Executive Summary
Threat actors frequently exploit trending events like global sporting championships to launch attacks, including phishing and scams. Because of this, proactive monitoring of event-related domain abuse is crucial for cybersecurity teams.
Our network abuse investigations regularly uncover suspicious domain registration campaigns, particularly those using event-specific keywords or phrases in newly registered domains. These campaigns often surge around notable events.
Our analysis of event-related abuse focuses on the following trends:
- Domain registrations
- DNS traffic
- URL traffic
- Most active domains
- Verdict change requests
- Domain textual patterns
Our example case studies include observations related to the 2024 Summer Olympics in Paris.
Palo Alto Networks customers are better protected against various network threats leveraging terminology associated with the current trending events through cloud-delivered security services such as Advanced DNS Security, Advanced URL Filtering and Advanced WildFire. If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response Team.
| Related Unit 42 Topics | Cybersquatting, ChatGPT |
Domain Registration for High-Profile Events
High-profile global events, including sporting championships and product launches, attract cybercriminals seeking to exploit public interest. These criminals register deceptive domains mimicking official websites to sell counterfeit merchandise and offer fraudulent services. These sites can reach millions of people searching for event-related information or resources.
For instance, during the COVID-19 pandemic, adversaries launched many campaigns exploiting the crisis to spread malware. We reported that attackers launched COVID-19-themed phishing campaigns targeting government and medical organizations or distributed Coronavirus-themed malware by tricking users into downloading malicious files.
Similarly, the rise of ChatGPT provided another opportunity for exploitation such as the scam attacks exploiting interest in ChatGPT. Attackers promoted fake ChatGPT tools or services through fraudulent domains, often luring victims with promises of early access or exclusive features, only to steal their credentials or spread malware. These examples expose how opportunistic threat actors are during significant global events.
To mitigate the risks posed by these malicious campaigns, it is critical for defenders to proactively monitor the network abuse trends related to specific events.
Metrics to Watch in Cases of Network Abuse
Threat actors exploiting high-profile events often leave telltale signs in specific metrics. Defenders should monitor the following for suspicious activity:
- Domain registrations
- Textual patterns used in deceptive domains
- Questionable DNS traffic trends
- Abnormal URL patterns
Further analysis of the most active domains and trends in verdict change requests can also provide valuable insights.
Domain Registration Trends
When malicious actors pick trending topics to exploit, one of their first moves is to register domains with relevant keywords. Therefore, to deep dive into specific event-related cyberthreats, we analyze the historical newly registered domains (NRDs) containing event-specific keywords.
We detect over 200,000 newly registered domains (NRDs) daily from sources like zone files, WHOIS databases and passive DNS. Our analysis begins by establishing the average daily domain registrations related to the target event.
We then highlight those registrations flagged as suspicious. We label domains as suspicious if they are linked to activities like command and control (C2), ransomware, malware, phishing or grayware.
Domain Textual Patterns
Understanding domain textual patterns is crucial in identifying deceptive domains. By analyzing the keywords, structure and even top-level domain (TLD) cues within these domains, we can uncover common features that indicate malicious intent. For example, many phishing domains combine event-specific keywords with suspicious terms like “rewards” to lure unsuspecting visitors.
We investigate the textual patterns of these newly registered domains so that for each keyword analyzed, we can present the number of domains containing that keyword along with the ratio of suspicious domains. We also compare the TLDs used by both suspicious and overall NRDs to analyze which TLDs are appealing to attackers.
DNS Traffic Trends
DNS traffic trends can provide valuable insight into the behavior of internet users and the strategies employed by attackers. Anomalies in DNS traffic, such as spikes in requests for specific domains, could indicate unusual activities like C2 communications.
We present both total and suspicious DNS traffic trends, which include notable increases, significant spikes and changes in the ratio of suspicious DNS traffic. Our reports are able to reveal how attackers behave during key dates in relation to current events.
URL Traffic Trends
We further analyze event-related NRDs through URL traffic. This illustrates the URL traffic trends for both overall and suspicious NRDs, along with the suspicious traffic ratio and significant spikes during current events. This trend can indicate the strategies attackers use to exploit event topics, particularly regarding visits to phishing websites.
Most Active Domain Trends
For DNS traffic and URL traffic, we analyze the trends of the top 10 domains most frequently visited over a specific period, if we note any interesting findings. This analysis can reveal shifts in visitor interest or point out potential emerging threats as new domains gain popularity.
Change Request Trends
Change request trends refer to the frequency and volume of requests to recategorize domains in our Palo Alto Networks URL testing system Test-A-Site. These requests include false-positive changes and false-negative changes. Sudden events, such as unexpected incidents, can trigger a surge in change requests within a short time frame.
Conclusion
High-profile events are prime targets for threat actors, where they frequently exploit public interest through deceptive domains, phishing and malicious traffic. By monitoring key metrics like domain registrations, textual patterns, DNS anomalies and change request trends, security teams can identify and mitigate threats early. Proactive analysis of these trends provides valuable intelligence, assisting organizations to block malicious domains and defend against opportunistic scams.
Palo Alto Networks customers are better protected from the threats discussed in this article through the following products:
- Next-Generation Firewall with cloud-delivered security services including Advanced DNS Security and Advanced URL Filtering.
