Intro
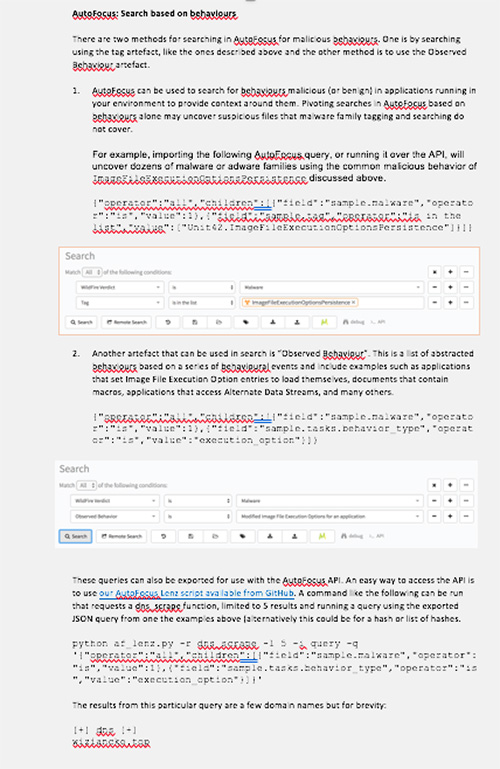
In December 2016 I posted the first of a two-part blog series, the second of which posted in April this year, to start a series of regular threat report updates to the public covering different sets of countries from around the EMEA (Europe Middle East and Africa) region. This blog is the first of a new series of bi-monthly threat reports that will focus only on one set of countries where before the series focused on two sets covering six or more countries. This new series will dig deeper into current trends, the threats affecting each country, and provide useful tips for mitigating these threats via our AutoFocus Threat Intelligence Service.
In my previous blogs, I introduced the EMEA region at a high-level– a large group of countries each with mixed languages, cultures, and cyber security maturity levels. Each also with different industry sectors and different economic profiles, which in turn creates a very diverse environment potentially ripe for cyberattacks.
The countries in this blog includes the United Kingdom, Germany, and France for the month of February.
Headlines
- France, Germany, and United Kingdom: Cerber ransomware remains prevalent and replaced Locky as the #1 volume-wise.
- France, Germany, and United Kingdom: Increase in malware that attempts to interact with digital currencies.
- France and United Kingdom: Uptick in Spora ransomware delivered over web-browsing application.
Trends
February by Country
We saw almost 120,000 total malicious sessions in AutoFocus in the three countries. Of these sessions, the United Kingdom received just over 70%; France just over 20% and Germany just under 10% of the volume. Despite the low session volume, Germany received the highest number of raw samples with nearly 50% of the total at 3,970 unique samples from the near 8,500 total. The United Kingdom received almost the same number of samples as Germany while France saw the lowest amount at just over 3,000 (35%).
The total session volume is some 50,000 less than the same three countries in December 2016 but the sample count in February was much higher with over 2,000 more samples compared to the previous time period.
Almost 50% of the aggregate samples and just over one third of the session volume in Germany can be attributed to the legacy – now some 13 years old – worm, MyDoom.
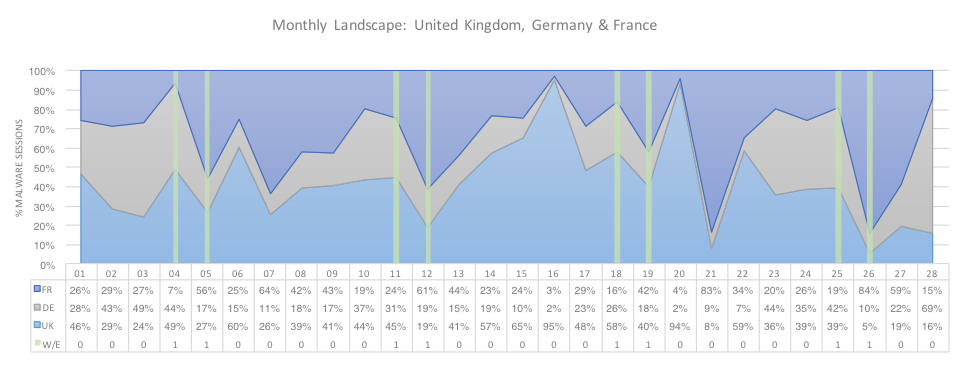
Figure 1 below shows the general trends of malicious sessions throughout the month of February for each country and highlighting the weekends where volume generally decreases. During the weekends, we tend to see less malspam inbound to organisations as people are not there to receive it and for the same reason, less outbound malicious session volume such as web-browsing. The United Kingdom’s most affected industry in terms of volume of malware sessions was Higher Education while both Germany and France’s most affected industry vertical was High Tech.
Figure 1: Daily malware sessions by Country, February 2017
The proportion of malware sessions we observed in these countries could be due to a variety of reasons, such as different malware families in active operations, the number of existing compromised hosts, or even how the Palo Alto Networks® security platform is deployed.
