Executive Summary
The ransomware landscape experienced significant transformations and challenges in 2023. The year saw a 49% increase in victims reported by ransomware leak sites, with a total of 3,998 posts from various ransomware groups.
What drove this surge of activity? 2023 saw high-profile vulnerabilities like SQL injection for MOVEit and GoAnywhere MFT services. Zero-day exploits for these vulnerabilities drove spikes in ransomware infections by groups like CL0P, LockBit and ALPHV (BlackCat) before defenders could update the vulnerable software.
Leak site data reveals at least 25 new ransomware groups emerged in 2023, indicating the continued attraction of ransomware as a profitable criminal activity. Despite the appearance of new groups such as Darkrace, CryptNet and U-Bomb, many of these new ransomware threat actors did not last and disappeared during the second half of the year.
2023 was an active year for international law enforcement agencies as they intensified their focus on ransomware. This focus led to the decline of groups like Hive and Ragnar Locker, and the near-collapse of ALPHV (BlackCat). Law enforcement actions in 2023 reflect the increasing challenges faced by ransomware groups.
Ransomware threat actors targeted a wide range of victims with no preference for specific industries.
Leak site data collected by Unit 42 indicates that manufacturing was the most affected industry in 2023, signaling significant vulnerabilities in this sector. Although organizations from at least 120 different countries have been impacted by ransomware extortion, the U.S. stood out as the primary target of ransomware. 47% of ransomware leak site posts in 2023 revealed victim organizations based in the U.S.
Palo Alto Networks customers are better protected from the threats discussed in this article through our Next-Generation Firewall with Cloud-Delivered Security Services, including Advanced WildFire, DNS Security, Advanced Threat Prevention and Advanced URL Filtering.
Cortex Xpanse can be used to detect vulnerable services. Cortex XDR and XSIAM customers have been protected from all known active ransomware attacks of 2023 out of the box, without additional protections having to be added to the system. The Anti-Ransomware Module helps prevent encryption behavior, local analysis helps prevent the execution of ransomware binaries, and Behavioral Threat Protection helps prevent ransomware activity. Prisma Cloud Defender Agents can monitor Windows VM instances for known malware.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | Ransomware |
| Ransomware Groups Discussed | ALPHV, Akira, CL0P, Hive, LockBit 3.0, Play, Ransomed, Royal, ThreeAM, Trigona, Vice Society |
Leak Sites and Our Dataset
Analysis for this article is based on data from ransomware leak sites, sometimes known as dedicated leak sites and abbreviated as DLS.
Ransomware leak sites first appeared in 2019, when Maze ransomware began using a double extortion tactic. Stealing a victim’s files before encrypting them, Maze was the first known ransomware group to establish a leak site to coerce a victim and release stolen data.
These threat actors pressure victims to pay – not only to decrypt their files, but to prevent the attackers from publicly exposing their sensitive data. Since 2019, ransomware groups have increasingly adopted leak sites as part of their operations.
Our team monitors data from these sites, often accessible through the dark web, and we review this data to identify trends. Since leak sites are now commonplace among most ransomware groups, researchers often use this data to determine overall levels of ransomware activity and pinpoint the date a specific ransomware group was first active.
However, defenders should use leak site data with caution because it might not always reflect actuality. A ransomware group might start without a leak site as it builds its infrastructure and expands operations. Furthermore, if a victim offers immediate payment, the ransomware incident might not appear on a group’s leak site. As a result, leak sites do not always provide a clear or accurate picture of a ransomware group's activities. The true scope of ransomware's impact might be different from what these sites suggest.
Despite these drawbacks, data pulled from ransomware leak sites provides valuable insight on the state of ransomware operations in 2023.
Key Findings
The dataset we have compiled reveals the rise and fall of ransomware groups in 2023, along with affected industries and geographical distribution of attacks. Most importantly, the volume of ransomware activity reflects the large-scale impact of zero-day exploits targeting critical vulnerabilities.
Critical Vulnerabilities
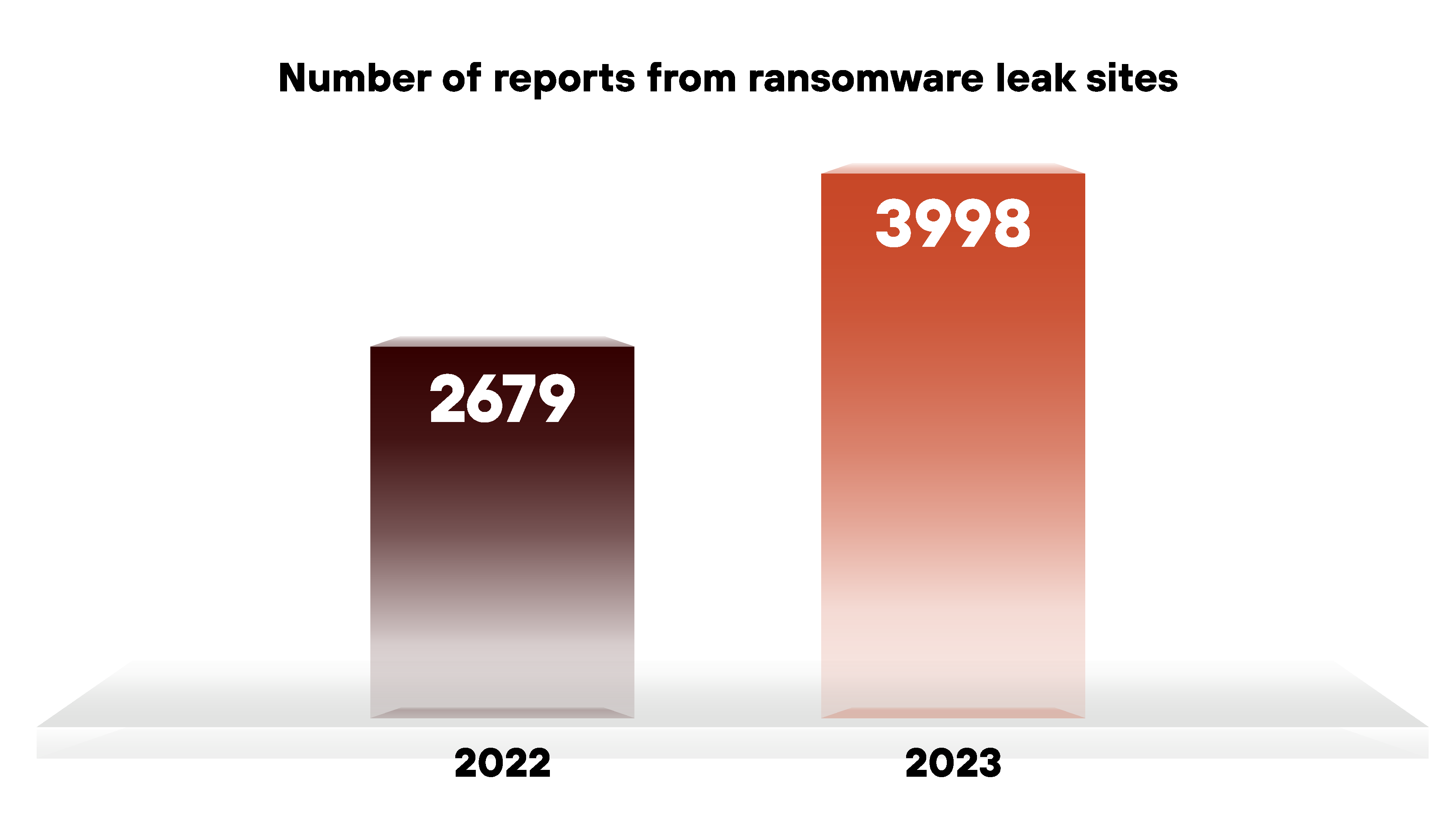
In 2023, we observed 3,998 posts from ransomware leak sites, compared to 2,679 posts in 2022. This marks approximately a 49% increase for the year as illustrated below in Figure 1.
