Executive Summary
Cloud-based alerting systems often struggle to distinguish between normal cloud activity and targeted malicious operations by known threat actors. The difficulty doesn’t lie in an inability to identify complex alerting operations across thousands of cloud resources or in a failure to follow identity resources, the problem lies in the accurate detection of known persistent threat actor group techniques specifically within cloud environments.
In this research, we hypothesize how a new method of alert analysis could be used to improve detection. Specifically, we look at cloud-based alerting events and their mapping to the MITRE ATT&CK® tactics and techniques they represent. We believe that we can show a correlation between threat actors and the types of techniques they use, which will trigger specific types of alerting events within victim environments. This distinct, detectable pattern could be used to identify when a known threat actor group compromises an organization.
To prove this method of alert analysis, Unit 42 researchers focused on two known threat actor groups that use two fundamentally different types of operational techniques to compromise their victims’ cloud environments. These groups are the cybercrime group Muddled Libra and the nation-state group Silk Typhoon. Both threat actor groups are known to target cloud operations.
- We analyzed cloud alerting events across 22 industries between June 2024 and June 2025.
- The research was conducted by pairing the cloud-related MITRE ATT&CK techniques known to be used by Muddled Libra and Silk Typhoon with the specific security alerts they are known to trigger in cloud environments.
The test confirmed, as you will see within the remainder of this article, that security teams can successfully distinguish unique alerting patterns between Muddled Libra and Silk Typhoon based solely on the types of alerts observed.
Additionally, the results show a clear link between threat actors’ cloud-focused operations and the industries those groups target. Therefore, at times when one of the groups was known to be attacking certain industries, we can see those patterns appear in our data.
The confirmation that our detection method works as expected opens the door to the possibility of automated prevention capabilities for complex cloud architectures.
Cortex Cloud is designed to detect and prevent the malicious operations, configuration alterations and exploitations discussed in this article, by associating events with MITRE tactics and techniques. These capabilities help organizations to maintain runtime detection of events.
Organizations can gain help assessing cloud security posture through the Unit 42 Cloud Security Assessment.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | Muddled Libra (related to Scattered Spider), API, IAM |
Another Lens on Cloud Alert Trends
Following our previous article on cloud alert trends, we conducted another analysis of cloud alert statistics.
As part of the effort to determine whether we could identify threat groups, this time we analyzed the data in terms of the industries in which cloud alerts were triggered. Adding industry telemetry to the analysis allowed us to focus our efforts on identifying the techniques, and thus the resulting alerts, used by these threat actors as a control parameter. Using alert data pulled between June 2024 and June 2025, we identified the industries that saw the highest number of unique alert types as well as the highest average number of daily alerts. We then correlated these trends with the activities and targets of two threat groups: Muddled Libra and Silk Typhoon.
This article presents our analysis of Muddled Libra and Silk Typhoon operational techniques and the associated alert analysis.
Glossary: Mapping Techniques to Alerts
The research was conducted by analyzing cloud-related MITRE ATT&CK techniques known to be used by Muddled Libra and Silk Typhoon and pairing them with the specific security alerts they are known to trigger in cloud environments. The following glossary will assist readers in understanding the results we present.
- Mapping MITRE Techniques to Alerts: A single MITRE technique can potentially trigger multiple unique security alerts, and conversely, a single alert can map to one or more MITRE techniques and tactics. For example, the alert Remote command line usage of serverless function’s token in the Cortex Cloud platform correlates to the MITRE tactic Credential Access, and the MITRE techniques Steal Application Access Token and Unsecured Credentials.
- Unique Alert Count: We counted each alert rule only once for the basis of this research. For example, we identified nearly 70 different unique alerting rules that could be attributed to at least one of the 11 different cloud-related MITRE techniques known to be used by Muddled Libra. For Silk Typhoon, we found just over 50 unique alerting rules that could be attributed to at least one of their 12 known cloud-related MITRE techniques. Additionally, we found that only three unique alert rules were present in both Muddled Libra and Silk Typhoon alert rule sets. In some cases, these alerting rules triggered multiple times within our data across multiple organizations, but when we refer to unique alerts within an industry, we are only considering whether an alert triggered at all during the specified period.
- Average Daily Occurrences: If a threat actor used the MITRE technique Data from Cloud Storage (T1530), one of the resulting unique Cortex alert rules might be Suspicious identity downloaded multiple objects from a bucket. If this alert is triggered 1,000 times in a single day, it counts as a single unique alert, but the 1,000 occurrences of that alert in that day will be calculated in the average daily occurrences. When we report average alerts per day by industry in the article below, we take the average for each organization within that industry vertical.
To use a metaphor to help explain how we considered alerts, if each alert rule was a type of fruit, we would see that Muddled Libra holds a very different basket of fruit than Silk Typhoon does. In fact, the baskets are so diverse, that out of the nearly 70 different types of fruit Muddled Libra has, and the more than 50 different types of fruit Silk Typhoon has, they only have 3 types of fruit in common.
When we look at alerts triggered within an industry, we might see a variety of fruit scattered about — maybe 10 oranges, 14 lemons and so on. When we analyze the fruit trail in terms of the types of fruit found within a particular industry, compared with the types of fruit found in the baskets we know Muddled Libra or Silk Typhoon to be holding, we can make a reasonable determination of which threat actor was involved.
Methodology
We collected alerts between June 2024 and June 2025 that were triggered on a combination of platforms, including:
- Cloud service providers
- Container environments
- Cloud-hosted applications
- SaaS platforms
We then analyzed the alerts based on their unique naming, originating platform, alert date and metadata such as:
- Industry
- Region
- Frequency of occurrence
- Average number of occurrences in each organization
As described above, we integrated the correlation of the MITRE ATT&CK framework, by pairing each alert with its corresponding MITRE technique.
We also analyzed the correlation between the targeted organization’s industry and region and the severity level of the alerts they experienced. This helped to identify the types of alerts that are more likely to occur, based on these factors.
Threat Actor Profiles
Muddled Libra
Background
Muddled Libra (also known as Scattered Spider, or UNC3944) is a cybercrime group that has been active since 2021.
Known for its use of social engineering, including making calls to organizations’ help desks, Muddled Libra has also been known to partner with ransomware-as-a-service (RaaS) programs. By continually updating its approach, the group has successfully used social engineering techniques, including smishing (SMS phishing), vishing (voice phishing) and spear phishing (directly targeting an employee).