- Advanced WildFire is a cloud-based threat detection engine that detects the malware.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Case Studies: Network Abuses Observed in Connection with High-Profile Events
Abuses Related to the Olympic Games in Paris 2024
Domain Registration Trends for the Paris Olympics
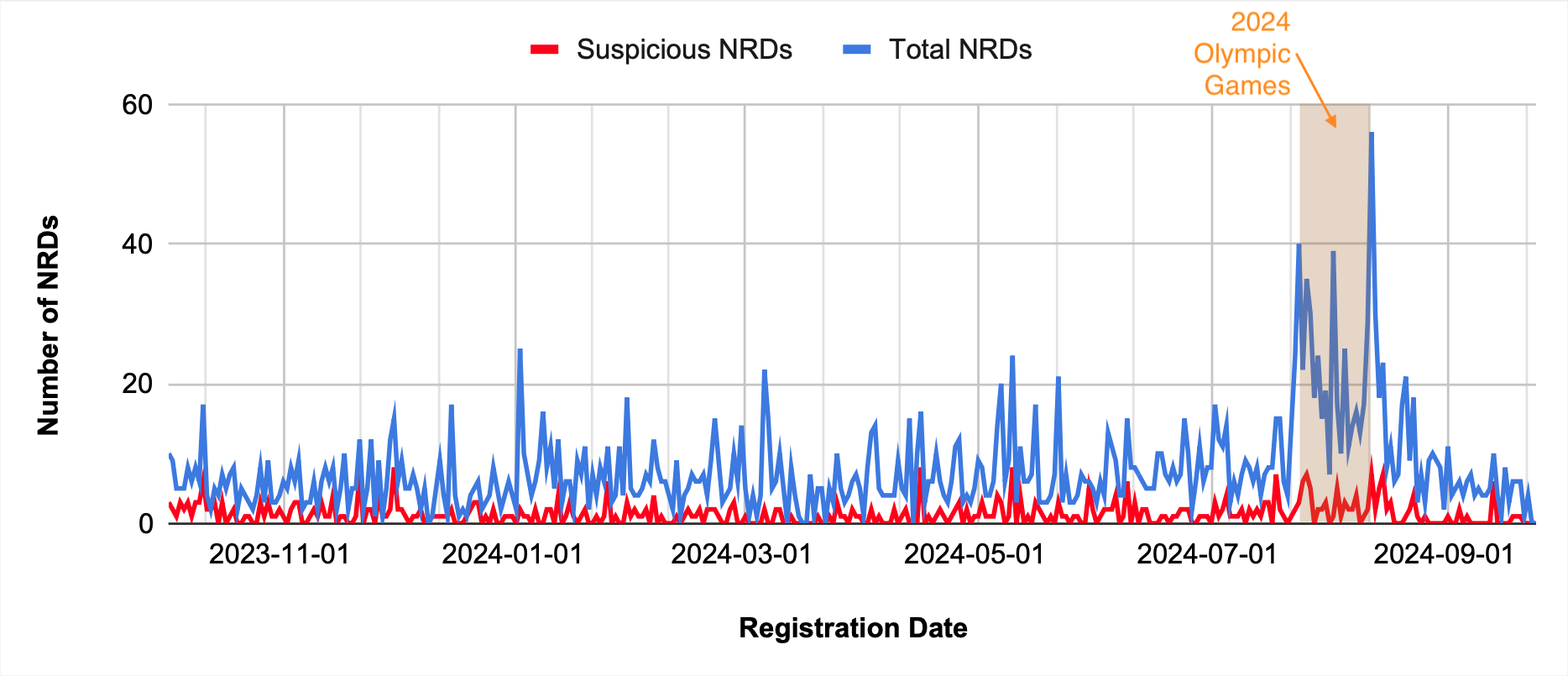
In the one year period from October 2023 through September 2024, we saw an average of seven Olympic-related domains registered daily. However, we noted a significant rise in domain registrations during the event weeks noted in Figure 1.
Specifically, Olympic-related registrations tripled compared to normal periods. Surprisingly, we deemed 16% of these domains suspicious – 13 times higher than the general rate for NRDs based on our previous research. This indicates how intensely threat actors exploited interest in the Olympics, and it highlights the critical need for ongoing threat monitoring.
Significantly, during the opening ceremony week, the number of suspicious domains doubled. On the day of the opening ceremony on July 26, 2024, we detected 20% of all newly registered domains with Olympic keywords as suspicious. This surge reflects attackers capitalizing on high-traffic events.
Domain Textual Patterns Leveraging the Olympic Games
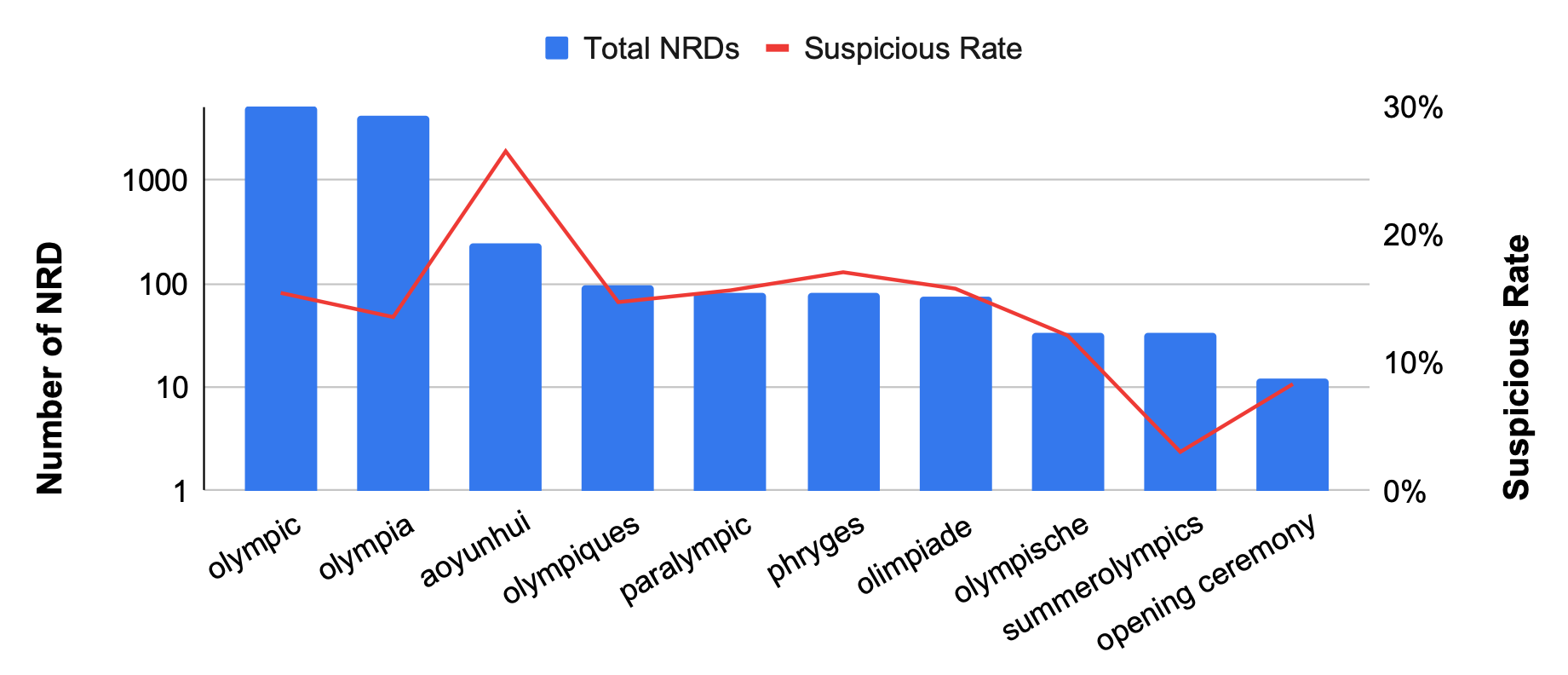
Figure 2 showcases the top 10 most commonly used keywords and their associated suspicious rate. Unsurprisingly, 98% of these domains leverage variations of the word “Olympic,” including translations in multiple languages.