The increase in activity can likely be attributed to zero-day exploits targeting critical vulnerabilities such as CVE-2023-0669 for GoAnywhere MFT or CVE-2023-34362, CVE-2023-35036 and CVE-2023-35708 for MOVEit Transfer SQL Injection.
CL0P has taken credit for exploiting the MOVEit transfer vulnerability. In June 2023, the U.S. Cybersecurity and Infrastructure Agency (CISA) estimated TA505, a group known for leveraging CL0P ransomware, has compromised more than 3,000 US-based organizations and approximately 8,000 victims globally. The scale of these attacks forced vulnerable organizations to shorten their response times so they could effectively counter the threat. However, the sheer volume of data from compromised websites also forced ransomware groups to adapt.
For example, the CL0P ransomware group updated its extortion tactics in 2023. By midyear, CL0P was leveraging torrents to distribute stolen data – a quicker and more efficient method than hosting stolen data on the group’s Tor website. We previously reported this activity in September 2023, and our article provides notable insight on recent CL0P ransomware operations.
CL0P was not the only group exploiting critical vulnerabilities. Ransomware groups like LockBit, Medusa, ALPHV (BlackCat) and others leveraged a zero-day exploit for the Citrix Bleed vulnerability CVE-2023-4966, which led to numerous compromises by these groups in November 2023.
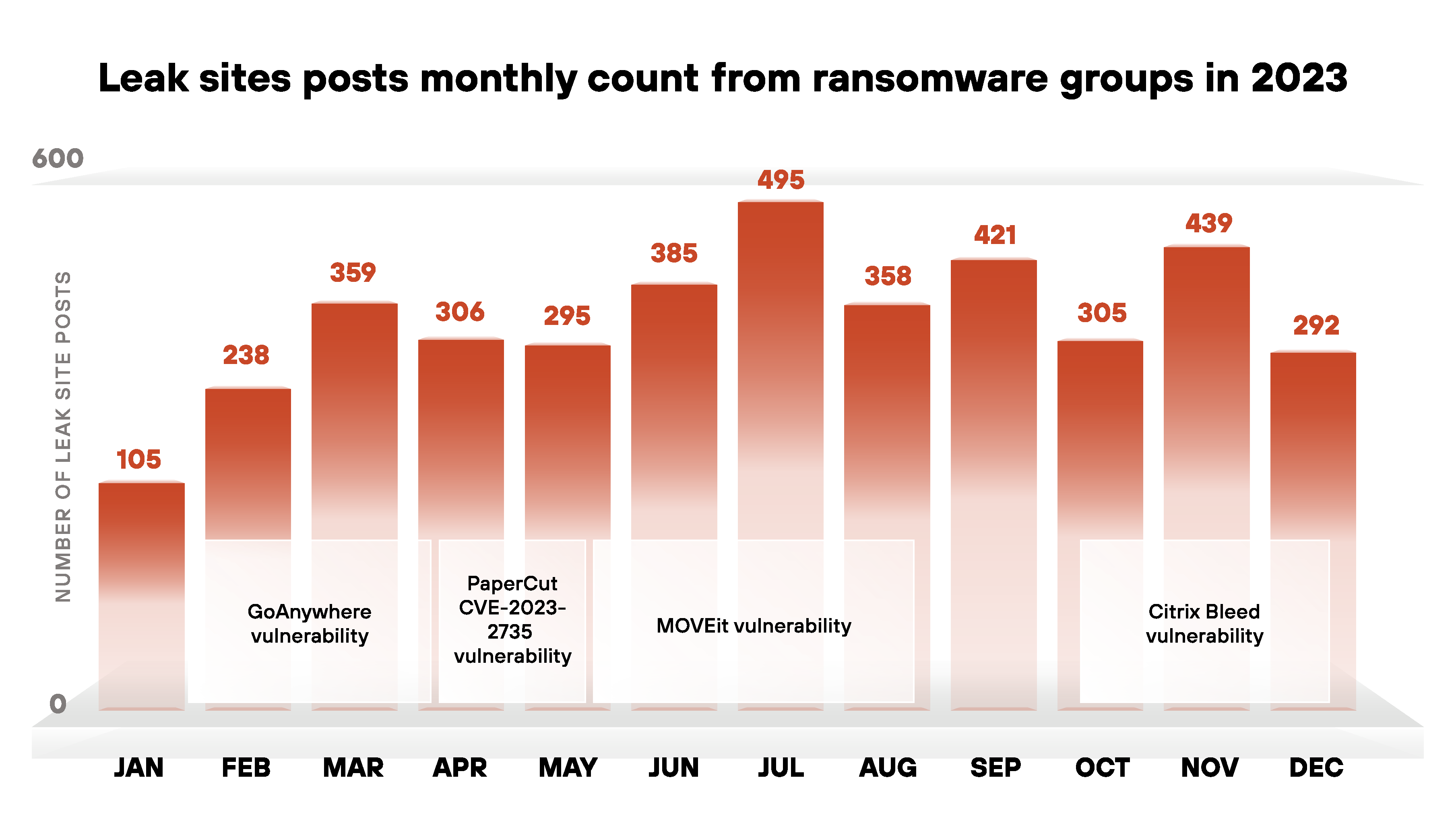
When reviewing the number of compromises reported by ransomware leak sites in 2023 on a month-by-month basis, we find increased compromises during certain months as shown below in Figure 2. These increases loosely align with the dates ransomware groups began exploiting specific vulnerabilities.
