeting various business communication and/or collaboration tools) and which phishing URLs were consumer-related (targeting well-known social media brands, consumer banking sites, etc.). We found that business-related and consumer-related phishing attacks increased by roughly 100% from February 2020 to June 2020. This suggests that the types of phishing attacks responsible for the spike during this time period did not necessarily change – but rather, the total volume of attempted phishing attacks increased across the board.
In addition, we can see from the upward trend toward the right side of Figures 4 and 5 that the rate of new phishing attacks shows no signs of slowing down anytime soon.
![office365invoicea[.]xyz/ce: A typical example of a business phishing attack targeting Office365. This page requires that the user first interacts with the page to see the phishing form, possibly in an attempt to evade automated phishing detection engines.](https://unit42.paloaltonetworks.com/wp-content/uploads/2021/08/word-image-53.png)
![ww3ecure-authlogin4[.]ns02[.]info/Chase%20New/: A typical example of a consumer phishing attack targeting Chase bank.](https://unit42.paloaltonetworks.com/wp-content/uploads/2021/08/word-image-54.png)
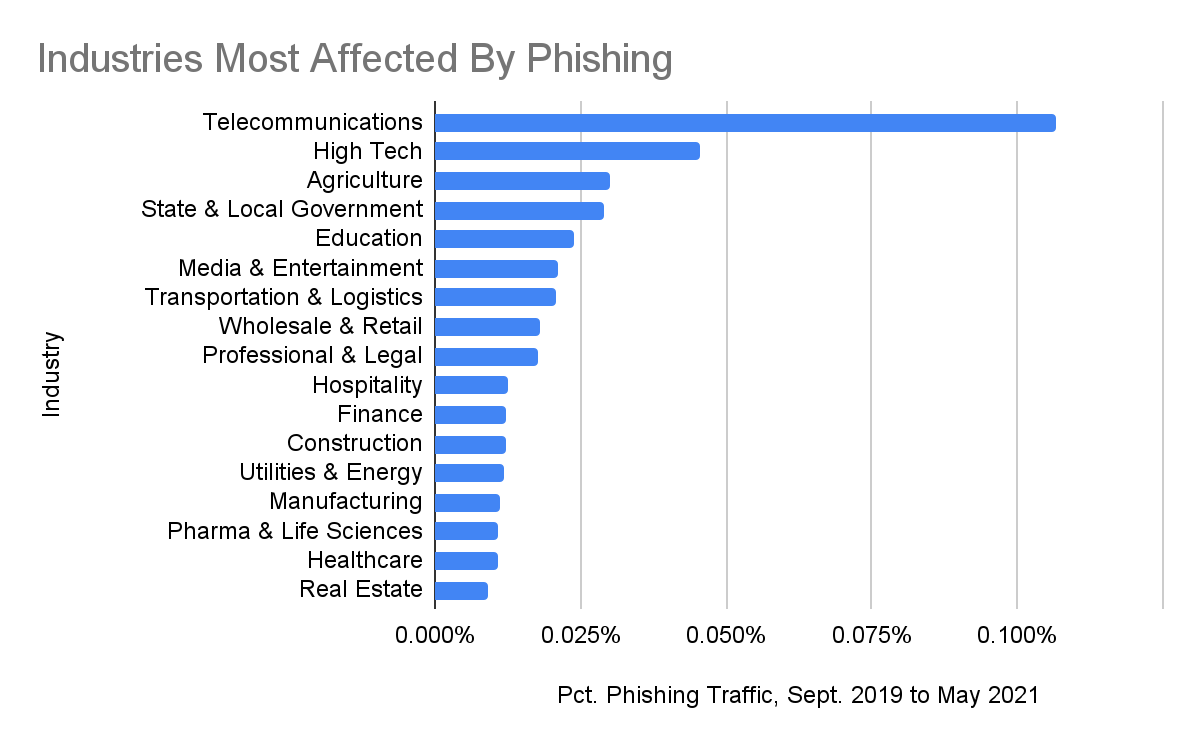
We found that the telecommunications industry was by far the most heavily impacted by phishing attacks, with about 0.1% of total traffic coming from phishing webpages. Of note, the high tech and education industries (both of which experienced significant drops in firewall traffic during the pandemic) also happen to be among the top-five most heavily affected industries.