The most heavily abused keyword was “aoyunhui” – the Chinese pinyin-based romanization term for “Olympic Games.” 27% of domains containing this term were flagged as suspicious.
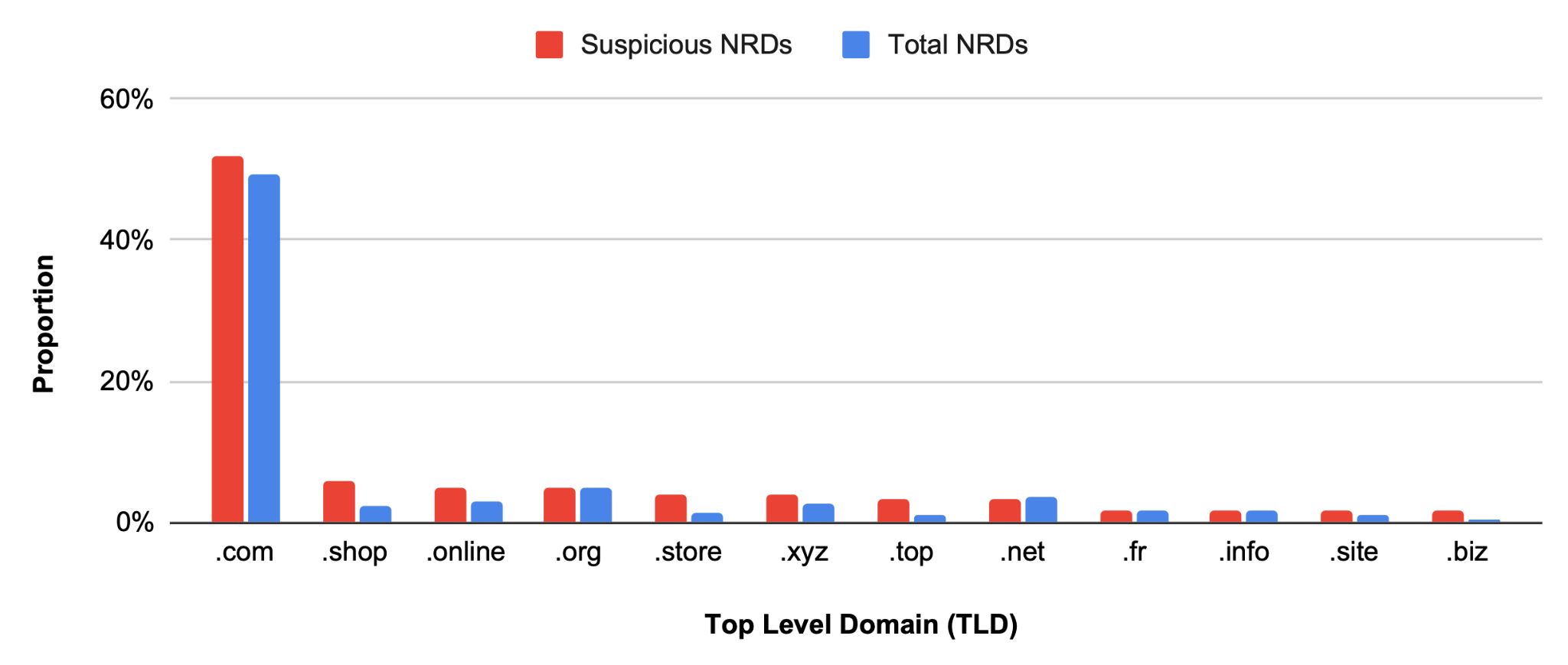
Figure 3 shows .com is the most commonly used TLD among suspicious NRDs, accounting for 52% of the total. Threat actors use shopping-oriented TLDs such as .shop and .store to create fake e-commerce websites to deceive victims. In addition, other TLDs such as .online, .xyz, .top and .biz also show a higher rate of abuse by suspicious NRDs compared to their general usage.