Not all ransomware threat actors are capable of leveraging zero-day vulnerabilities. Some ransomware groups are run by inexperienced threat actors who will leverage anything at their disposal.
For example, an unknown ransomware group targeted VMware ESXi environments during a campaign nicknamed ESXiArgs. This campaign exploited CVE-2021-21974, a vulnerability already two years old at the time of the attacks.
According to CISA, ESXiArgs impacted over 3,800 servers. These types of campaigns are usually not posted on ransomware leak sites because the threat actors are interested in a quick payout instead of extorting victims for maximum impact or selling their data. Even though these groups use older exploits, their campaigns can have as much impact as efforts by more experienced ransomware threat actors.
But experienced or not, ransomware threat actors have come and gone in the evolving threat landscape. Let's review the new ransomware threat actors seen in 2023.
Newcomers in 2023
Due to high payouts by victims in recent years, cybercriminals are often enticed by the idea of ransomware as a source of revenue. As these criminals form new ransomware groups, not every attempt is successful or sustainable.
A new ransomware group must consider several challenges not applicable to other malware, such as communicating with victims and increased operational security. The public nature of ransomware operations increases their risk of detection by law enforcement agencies, security vendors and other defenders.
Ransomware groups must also consider their competition. Profit sharing, software capabilities and affiliate support can significantly impact a new group's standing in the highly competitive criminal market for ransomware.
Despite these challenges, the data reveals 25 new leak sites in 2023. These groups have at least launched a ransomware-as-a-service (RaaS) offering, hoping to become a contender in the ransomware marketplace. The names of these threat groups are shown below in Table 1.
Table 1. Names of 25 new leak sites for ransomware that appeared in 2023.
Of note, at least three of these sites were reported as first active sometime in 2022. But we consider these ransomware families as new in our analysis for two reasons. First, even if analysis indicates these ransomware families started operations sometime in 2022, they were all first publicly reported in 2023. Second, leak sites are necessary to become a notable player in today’s criminal ransomware market.
The three ransomware families that reportedly started in 2022 with newly established leak sites in 2023 are:
The new groups reflected by leak site data reveal a competitive criminal market for ransomware. Of the 25 groups with newly established leak sites in 2023, at least five had no new posts in the second half of 2023, indicating these groups might have shut down. Table 2 shows a list of these new ransomware leak sites that might have shut down before the end of 2023.
