Spear Phishing is a specific attack technique that has become widely used in the past few years. In our new research blog “FreeMilk: A Highly Targeted Spear Phishing Campaign”, our Unit 42 research team has discovered an attack campaign that takes spear phishing targeting to the next level by hijacking in-progress email conversations. While these are not broad attacks, they represent an escalation in attacker spear phishing techniques in a way that makes it even more important than ever to have a prevention framework in place.
Standard phishing attacks are broad attacks that use general email messages to carry out the attacks. Standard phishing attacks aren’t personalized: they use very common themes or lures in a generalized way in conjunction with a large enough pool of targets. The idea is that by chance some percentage of the phishing emails will look legitimate enough to the recipient to be successful.
Basically, standard phishing attacks rely on the law of averages for its success. As such, it’s a suitable tactic when an attacker cares less about who falls for it than how many fall for it.
A good example of a generalized phishing campaign is the Blank Slate Campaign we wrote about in March 2017. This attack campaign was so generalized that the attackers didn’t even bother with any theme or lure: they simply sent blank messages with malicious attachments for the recipient to open.
Spear phishing is a more refined and focused version of phishing. Instead of using generalized themes or lures, spear phishing uses themes or lures that are in some way relevant or appropriate for the target recipient. For example, a spear phishing attack could use email messages about military exercises sent to military or government targets like we saw with our recent research into CMSTAR Trojan attacks. Because the malicious email has a context for the target, he or she is more likely to trust it and open the email message and any attachments.
Spear phishing focuses on the quality of the theme and lure where standard phishing focuses on quantity. Spear phishing is a suitable tactic when an attacker cares about who falls for it. Where a phishing attack campaign may send malicious emails out to thousands or tens of thousands of targets, a spear phishing campaign my send out just one malicious email to one target. Sometimes, when that target is a high-value target this attack can also be referred to as ‘Whaling”.
In our new research, our Unit 42 research team has found an attack that takes the refining of spear phishing one step further. Rather than simply using a theme or lure that is relevant to the target, the attackers behind these attacks use an email conversation that’s in progress to carry out their attack.
You can see an image of how this works below in Figure 1.
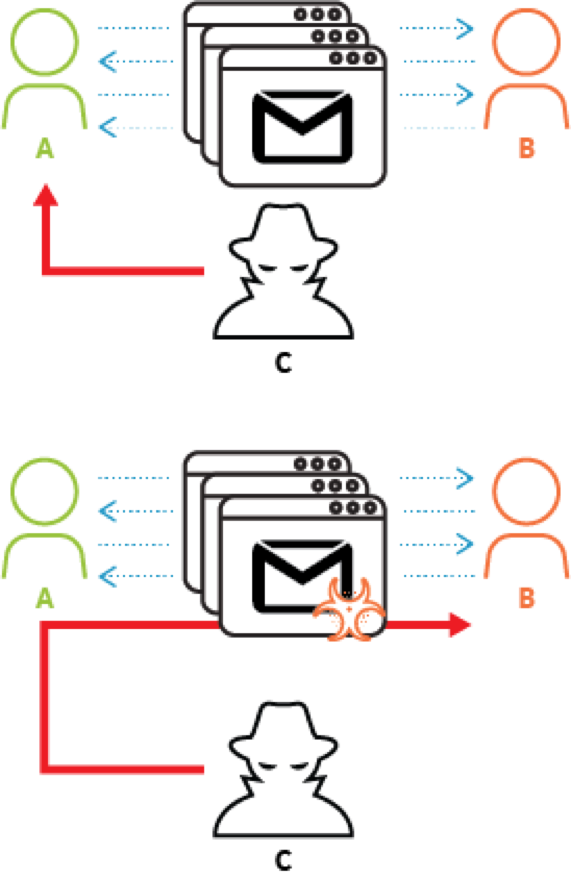
Figure 1 Conversation Hijacking to Deliver Malware
How this works is that two users, Alice (A) and Bob (B) are carrying on an email conversation. A shown in the top figure, an attacker, Charlie (C), carries out an attack that enables him to gain complete control of Alice’s email account, most likely through some form of credential theft. Once Charlie has access to Alice’s email account, he then finds email conversations between Alice and Bob, his ultimate target. When he finds one that is still in progress, he crafts a malicious attack email that seems to be relevant to the ongoing email conversation and sends it to Bob as shown in the bottom figure. If Charlie was successful in crafting the attack email to seem legitimate enough, Bob will open the email and any attachments and the attack will succeed.
Unlike phishing or even general spear phishing, this is a highly sophisticated, labor intensive, focused attack. Carrying out a successful conversation hijacking spear phishing attack requires knowing someone that the ultimate target is communicating with, compromising that person’s account, identifying an ongoing email conversation with the ultimate target, crafting an email to appear part of that ongoing email conversation and finally sending it. Even then there’s no guarantee of success since the target may somehow recognize the attack or have sufficient prevention controls in place to prevent the attack from succeeding.
Given all those points, this isn’t an attack that many of us need to worry about. But those out there who are in positions that might make them a high value target do need to be concerned about this. Whether you’re on the board of directors for an organization, a CEO/CFO/CSO, entrusted with important military or political information, are a journalist, or an activist/dissident, this is a kind of attack that you could face. And like with all targeted attacks, you don’t have to be the ultimate target of the attack campaign to be a target: this is a tactic that can be used as part of a broader attack campaign. For example, if you are the executive assistant for a CEO, you could be the target of an attack like this (“Bob” in our scenario above) so that you in turn are used to carry out an attack (“Alice” in our scenario above) against your CEO (who then becomes “Bob” in our scenario above).
Because of the nature of the attack, unless you verify each and every email you receive, it’s unlikely that you’ll necessarily be able to spot and thwart an attack. In this case, your best means of protection lies in prevention. And prevention here is really focused on two things.
First, keeping your systems and devices fully up-to-date with the latest software and security updates. The specific attack our Unit 42 research team has seen using this technique relied on an attack against a vulnerability in Microsoft Office for which a patch is available. If an attacker tried to carry this attack out against a target that was patched for this vulnerability, it would fail.
Second, using security on your systems, devices and networks that provides multiple layers of protection can help prevent attacks.
Conversation hijacking spear phishing isn’t a threat everyone faces, but for those who do it represents a significant escalation in terms of sophistication and social engineering of spear phishing attacks. It also takes spear phishing attacks to a level that makes it nearly impossible to distinguish an attack email from a legitimate email. And so technological prevention controls (patching, robust security) are even more for effective prevention.











 Get updates from Unit 42
Get updates from Unit 42