Executive Summary
In 2019, Business Email Compromise (BEC) maintained its rankings as both the most profitable and the most prominent threat facing our customers. According to the Federal Bureau of Investigation (FBI) Internet Crime Complaint Center (IC3), which recently released its annual report, US$1.77 billion in losses were attributed to BEC attacks over the course of 2019. This number dwarfed losses associated with romance scams, identity theft, credit card fraud, phishing, and ransomware combined over the same period.
With cases reported across all 50 states and in 177 countries, the FBI also published a press release in September 2019 announcing that in the preceding three-year period, BEC losses eclipsed US$26 billion globally. Put into perspective, the known and reported losses associated with this threat now exceed the estimated global losses from WannaCry (an estimated US$4 billion) and NotPetya (an estimated US$10 billion) combined.
Recognizing the severity of the threat combined with its impacts on our customers, Palo Alto Networks’ Unit 42 researchers continue to focus a core area of their research on Nigerian cybercrime, given the dominant proportionality and sheer enormity of BEC attacks originating from the region. Assigned the name SilverTerrier, these actors have now collectively produced more than 81,300 samples of malware linked to 2.1 million attacks. From their humble beginnings as a few individuals experimenting with commodity malware in 2014, our recent global data shows the number of threat actors has grown significantly to encompass over 480 different actors and groups that we track today.
In five years (from 2014 to 2019), SilverTerrier actors have evolved from being novice threat adversaries to mature cybercriminals.
According to our latest findings, we saw an 1163% increase in BEC attacks against the professional and legal services industry in 2019. While we lack insight into the root cause, this jump nevertheless demonstrates a significant shift in targeting practices amongst SilverTerrier actors.
Peaking at 245,637 BEC attacks in June 2019, the year ended with an average of 92,739 BEC attacks per month, representing a 172% increase from 2018. Of those BEC attacks, 97.8% leveraged email protocols to reach target networks. The most common tools that SilverTerrier actors used to attack organizations once they infiltrated those networks were information stealers and remote administration tools (RATs).