| Group | Date of Last Leak Site Post |
| U-Bomb | March 20, 2023 |
| CryptNet | April 15, 2023 |
| CrossLock | May 2, 2023 |
| Rancoz | May 2, 2023 |
| DarkRace | June 8, 2023 |
Table 2. Last known date of leak site posts from five new ransomware groups in 2023.
A lack of leak site posts does not necessarily mean these groups have ceased operations. Criminals from these groups could have moved to other types of operations, retreated from public view or merged with other ransomware groups.
If some of these groups did not last the entire year, new threat actors can fill the void. The second half of 2023 revealed posts from 12 new leak sites, indicating these groups might have started later in the year, as indicated below in Table 3.
| Group | Date of First Leak Site Post |
| BlackSuit | June 18, 2023 |
| Cyclops | July 4, 2023 |
| Cactus | July 17, 2023 |
| INC | Aug. 8, 2023 |
| ThreeAM | Aug. 14, 2023 |
| LostTrust (MetaEncryptor) | Aug. 16, 2023 |
| Cloak | Aug. 23, 2023 |
| Ransomed.Vc | Aug. 24, 2023 |
| Meow | Sept. 4, 2023 |
| Knight | Sept. 11, 2023 |
| CiphBit | Sept. 15, 2023 |
| Hunters International | Oct. 19, 2023 |
Table 3. First date of leak site posts from 12 ransomware groups in 2023.
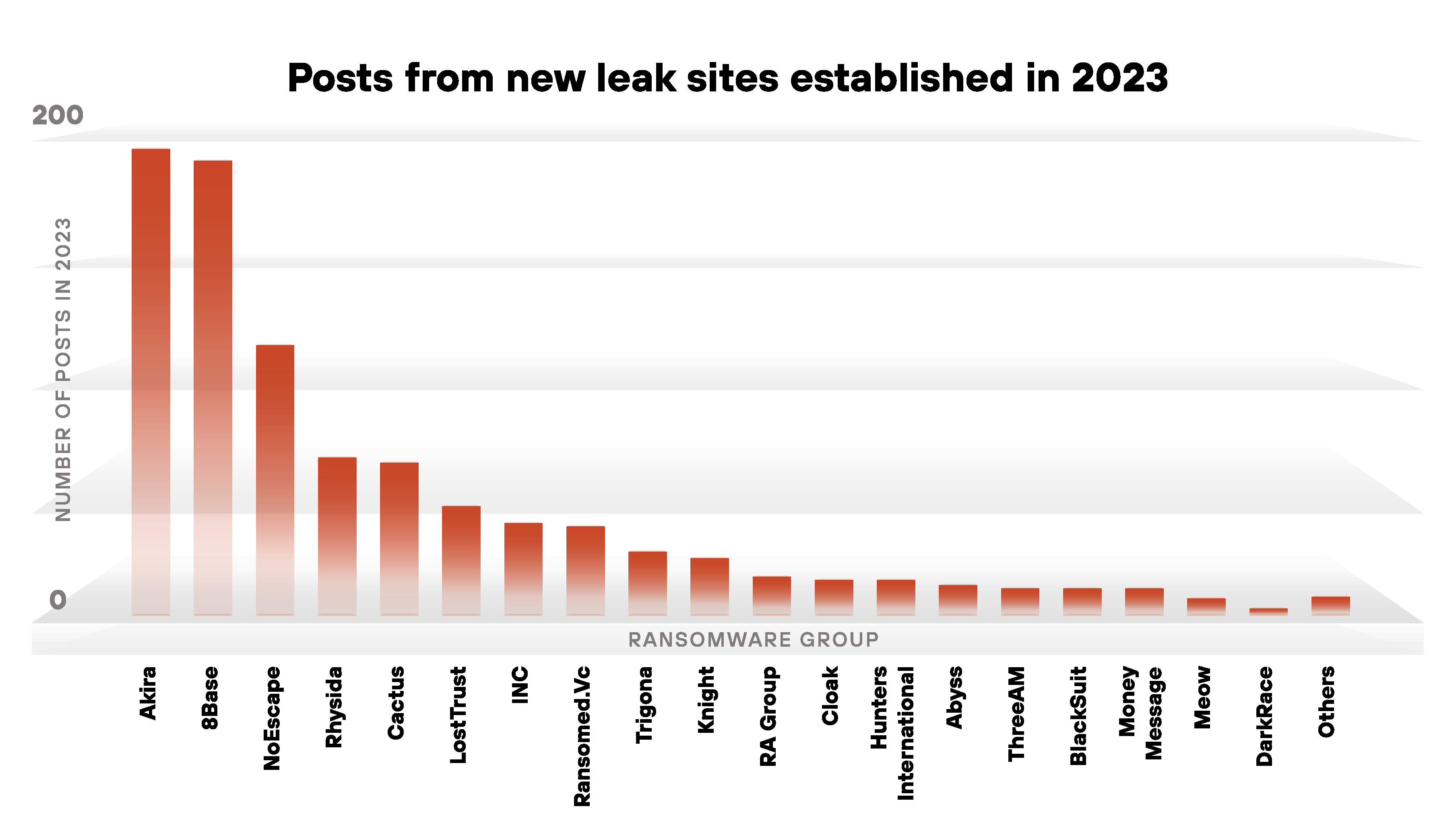
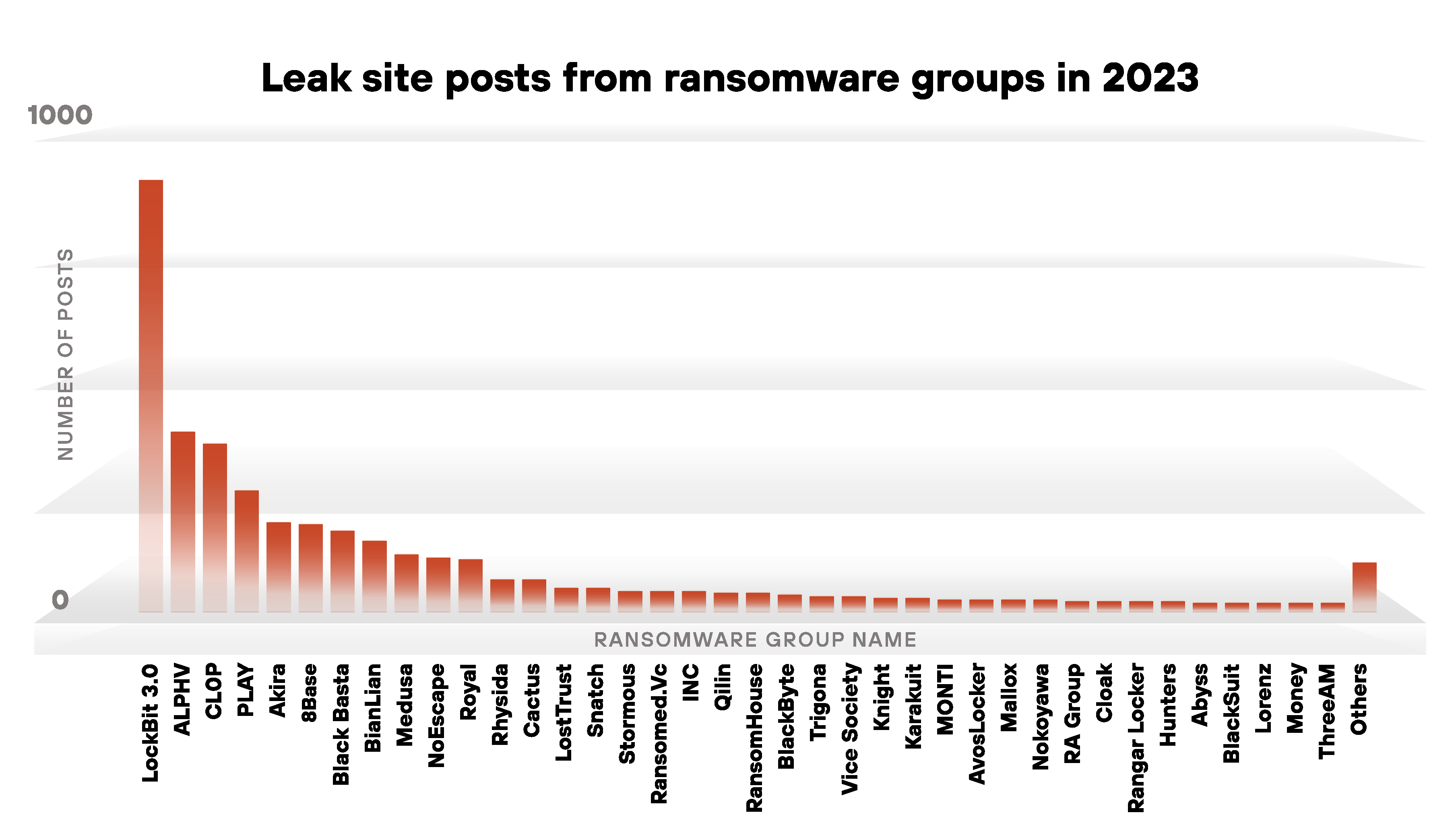
These 25 new leak sites contributed to approximately 25% of the total ransomware posts from 2023. Of these new groups, Akira led with the most posts as illustrated in Figure 3.
First observed in March 2023, Akira has been described as a fast-growing ransomware group, and researchers have linked this group to Conti through cryptocurrency transactions associated with the Conti leadership team.
Second place in the number of leak site posts in 2023 is 8Base ransomware. 8Base is one of the ransomware groups active since 2022, but this group started publicly disclosing its victims in May 2023.
Goners in 2023
2023 saw the downfall of several prominent ransomware groups. Reasons include overexposure and aggressive tactics, which attracted the attention of law enforcement agencies and cybersecurity organizations. These ransomware groups were under a spotlight that led to increased pressure and operational challenges.
The crucial role played by international law enforcement agencies in 2023 cannot be overstated. Their increased collaborative efforts led to major successes in disrupting ransomware operations.
These actions include providing decryption keys to victims, seizing infrastructure and arresting key threat actors. Law enforcement efforts destabilized notable ransomware groups and prevented them from earning as much money. The results forced affiliates to abandon these groups and seek more profitable alternatives.
