CTB-Locker is a well-known ransomware Trojan used by crimeware groups to encrypt files on the victim’s endpoints and demand ransom payment to decrypt the files back to their original state. Earlier this week we detailed a new CTB-Locker campaign and why legacy security products won’t protect enterprise networks.
In this blog post we will detail how to protect yourself from CTB-Locker, even if you aren’t protected by Palo Alto Networks next-generation enterprise security.
Since our first blog post on the campaign, here are some updates:
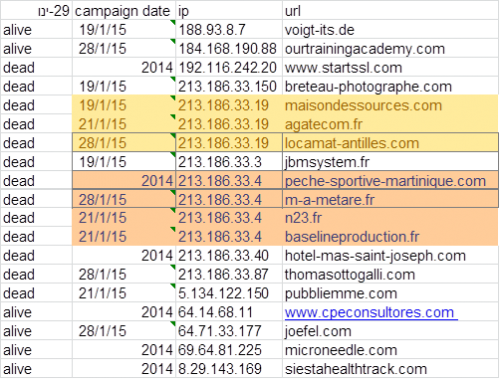
- We discovered another campaign that started on January 21, and you can see a few paragraphs below the malicious sites used.
- We can see that during four campaigns over at least three months, attackers kept the IP 213.186.33.4 and 213.186.33.19 in three out of four campaigns. The other servers appear to have been used only for single campaigns.
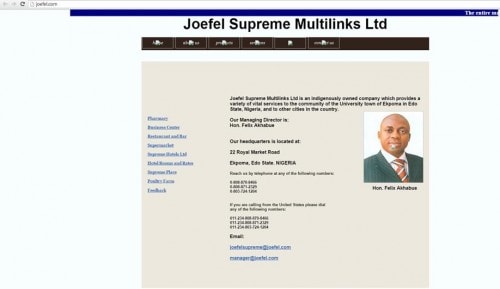
- Six of the 20 malicious sites we’ve identified are still live as of this posting, and this is the one of them:
There are two possible scenarios for sites like this:
- The attackers have gained unauthorized access to those servers or specific websites and planted C&C inside a legitimate website.
- The attackers bought this website and have added what appears to be "legit" content to disguise its real purpose.
User Awareness
Here are some things to watch out for:
- The below icon is used by the attacker against at least two of our protected customers. (Of course, it can be easily replaced by the attacker.)

- Suspicious file extension (SCR) is almost always malicious (especially if you received it from unknown sender).
New IOC
- Additional Mutex 93031785
- Full server list – you can block traffic to this sites on port 443:
- The latest campaign is still going on – we have just discovered about 70 new hashes: please see attached .csv file.
- One attack from the newest campaign called "industriestr_3-7_49832_freren.scr" (using joefel.com site) is unknown to VirusTotal. Sha256: 614f3d7ef084f12e9034f3723a8016783ced90240c0425fc9fc2324e7d1b5d2e
Conclusion
Earlier this week we identified new CTB-Locker campaigns. Palo Alto Networks Enterprise Security Platform protects from CTB-Locker in a way legacy security solutions can’t.
The above data should help in identifying and understanding CTB-Locker a bit better, but these are temporary solutions. Solving this endless cat-and-mouse game means upgrading to next-generation security. Learn more about Palo Alto Networks Enterprise Security Platform here.











 Get updates from Unit 42
Get updates from Unit 42