In this report, we identify the trends associated with SilverTerrier attacks, provide a refined adversary profile for network defenders, highlight the implications associated with the emergence of the first Nigerian commodity tool developer, and provide an overview of actions Palo Alto Networks is undertaking internally and externally to address this threat.
Attacks
In 2018 we noted an average of 34,039 attacks per month against our customer base. Over the course of 2019, those metrics have more than doubled, as monthly attack rates crossed the 50K, then 100K, and ultimately the 200K thresholds. Peaking at 245,637 attacks in June, 2019 ended with an average of 92,739 attacks per month, representing a 172% increase from 2018. Furthermore, while we continue to assess that this growth is representative of global trends, it remains important to note that our metrics only reflect attacks against our customer base, and as such, the total number of global attacks launched by these actors is presumed to be far greater.
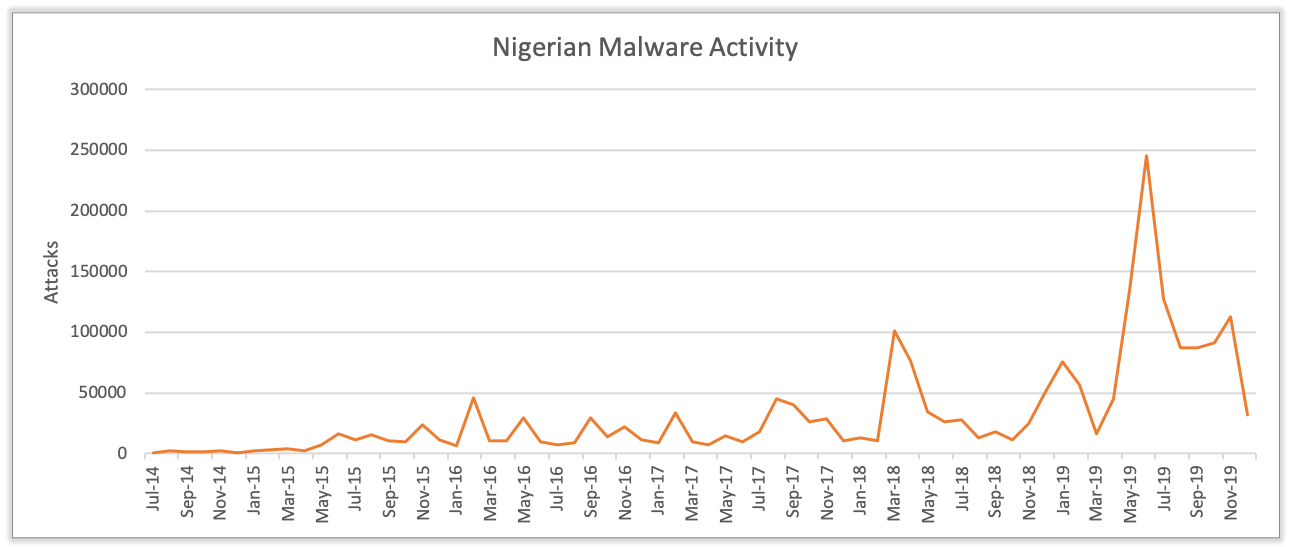
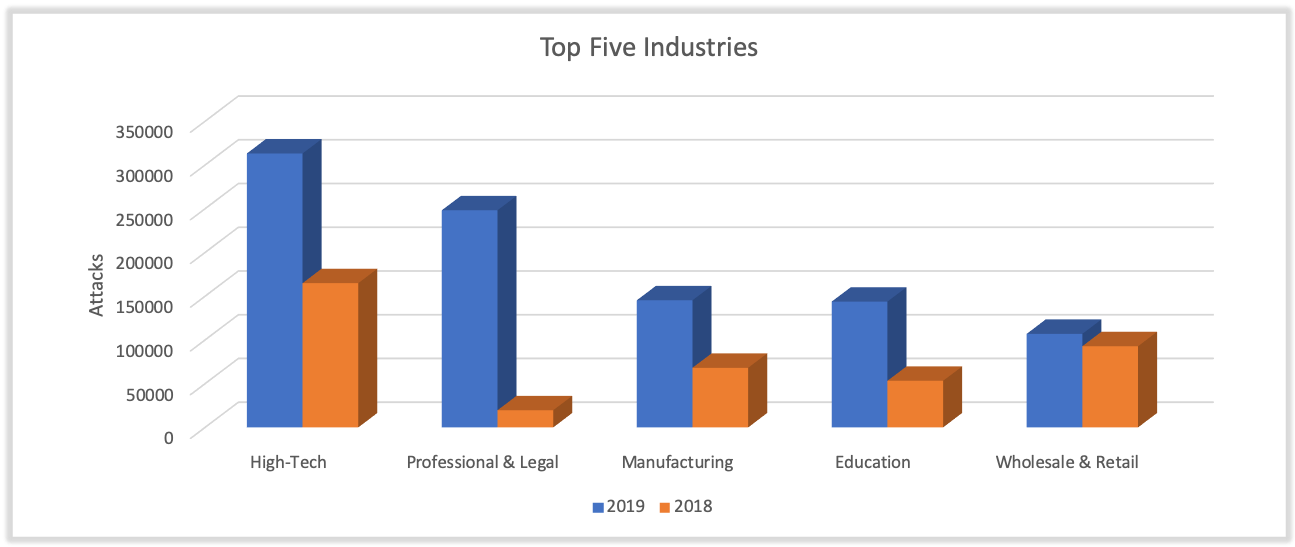
Exploring the targets of these attacks, we found that Nigerian threat actors remain indiscriminate in their targeting. Our data shows attacks targeted all industry segments, including small to large businesses, healthcare organizations, and even local, state, and federal government institutions. In measuring the top five targeted industries, we found the following:
- The high-tech industry received the greatest number of attacks, nearly doubling from 164K in 2018 to 313K in 2019.
- Close behind with 248K attacks, the professional and legal services industry advanced from being the fifth-most targeted industry in 2018 to the second-most targeted industry in 2019. Fueled by an alarming 1163% increase in attacks in 2019, this jump demonstrates a significant shift in targeting practices amongst SilverTerrier actors.
- The manufacturing industry was third, with 145K attacks in 2019, up from 68K in 2018.
- The education industry was fourth, with 143K attacks in 2019, up from 53K in 2018.
- The wholesale and retail industry was fifth, observing 107K attacks in 2019, reflective of a marginal 15% increase from 2018.
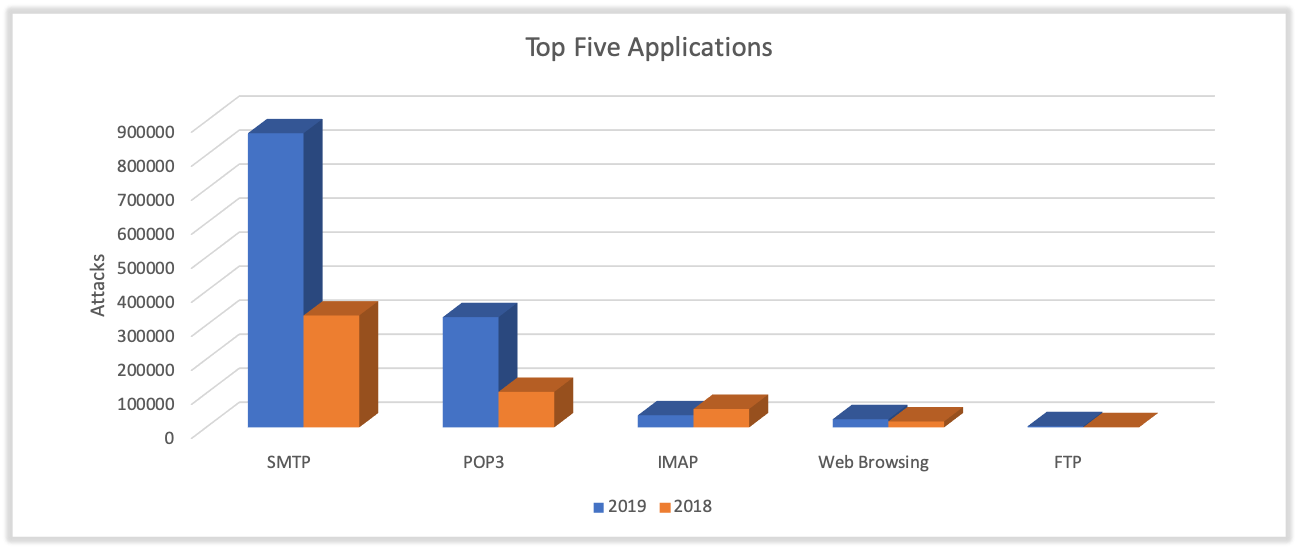
Taking a look at delivery vectors, we found that 97.8% of attacks leveraged email protocols to reach target networks, thus stressing the importance of employing and enabling security solutions capable of evaluating content entering corporate networks through these protocols.