Let's review some of the notable ransomware operations that appear to have ceased activity in 2023.
Hive
One of the most prolific groups in 2022, Hive ransomware was shut down as part of a law enforcement-led operation reported in January 2023. This operation captured the group's decryption keys and offered them to victims worldwide, saving victims over $130 million in potential ransom payments.
The FBI seized Hive ransomware's main site as shown below in Figure 4. Hive affiliates scattered, and this group disappeared for the remainder of 2023.

Ragnar Locker
Ragnar Locker also felt the wrath of international law enforcement agencies. This group originally started in 2019 and had been very active since then.
In October 2023, Europol reported a coordinated international law enforcement effort that seized Ragnar Locker infrastructure, and the main perpetrator was subsequently presented to the Paris Judicial Court. Figure 5 shows a screenshot of Rangar Locker's Tor site in 2023 shortly after it was taken over by law enforcement.

Ransomed.Vc
Ransomed.Vc started operations in August 2023 and brought attention to itself by claiming responsibility for a compromise of Sony in September. Also known simply as Ransomed, this group ceased operations and put its available infrastructure up for auction near the end of October, making its success very short-lived.
The shutdown likely occurred due to law enforcement intervention. The following month, six individuals affiliated with this group were allegedly arrested.
Trigona
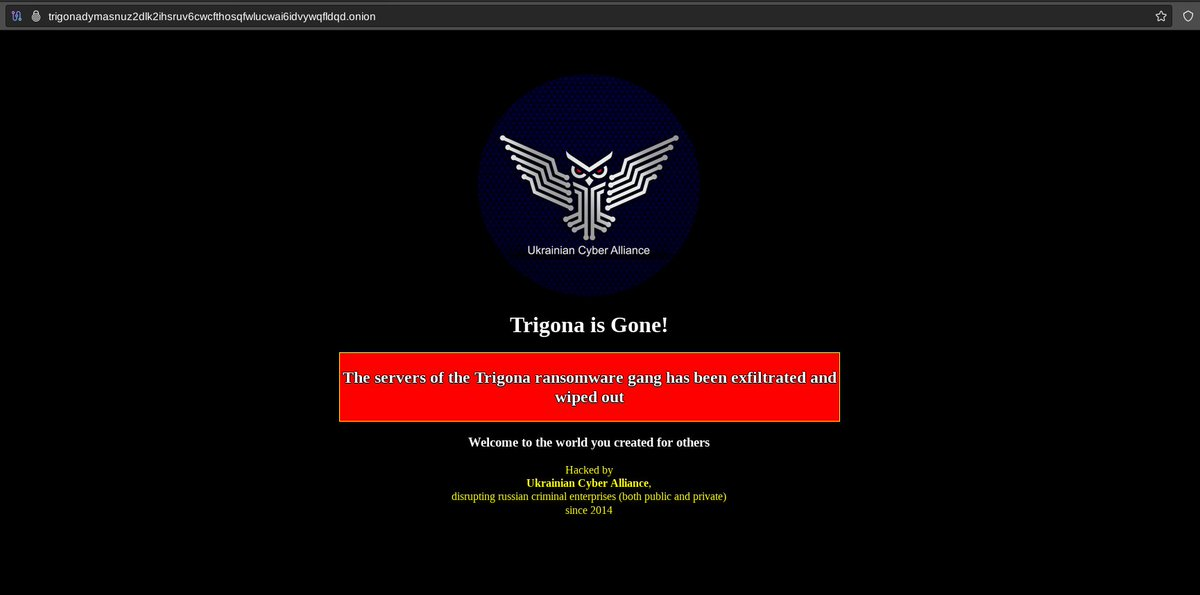
Trigona was another noteworthy ransomware departure in 2023. First spotted in 2022, Trigona was taken down not from law enforcement action, but from the efforts of pro-Ukrainian hacktivists.
A hacktivist group that calls itself the Ukrainian Cyber Alliance took advantage of a Critical vulnerability in Confluence and used a zero-day exploit to access Trigona's infrastructure. The hacktivist group erased all of Trigona's data, an action that ultimately led to the ransomware group's demise.
Below, Figure 6 shows a screenshot of Trigona's Tor site after it was defaced by the Ukrainian Cyber Alliance.
ALPHV (BlackCat): Almost a Goner
Also known as BlackCat, the ALPHV group was hit hard during 2023. In December, the FBI disrupted ALPHV (BlackCat) operations and released a decryption tool that allowed compromised victims to recover their data. This was a huge setback for ALPHV, and it offered incentives to keep its criminal affiliates from being spooked by the FBI. Meanwhile, other ransomware groups like LockBit began poaching ALPHV affiliates.
The ALPHV group has since responded to the FBI disruption and fought back against law enforcement action. But if this group cannot fix its reputation, it could shut down and rebrand as a new ransomware gang.
Possible Rebrands
2023 also saw the sudden disappearance of Royal ransomware and Vice Society. Both were active in 2022 through the first half of 2023 performing multi-extortion strategies, and both have attracted the attention of law enforcement.
Royal ransomware was created by former members of Conti, and it has been involved in multiple high-profile attacks against critical infrastructure. The Royal leak site ceased operations sometime in July 2023. Various sources have reported similarities in code between Royal and the newly established BlackSuit ransomware, indicating a possible rebranding from Royal to BlackSuit.
Vice Society attracted the attention of the public and law enforcement by targeting organizations in healthcare and education. This group stopped posting on its leak site in June 2023, but Vice Society might not have completely vanished. Multiple researchers have linked Vice Society to the newly established Rhysida ransomware, suggesting a rebrand.
One of the new ransomware groups in 2023 appears to have been rebranded during the same year. Leak site data indicates Cyclops ransomware was active in July 2023, but a version 2.0 update of Cyclops was rebranded as Knight ransomware. Cyclops had no more leak site posts after July 2023, while Knight’s leak site posts started later that year in September.
Leak Site Statistics for 2023
Analyzing leak site data provides key insight into the ransomware threat. We reviewed 3,998 leak site posts from 2023, and this data suggests the most active groups, the most affected industries and areas of the world that have been hit hardest by ransomware.
Group Distribution
Of the 3,998 leak site posts from 2023, LockBit ransomware remains the most active, with 928 organizations accounting for 23% of the total.
Operating since 2019 with minimal breaks, LockBit has been the most prolific ransomware group for two years in a row now. With the downfall of groups like Conti, Hive and Ragnar Locker, LockBit has become the ransomware of choice for many threat actors who have subsequently become its affiliates.