Upon successfully compromising an organization, the group uses several tools, including ransomware variants such as DragonForce – a subscription-based RaaS framework created by a group of the same name, tracked by Unit 42 as Slippery Scorpius. The group also uses cloud enumeration tools such as ADRecon, an open source Active Directory reconnaissance tool.
Targeted Industries and Techniques
While Muddled Libra’s targeted industries have evolved since 2022, the following sectors have been consistently reported:
- Aerospace and defense
- Financial services
- High technology
- Hospitality
- Media and entertainment
- Professional and legal services
- Telecommunications
- Transportation and logistics
- Wholesale and retail
Muddled Libra employs multiple offensive techniques to compromise and maintain access within a victim’s environment. We analyzed the group’s known techniques, and extracted those techniques that specifically focus on cloud infrastructure, as Table 1 shows. Together, these form a sort of “fingerprint” that we can use to identify the group within cloud alert data.
| MITRE Tactics | MITRE Techniques | MITRE Technique Name |
| Collection | T1530 | Data from Cloud Storage |
| Defense Evasion | T1578.002 | Modify Cloud Compute Infrastructure: Create Cloud Instance |
| Defense Evasion, Persistence, Privilege Escalation, Initial Access | T1078.004 | Valid Accounts: Cloud Accounts |
| Discovery | T1069.003 | Permission Groups Discovery: Cloud Groups |
| Discovery | T1087.004 | Account Discovery: Cloud Account |
| Discovery | T1526 | Cloud Service Discovery |
| Discovery | T1538 | Cloud Service Dashboard |
| Discovery | T1580 | Cloud Infrastructure Discovery |
| Lateral Movement | T1021.007 | Remote Services: Cloud Services |
| Persistence, Privilege Escalation | T1098.001 | Account Manipulation: Additional Cloud Credentials |
| Persistence, Privilege Escalation | T1098.003 | Account Manipulation: Additional Cloud Roles |
Table 1. Known Muddled Libra cloud tactics and techniques.
Methodology Walkthrough
Even though each MITRE Technique is relatively granular in terms of scope of operation, there can be multiple types of computational events from a cloud platform or software-as-a-service (SaaS) application which can fall under the purview or scope of a single MITRE technique.
For example, the MITRE technique T1078.004 - Valid Accounts: Cloud Accounts is focused on the operational event of a valid cloud account. This can have a wide scope in the types of event which can be counted, such as:
- Unusual resource modification from a newly seen IAM user
- Deletion of multiple cloud resources by a newly created IAM role
- A suspicious identity created or updated password for an IAM user
Each of these can be linked to a valid cloud account but each one could have vastly different root causes.
Additionally, when looking specifically at an individual alert type, such as Unusual resource modification from a newly created IAM role, this event could be considered to align not only with the MITRE tactic Initial Access, but it could also align with the MITRE tactics Defense Evasion or even Persistence.
When we expanded our scope to include potential alerting events that could be triggered by any of the MITRE techniques known to be used by Muddled Libra, we found nearly 70 alerting events that could be attributed to at least one of these MITRE techniques.
We collected all of these alerts, which were associated with each of the MITRE techniques known to be used by Muddled Libra. We then distilled those alerts to identify the number of unique alerts that were present within each industry. We also tracked the number of average daily occurrences for each organization within those industries. To use our fruit analogy, we identified the number of unique fruit that the threat actors left at each respective industry (unique alerts), then we also counted how many of each fruit type were present at each organization within that industry (average alert count).
As explained in the Glossary section, we were able to use these numbers to build patterns.
Industry and Technique Analysis
Comparing the triggered alerts and their associated MITRE techniques with the targeted industries shows a correlation between the industries targeted according to public reports and the alerts triggered by Muddled Libra operations. Figure 1 shows this correlation by ranking industries from the highest to the lowest based on the number of unique alerts related to the MITRE techniques listed within Table 1, between June 2024 and July 2025. Industries that were publicly reported as targeted are shown in red.
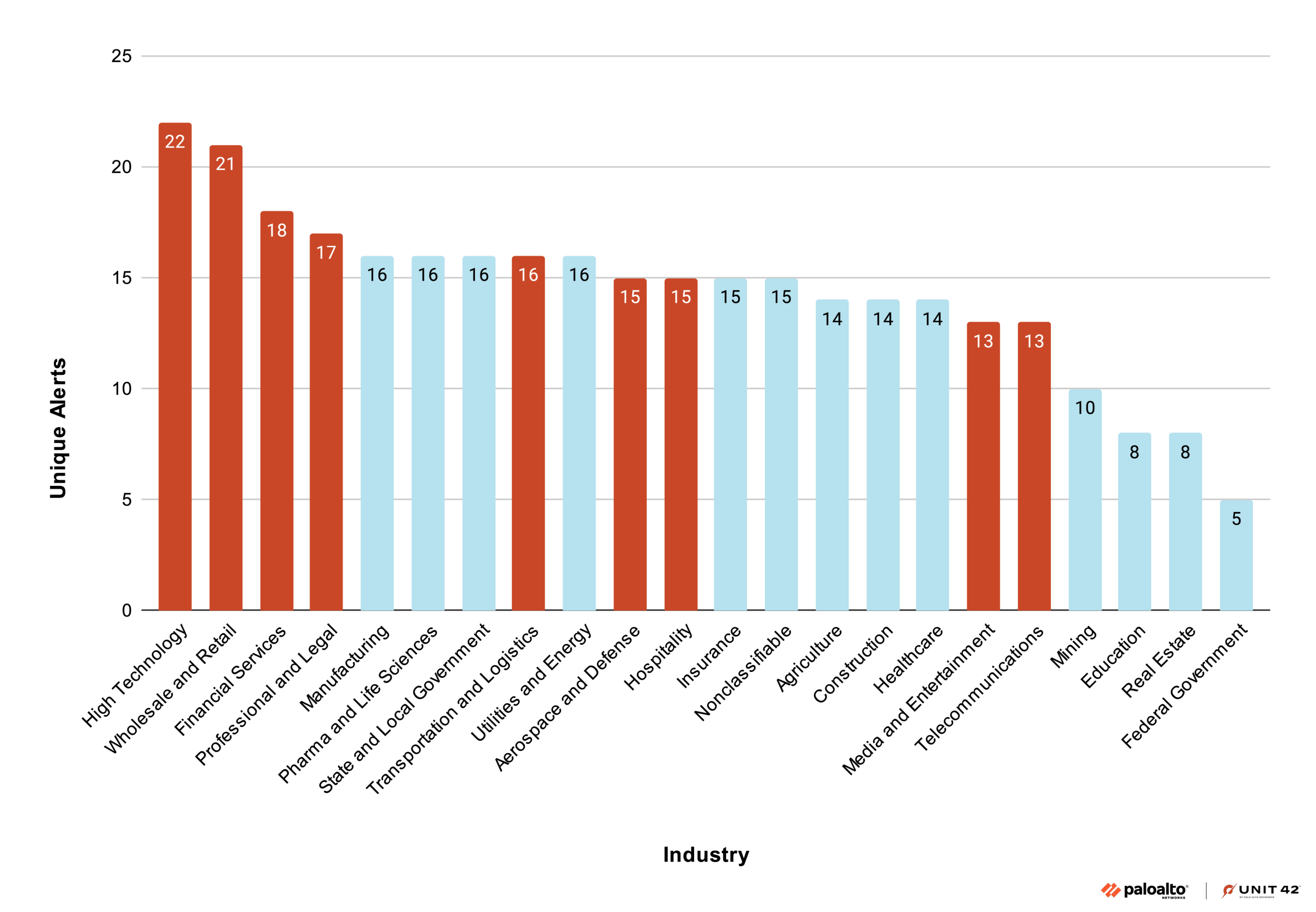
Figure 2 shows the average daily number of alerts that occurred during the same timeframe.