- At the top of the list, SMTP traffic accounted for 864K (69%) of attacks observed in 2019.
- POP3 and IMAP accounted for 324K (26%) and 35K (2.8%) attacks, respectively.
- It is also worth noting that the number of attacks witnessed in IMAP traffic dropped for the first time in 2019. We assess that this drop is likely due to customers shifting away from IMAP, as they modernize and adopt SMTP as an industry standard.
- Beyond email, web browsing served as the fourth most common delivery vector in 2019 with 24K (1.9%) of attacks.
- We only observed 3.6K (.3%) attacks delivered through FTP traffic.
Malware
In years past, we have highlighted the ever-expanding ability of SilverTerrier actors to employ new technologies, tactics, and capabilities designed to advance their fraudulent schemes. Concurrently, the cybersecurity industry has historically characterized Nigerian malware actors as an emerging, rather than an established threat. As the analysis of this threat group turns five years old, we believe it is now pivotal to recognize that in many aspects, SilverTerrier actors have evolved to a point where they are demonstrating signs of maturity consistent with established threat groups in their delivery techniques, malware packaging, and technical abilities.
Over the course of 2019, our cloud-delivered WildFire® malware analysis service identified 27,310 samples of SilverTerrier malware. The vast majority of these samples were commodity malware tools, which employed a variety of obfuscation techniques designed to deceive traditional signature-based antivirus programs.
A comparison of these samples to VirusTotal revealed an average detection rate of 57.3% across all vendors at the time of discovery, demonstrating the effectiveness of obfuscation techniques against legacy antivirus platforms. A subsequent comparison conducted at the end of 2019 identified a greater proportion of samples available on the platform, but this increase, unfortunately, did not yield any notable improvements in detection rates across vendors. Counter-intuitively, the average rate actually decreased slightly to 57.1%, demonstrating that even with the benefit of time and prolonged exposure to the cybersecurity community, these samples remain undetected by over 40% of antivirus solutions.
By performing an analysis of the commodity malware tools themselves, we found that Nigerian threat actors continued to adopt new, and abandon old, capabilities consistent with tool popularity, effectiveness, detection rates, availability, and other market factors.
In tracking these trends, the following sections provide key insights designed to:
-
- Inform network administrators of the top threats facing their networks;
- Guide the cybersecurity industry in prioritizing detection and remediation capabilities; and
- Enable law enforcement to focus on attribution and legal process against the most prevalent tools.
Information Stealers
Information stealers are tools designed with a core information-stealing component that most commonly captures screenshots, passwords, and other sensitive files on an infected system. Once captured, the malicious programs then package and transmit these stolen items via various protocols to internet infrastructure controlled by a malign actor.
Over the past five years, we have tracked the use of 10 different commodity information stealer families by SilverTerrier actors. Over time, as new tools emerge on the market, the older, less effective tools have faded in popularity.
Our data shows that usage of the following five tools has subsequently dropped to negligible levels: Atmos, Keybase, ISpySoftware, ISR Stealer, and Zeus.
Conversely, there are five tools that still remain in active use with SilverTerrier actors: AgentTesla, AzoRult, Lokibot, Pony, and PredatorPain. Our analysis of these malware families found that Nigerian threat actors produced an average of 516 unique samples per month in 2019 (Figure 4). However, despite a steady flow of new samples each month, the usage of information stealers appears to have peaked in 2017, before entering a continued state of decline. While the root cause of this decline is hard to pinpoint, we assess that the lack of new tools entering the market, advancements in the cybersecurity landscape, increased law enforcement actions, routine exposure of control infrastructure, and a shift toward RATs by these actors are all contributing factors.
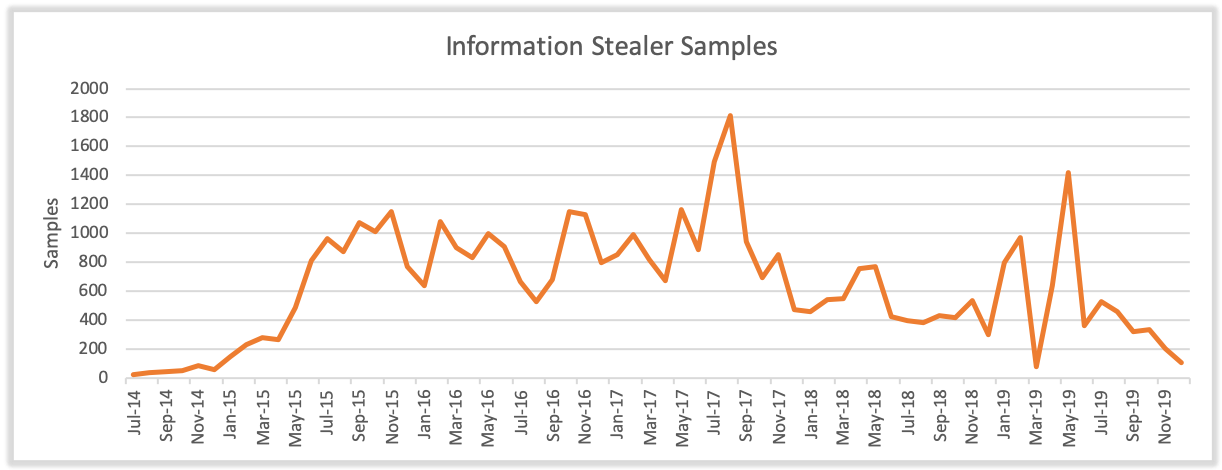
Amongst the five active tools in this category, we found that SilverTerrier actors only produced three tools in quantities greater than 50 samples per month. Consistent with 2018, LokiBot was the most popular tool in 2019, with an average of 291 new samples per month. However, this average was inflated largely by an anomalous, single month high of 1240 samples in May 2019. Pony, also known as Fareit, was second with an average of 146 samples per month, but production largely declined throughout the year. Finally, we observed a small uptick in the adoption of AzoRult in 2019, resulting in an average of 55 samples per month throughout the year.
