In October 2017, Palo Alto Networks Unit 42 published research showing how attackers were adapting attack techniques to generate cryptocurrency for themselves. In that research, we also showed how these attacks were very broad and grew very quickly.
At the time, we said that the sudden, surging value of cryptocurrencies was likely behind the sudden, strong rise of these new attacks. We said that if cryptocurrency values continue to remain high, we could expect to see attackers continue to focus on finding ways to carry out attacks to gain cryptocurrency, and that those attacks would continue to adapt proven attack techniques.
Unit 42 has just released new research showing that attackers are indeed continuing to adapt existing techniques to generate cryptocurrency. In our research posting “Large Scale Monero Cryptocurrency Mining Operation using XMRig” we detail a new malware campaign that is global in scale, very large in the likely number of victims and uses well established techniques to mine the Monero cryptocurrency.

Monero is a cryptocurrency similar to bitcoin but notable for its increased emphasis on providing a higher level of privacy around its transactions. Like bitcoin, Monero is generated through “mining” a computationally intensive process that provides cryptocurrency credit in exchange for computing resources provided in service to the cryptocurrency and its transaction infrastructure.
The operation that Unit 42 has recently uncovered works to deliver XMRig, software that is used to mine the Monero cryptocurrency, to victims’ systems without their knowledge or consent. While XMRig isn’t itself specifically malware, it’s being delivered using malware-delivery techniques without the user’s knowledge and consent just like malware. The attackers are doing this by using URL shorteners to make XMRig look like other, legitimate, and expected programs. This is a method attackers have used for years to deliver malware and they are using it now to get coinmining software on to people’s systems illicitly.
The attackers’ use of URL shortners enables our Unit 42 researchers to get an idea of the size, scope, and scale of this operation. And these are all notable and sobering.
First, this is a young campaign. Our research shows this operation to be only about four months old.
Second, this is a very large campaign. Our researchers can show that about one-half of the samples we found have affected 15 million people worldwide. While we can’t see how many people the other half of the samples affect, it’s a reasonable supposition that the other half of the total samples affect just as many people as the half we can see. This would mean that this operation may affect about 30 million people worldwide.
In terms of who’s been affected by this operation, again, we can only see half of those who have been affected. But what we do see shows that this is a truly global operation. This operation affected countries around the globe, but it appears that southeast Asia, northern Africa, and countries in South America were hit the most as shown below.
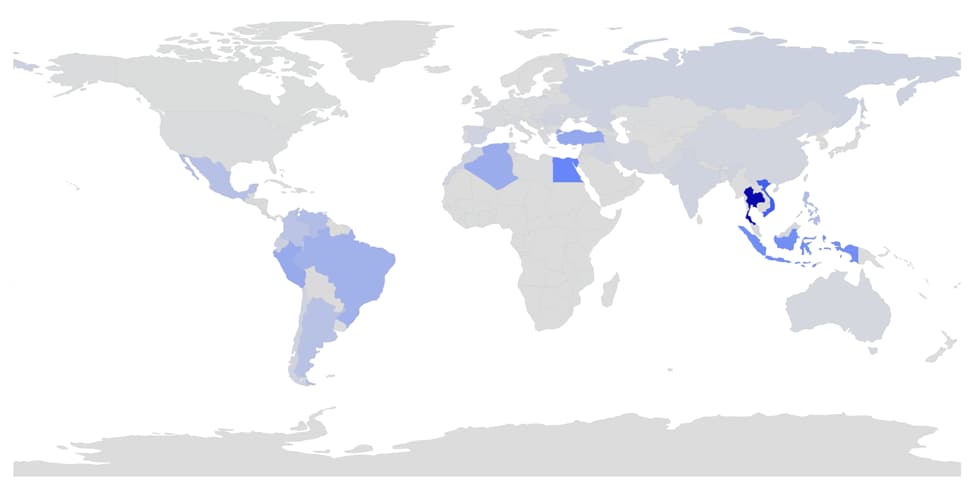
Malicious downloads by country
The specific breakout of countries affected, and their download counts are as follows:
- Thailand – 3,545,437
- Vietnam – 1,830,065
- Egypt – 1,132,863
- Indonesia – 988,163
- Turkey – 665,058
- Peru – 646,985
- Algeria – 614,870
- Brazil – 550,053
- Philippines – 406,294
- Venezuela – 400,661
Taking all those points together, this is operation is very large and clearly very effective. It shows how attackers are aggressively focusing their operations and campaigns on generating and acquiring cryptocurrency.
From a threat point of view, there are two things that are notable.
First is the fact that from an attack technique point of view, there is nothing new here. The tactics and techniques are not new or sophisticated.
Second is the fact that this operation is clearly very successful based on its size, scope, and age.
Looking at this latest operation on the continuum of evolving cryptocurrency-focused threats, it’s clear that this is an early-stage threat given its lack of sophistication and reuse of established techniques and tactics. But given how quickly and broadly successful it is, combined with the continued high value of cryptocurrencies, we can also conclude that attackers will continue to focus on cryptocurrency and likely will evolve their techniques and tactics quickly. Cryptocurrency-focused threats is a key area that all defenders should focus their intelligence and prevention efforts around in 2018.
Meanwhile, see our full research blog for full details on how attackers are distributing and using XMRig to generate Monero.











 Get updates from Unit 42
Get updates from Unit 42