DNS Traffic Trends Leading Up to the 2024 Olympics
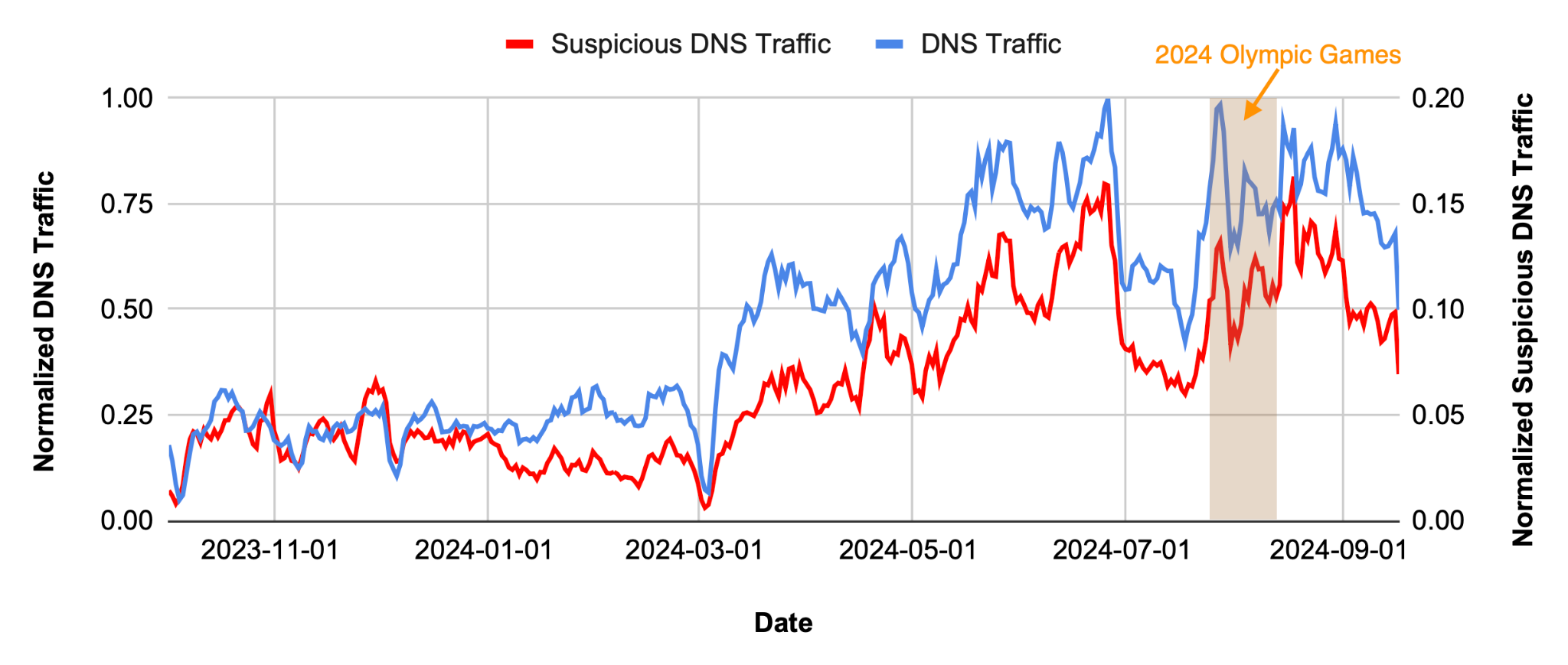
Figure 4 illustrates DNS traffic for Olympic-related NRDs began to rise during March 2024, coinciding with the release of Olympic posters and various event preparations. Alongside this overall increase in Olympic-related DNS traffic, we see a corresponding increase of suspicious DNS traffic.
During the 2024 Olympic Games event, the malicious DNS traffic ratio fluctuated between 10-15%. Spikes in malicious DNS traffic occurred around key dates, such as the 100-day countdown on April 20 and the opening ceremony on July 26.
URL Traffic Trends for the Paris Olympics
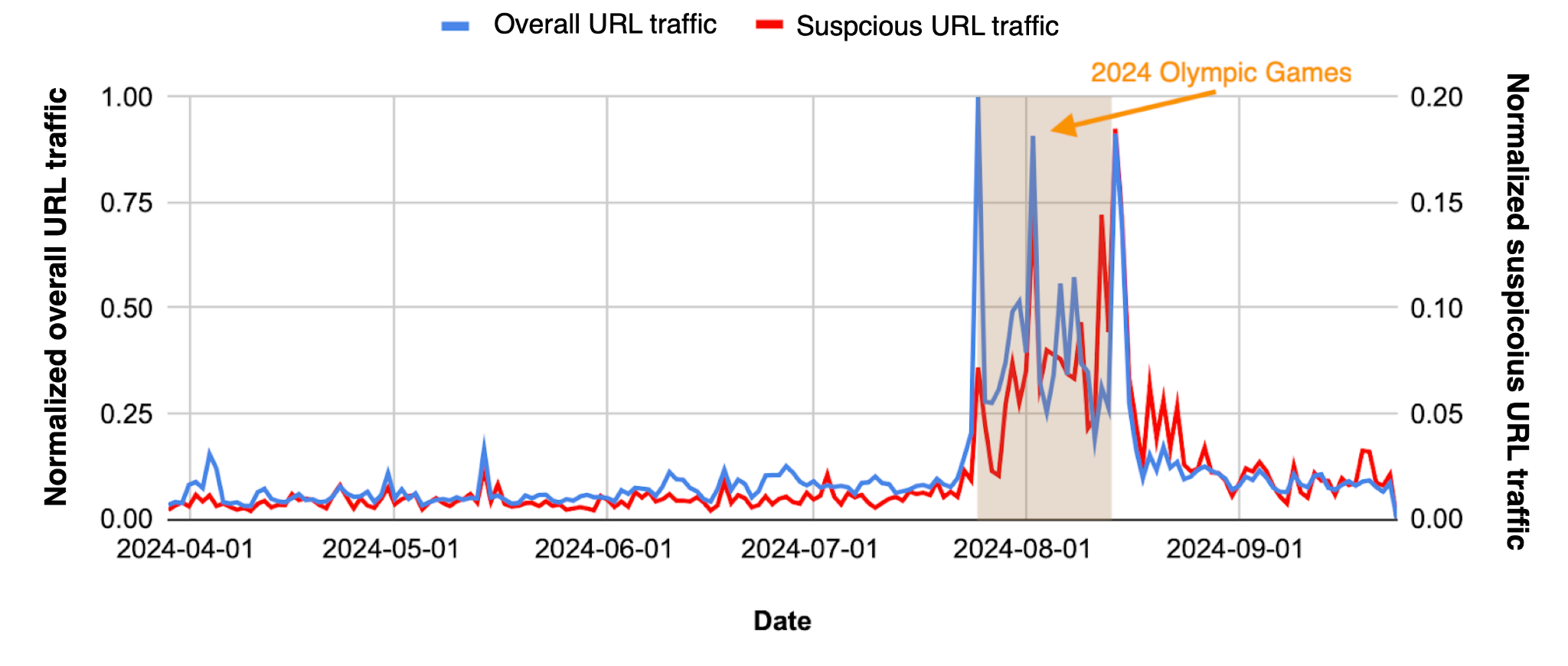
As Figure 5 shows, in the months leading up to the event, Olympic-related URLs were initially negligible. However, the amount jumps to concerning levels during the event, with the highest level on Aug. 2, 2024. At that point, 16.2% of all Olympic-related URLs were flagged as suspicious. Other significant suspicious spikes occur on August 12 (the closing ceremony) and August 14, during the final week of the games.