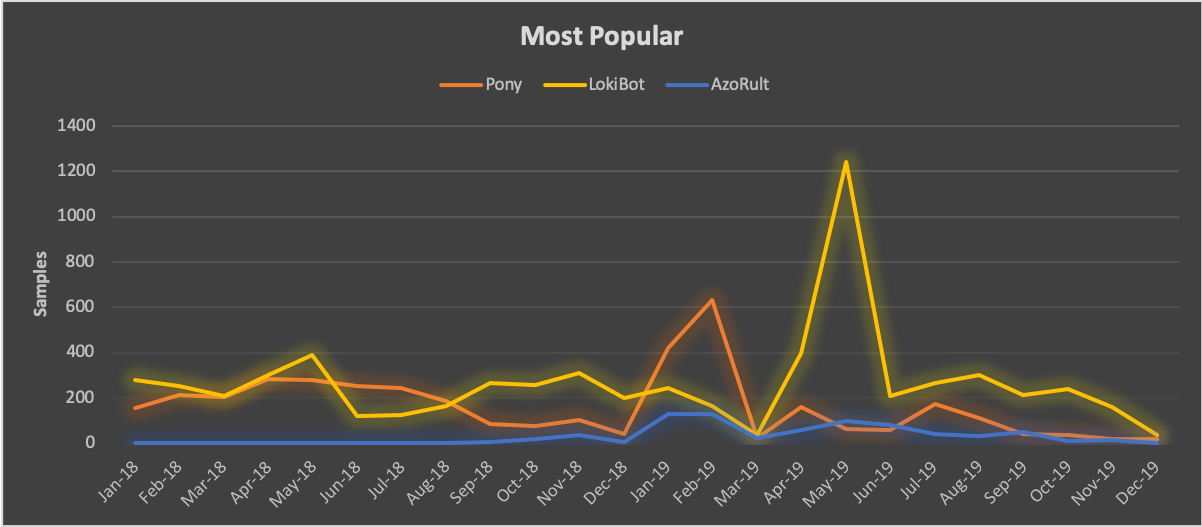
On the other end of the spectrum, PredatorPain, a tool that has received multiple updates over the years, continues to decline from its peak usage in 2016 with actors producing an average of only 17 samples per month in 2019. Additionally, AgentTesla, a small .NET keylogger, has also declined since its peak usage in 2017, with actors now producing an average of less than four new samples per month in 2019.
Remote Administration Tools
RATs are programs designed to provide remote access to compromised systems. These tools expand beyond the basic capture of sensitive files inherent with information stealers, and typically allow their users to interact directly with victim machines. To that end, these tools are often more complex than information stealers in terms of code and infrastructure requirements. Leveraging these tools, Nigerian threat actors can modify systems, access network resources, and perform common functions on behalf of compromised users. Over the past five years, we have tracked SilverTerrier use of 13 different RAT families. Similar to other types of commodity malware, these tools rise and fall in popularity, and over the course of 2019, our data shows that usage of LuminosityLink, NJRat, Quasar, and WarZone RATs have all dropped to negligible levels.
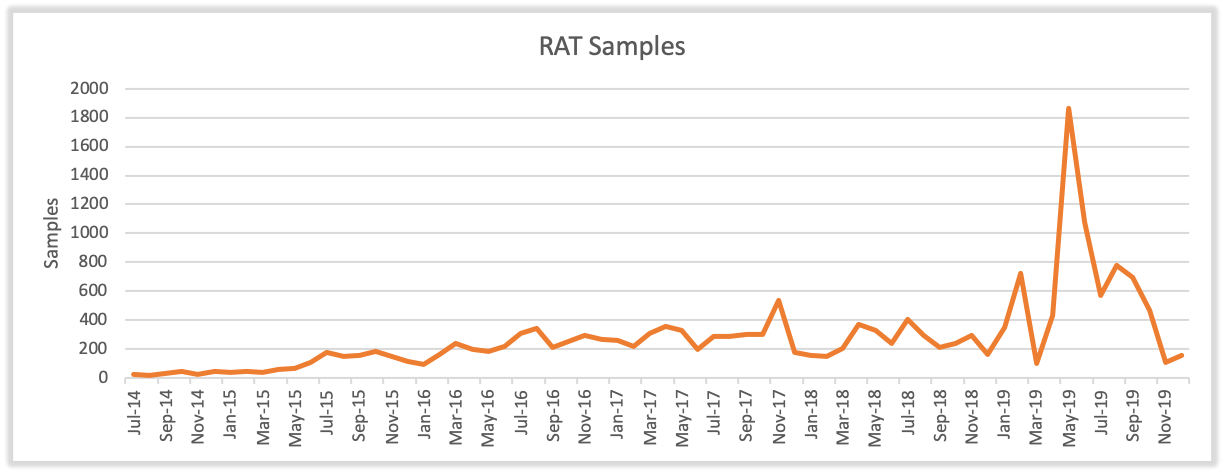
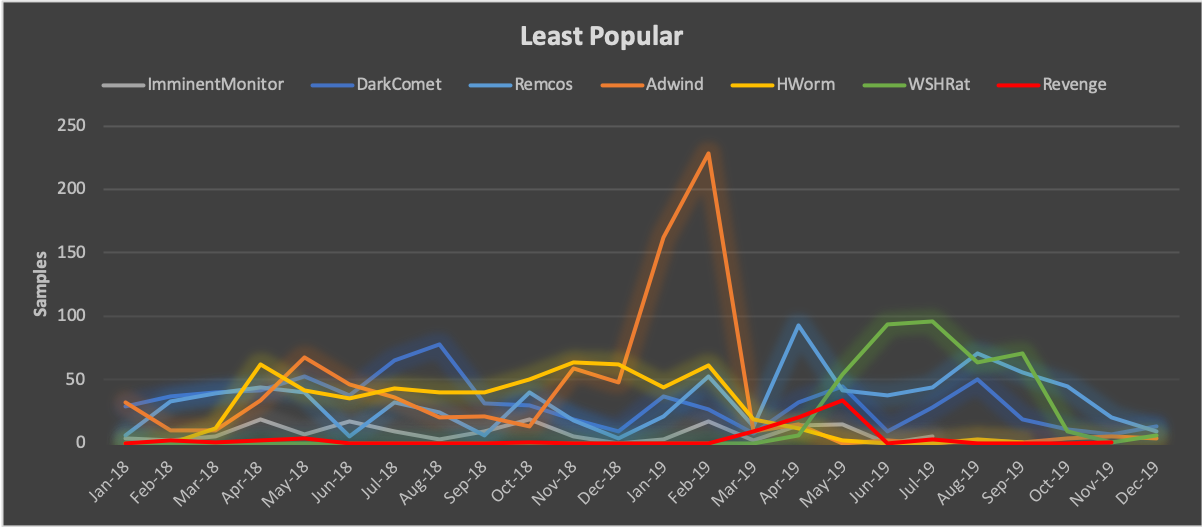
