This post is also available in: 日本語 (Japanese)
Threat Assessment: Phobos Ransomware
Executive Summary
Phobos is a relatively basic and prolific ransomware family first publicly identified in December 2018. Because of its basic design and implementation, Phobos has been popular among threat actors. Phobos uses well-established infection vectors, such as hacked, sold, insecure or otherwise vulnerable Remote Desktop Protocol (RDP) connections or malicious attachments in phishing emails. Phobos is very similar to another ransomware family, Dharma, of which Phobos is considered a variant. In addition to the code similarities it shares with Dharma, Phobos is in part likely distributed by the same group of actors that distributed Dharma.
Phobos Ransomware Overview

While Phobos is relatively basic in its technical functionality, there are some notable functions that make Phobos interesting. While Phobos’ abuse elevation techniques do not directly include a User Account Control (UAC) bypass, a UAC bypass confirmation does routinely pop up.
Upon accepting the popup and when the encryption processes using an AES-256 key are completed, .HTA and .TXT ransom notes are displayed on the infected endpoint with a filename of info[.]txt. Phobos continues to run in the background, encoding new files the code is instructed to encrypt.
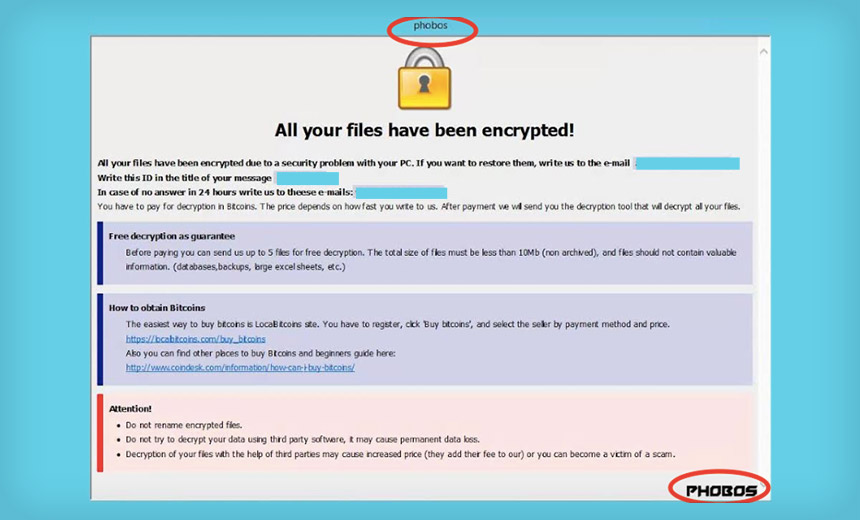
Phobos attempts to ransom all local and network shares connected to the infected host. Each infected file is encrypted with an individual key and the encrypted files have an extension of .acute. Phobos’ persistence mechanisms include installing itself in %APPDATA%, adding registry keys to autostart to ensure the malware process is persistent after a reboot. One interesting part of its functionality is the different file encoding technique used for large files. Phobos will only encrypt specific portions of large files, which reduces the amount of time it takes to encrypt the large files.
Phobos has served as the foundation for later variants, such as Eking ransomware, which was discovered in October 2020.
Phobos is most often sold in underground ransomware-as-a-service (RaaS) offerings. Phobos has historically targeted organizations of varying sizes, but in some isolated instances, Phobos has infected individuals. The total victim count of Phobos remains currently unknown.
Phobos and Dharma share several actor and code similarities. Both families share the same ransom note post-infection. Additionally, initial correspondence from the victim to both actors is the same. These shared features, along with coding similarities that Dharma and Phobos have, suggest that this malware is being developed by the same actor.
However, code differences, particularly in the file structure, define it as a variant. Specifically, Phobos has some notable differences, namely in adding in modular configuration support and providing functionality to manually encrypt folders of interest.
The average ransom payment in 2020 for Phobos was $13,955. Palo Alto Networks observed attacks on victims in the finance, education, manufacturing, professional and legal services, insurance, high tech, construction and engineering, healthcare and energy sectors. Similar to Dharma, the threat actors focus on small to medium-sized businesses. Phobos victims were located in the U.S., Portugal, Brazil, Seychelles, Romania, Indonesia, Germany and Japan.