Specific Case Studies
(1) Persistent Network Threat Actor for Two Separate Olympics
For this case study, we investigated 23 specific Olympic-related domains from both the Tokyo Olympics held in 2021 and the 2024 Paris Olympics. Despite being registered and active at different times, our analysis reveals a strong correlation among these domains.
First, the domains exhibited similar naming conventions, using a consistent set of keywords such as live, tickets and games, along with the specific years and locations of the Olympic Games.
Second, we observed a significant overlap in the resolved IP addresses of these domains, as illustrated in Figure 6 below.
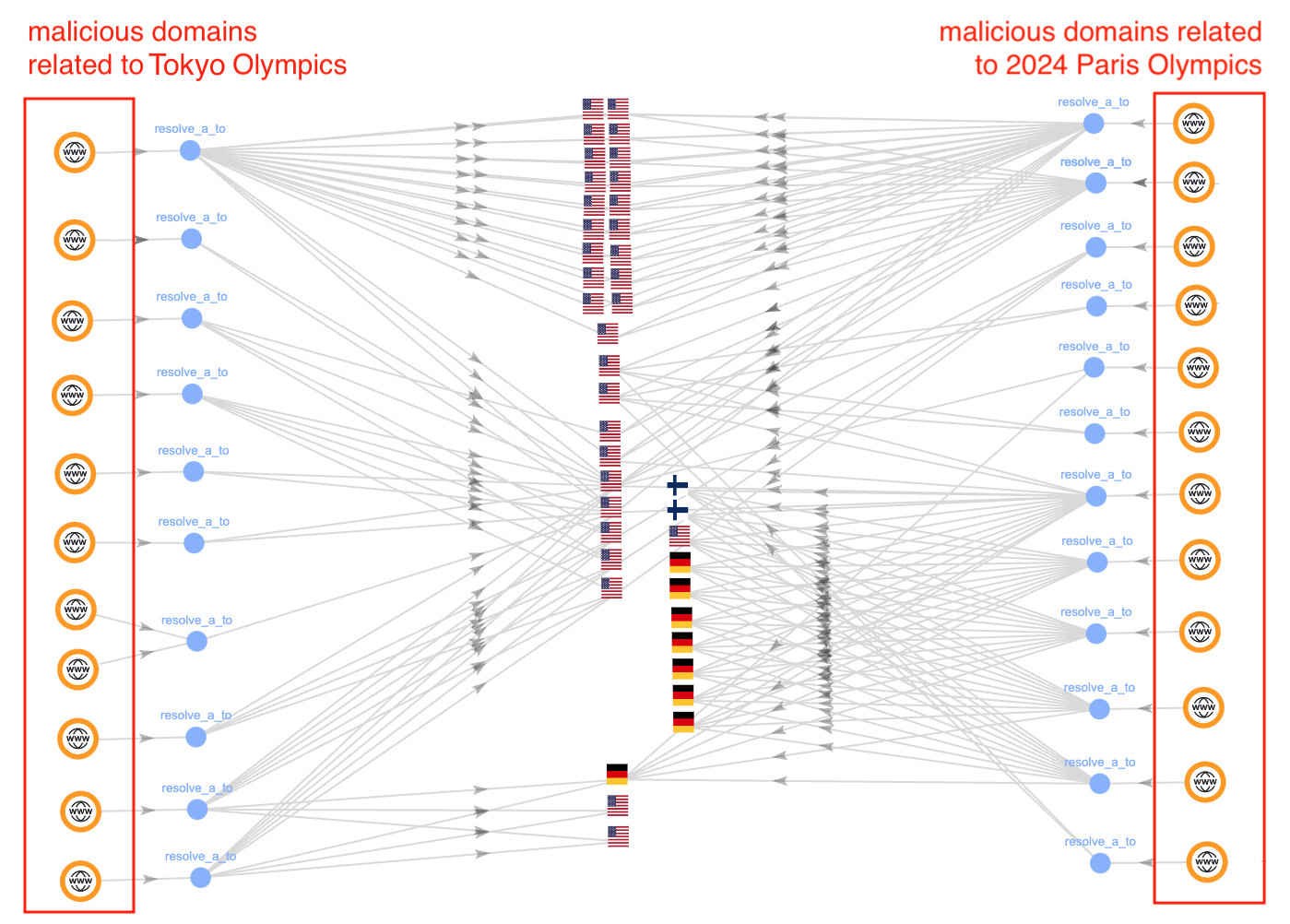
For instance, the IP address 3.64.163[.]50 was shared by domains from 2021 (e.g., 2021olympicupdateslive[.]com) and those from 2024 (e.g., parisolympicgames2024[.]com).
In addition, multiple domains from both Olympic events resolved to 76.223.67[.]189. This included domains targeting previous Olympics (e.g., tokyoolympicsport[.]com) and the 2024 Olympics (e.g., 2024olympicslive[.]com).
From the observed infrastructure patterns, we infer that a single malicious actor is behind this persistent network abuse.
(2) Scams Leveraging Paris Olympics
We identified several scam campaigns exploiting the 2024 Paris Olympics, ranging from fake ticket sales to fraudulent internet data giveaways and fake cryptocurrency investment schemes. This section focuses on the latter two scam campaigns.
Threat actors distributed the scam for fraudulent Paris Olympic internet data giveaways through a large number of domains. Figure 7 shows screenshots from an example that enticed victims by offering 48 GB of free internet data.