LockBit has launched multiple variants that affect both Linux and Windows operating systems. By repurposing freely available software tools and taking advantage of LockBit’s fast encryption, affiliates can tailor ransomware operations to meet their individual needs.
Second place in leak posts was ALPHV (BlackCat) ransomware, with roughly 9.7% of the total leak site posts in 2023. Third place was CL0P ransomware, with approximately 9.1% of 2023’s posts.
CL0P is notorious for utilizing zero-day exploits of critical vulnerabilities like those for Progress Software's MOVEit and Fortra’s GoAnywhere MFT. However, the number of organizations reported by CL0P on the group's leak site might not accurately reflect the full impact of these vulnerabilities.
For example, CL0P's leak site data indicates it had compromised 364 organizations during the year, but a report analyzing CL0P's exploitation of the MOVEit vulnerability in 2023 states 2,730 organizations were affected. This is a prime example of the disparities we often find between leak site data and real-world impact.
Figure 7 illustrates the leak site post count from different ransomware families in 2023.
Monthly and Weekly Averages
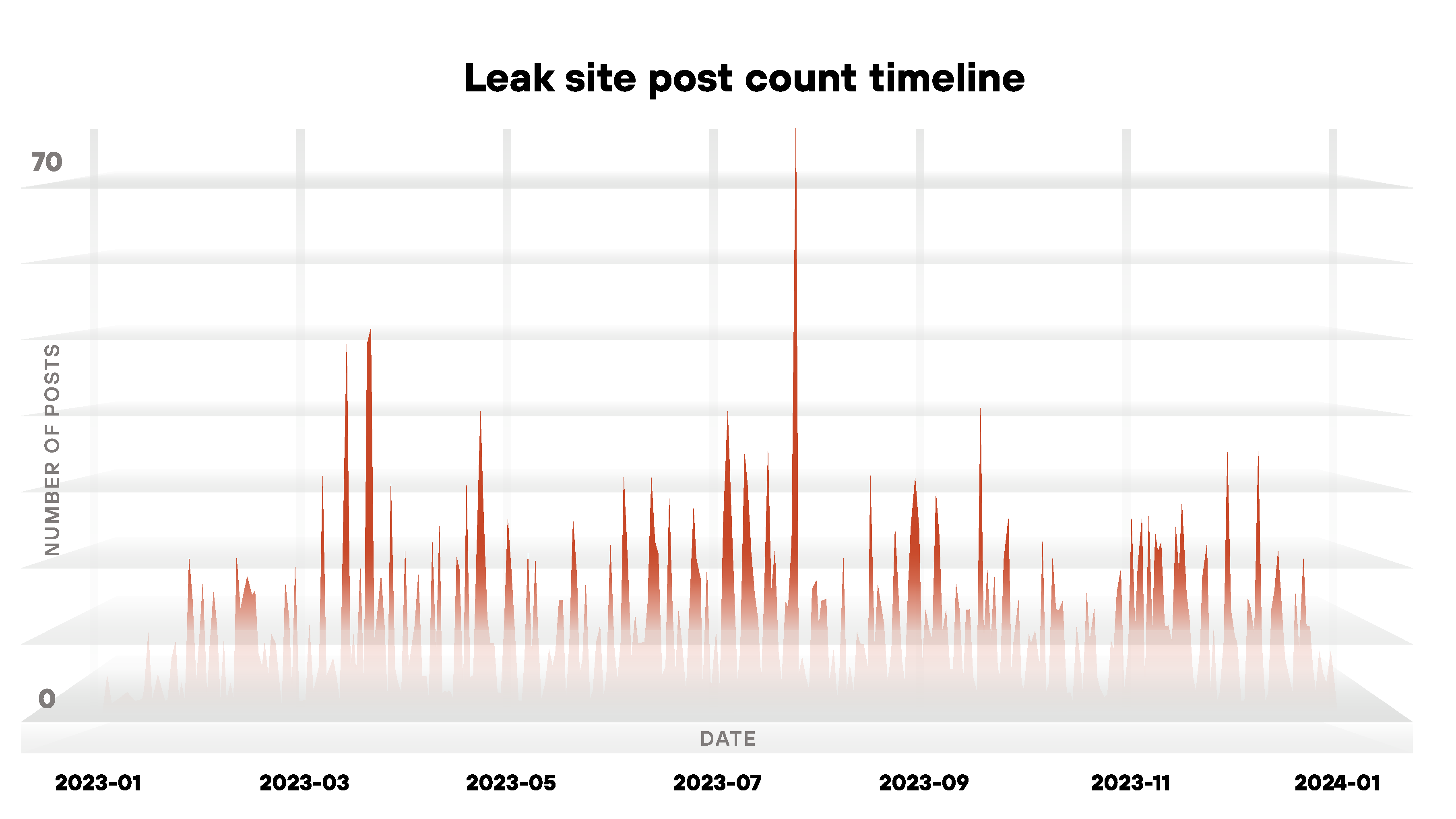
The 3,998 ransomware posts we reviewed mean ransomware groups generated an average of 333 posts per month in 2023. This annual number also equates to an average of almost 77 posts each week. The numbers for 2023 show a growth in ransomware activity compared to 2022.
2022 saw a total of 2,679 leak site posts with an average of 223 each month and an average of 52 each week. The annual total marks a 49% increase of ransomware leak site posts in 2023 compared to the previous year.
The number of leak site reports in 2023 was highest in July, with 495 posts. CL0P had the most posts that month, probably due to its large-scale exploitation of the MOVEit vulnerability.
According to the leak site post count, January and February were the least active months for ransomware in 2023. A line graph illustrating the occurrence of leak site posts throughout the year is shown in Figure 8.
Affected Industries
Some ransomware groups might focus on specific countries or industries, but most are opportunistic and primarily concerned with making a profit. As a result, many ransomware groups compromise organizations across multiple industries.
Leak site posts in 2023 reveal the manufacturing industry was most impacted by ransomware, with 14% of the total posts as shown below in Figure 9.

Why was manufacturing hit the most by ransomware? Manufacturers usually have limited visibility into their operational technology (OT) systems, often lack adequate network monitoring and occasionally fail to implement best security practices.
Geographic Impact
Leak site data reveals most victims in 2023 were based in the U.S., with 47.6% of the total posts. The U.K. was second at 6.5%, then Canada at 4.6% and Germany at 4%. See Figure 10 for a pie chart showing the most affected locations.