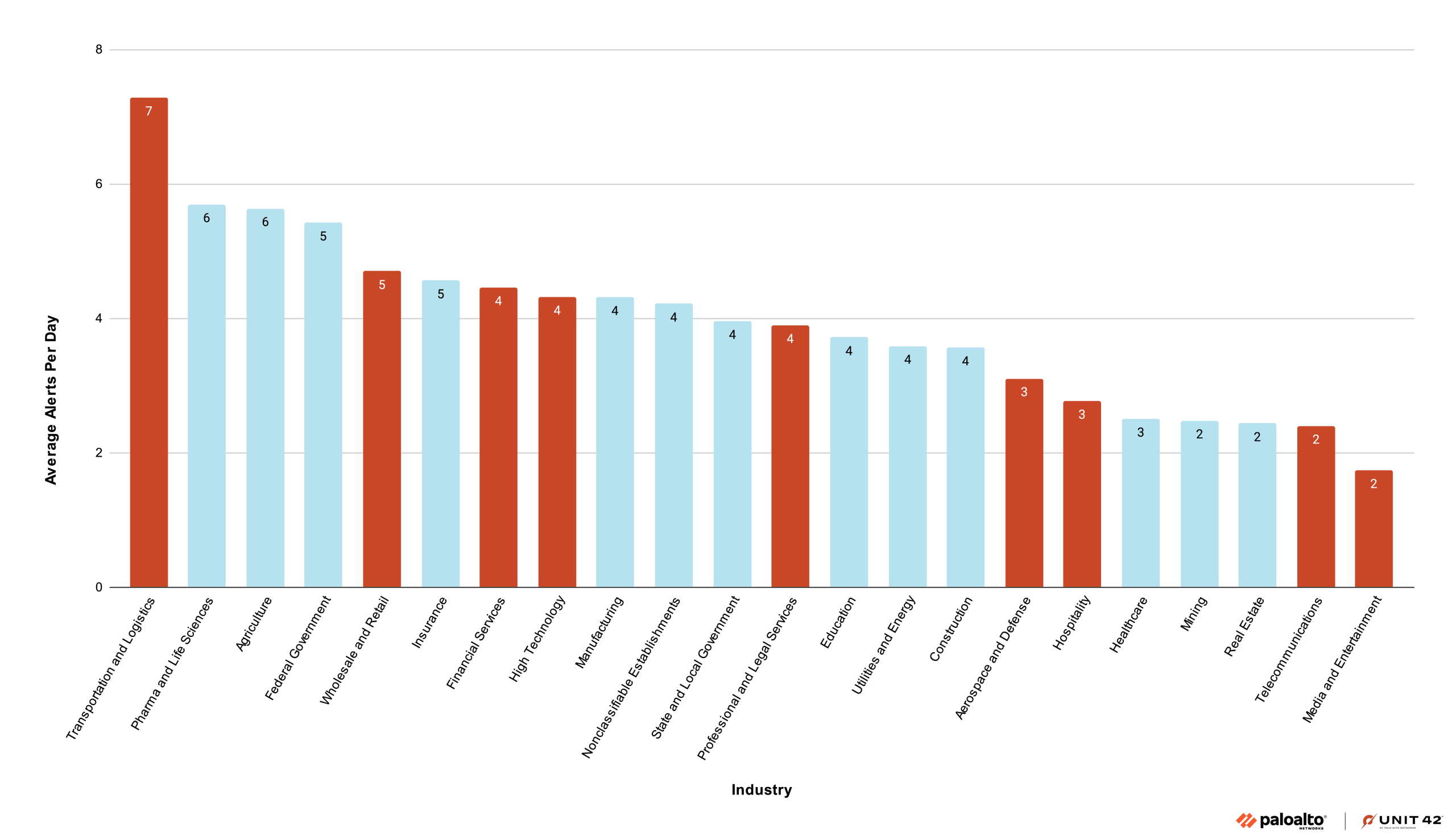
Figure 2. Count of the average daily alerts by industry from June 2024-June 2025. Red bars indicate the industries publicly reported as targeted by Muddled Libra.
While the highest volume of unique alerts (shown in Figure 1) aligns perfectly with Muddled Libra’s most-reported targets — specifically high technology, wholesale and retail, financial, and professional and legal services—the presence of a number of signature alerts in other sectors shouldn't be ignored. When an industry like manufacturing or pharma and life sciences or state and local government shows a significant subset of Muddled Libra’s "fingerprint" (for instance, 16 or more unique alert types), it suggests the group could have an active interest in these environments even if we haven’t seen headlines about it. Security teams in these "middle-tier" industries should treat these clusters of unique alerts as early warning signs that these industries are witnessing a significant number of the group's known operational techniques.