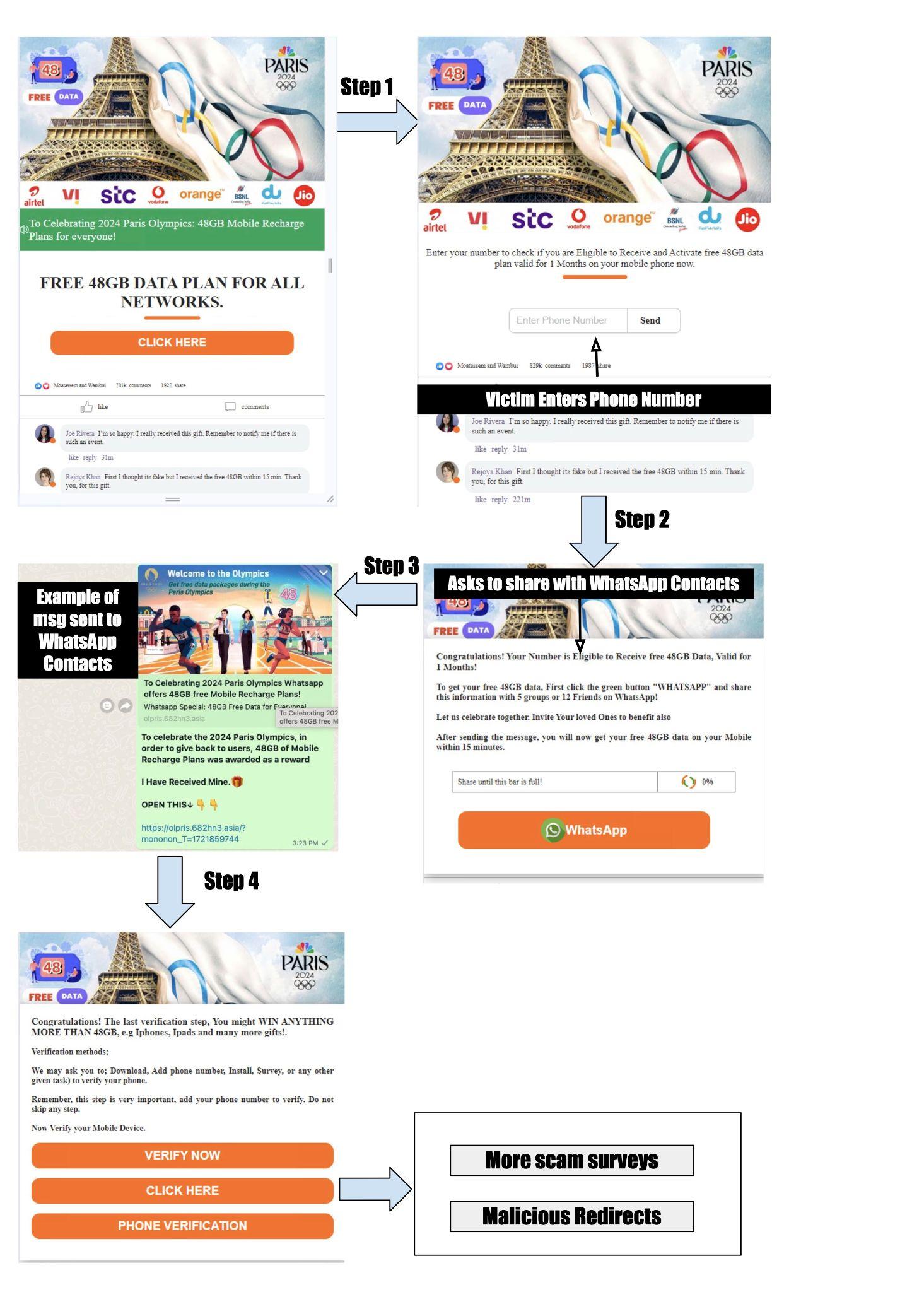
To claim the data, victims were prompted to enter their phone numbers and share the scam with their WhatsApp friends/groups. The final confirmation page offers additional scam surveys or malicious redirects.
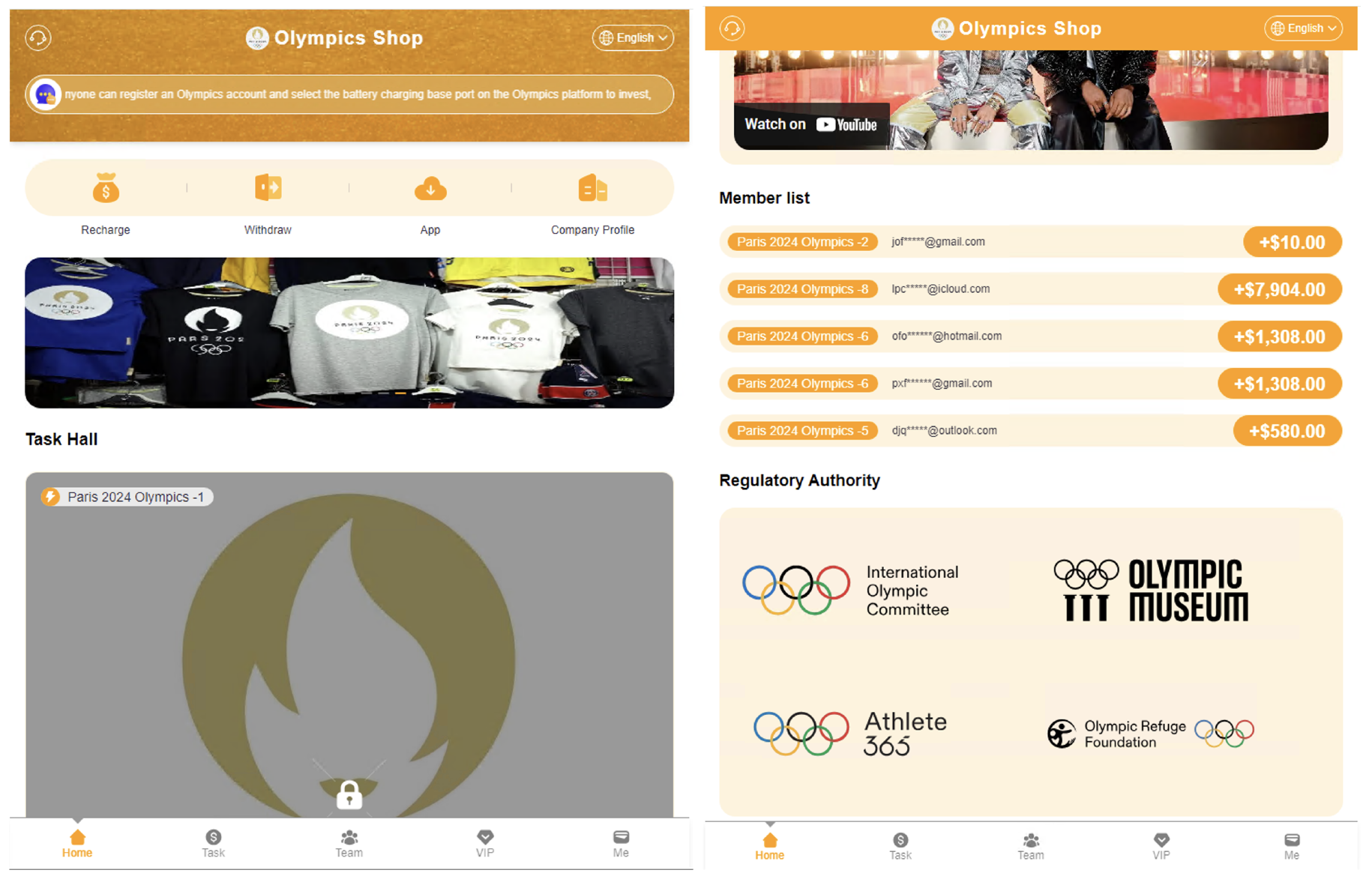
In another scam, threat actors capitalized on the Olympics to promote a fake cryptocurrency investment. Figure 8 shows two screenshots from the landing page of 2024olympics-shop[.]com that tricked visitors into registering for a bogus investment opportunity. The site also offers a download link for an Android app named Olympics[.]apk that poses as a legitimate cash app, but it is actually suspicious and likely intended to defraud people.
