Threat Assessment: Zeppelin Ransomware
Executive Summary
Originally reported by BlackBerry Cylance in 2019, the Zeppelin ransomware family is a variant of the VegaLocker/Buran ransomware-as-a-service (RaaS) family – named because the text “ZEPPELIN” is added to the encrypted file code. Zeppelin continues to have a strong presence in the ransomware threat landscape, with new campaigns emerging routinely. Although it is not on the level of Egregor, DoppelPaymer or Ryuk in terms of its sophistication, targeting or attack pattern, Zeppelin has proven itself to be a formidable and robust commodity malware variant in the RaaS realm.
Although the earliest observed Zeppelin samples are from November 2019, the ransomware family is still very much in use by malicious actors. Unit 42 continues to track Zeppelin ransomware campaign activity in both its own telemetry data, and via open-source intelligence (OSINT).
Zeppelin Ransomware Overview
Zeppelin is highly configurable, but maintains common methods for distribution and deployment found with many ransomware families today, including:
- Phishing emails.
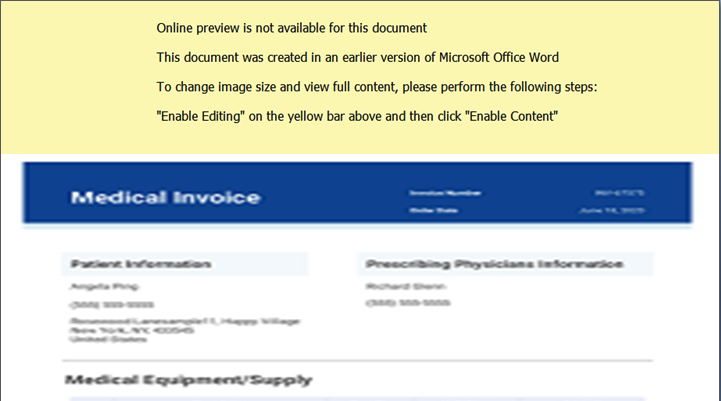
- Microsoft Word document with malicious macros embedded.
- PowerShell loaders.
- Open ScreenConnect or VPN connections.
- Malicious EXE files.
- Malicious DLL files.
Additionally, Zeppelin is often distributed via compromised websites or temporary command and control (C2) infrastructures that are active only during distribution. Further complicating things, recent Zeppelin variants include a sleep function that lasts for 26 seconds in an attempt to bypass dynamic analysis engines and sandboxes. Zeppelin also notably includes functionality that checks the victim’s country code to make sure it’s not running in Russia, Ukraine, Belarus or Kazakhstan.
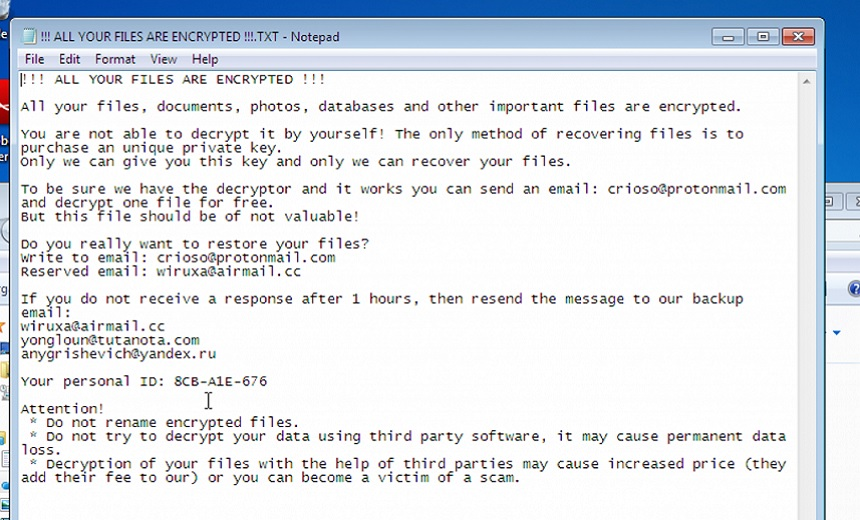
Zeppelin has spared few industries in terms of targeting, but some of the hardest-hit industry verticals include real estate, healthcare, manufacturing, finance and high tech. Zeppelin’s ransom notes vary widely from highly generic to specifically crafted notes related to the targeted organizations. In some cases, the actors behind Zeppelin target high-profile organizations within those same industry verticals. Average ransom payment for 2020 was $14,088, paid in Bitcoin. Zeppelin victims spanned several countries, with victims in the U.S., Canada, Bulgaria, Japan, South Korea, France and Taiwan.