The unique alert data (Figure 1) should be considered alongside average daily alert data (Figure 2) to distinguish between a threat actor’s strategic breadth and their operational persistence. For instance, transportation and logistics serves as a primary example of high-intensity targeting; it ranks sixth in unique alert variety but first in average daily volume, showing a 25% spike in unique alerts in June 2025 alone. This combination indicates that Muddled Libra is not only using a wide array of its signature techniques in this sector but is doing so with higher frequency. We will take a deeper dive into transportation and logistics in the next section.
In contrast, telecommunications and media and entertainment were some of the first and most frequent targets of Muddled Libra in 2022 and 2023, but their standings as the last two positions for average daily alerts in 2024-2025 suggest that these two industries in particular have experienced a saturation effect. Namely, the targeting of these groups may be aging off. They no longer appear to be the key focus of the Muddled Libra actors. The other industries that could also fall into this category are hospitality and aerospace and defense.
For a defender, this data provides a threshold for proactive investigation. A high count of unique alerts (the "variety" of the fruit basket) typically signals a sophisticated, multi-stage intrusion attempt, whereas a high daily average (the "quantity" of fruit) may point to automated scanning or persistent credential stuffing. If your organization sees more than 10 unique Muddled Libra-associated alerts within a 30-day window, it is time to look deeper, regardless of whether your specific industry is currently "trending" in threat intelligence circles. The goal is to move from reactive patching to proactive defense by identifying these actor-specific patterns before they escalate to data exfiltration.
Focused Analysis: Aviation
Reports that Muddled Libra was targeting the aviation industry initially surfaced in June 2025. Unit 42 does not track aviation as a singular category. Instead, aviation organizations appear under our transportation and logistics category.
When looking at the transportation and logistics industry alerts, we found an increase in the number of unique alerts based on the MITRE techniques used by Muddled Libra during this same timeframe.
It is important to note that here we are looking at the number of unique alert rules for this analysis and breaking this out by month, as opposed to the whole year view shown in Figure 1. We arrive at “unique alerts” for the industry by taking the average number of unique alerts seen for each organization tracked in that category over a monthly timeframe.
Figure 3 shows that the average number of unique alerts per organization in the transportation industry increased by 25% from May-June 2025. What makes this finding important is that Muddled Libra made several headlines during June 2025 for its operations targeting airline organizations.
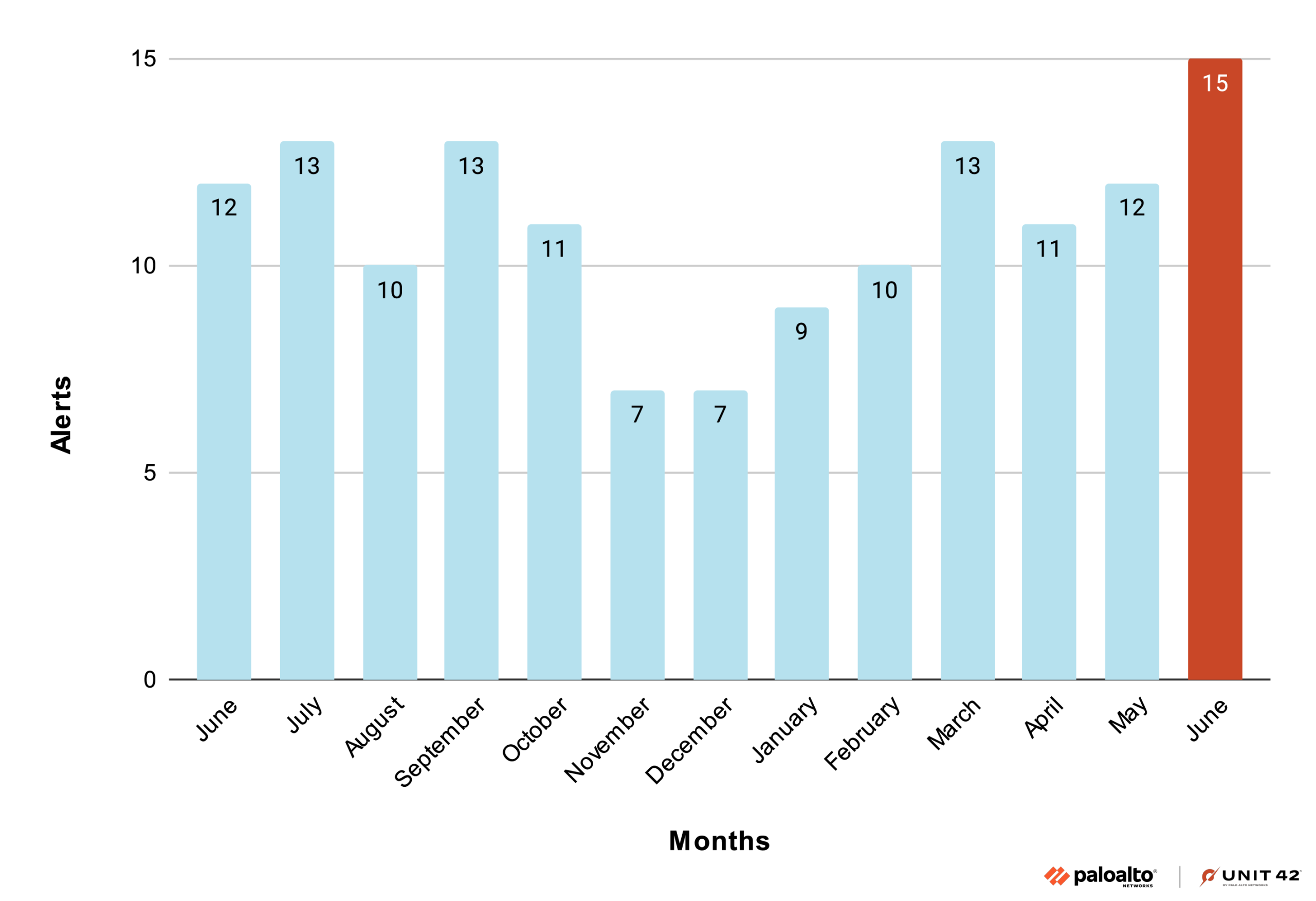
As illustrated in Figure 3, June 2025 saw the highest number of unique alerts for the transportation industry, with 15 unique alerts.