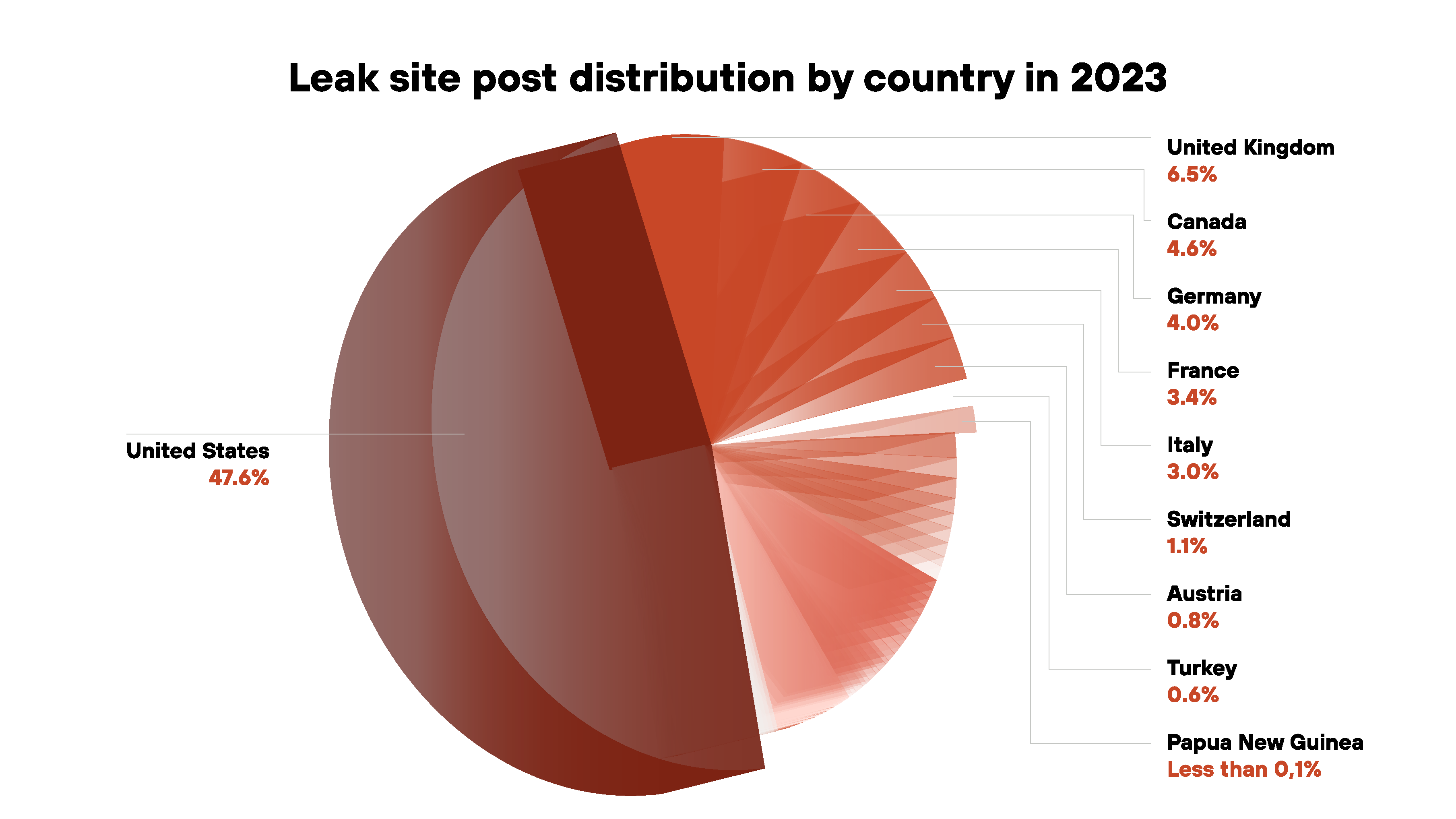
Organizations in the U.S. have been the top target of ransomware since leak sites first appeared in 2019. The U.S. presents a very attractive target, especially when examining the Forbes Global 2000, which ranks the largest companies in the world according to sales, profits, assets and market value. In 2023, the U.S. accounted for 610 of these organizations, consisting of almost 31% of the Forbes Global 2000, indicating a high concentration of wealthy targets.
While ransomware groups tend to target wealthy regions like the U.S., this threat remains a widespread global issue. Leak site data from 2023 reveals victims from at least 120 different countries across the world.
Conclusion
2023 presented a thriving and evolving ransomware landscape as reflected in posts from ransomware leak sites. Posts from these sites indicate a notable increase in activity, and this data also reflects new ransomware groups that have appeared and existing groups that have declined. Although the landscape remains fluid, law enforcement's growing effectiveness in combating ransomware signals a welcome change.
Ransomware groups such as CL0P have used zero-day exploits against newly discovered critical vulnerabilities, which represent a complex challenge for potential victims. While ransomware leak site data can provide valuable insight on the threat landscape, this data might not accurately reflect the full impact of a vulnerability. Organizations must not only be vigilant about known vulnerabilities, but they must also develop strategies to quickly respond to and mitigate the impact of zero-day exploits.
Protections and Mitigations
Palo Alto Networks customers are better protected from ransomware through the following products:
- Advanced WildFire: The Advanced WildFire machine-learning models and analysis techniques are frequently updated with information discovered from our day-to-day research on ransomware.
- Cortex Xpanse: Cortex Xpanse can be used to detect vulnerable services exposed directly to the internet that might be exploitable and infected by ransomware.
- Cortex XDR and XSIAM: All known ransomware samples are prevented by the XDR agent out of the box using the following modules:
- Anti-ransomware module to prevent encryption behaviors on Windows
- Local Analysis prevention for ransomware binaries on Windows
- Behavioral Threat Protection (BTP) rule helps prevent ransomware activity on Windows as well as Linux
- Next-Generation Firewall (NGFW) with Cloud-Delivered Security Services:
- Advanced URL Filtering and DNS Security block related malicious URLs and domains as ransomware, command and control (C2), and malware categories.
- Advanced Threat Prevention can block ransomware threats at both the network and application layers, including port scans, buffer overflows and remote code execution.
- Prisma Cloud: Any cloud infrastructure running Windows virtual machines (VMs) should monitor their Windows-based VMs using Cortex XDR Cloud Agents or Prisma Cloud Defender Agents. Both agents will monitor the Windows VM instances for known malware, using signatures pulled from Palo Alto Networks WildFire.