More information on Zeppelin victimology can be found in the 2021 Unit 42 Ransomware Threat Report.
Courses of Action
This section documents relevant tactics, techniques and procedures (TTPs) used with Zeppelin and maps them directly to Palo Alto Networks product(s) and service(s). It also further instructs customers on how to ensure their devices are configured correctly.
| Product / Service | Course of Action |
| Initial Access, Defense Evasion, Execution, Discovery, Command and Control, Impact | |
| Spearphishing Attachment [T1566.001], Web Protocols [T1071.001], Obfuscated Files or Information [T1027], Windows Command Shell [T1059.003], Inhibit System Recovery [T1490], Modify Registry [T1112], File and Directory Discovery [T1083], Data Encrypted for Impact [T1486] | |
| NGFW | Ensure application security policies exist when allowing traffic from an untrusted zone to a more trusted zone |
| Ensure 'Service setting of ANY' in a security policy allowing traffic does not exist | |
| Ensure 'Security Policy' denying any/all traffic to/from IP addresses on Trusted Threat Intelligence Sources Exists | |
| Set up File Blocking | |
| WildFire | Ensure that WildFire file size upload limits are maximized |
| Ensure forwarding is enabled for all applications and file types in WildFire file blocking profiles | |
| Ensure a WildFire Analysis profile is enabled for all security policies | |
| Ensure forwarding of decrypted content to WildFire is enabled | |
| Ensure all WildFire session information settings are enabled | |
| Ensure alerts are enabled for malicious files detected by WildFire | |
| Ensure 'WildFire Update Schedule' is set to download and install updates every minute | |
| Threat Prevention† | Ensure an anti-spyware profile is configured to block on all spyware severity levels, categories and threats |
| Ensure DNS sinkholing is configured on all anti-spyware profiles in use | |
| Ensure passive DNS monitoring is set to enabled on all anti-spyware profiles in use | |
| Ensure a secure anti-spyware profile is applied to all security policies permitting traffic to the Internet | |
| Set up File Blocking | |
| Ensure that antivirus profiles are set to block on all decoders except 'imap' and 'pop3' | |
| DNS Security† | Enable DNS Security in Anti-Spyware profile |
| URL Filtering† | Ensure that PAN-DB URL Filtering is used |
| Ensure that URL Filtering uses the action of ‘block’ or ‘override’ on the <enterprise approved value> URL categories | |
| Ensure that access to every URL is logged | |
| Ensure all HTTP Header Logging options are enabled | |
| Ensure secure URL filtering is enabled for all security policies allowing traffic to the internet | |
| Cortex XDR | Enable Anti-Exploit Protection |
| Enable Anti-Malware Protection | |
| Configure Behavioral Threat Protection under the Malware Security Profile | |
| Cortex XSOAR | Deploy XSOAR Playbook - Palo Alto Networks Endpoint Malware Investigation |
| Deploy XSOAR Playbook - Ransomware Manual for incident response | |
Table 1. Courses of Action for Zeppelin ransomware.
†These capabilities are part of the NGFW security subscriptions service.
Conclusion
Stable in its operation, straightforward to implement and effective in its impact, Zeppelin continues to operate globally. Unit 42 fully expects Zeppelin ransomware activity to continue for the foreseeable future.
Indicators of Compromise (IoCs) associated with Zeppelin are available here, and have been published to the Unit 42 TAXII feed.
Palo Alto Networks detects and prevents Zeppelin in the following ways:
- WildFire: All known samples are identified as malware.
- Cortex XDR with:
- Indicators for Zeppelin.
- Anti-Ransomware Module to detect Zeppelin encryption behaviors.
- Local Analysis detection for Zeppelin binaries.
- Next-Generation Firewalls: DNS Signatures detect the known command and control (C2) domains, which are also categorized as malware in URL Filtering.
- AutoFocus: Tracking related activity using the Zeppelin tag.
Additionally, campaign-centric Indicators of Compromise (IoCs) observed by Unit 42 associated with Zeppelin were published on the Unit 42 Twitter feed on Dec. 11, 2020 (part one and part two), and Dec. 16, 2020.
Additional Resources
- Zeppelin: Russian Ransomware Targets High Profile Users in the U.S. and Europe
- Zeppelin Ransomware returns with a fresh wave of attacks
Continue Reading: DoppelPaymer












 Get updates from Unit 42
Get updates from Unit 42