The Verdict on the Fingerprinting Effort
Looking at the correlation, there does appear to be a fingerprint capability that could be used as a detection pattern. This pattern could help organizations identify if they are potentially targeted and take mitigative steps. Additionally, this could also assist organizations in developing an early warning detection trigger. For example, if defenders witness an increase in the number of daily average occurrences alerts from known Muddled Libra techniques, this could indicate reconnaissance or discovery activity occurring against their infrastructure. This then provides an opportunity to proactively prepare for future operations.
Top 10 Alerts from Muddled Libra Techniques
Table 2 lists the top 10 alerts that we observed in association with Muddled Libra’s MITRE techniques.
| Alert Names | MITRE Techniques | Tactics |
| Azure sensitive resources enumeration activity using Microsoft Graph API | T1526 | Discovery |
| Microsoft 365 storage services exfiltration activity | T1530 | Collection, Exfiltration |
| Multi region enumeration activity | T1580 | Discovery |
| Storage enumeration activity | T1619 | Discovery, Collection |
| Cloud Identity Queried Cost or Usage Information | T1087.004 | Discovery |
| A cloud identity invoked IAM related persistence operations | T1098 | Defense Evasion, Persistence, Privilege Escalation, Initial Access |
| Cloud infrastructure enumeration activity | T1580 | Discovery |
| Suspicious identity downloaded multiple objects from a bucket | T1530 | Collection, Exfiltration |
| Suspicious cloud infrastructure enumeration activity | T1580 | Discovery |
| ML model discovery | T1526 | Discovery |
Table 2. The top 10 alerts associated with Muddled Libra’s MITRE techniques.
As outlined in Table 2, Muddled Libra has an extensive history of targeting Microsoft Azure environments using Graph API, a RESTful API that enables access to Azure cloud resources. This type of activity correlates with the MITRE techniques used by Muddled Libra and the alerts triggered by their operations. The most frequent alert between June 2024 and June 2025, in relation to the MITRE techniques used by Muddled Libra, was resource enumeration using Microsoft Graph API. The next most common alert was for exfiltration activity from Microsoft 365 storage services. While discovery operations represented the bulk of the remaining alert types, collection and exfiltration operations were the second most frequent alert type.
Silk Typhoon
Background
Silk Typhoon (also known as HAFNIUM) is a China-nexus threat actor group that has been in operation since at least 2021. This group has historically exploited multiple vulnerabilities on Microsoft Exchange Servers. In recent years, the group appears to be shifting targets towards cloud environments, using compromised credentials obtained via vulnerable public-facing VPN endpoints to move laterally through cloud environments. The group relies on remote monitoring and management (RMM) tools to maintain persistent access and leverages Microsoft’s Graph API to enumerate cloud resources.
Targeted Industries and Techniques
Cybersecurity researchers have identified that the industries most commonly targeted, primarily located within the U.S., include:
- Education
- High technology
- Federal governments
- Financial services
- Nongovernmental organizations (NGOs)
- Professional and legal services
- State and local governments
- Utilities and energy
Silk Typhoon has employed several offensive techniques to compromise and maintain access within a victim’s environment. Using the same methodology that was employed during the Muddled Libra analysis above, we analyzed the techniques and identified those that focus on cloud infrastructure, as Table 3 shows. We found that between Silk Typhoon and Muddled Libra’s known employed technique usage, only three techniques were employed by both threat actor groups, T1530, T1078.004 and T1098.001. This provides a basis on which to compare and contrast the results between both groups’ operations and, more importantly, on the types of alerts witnessed by organizations in the industries they target.
| MITRE Tactics | MITRE Techniques | MITRE Technique Name |
| Collection | T1119 | Automated Collection |
| Collection | T1530 | Data from Cloud Storage |
| Credential Access | T1555.006 | Credentials from Password Stores: Cloud Secrets Management Stores |
| Defense Evasion,
Lateral Movement |
T1550.001 | Use Alternate Auth Material: Application Access Token |
| Defense Evasion,
Persistence, Privilege Escalation, Initial Access |
T1078.004 | Valid Accounts: Cloud Accounts |
| Discovery | T1619 | Cloud Storage Object Discovery |
| Exfiltration | T1567.002 | Exfiltration Over Web Service: Exfiltration to Cloud Storage |
| Impact | T1485 | Data Destruction |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1199 | Trusted Relationship |
| Persistence | T1136.003 | Create Account: Cloud Account |
| Persistence,
Privilege Escalation |
T1098.001 | Account Manipulation: Additional Cloud Credentials |
Table 3. Known Silk Typhoon cloud tactics and techniques.
Methodology Walkthrough
As a brief recap to the methodology of our research, we analyzed the types of alerting events that could be associated with each of the MITRE Techniques known to be used by Silk Typhoon. When we included potential alerting events that could be triggered by any of the MITRE Techniques known to be used by Silk Typhoon, we found just over 50 alerting events that could be attributed to at least one of these MITRE Techniques.
We collected all of these alerts and distilled those alerts to identify the number of unique alerts that were present within each industry and the number of average daily occurrences of those alerts for each organization within those industries.
To use the same analogy as above, we wanted to identify what types of fruit Silk Typhoon brought to the party, and how many pieces of fruit they typically deploy when attacking.
Industry and Technique Analysis
We compared the total number of unique alerts for each month from June 2024 to June 2025 with the industries from which those alerts were triggered. This comparison confirmed that we were able to see the “fingerprints” of Silk Typhoon in the alerts triggered in industries that the group was known to be targeting.
As mentioned, Silk Typhoon had just over 50 unique alerts associated with their known technique usage, where Muddled Libra had nearly 70.
In contrast, we saw higher numbers of unique alerts within each industry when examining our Silk Typhoon data than we did in our Muddled Libra data.
In other words, Silk Typhoon may be holding a basket with fewer types of fruit (50) than in Muddled Libra’s (70), but the threat actor seems to use more types from the basket in its operations (i.e. as many as 27 unique alerts as opposed to 22).
The graph in Figure 4 shows our observations of alerts by industry over the period studied.