The nine RATs that remain in varying degrees of active use are: Netwire, DarkComet, NanoCore, Remcos, ImminentMonitor, Adwind, Hworm, Revenge, and WSHRat. Combined, SilverTerrier actors produced an average of 609 samples per month in 2019, representing an impressive 140% growth in production from 2018 (Figure 7). This growth represents the first time that the production and employment of RATs has exceeded the sample rate for information stealers over the five years that we have tracked this threat group. We assess that this shift is largely indicative of growing technical abilities, combined with the effectiveness of these tools in enabling fraudulent schemes. Further, we anticipate that this growth trend will continue throughout 2020, as we see increasing numbers of actors adopting these tools.
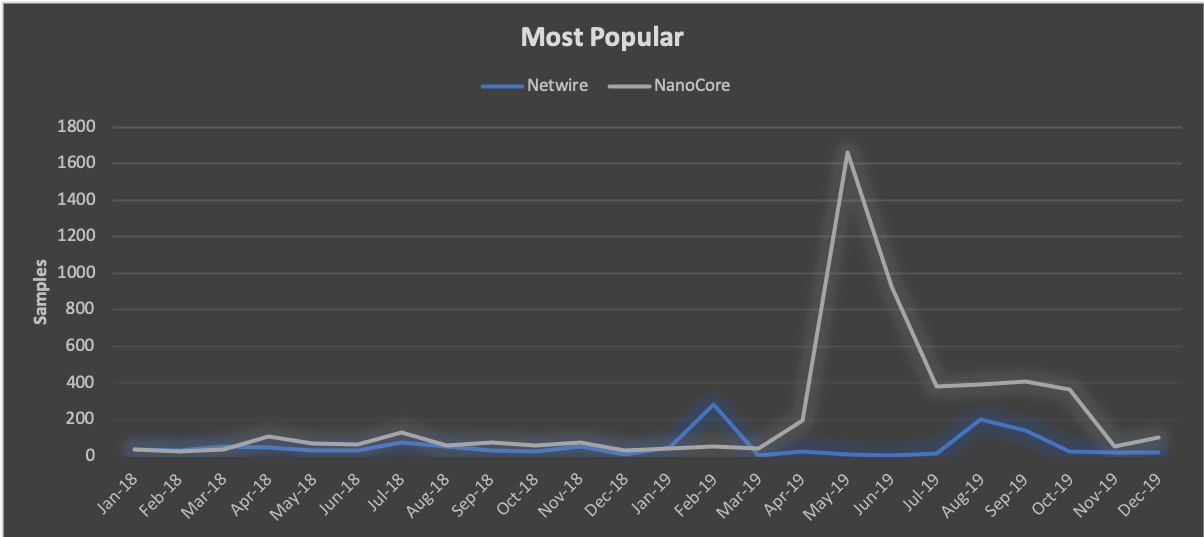
The most popular RATs have narrowed in 2019. In 2018, there were six tools that exceeded averages of 50 samples per month, while in 2019 that number dropped to just two. The most popular was NanoCore, with an average of 384 samples per month, signaling a 520% increase. This result remains particularly fascinating because the tool developer was arrested in 2017. Yet, despite his initial incarceration, a “cracked” version of the tool remains freely available, and given its effectiveness, it has become the “tool du jour”. The second most popular tool in 2019 was Netwire in which we observed an average of 64 samples per month. While SilverTerrier actors have used this tool since 2014, it remains popular due to a small, but loyal, following of actors.