(3) Malicious Gambling
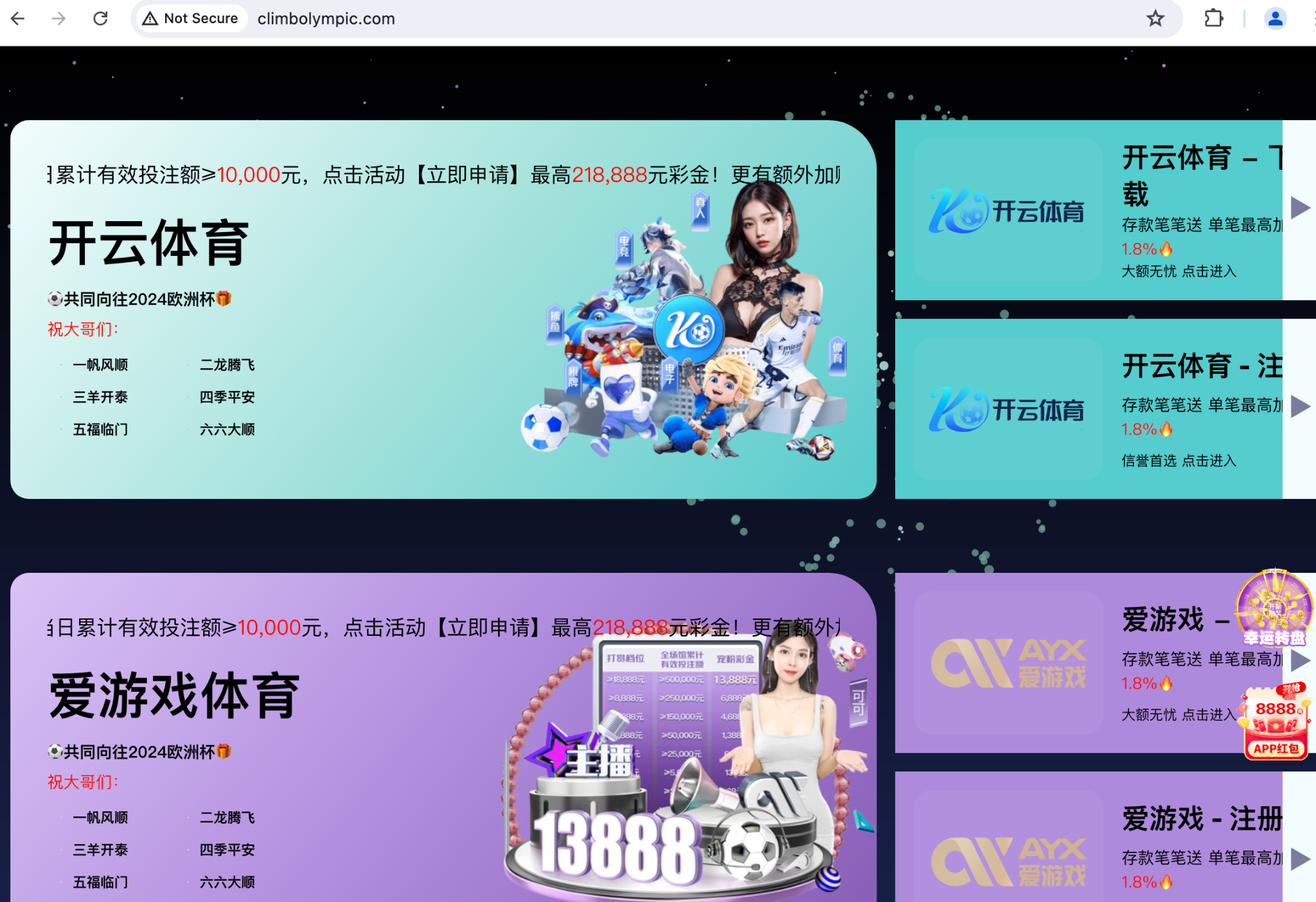
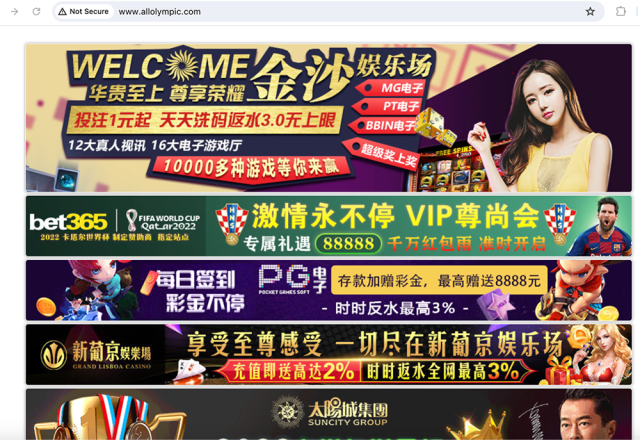
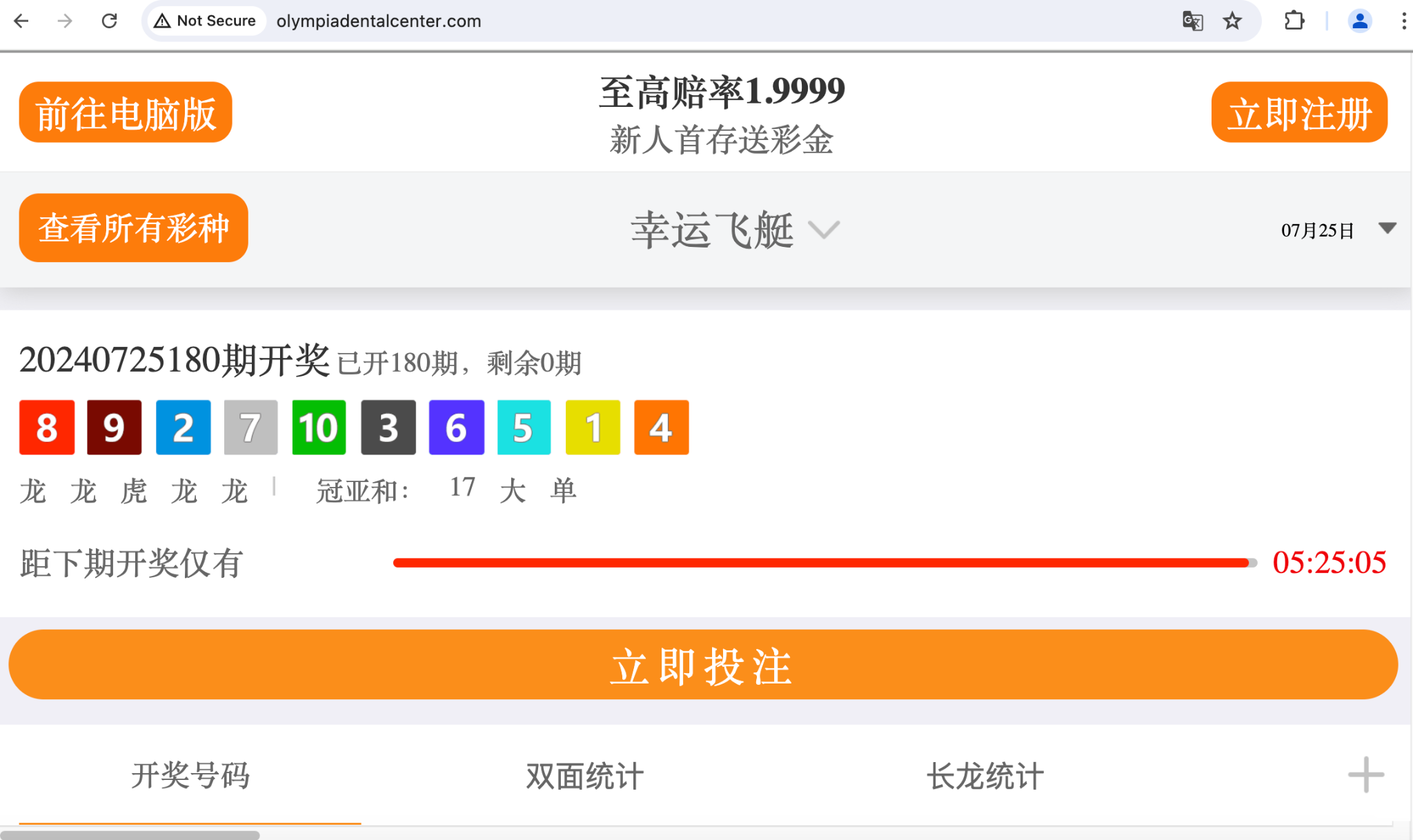
We identified a campaign involving malicious gambling websites that exploited Olympic-related keywords to lure unsuspecting victims. These websites share several key characteristics:
- Name servers: All gambling domains are resolved by the same DNS hosting service (share-dns), suggesting a potential connection between the operators.
- WHOIS records: While most registration information for these Olympic-themed gambling NRDs is redacted, we observed that all registrant locations are listed as different provinces in China.
- Website templates: The adversaries use various templates for gambling websites. Figures 9-11 showcase examples of gambling websites built with distinct templates within this campaign.
Indicators of Compromise
Suspicious Domains From Persistent Olympic Targeting Threat
- 2024olympicslive[.]com
- 2024parisolympicathletes[.]com
- olympicparis2024[.]com
- paris-olympics2024[.]com
- paris24olympics[.]com
- parisolympic24[.]com
- parisolympicgames2024[.]com
- parisolympicgames2024official[.]com
- parisolympicgamesevents[.]com
- parisolympicgamesofficial[.]com