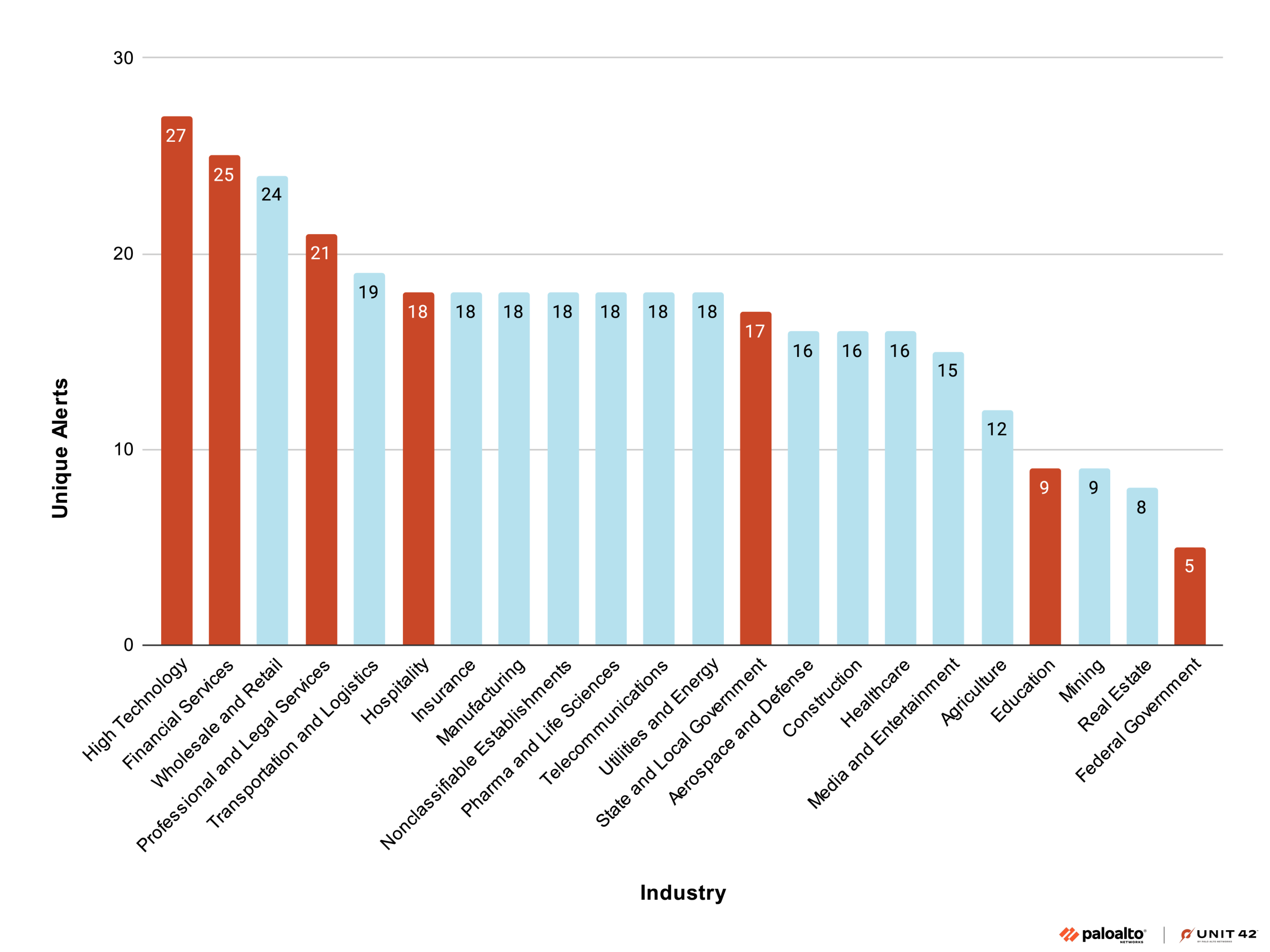
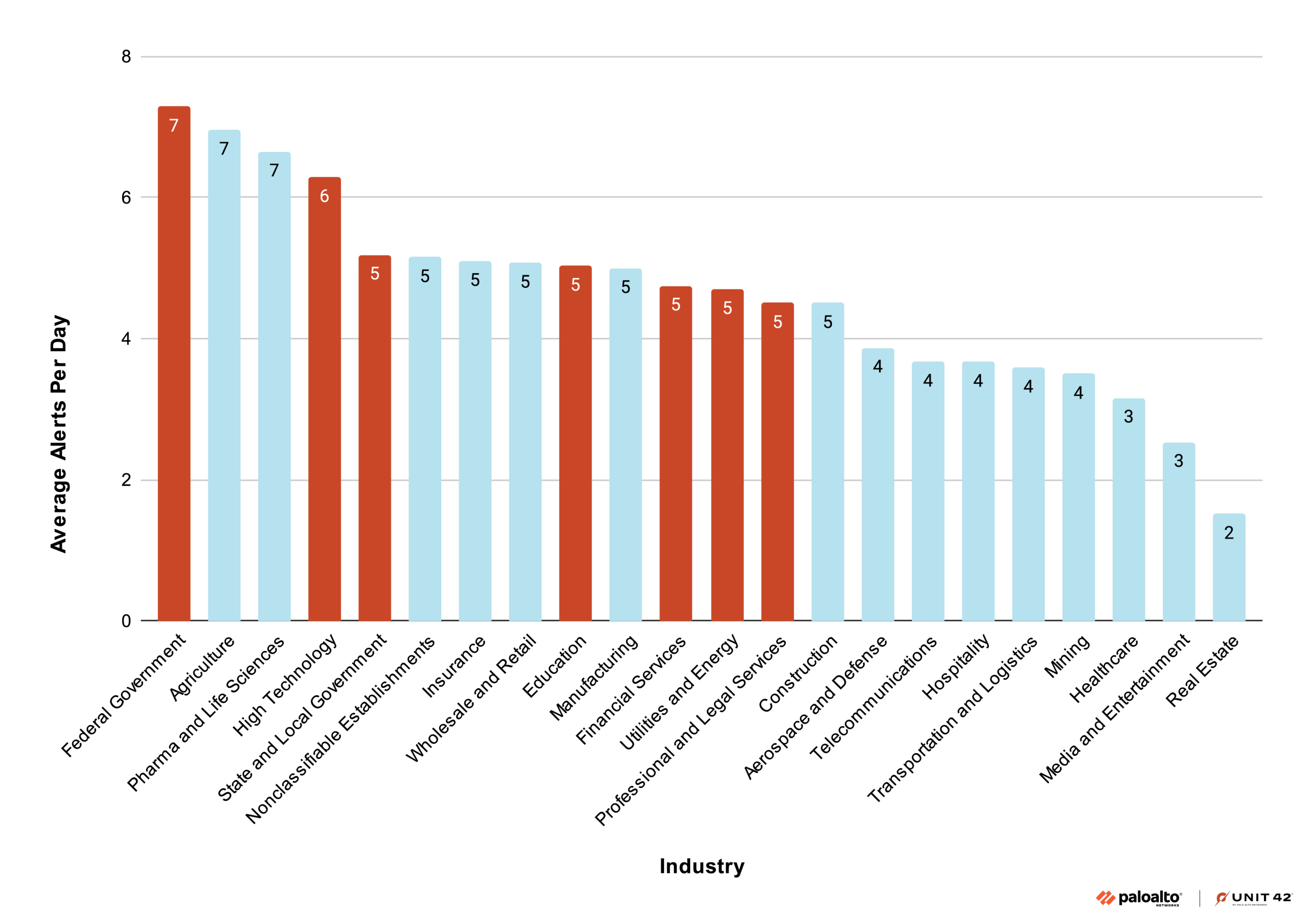
While the highest volume of unique alerts aligns with Silk Typhoon’s most-reported targets—specifically high technology, financial services, and professional and legal services—the presence of signature alerts in other sectors is equally telling. When an industry like wholesale and retail or manufacturing shows a significant subset of Silk Typhoon’s "fingerprint" (for instance, 18 or more unique alert types), it indicates that the group could be actively deploying their offensive techniques against these industry environments. This could be occurring even if public reporting is minimal or nonexistent at this date. Security teams in these "middle-tier" industries should treat these clusters of unique alerts as evidence that they are witnessing a broad spectrum of the group's known operational techniques, rather than isolated incidents.