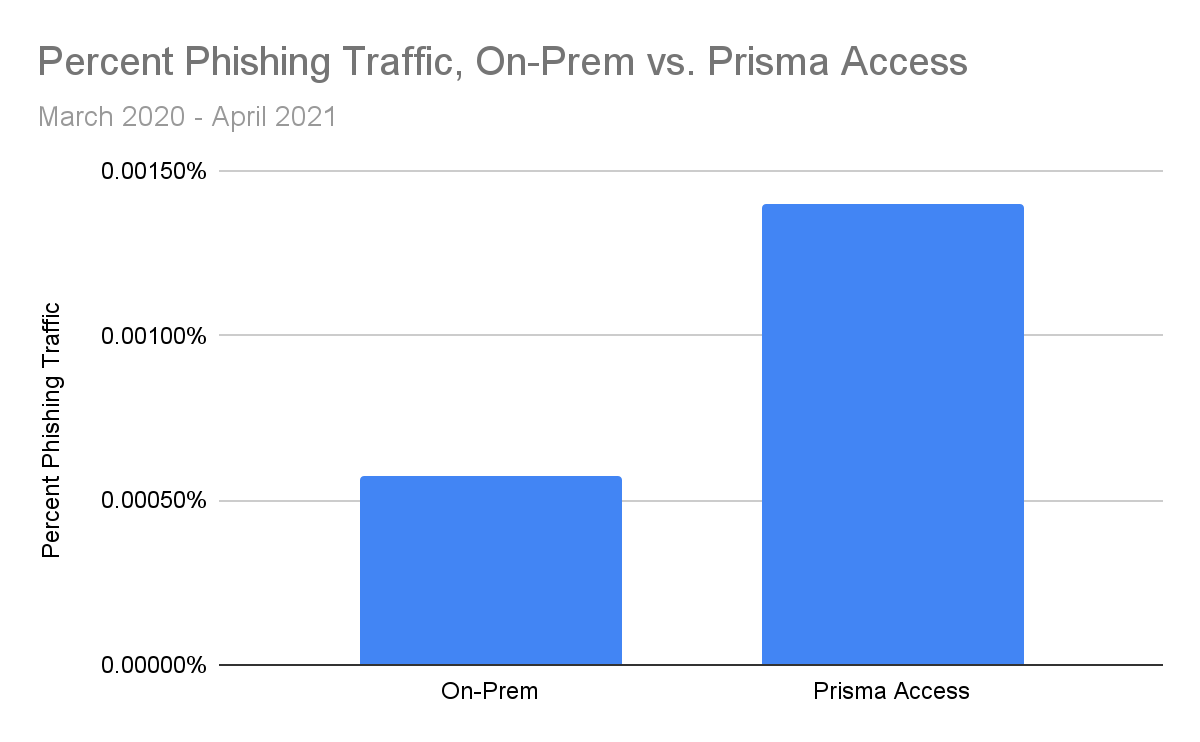
Furthermore, we saw that the percentage of traffic coming from phishing pages was more than 2.4 times greater in Prisma Access traffic than in on-prem firewall traffic. While we can’t be certain of the underlying reasons behind this, one plausible explanation is that employees may be less on-guard against phishing links when working outside the office. If this is indeed the case, then that would make it doubly important that employees who are working remotely have access to adequate internet security like URL Filtering to protect them from online threats such as phishing attacks and other malicious webpages.
Securing Your Remote/Hybrid Workforce
With today’s work environment shifting more and more to the virtual sphere, and with more and more work happening outside the physical boundaries of an office or corporate campus, it’s often no longer enough to rely entirely on on-prem firewalls to keep end users protected while browsing the web.
We can see that attackers tried to make the most of this sudden spike in remote work by ramping up their rate of phishing attacks, going after end users’ corporate credentials, as well as their personal credentials. We are now observing more new phishing attacks per week now than ever before, and our findings suggest that remote employees may be especially vulnerable to these phishing attacks, emphasizing the importance of having the proper defenses in place.
For end users who have access to Palo AltoNetworks URL Filtering services (e.g. via Prisma Access or GlobalProtect), it is likely that many of these phishing URLs would have been blocked before even being rendered in the user’s web browser. For end users working from home without access to a Next-Generation Firewall or cloud-delivered security service, it is likely that more of these attacks would have been successful, and that many end users have been fooled into giving attackers either their business login credentials or sensitive personal information.
With more companies looking to adopt remote and/or hybrid work models in the future, it is more important than ever to ensure that all employees have secure access to the internet, no matter where they happen to be physically located.
Conclusion
We have seen that threat actors ramped up their rate of phishing attacks at the same time as the number of employees who were working from home increased. If employers want to maintain a secure workforce in this new hybrid/remote environment, it is crucial that employees who are working from home have the same access to adequate coverage from cyberthreats that employees who are working in the office do.
Palo Alto Networks remote-work offerings, including cloud-delivered security services such as URL Filtering and Threat Prevention, can protect employees from the latest phishing and malware attacks regardless of whether they are working from the office or remotely.
In addition to these security services, best practices to protect yourself and your organization from phishing attacks include:
For individuals:
- Exercising caution when clicking on any links or attachments contained in suspicious emails, especially those relating to one’s account settings or personal information, or otherwise trying to convey a sense of urgency.
- Verifying the sender’s address for any suspicious emails in your inbox.
- Double-checking the URL and security certificate of each website before inputting your login credentials.
- Reporting suspected phishing attempts to your organization’s IT or InfoSec department
For organizations:
- Implementing security awareness training to improve employees’ ability to identify fraudulent emails.
- Regularly backing up your organization’s data as a defense against ransomware attacks initiated via phishing emails.
- Enforcing multi-factor authentication on all business-related logins as an added layer of security.
Phishing emails can be the start of ransomware attacks. If you think you may have been impacted by ransomware, please email unit42-investigations@paloaltonetworks.com or call (866) 486-4842 – (866) 4-UNIT42 – for U.S. toll free, (31-20) 299-3130 in EMEA or (65) 6983-8730 in JAPAC. The Unit 42 Incident Response team is available 24/7/365. You can also take preventative steps by requesting a Ransomware Readiness Assessment.
Additional Resources
Acknowledgements
The author would like to thank Wei Wang, Huagang Xie, Mayuresh Ektare, Vaishnavi Grudanti and Mike Jacobsen for helping to set the direction for this research; Claud Xiao, Russell Holloway and Eric Chen for helping to gather the data used in the analyses; and Laura Novak, Jen Miller Osborn, Jim Finkle and Lakshmi Kandadai for their help in publishing the blog.











 Get updates from Unit 42
Get updates from Unit 42