More information on Phobos victimology can be found in the 2021 Unit 42 Ransomware Threat Report.
Courses of Action
This section documents relevant tactics, techniques and procedures (TTPs) used with Phobos and maps them directly to Palo Alto Networks product(s) and service(s). It also further instructs customers on how to ensure their devices are configured correctly.
| Product / Service | Courses of Action |
| Execution | |
| Windows Management Instrumentation [T1047] | |
| NGFW | Ensure that User-ID is only enabled for internal trusted interfaces |
| Ensure that 'Include/Exclude Networks' is used if User-ID is enabled | |
| Ensure that the User-ID Agent has minimal permissions if User-ID is enabled | |
| Ensure that the User-ID service account does not have interactive logon rights | |
| Ensure remote access capabilities for the User-ID service account are forbidden. | |
| Ensure that security policies restrict User-ID Agent traffic from crossing into untrusted zones | |
| Ensure application security policies exist when allowing traffic from an untrusted zone to a more trusted zone | |
| Ensure 'Service setting of ANY' in a security policy allowing traffic does not exist | |
| Ensure 'Security Policy' denying any/all traffic to/from IP addresses on Trusted Threat Intelligence Sources Exists | |
| Cortex XDR Prevent | Configure Restrictions Security Profile |
| Defense Evasion, Persistence | |
| Masquerading [T1036], Modify Registry [T1112], Registry Run Keys / Startup Folder [T1547.001] | |
| Threat Prevention† | Ensure that antivirus profiles are set to block on all decoders except 'imap' and 'pop3' |
| Ensure a secure antivirus profile is applied to all relevant security policies | |
| WildFire | Ensure that WildFire file size upload limits are maximized |
| Ensure forwarding is enabled for all applications and file types in WildFire file blocking profiles | |
| Ensure a WildFire Analysis profile is enabled for all security policies | |
| Ensure forwarding of decrypted content to WildFire is enabled | |
| Ensure all WildFire session information settings are enabled | |
| Ensure alerts are enabled for malicious files detected by WildFire | |
| Ensure 'WildFire Update Schedule' is set to download and install updates every minute | |
| Cortex XDR Prevent | Configure Behavioral Threat Protection under the Malware Security Profile |
| Enable Anti-Exploit Protection | |
| Enable Anti-Malware Protection | |
| Lateral Movement | |
| Replication Through Removable Media [T1091] | |
| Cortex XDR Prevent | Enable Device Control |
| Impact | |
| Inhibit System Recovery [T1490], Data Encrypted for Impact [T1486] | |
| Cortex XSOAR | Deploy XSOAR Playbook - Palo Alto Networks Endpoint Malware Investigation |
| Deploy XSOAR Playbook - Ransomware Manual for incident response. | |
Table 1. Courses of Action for Phobos ransomware.
†These capabilities are part of the NGFW security subscriptions service.
Conclusion
Phobos is much like that of other ransomware families witnessed and analyzed by Unit 42. Capitalizing on the ease of use typical to RaaS, the actors distributing Phobos can often vary widely. Malware author and code-reuse similarities are common among Phobos ransomware families and represent an evolving threat ecosystem that thrives on sharing and common RaaS affiliate models enabling a ransomware actor to capitalize on minimal time investment.
Palo Alto Networks detects and prevents Phobos in the following ways:
- WildFire: All known samples are identified as malware.
- Cortex XDR with:
- Indicators for Phobos.
- Anti-Ransomware Module to detect Phobos encryption behaviors.
- Local Analysis detection to detect Phobos binaries.
- Next-Generation Firewalls: DNS Signatures detect the known command and control (C2) domains, which are also categorized as malware in URL Filtering.
- AutoFocus: Tracking related activity using the Phobos tag.
Additionally, Indicators of Compromise (IoCs) associated with Phobos are available on GitHub, and have been published to the Unit 42 TAXII feed.
Additional Resources
Continue Reading: Dharma











 Get updates from Unit 42
Get updates from Unit 42