Threat Assessment: GandCrab and REvil Ransomware
Executive Summary
GandCrab ransomware was a short-lived but prolific ransomware family in its time. It was first observed in January 2018 and was a prevalent threat until May 2019. During that time, it went through a number of different versions. GandCrab infections were most commonly observed as payloads in malvertising, spam and exploit kit attacks. Malvertising attacks are malicious advertisements that are used to infect victims via a drive-by download. Exploit kits have routinely been used in a similar manner, with a multitude of them dropping GandCrab on a victim’s computer. The most common exploit kits used to distribute GandCrab were Rig and Grandsoft.
In early 2019, the authors behind GandCrab announced that they were retiring as they had made enough money and done enough damage. However, around the same time, a new ransomware threat called REvil was emerging (also known as Sodinokibi). There were strong similarities between the two ransomware families, which have led security researchers to believe that REvil was an evolution of GandCrab. The victims and tactics employed by affiliate attackers had changed. REvil was still an affiliate ransomware like GandCrab, but the affiliates used were more skilled at targeted attacks as opposed to the commodity attacks employed by GandCrab.
GandCrab Ransomware Overview
What made GandCrab unique was the affiliate program that was used to propagate the malware. This left the distribution of the ransomware to partners who would gather victims and would in turn receive a portion of the profits from ransoms paid. It's been reported that affiliates would receive 30 to 40 percent.
This left the distribution logistics to other attackers, which explains the wide array of attacks used, leaving the authors of GandCrab free to further develop and harden the malware. This was necessary for the authors, as there had been instances in which decryptors were released by researchers that would allow victims to decrypt their files after infection without needing to pay ransom. It's also suspected that the authors may be Russian, as the malware had been known to check victim keyboard layout and ignore a Russian layout. It's been suspected that this was to avoid prosecution in that country.
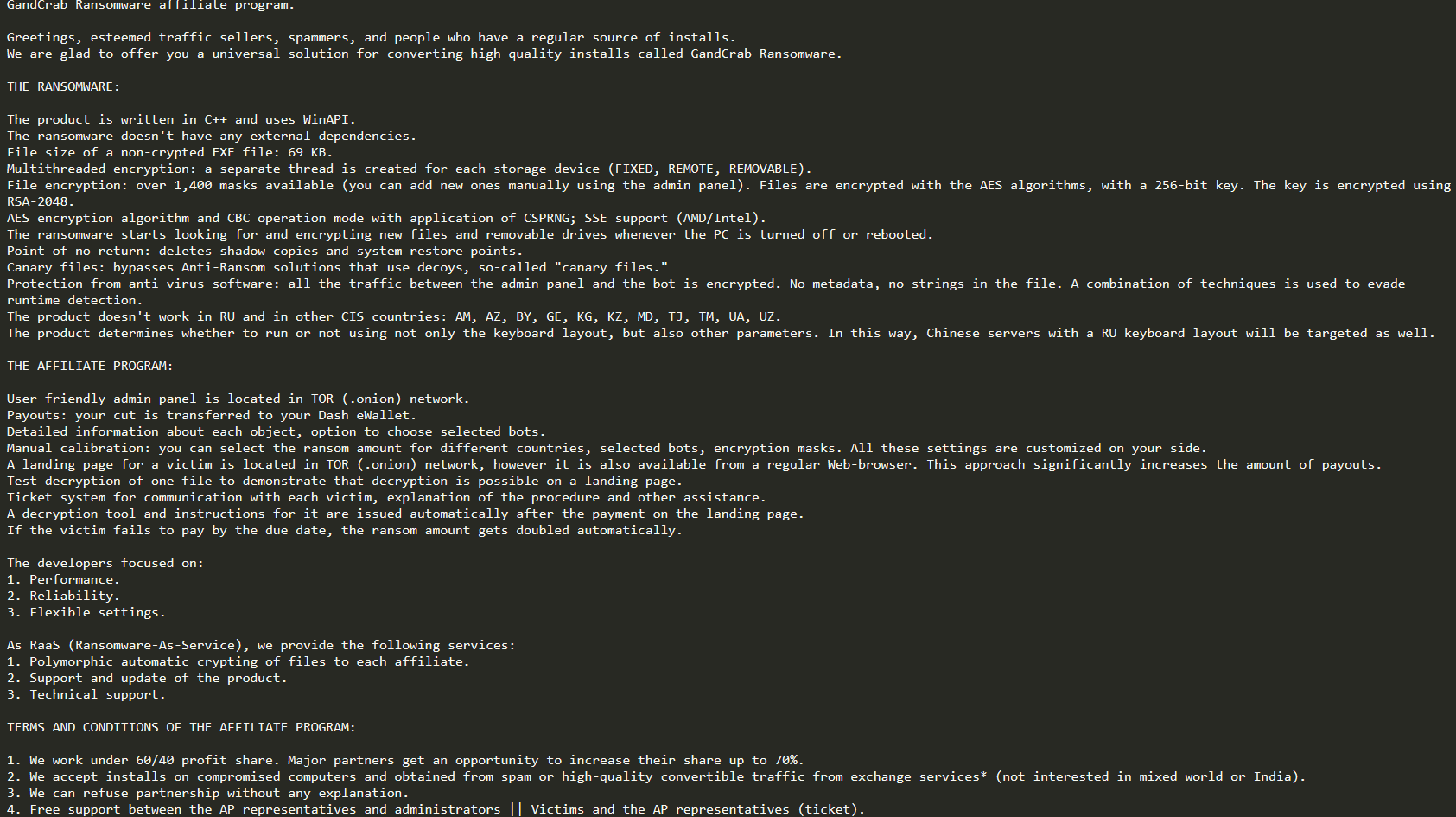
GandCrab is often easily identifiable by the file extension appended to the end of ransomed files – .KRAB and .CRAB