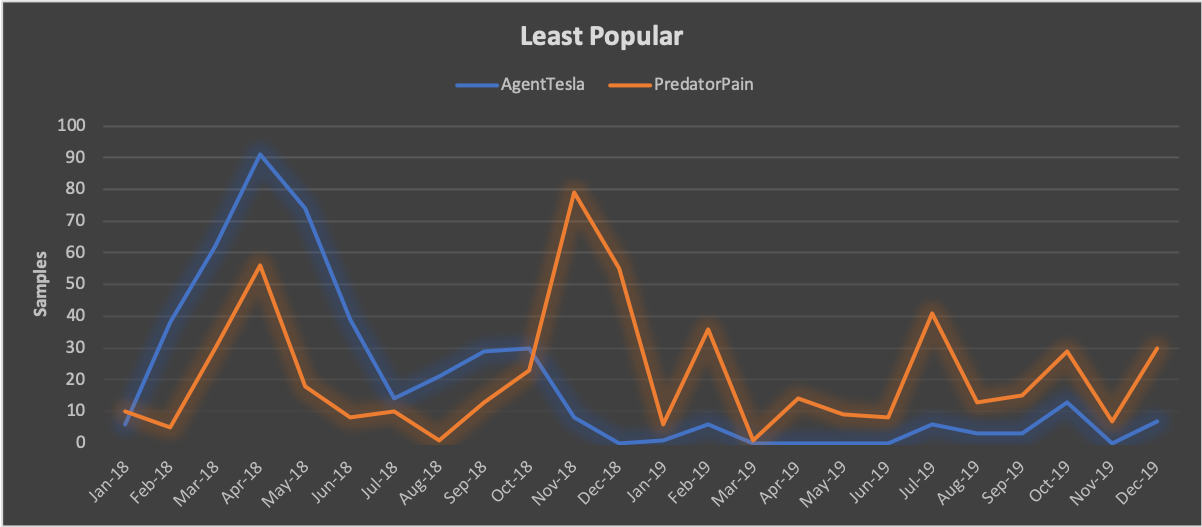
In contrast, we found seven RATs in active use with stalled adoption and minimal deployment throughout 2019. Of the seven, Remcos, first seen in 2016, and DarkComet, first seen in 2014, stood out as the only two to maintain relatively stable sample rates. The average sample rate for Remcos was 42 samples per month, while DarkComet’s was 24 samples per month.
Conversely, usage of Adwind, Revenge, and ImminentMonitor all declined over the course of the year, with sample rates of 36, 6, and 5 samples per month, respectively. Of note, Palo Alto Networks also identified the developers behind Adwind and ImminentMonitor, and collaborated with international law enforcement to subsequently dismantle global ImminentMonitor infrastructure.
Finally, the connection between HWorm and WSHRat is noteworthy. The code for HWorm, originally released in 2013, has been repackaged with several tools over the years. However, while SilverTerrier usage was first observed in March 2018, HWorm usage was brief. The tool peaked in November 2018 before declining through April 2019, with an average of only 12 samples per month. Coincidently, samples of WSHRat, which we assess to be a Nigerian variant of HWorm, began to appear that same month (April 2019), and continued throughout the year resulting in an average of 33 samples per month.
Attribution
In 2014, Unit 42 published its first research identifying a small group of Nigerian threat actors employing malware for financial gain. Over the past five years, the number of actors involved in this activity has grown substantially. As of this publication, we have attributed attacks to more than 480 Nigerian threat actors and groups. Combined, these actors have registered more than 23,300 fraudulent and malicious domains. Many of these domains have directly supported command and control (C2) activities for the roughly 81,300 samples of malware associated with 2.1 million attacks against our customer base.
Focusing on the actors themselves, we have found that corporate network security teams traditionally tend to explain threats to their respective organizations in terms of capabilities and vulnerabilities, while often discounting the perpetrating actors as elusive, amorphous, and faceless adversaries. This habit forms naturally due to the plethora of difficulties associated with attributing APT level and ransomware activities to specific individuals with unique motivations. However, in the world of cybercrime, attribution is often easier to achieve and as such, details about SilverTerrier attackers are within grasp. Thus, in seeking to enable network defenders and more importantly, their corporate employees, to better understand and defend against this threat, we believe there is value in providing a deep dive into a profile of a typical SilverTerrier actor. Additionally, we provide a description of the first Nigerian commodity tool developer in order to better illuminate the fundamental human nature and motivations of this threat.
Malware Actor
Actor X is an actual person and is one of the more active SilverTerrier actors that we track. He holds an undergraduate degree from the Federal University of Technology in Owerri (FUTO). Following graduation, he completed a year of national service with the National Youth Service Corps in Nigeria. Now in his early 40’s, he is married and the proud parent of three children. Together, they live in Owerri, Nigeria, where he appears to be active in the community and presents himself as a legitimate businessman, providing technical services. Additionally, like many threat actors, he maintains accounts on Facebook and Skype, in which his contacts include friends, family, other malware actors, local law enforcement, and prominent figures from his community.
In terms of online activity, Actor X has registered more than 480 domains for the purpose of supporting other threat actors, as well as his own fraudulent activities. In order to register these domains, he has built over 90 email accounts with common email providers such as Microsoft, Yahoo, and Google. While these accounts all follow a pattern of using an alias or nickname followed by a number, his platform diversification strategy guarantees a degree of redundancy should one of the providers take action to close these accounts.
