After news of WireLurker began circulating in handful Chinese-language tech forums over the summer, a Chinese-language technology blogger conducted online research in an attempt to track down the author of WireLurker and engage him in an online chat. While it is unclear whether he found the actual author, it appears he was able to locate someone associated with the company that produced WireLurker and controlled the Command and Control (C2) domain.
The following is a translated summary of the Chinese blogger’s investigation with supplemental research and analysis conducted by Unit 42. Due to the amount of personal information the original blog contains, we will make the blog address available only upon request.
Initial Investigation
While the WireLurker C2 domain registrant information did not reveal personal registrant information, the blogger was able to track down two related apps within Apple’s App Store (Note: Apple has since removed both of these apps). Both had the same developer, Lei Li, and QQ number, 127863672.
The support site for one of the applications was www.comeinbaby[.]com, the C2 server for WireLurker; the support site for the second was manhuaba.com[.]cn. The aforementioned QQ number is also listed for support on www.comeinbaby[.]com. At the time, both of these sites resolved to the same IP address, 124.248.245.78. This led the blogger to an individual using the online handle”段誉523”, which in turn revealed a Weibo page for a man who claimed he:
- Lived in Beijing
- Referenced a QQ number (not a match with 127863672)
- Worked at a small company in the Pingguoyuan area of Beijing
- Graduated from the Shenyang Academy of Engineering in 2003
Blogger Contact With ”段誉523”
The individual behind the ”段誉523” handle played coy when contacted by the blogger, noting he was “envious” of WireLurker. However, when pressed, he admitted that his skills include iOS front-end, client-side development, and that he was not responsible for “backend issues”. He follows up by promising to share the blogger’s questions with his boss. He also expresses concern that the blogger found him so easily. The conversation between the two ends without any definitive closure. Below are relevant screenshots of the summarized conversation.
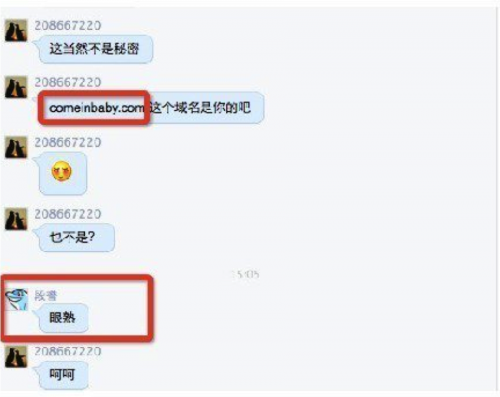
Figure 1. The individual claims to be “envious” of the C2 domain.
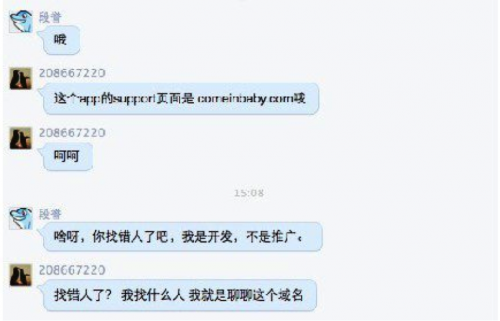
Figure 2. The individual claims the blogger found the wrong person, as he is just a developer.
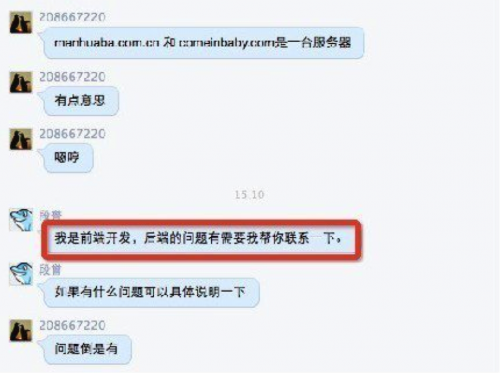
Figure 3. The blogger notes the relationship between the two domains, and the individual again says he is just a front-end developer and offers to help the blogger contact the right person.
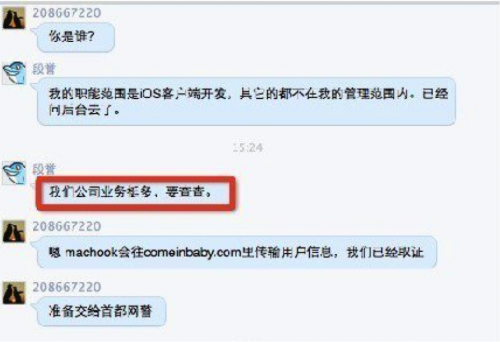
Figure 4. The individual again says he just does development for iOS front-end, client side apps and is not responsible for anything else. He also says his company has lots of skilled employees and offers to let the blogger visit. However, he never gives the company name or specific location.
Further Research on ”段誉523”
Our open source searches for the ”段誉523” handle reveal multiple accounts and posts within tech forums, particularly for Nokia and iOS apps. Notably, this handle is associated with an iOS developer within a third-party app store known for proliferation of trojanized WireLurker apps. In fact, this association is what enabled the blogger to track him down, as the listed QQ was the same as that listed for the two aforementioned apps in the Apple Store. However, in recent posts, the individual behind the ”段誉523” handle claimed he was the subject of significant online harassment and maintained he was not responsible for the malicious behavior of WireLurker. Most of the community responses to these posts are unsympathetic, sharing in the belief that this individual is at a minimum culpable of covering for the responsible party where he works.












 Get updates from Unit 42
Get updates from Unit 42