In May 2019, the developers of GandCrab famously announced that they were no longer going to develop the ransomware. Their reasoning was that they had made enough money in over a year to retire and prove that they could do evil and get away with it. The developers also claimed that they had made over $150 million in over a year and that they had dispersed their profits into other legal projects. Since this announcement, there have been other ransomware samples observed with similar indicators, so it's thought that some of the authors continued with the development of ransomware.
REvil Ransomware Overview
In April 2019, another ransomware called REvil appeared (also known as Sodinokibi). There were immediate similarities between GandCrab and REvil, which caused early samples of REvil to be identified as GandCrab. REvil is also a Ransomware-as-a-Service (RaaS), which uses affiliates to distribute infections of the malware. The affiliates would then get a percentage of the ransoms paid after developers of the ransomware got their cut.
The distribution methods for REvil differed from those of GandCrab because affiliates were more skilled and actively attacked victims to compromise enterprise networks via exploits such as Oracle WebLogic CVE-2019-2725 or brute-forcing Remote Desktop Protocol (RDP) passwords to drop REvil. There would also be usage of red team tools, techniques and procedures (TTP) as opposed to the malicious spam, exploit kits and malvertising vectors of GandCrab. This also meant that victims would be more targeted for the intent of higher ransoms to be paid.
Analysis of GandCrab has shown that there are strong similarities between REvil and GandCrab ransomware samples. Based on the similarities between the two, it's widely believed that REvil is just a rebrand and evolution of GandCrab. This in turn leads to the conclusion that not all of the developers of GandCrab were done creating such malware. The tactics for infection by affiliates also shows an evolution of the malware by moving on from commodity-based attacks to attacks using more skilled affiliates with familiarity of red team TTP. Targeted users also changed from anyone who may have clicked on a link in a malicious email to companies with exterior-facing vulnerabilities that allowed attackers in to drop REvil.
In 2020, the average ransom payment was $508,523, with REvil threat actors targeting victims in the professional and legal services, manufacturing, media and communication, wholesale and retail, construction and engineering, and energy sectors in the US, Australia, Canada, Finland, and Hong Kong.
More information on REvil victimology can be found in the 2021 Unit 42 Ransomware Threat Report.