Finally, as it applies to his illicit activity, this single threat actor has produced more than 4,000 samples of malware. These samples are associated with 15 different malware families that he has experimented with over time, as his skills have improved from novice to advanced. Combined, we have observed these samples in over 363K mostly automated attacks against our customers. In doing so, we assess that his attack technique is largely indiscriminate, as he has targeted over 2,600 customers including 93 local, state, and federal government entities across 31 states.
Combining all of these characteristics empowers a refined understanding of the threat targeting our customers. Specifically, the adversary is a person (not a vulnerability or piece of software) who has a technical college education, has put in the time to develop a web of online aliases required for his campaigns, and is following a strategy of deploying malware indiscriminately, and at scale, with the motivation of generating the income necessary to support his family.
Tool Developer
In January 2018, an unknown developer began advertising a new tool called “FUD Crypt” on the popular hacking website HackForums[.]net. Priced at $65 a month, the developer also posted a tutorial on YouTube, demonstrating how to use his new cryptor to make RATs, keyloggers, and other malware files undetectable to antivirus solutions. Eleven months later, in December 2018, a second tool called “Unknown Crypter” hit the market in a similar fashion with similar capabilities. Priced at $20 a week, this tool also came with a YouTube tutorial. Common amongst both tutorials was the fact that the developer took the time to provide credit to the source of the royalty-free music used in each video.
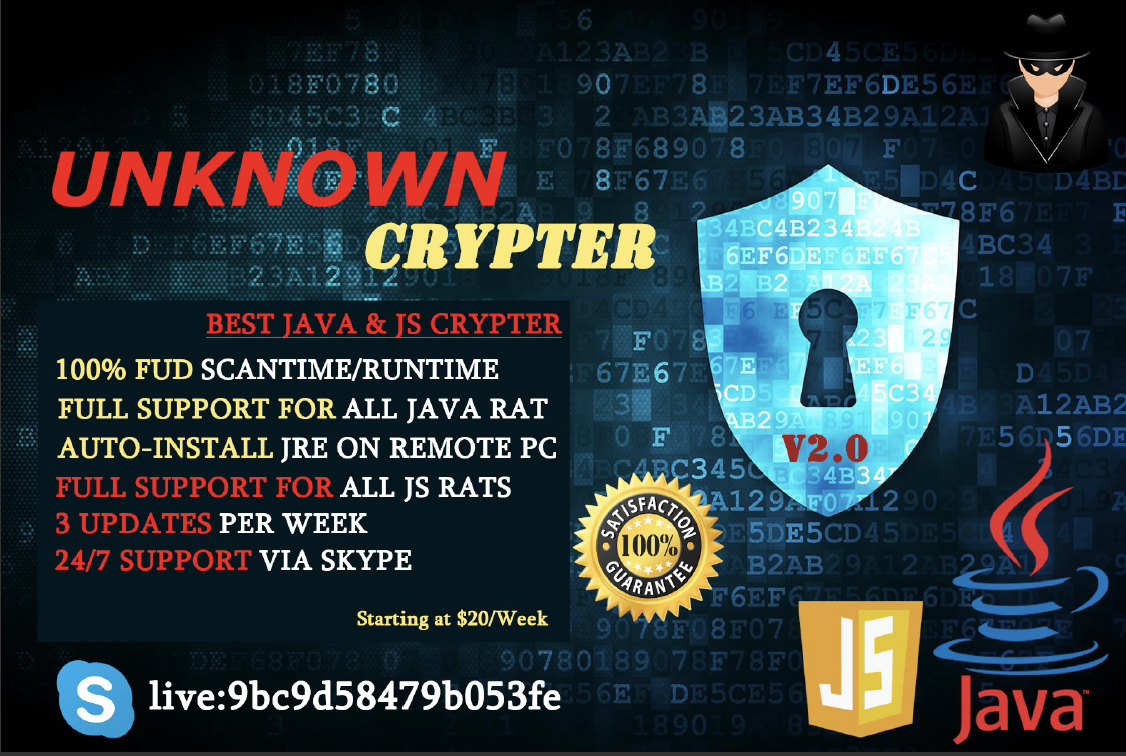
Following the release of both of these tools, in April 2019, we saw a new variant of HWorm RAT hit the market in VBScript and JavaScript languages packaged as “WSHRat”. Priced at $24 a month, this tool once again came with its very own YouTube tutorial that, like the previous two, provided credit for its music.
So beyond citing music sources in the video tutorials, what do these three tools have in common? Beginning in January 2019, an independent researcher set out to answer that question. Over a series of five blogs, the researcher documented his findings which link all three of these tools to the same developer. Taking that analysis one step further and expanding beyond the commonalities of the code to the attribution of the developer, Unit 42 found that the FudCrypt[.]com website contained Nigerian registration details. Additionally, the email address used for the domain registration also resolved to a Skype account belonging to a Nigerian individual.