The unique alert data for Silk Typhoon (Figure 4) should be considered alongside average daily alert data (Figure 5) to distinguish between a threat actor’s strategic breadth and their operational persistence. To return to our metaphor, Silk Typhoon holds a "basket" with fewer types of fruit (50) than Muddled Libra (70), but they tend to use more of what is in their basket at any given time. For example, we witnessed as many as 27 unique alerts in a single sector compared to Muddled Libra’s 22.
The federal government serves as a primary example for high-intensity targeting. This industry ranks last in the number of unique alerts, or rather in variety, ie. the "types of fruit" in its basket, but first in average daily volume, peaking at 7.28 alerts per day (the "quantity of fruits witnessed"). This suggests that while Silk Typhoon may use a narrower set of techniques against government targets, it deploys those specific tactics with relentless frequency. Conversely, high technology shows a "worst-of-both-worlds" scenario, ranking first in unique tactical variety and near the top for daily volume. This indicates campaigns that are both sophisticated and persistent.
Similar to our comments on unique alerts, when we see a high level of activity possibly related to the threat group, it may be worth defenders' threat hunting for other known alerts related to Silk Typhoon, out of an abundance of caution. High levels of average alert activity could signify threat groups trying to gain initial access, but not yet succeeding in deploying their full toolset.
For a defender, this data provides a threshold for proactive investigation: a high count of unique alerts (the "variety" of the fruit basket) typically signals a sophisticated, multi-stage intrusion attempt, whereas a high daily average (the "quantity" of fruit) may point to automated scanning or persistent exploitation of specific vulnerabilities. If an organization observes more than 10 unique Silk Typhoon-associated alerts within a month, it is time to look deeper, regardless of whether a specific sector is making headlines as a common target.
Top 10 Alerts from Silk Typhoon Techniques
Table 4 lists the alerts most commonly seen in relation to the MITRE techniques used by Silk Typhoon.
| Alert Names | MITRE Techniques | Tactics |
| Microsoft O365 storage services exfiltration activity | T1530 | Collection, Exfiltration |
| Process execution with a suspicious command line indicative of the Spring4Shell exploit | T1190 | Initial Access |
| Storage enumeration activity | T1619 | Discovery |
| A cloud identity invoked IAM related persistence operations | T1098 | Persistence, Privilege Escalation |
| Suspicious identity downloaded multiple objects from a bucket | T1530 | Collection, Exfiltration |
| Suspicious identity downloaded multiple objects from a backup storage bucket | T1530 | Collection, Exfiltration |
| An identity performed a suspicious download of multiple cloud storage objects | T1530 | Collection, Exfiltration |
| An identity performed a suspicious download of multiple cloud storage objects from multiple buckets | T1530 | Collection, Exfiltration |
| Massive code file downloads from SaaS service | T1530 | Collection |
| Deletion of multiple cloud resources | T1485 | Impact |
Table 4. The top 10 alerts associated with Silk Typhoon’s MITRE techniques.
As outlined in Table 4, collection and exfiltration techniques were the most common alerts associated with Silk Typhoon’s MITRE techniques. Microsoft 365 storage services exfiltration was the most frequently observed alert. Other alerts identified include cloud storage enumerations and suspicious downloads of cloud storage objects.
Industry Cloud Alert Trends
Perhaps the most striking result of our research came to light when we compared general cloud alerting trends with the trends we discovered while performing the fingerprinting analysis of Muddled Libra and Silk Typhoon.
The industry of high technology was consistently the top ranked industry when considering general cloud alerting trends, as well as the two threat actor groups’ alerting trends. However, the remaining industries we studied did not follow a uniform pattern. As shown in Figure 6, we found that the order of the most targeted industries shifted when we only counted alerts from Muddled Libra and Silk Typhoon operations.