Courses of Action
This section documents relevant tactics, techniques and procedures (TTPs) used with GandCrab and REvil, and maps them directly to Palo Alto Networks product(s) and service(s). It also further instructs customers on how to ensure their devices are configured correctly.
| Product / Service | Courses of Action |
| Command And Control | |
| Application Layer Protocol [T1071.001], Non-Application Layer Protocol [T1095] | |
| NGFW | Ensure application security policies exist when allowing traffic from an untrusted zone to a more trusted zone |
| Ensure 'Service setting of ANY' in a security policy allowing traffic does not exist | |
| Ensure 'Security Policy' denying any/all traffic to/from IP addresses on Trusted Threat Intelligence Sources Exists | |
| Threat Prevention† | Ensure that antivirus profiles are set to block on all decoders except 'imap' and 'pop3' |
| Ensure a secure antivirus profile is applied to all relevant security policies | |
| Ensure an anti-spyware profile is configured to block on all spyware severity levels, categories and threats | |
| Ensure DNS sinkholing is configured on all anti-spyware profiles in use | |
| Ensure passive DNS monitoring is set to enabled on all anti-spyware profiles in use | |
| Ensure a secure anti-spyware profile is applied to all security policies permitting traffic to the internet | |
| DNS Security† | Enable DNS Security in Anti-Spyware profile |
| URL Filtering† | Ensure that URL Filtering is used |
| Ensure that URL Filtering uses the action of ‘block’ or ‘override on the <enterprise approved value> URL categories | |
| Ensure that access to every URL is logged | |
| Ensure all HTTP Header Logging options are enabled | |
| Ensure secure URL filtering is enabled for all security policies allowing traffic to the internet | |
| Cortex XSOAR | Deploy XSOAR Playbook - Block IP |
| Deploy XSOAR Playbook - Block URL | |
| Deploy XSOAR Playbook - Palo Alto Networks - Hunting And Threat Detection | |
| Defense Evasion, Persistence, Discovery | |
| Exploitation for Defense Evasion [T1211], Registry Run Keys / Startup Folder [T1547.001], Masquerading [T1036.005], Modify Registry [T1112], Process Discovery [T1057] | |
| Threat Prevention† | Ensure a Vulnerability Protection Profile is set to block attacks against critical and high vulnerabilities, and set to default on medium, low and informational vulnerabilities |
| Ensure a secure Vulnerability Protection Profile is applied to all security rules allowing traffic | |
| Cortex XDR | Enable Anti-Exploit Protection |
| Enable Anti-Malware Protection | |
| Configure Behavioral Threat Protection under the Malware Security Profile | |
| Configure Restrictions Security Profile | |
| Impact | |
| Data Encrypted for Impact [T1486], Inhibit System Recovery [T1490] | |
| Cortex XSOAR | Deploy XSOAR Playbook - Ransomware Manual for incident response. |
| Deploy XSOAR Playbook - Palo Alto Networks Endpoint Malware Investigation | |
Table 1. Courses of Action for GandCrab and REvilransomware.
†These capabilities are part of the NGFW security subscriptions service.
Conclusion
While the concept of an attacker leveraging ransomware affiliate programs is not new, GandCrab proved just how easy and successful these programs can be in practice. Key to this success is creating a low barrier for entry into the cybercrime ecosystem, while also distributing funds across affiliate program members. GandCrab helped establish itself as a power player in the affiliate market schemes common in underground forums and social networks.
The actors behind GandCrab would have had people believe in 2019 that they were done with ransomware, but there were similarities in an emerging threat called REvil. The similarities observed became so strong that the security community believes that REvil is an evolution of Gandcrab. The evolution was not only in the malware, but in the affiliates used to distribute and their TTP to compromise enterprise victims. This led to more targeted victims and unfortunately higher ransoms. To top this all off, there is also an extortion angle that REvil employs. If victims would not pay by a deadline, their data stolen during encryption would be auctioned off in underground forums. It’s this direction of targeted attacks for affiliate ransomware that makes REvil so dangerous to enterprises.
Palo Alto Networks detects and prevents GandCrab in the following ways:
- WildFire: All known samples are identified as malware.
- Cortex XDR with:
- indicators for GandCrab.
- Anti-Ransomware Module to detect GandCrab encryption behaviors.
- Local Analysis detection to detect GandCrab binaries.
- Next-Generation Firewalls: DNS Signatures detect the known command and control (C2) domains, which are also categorized as malware in URL Filtering.
- AutoFocus: Tracking related activity using the GandCrab tag.
- AutoFocus: Tracking related activity using the REvil AKA Sodinokibi tag
Additionally, Indicators of Compromise (IoCs) associated with GandCrab are available on GitHub, and have been published to the Unit 42 TAXII feed.
Continue Reading: Defray777












 Get updates from Unit 42
Get updates from Unit 42