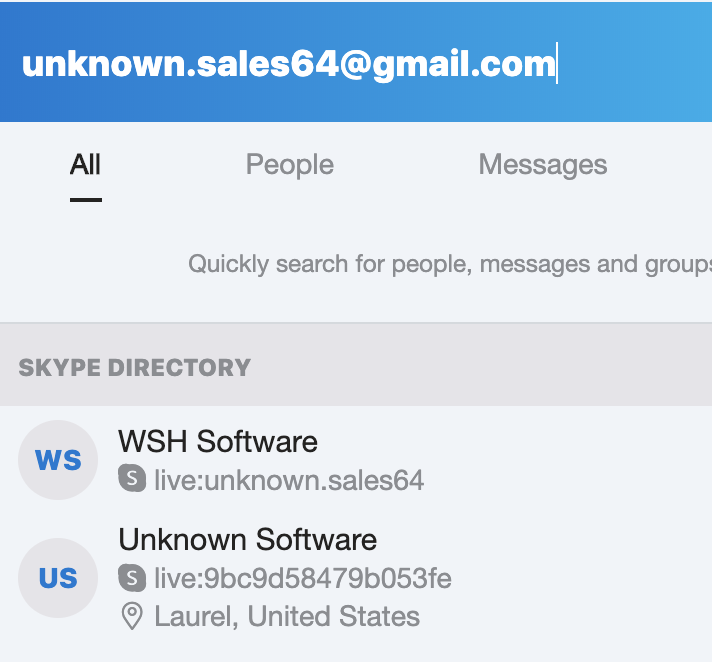
Looking into UnknownCrypter, we found two items of interest on the desktop of the tutorial video. The first was a folder that contained the same name as the aforementioned Skype account, while the second was a file named “Fudcrypt edited.zip.” Meanwhile, on the Skype account referenced in the UnknownCrypter advertisements, we discovered that the same Gmail account linked both the Unknown Software and WSH Software accounts. Pivoting on this email address further revealed four dynamic DNS domains that were all registered using a Nigerian IP address to support WSHRat infrastructure.
In taking a deeper look at WSHRat, we found that the sales website WSHSoftware[.]site contained the same Nigerian registration address, phone number, and email address as FudCrypt[.]com. Pivoting further off of the email address led to a Facebook profile of a college-educated individual in his mid-30’s who serves as both the co-founder and CEO of two software companies. Furthermore, in January 2019, this individual just happened to be advertising for assistance on a Java development project at a time when the Java-based UnknownCrypter was being sold, and WSHRat was likely under development.
We find the implications of this development to be significant in that they speak directly to the evolution and maturity of the SilverTerrier threat. While 2014 may mark the first documented case of Nigerians using malware for financial gain, this attribution demonstrates that it has taken less than five years for the threat to evolve from “script kiddie” status, to commodity malware cybercriminals, to developers of their own native capabilities with the ability to market and sell their tools globally. Regardless of the effectiveness of these tools, one should regard this development activity to be a significant and alarming step forward for a threat group that consistently launches BEC campaigns with a sense of impunity.
Empowering Law Enforcement
Over the past few years, Palo Alto Networks has launched several initiatives to combat this ongoing threat. We’ve actively worked to support domestic and international law enforcement in their efforts to curb SilverTerrier, as well as combat broader BEC activity and malicious tool usage on behalf of our customers.
Highlights include:
-
- June 2018 - The United States Department of Justice (DOJ) announced Operation WireWire, in which 74 individuals globally, including 29 Nigerians, were arrested for their involvement in BEC schemes.
- October 2018 - The United States DOJ sentenced the developer of LuminosityLink RAT to 30 months in prison for computer intrusion crimes.
- September 2019 - Unit 42 traced the development of Adwind RAT to an individual in Mexico. Additionally, the United States DOJ announced Operation ReWired, in which 281 individuals globally, including 167 Nigerians, were arrested for their involvement in BEC schemes.
- November 2019 - The Australian Federal Police (AFP), with international activity coordinated by Europol, arrested the developer as well as the most prolific users of ImminentMonitor RAT.
- December 2019 - The Canadian Radio-television and Telecommunications Commission (CRTC) issued $115,000 in fines to the developers of Orcus RAT.
Conclusion
As 2020 progresses, the most prominent threat facing customers is commodity malware deployed in support of sophisticated BEC schemes. With the emergence of the first Nigerian commodity tool developer, growing adoption of RATs amongst SilverTerrier actors, and an observed 172% increase in attacks in 2019, this threat shows no signs of slowing down. As a result, we strongly encourage network defense teams across all industry verticals to take note of these trends and ensure staff receive the training necessary to identify and eradicate the most popular tools employed by this threat group.
Additionally, while our analysts and engineers remain actively engaged in tracking and developing novel countermeasures to protect against this threat, Palo Alto Networks customers benefit from the following:
| Cortex XDR protects endpoints from all malware, exploits and fileless attacks associated with SilverTerrier actors. | |
 |
WildFire® cloud-based threat analysis service accurately identifies samples associated with these malware families. |
 |
Threat Prevention provides protection against the known client and server-side vulnerability exploits, malware, and command and control infrastructure used by these actors. |
 |
URL Filtering identifies all phishing and malware domains associated with these actors and proactively flags new infrastructure associated with these actors before it is weaponized. |
 |
Users of AutoFocus™ contextual threat intelligence service can view malware associated with these attacks using the following tags: |
Indicators of Compromise
A complete list of the malware domains associated with SilverTerrier actors is available on GitHub.
Palo Alto Networks has shared our findings, including file samples and indicators of compromise, in this report with our fellow Cyber Threat Alliance members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. For more information on the Cyber Threat Alliance, visit www.cyberthreatalliance.org.
Additional Resources:
- SilverTerrier: 2018 Nigerian Business Email Compromise Update
- SilverTerrier: The Rise of Nigerian Business Email Compromise
- SilverTerrier: The Next Evolution in Nigerian Cybercrime
- 419 Evolution












 Get updates from Unit 42
Get updates from Unit 42