- parisolympicgamestickets[.]com
- parisolympicsphotographe[.]com
- parisolympictickets[.]com
Scam Domains Leveraging Olympics
- 2024olympics-shop[.]com
Malicious Gambling Domains
- climbolympic[.]com
- allolympic[.]com
- olympiarealestate-online[.]com
Additional Resources
- Newly Registered Domains: Malicious Abuse by Bad Actors – Unit 42, Palo Alto Networks
- Malicious Attackers Target Government and Medical Organizations With COVID-19 Themed Phishing Campaigns – Unit 42, Palo Alto Networks
- Studying How Cybercriminals Prey on the COVID-19 Pandemic – Unit 42, Palo Alto Networks
- ChatGPT-Themed Scam Attacks Are on the Rise – Unit 42, Palo Alto Networks
- 2024olympics.shop Scam Store: The Olympic Shop Scam – Malwaretips
- Paris 2024 : 338 sites internet frauduleux de revente de billets recensés à quelques semaines du début de la compétition – Franceinfo
- Security Brief: Scammers Create Fraudulent Olympics Ticketing Websites – Proofpoint
- Olympics-related domains used for phishing and scams for the Tokyo and Paris2024 Olympics – Unit 42 on X
- Threat actors exploit public attention in the Olympics by creating domains that seem related to the event – Unit 42 on X












 Get updates from Unit 42
Get updates from Unit 42