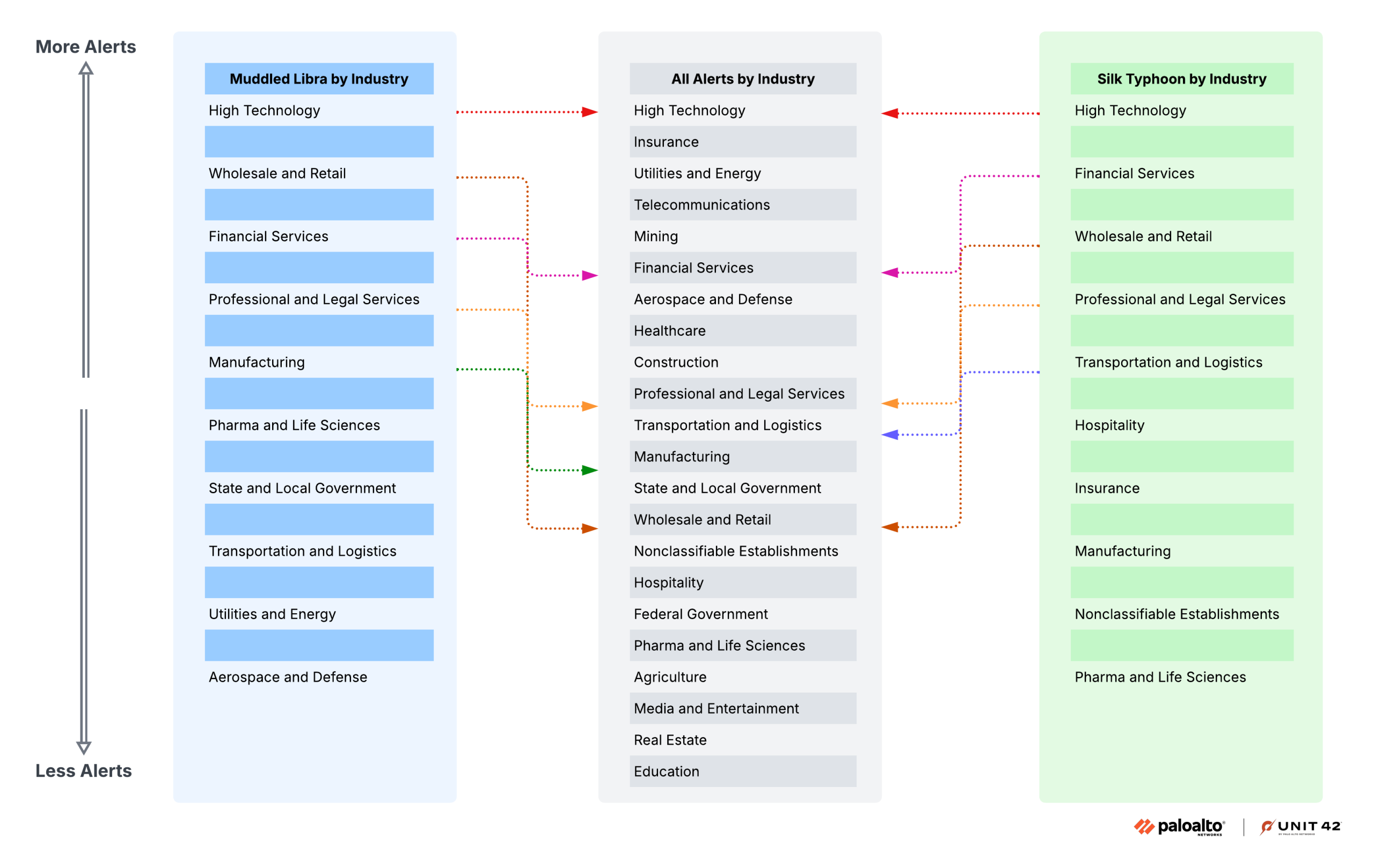
As stated above, the high technology industry is in first place across both threat actor group findings, as well as the top ranking industry when looking at all cloud alerts by industry.
However, the remaining industry ranks do not mirror the same results. Looking at the wholesale retail industry illustrates a key finding. This industry is the second highest for Muddled Libra alerting events and third highest for Silk Typhoon, but is 14th on the industry list for all alerts.
This indicates that the fingerprinting analysis on these alerting operations does not reflect the same pattern as the general noise of all alerting trends. It appears that the distinct operations performed by the threat actors against the industries they target carry their own unique trends.
Conclusion
Our analysis confirms the capacity to leverage the alerts triggered as a fingerprint detection pattern for the malicious techniques used by Muddled Libra and Silk Typhoon. This distinct detection capacity offers a new pathway for organizations to implement predictive and proactive cloud defense strategies.
Our research successfully differentiated the MITRE tactic and technique operations used by Muddled Libra, notably the aviation industry’s 25% increase in the number of unique alerts compared to the previous month, and Silk Typhoon’s increased higher than average number of daily alerts within the Federal and State Government industry.
By identifying the alert patterns that each threat actor’s techniques have on the alerting events within cloud environments, threat researchers can identify the threat actors most likely to target certain industries using specific techniques. This can then help defenders to proactively prepare defenses against those types of threats. Through the analysis of threats based on the types of attack techniques they leverage, organizations can create a defense methodology built specifically for their industry vertical.
Proper implementation of these defense controls can be effective in defending against targeted threat actor scenarios through the creation of tailored defensive alerting. Additionally, these controls can provide the capability to detect early warning scenarios and techniques, such as initial access operations, enabling prevention operations to block malicious cloud operations before they escalate to execution, impact or exfiltration.
Palo Alto Networks customers are better protected from the threats discussed above through the following products:
Cortex Cloud customers can help secure and protect their cloud environments through compliance guardrails, application security monitoring and prevention techniques and through the proper placement of Cortex Cloud XDR endpoint agent and serverless agents within a cloud environment. Cortex Cloud is designed to identify cloud events witnessed on cloud platforms, to protect cloud posture and runtime operations. By associating events with MITRE tactics and techniques, Cortex Cloud helps detect and prevent the malicious operations, configuration alterations and exploitations discussed within this article.
Organizations can gain help assessing cloud security posture through the Unit 42 Cloud Security Assessment.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 000 800 050 45107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Additional Resources
- Updated Advisory on Scattered Spider Group – U.S. Cybersecurity and Infrastructure Security Agency
- Scattered Spider Tactics Observed Amid Shift to US Targets – Halcyon
- Silk Typhoon targeting IT supply chain – Microsoft
- HAFNIUM targeting Exchange Servers with 0-day exploits – Microsoft
- Scattered Spider – MITRE
- MITRE Cloud Techniques – MITRE
- Cloud Threats on the Rise – Unit 42, Palo Alto Networks
- Muddled Libra Threat Assessment – Unit 42, Palo Alto Networks
- Muddled Libra - Further and Faster – Unit 42, Palo Alto Networks
- Threat Actor Groups Tracked by Palo Alto Networks Unit 42 – Unit 42, Palo Alto Networks
- Active Exploitation of Multiple Zero-Day Microsoft Exchange Vulnerabilities – Volexity











 Get updates from Unit 42
Get updates from Unit 42