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Additional Resources
The following reports were referenced in this article. These can provide more insight on ransomware operations, individual ransomware families or specific operations related to ransomware in 2023.
- Dedicated Leak Sites (DLS): Here’s what you should know – Group-IB
- What is Multi-Extortion Ransomware? – Palo Alto Networks
- Allied Universal Breached by Maze Ransomware, Stolen Data Leaked – Bleeping Computer
- What is a zero-day exploit? – IBM
- Tor (Network) – Wikipedia
- Summary of the Investigation Related to CVE-2023-0669 – Fortra GoAnywhere Blog
- Threat Brief - MOVEit Transfer SQL Injection Vulnerabilities: CVE-2023-34362, CVE-2023-35036 and CVE-2023-35708 – Unit 42, Palo Alto Networks
- #StopRansomware: CL0P Ransomware Gang Exploits CVE-2023-34362 MOVEit Vulnerability – U.S. Cybersecurity & Infrastructure Security Agency (CISA)
- CL0P Seeds ^_- Gotta Catch Em All! – Unit 42, Palo Alto Networks
- Understanding Ransomware Threat Actors: LockBit – U.S. Cybersecurity & Infrastructure Security Agency (CISA)
- Medusa Ransomware on the Rise: From Data Leaks to Multi-Extortion – The Hacker News
- #StopRansomware: ALPHV Blackcat – U.S. Cybersecurity & Infrastructure Security Agency (CISA)
- What Is Citrix Bleed? The Next Ransomware Patch You Need – Government Technology
ESXiArgs: Questions & Answers – VMware - CVE-2021-21974 – CVE List, The MITRE Corporation
- ESXiArgs Ransomware Virtual Machine Recovery Guidance – U.S. Cybersecurity & Infrastructure Security Agency (CISA)
- 8Base Ransomware: A Heavy Hitting Player – VMware Security Blog
- Hackers use new 3AM ransomware to save failed LockBit attack – Bleeping Computer
- Abyss Locker Ransomware Looks to Drown VMware's ESXi Servers – Dark Reading
- Akira, again: The ransomware that keeps on taking – Sophos
- [PDF] BlackSuit Ransomware – HC3: Analyst Note
- CACTUS Ransomware Exploits Qlik Sense Vulnerabilities in Targeted Attacks – The Hacker News
- Ransomware review: October 2023 – Malwarebytes
- Cloak Ransomware: Who’s Behind the Cloak? – Cyberint
- Netskope Threat Coverage: CrossLock Ransomware – Netskope
- New RaaS CryptNet Advertised for Double Extortion Attacks in Dark Web Forums – Retail & Hospitality ISAC
- Knight: An analysis of Cyclops’ ransomware successor – Acronis
- Unmasking the Darkrace Ransomware Gang – Cyble
- Hunters International Cyberattackers Take Over Hive Ransomware – Dark Reading
- Inc. Ransom – SentinelOne
- Novel LostTrust ransomware operation emerges – SC Media
- NoEscape Ransomware – HC3: Analyst Note
- Nokoyawa – SentinelOne
- Vanderbilt University Medical Center investigating cybersecurity incident – Recorded Future
- New Money Message ransomware demands million dollar ransoms – Bleeping Computer
- Newly identified RA Group compromises companies in U.S. and South Korea with leaked Babuk source code – Cisco Talos
- Ransomware Roundup - Rancoz – Fortinet
- The Emergence of Ransomed: An Uncertain Cyber Threat in the Making – Flashpoint
- #StopRansomware: Rhysida Ransomware – U.S. Cybersecurity & Infrastructure Security Agency (CISA)
- U-Bomb – SentinelOne
- Bee-Ware of Trigona, An Emerging Ransomware Strain – Unit 42, Palo Alto Networks
- Conti and Akira: Chained Together – Arctic Wolf
- 8Base Ransomware [PDF] – Health Sector Cybersecurity Coordination Center (HC3): Analyst Note
- #StopRansomware: Hive Ransomware – U.S. Cybersecurity & Infrastructure Security Agency (CISA)
- U.S. Department of Justice Disrupts Hive Ransomware Variant – Office of Public Affairs, U.S. Department of Justice
- Hive Ransomware Operation Shut Down by Law Enforcement – Security Week
- Ragnar Locker ransomware gang taken down by international police swoop – Europol
- Sony was attacked by two ransomware operators – Malwarebytes
- Get your very own ransomware empire on the cheap, while stocks last – The Register
- Ransomed.vc gang claims to shut down after six affiliates allegedly arrested – Recorded Future
- CVE-2023-22515 - Broken Access Control Vulnerability in Confluence Data Center and Server – Atlassian Support
- Ukrainian activists hack Trigona ransomware gang, wipe servers – Bleeping Computer
- Servers of the Trigona ransomware gang has been exfiltrated and wiped out – X (Twitter)
- Justice Department Disrupts Prolific ALPHV/Blackcat Ransomware Variant – Office of Public Affairs, U.S. Department of Justice
- AlphV ransomware site is “seized” by the FBI. Then it's "unseized." And so on. – ArsTechnica
- LockBit ransomware now poaching BlackCat, NoEscape affiliates – Bleeping Computer
- BlackCat Rises: Infamous Ransomware Gang Defies Law Enforcement – Infosecurity Magazine
- Threat Assessment: Royal Ransomware – Unit 42, Palo Alto Networks
- Vice Society: Profiling a Persistent Threat to the Education Sector – Unit 42, Palo Alto Networks
- #StopRansomware: Royal Ransomware Update [PDF] – U.S. Cybersecurity & Infrastructure Security Agency (CISA)
- CISA, FBI warn that Royal ransomware gang may rebrand as ‘BlackSuit’ – Recorded Future
- Rhysida, the new ransomware gang behind British Library cyber-attack – The Guardian
- Threat Alert: Cortex vs. LockBit 3.0 – Palo Alto Networks
- Conti Ransomware Operation Shut Down After Brand Becomes Toxic – Security Week
- LockBit wins ransomware speed test, encrypts 25,000 files per minute – The Register
- Clop ransomware gang begins extorting GoAnywhere zero-day victims – Bleeping Computer
- Ransomware Attacks Increasingly Targeting Manufacturers – NAM News Room, National Association of Manufacturers
- Unpacking the MOVEit Breach: Statistics and Analysis – Emsisoft
- The Global 2000 – Forbes
Updated on Feb. 20, 2024 at 12:56 p.m. PT.
Updated on April 25, 2024 at 2:10 p.m. PT.












 Get updates from Unit 42
Get updates from Unit 42