February’s Top Malware
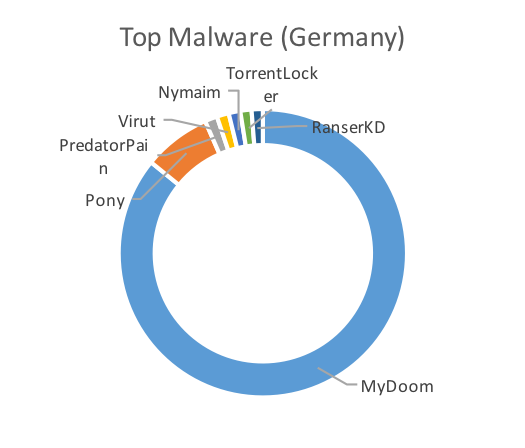
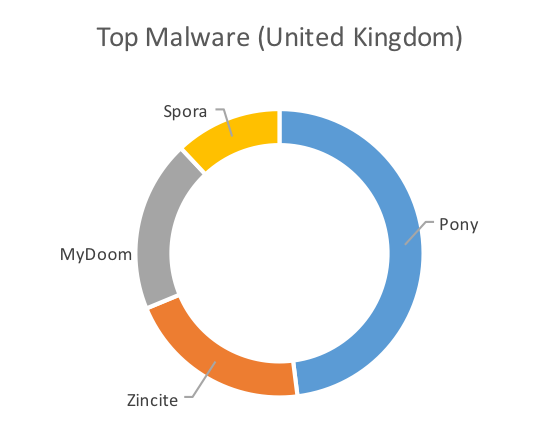
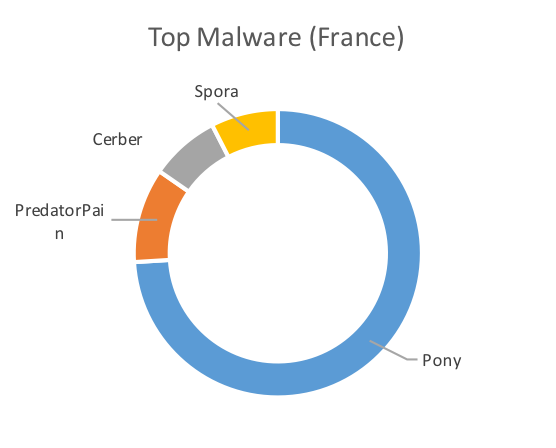
The following charts show the top malware by way of the highest number of unique samples seen targeting each of the three countries.
The charts clearly show overlap between the countries and the malware observed in the region. Pony, for example accounted for almost half of the malware in the United Kingdom and almost three-quarters of the top malware in France. MyDoom, on the other hand, dominated the German charts. Beyond MyDoom, Germany also saw a higher number of malware families that were present in the other countries as well. These included two ransomware families, Nymaim and RanserKD.
Figure 2: Top Malware by Country, February 2017
February by application
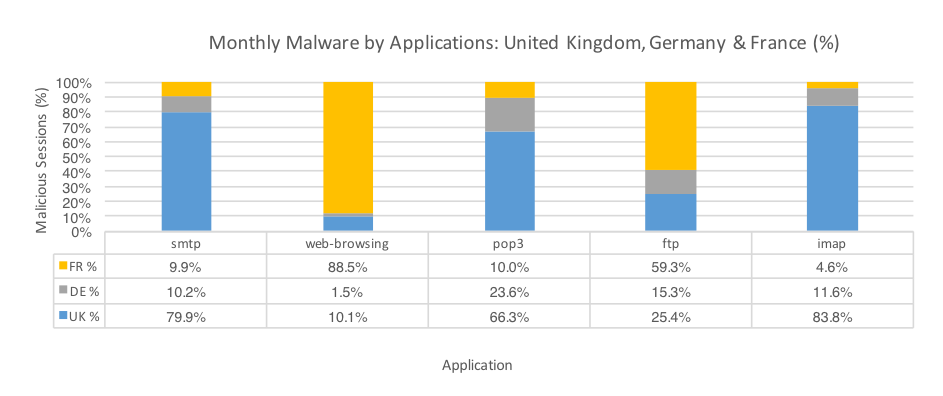
Figure 3 plots the three countries in terms of malware volume delivered via different applications. The most common method for malware delivery were email protocols with SMTP, POP3, and IMAP being the highest combined volume of malware sessions by far. This is in-line for malware delivery activity globally. Based off these metrics, we can deduce that social engineering via specially crafted phishing emails is still a heavily used attack method.
The SMTP volume breakdown between the three countries indicates the UK received the most malicious sessions by far. The malware in the bulk of these SMTP sessions consisted of Pony and Cerber.
Figure 3: Malware sessions by application by Country, February 2017
Pony is a popular downloader program that can download additional malware onto the infected system. It is also equipped with a number of plugins that may be used to steal stored credentials for various applications such as FTP clients, web browsers, email clients, and other software. Pony is also commonly known as Fareit.
This commodity Trojan is common and often seen in high volumes throughout the world. Although this sparkline indicates what appears to ![]()
be a slight decline in February as compared to three to four months prior, the session volume still averages well over two thousand per day. For the three countries examined, the industries most targeted were Higher Education in the United Kingdom, Aerospace and Defence in France, and High Tech in Germany.
Globally, over the past six months, Cerber ransomware activity has been voluminous at over half a million sessions in total, much of which occurred in January and early February. Some individual days reached well into the tens of thousands of sessions. The industries most targeted included Higher Education in the United Kingdom, Government in France, and Wholesale in Germany.
Cerber is similar to many other ransomware families – using encryption, bitcoin ransom, and the TOR network for anonymity. It does have a few unique aspects not found in other ransomware however. Aside from the file extension ".cerber" used to indicate encrypted files, Cerber has conditional behaviour based on the language settings of the operating system. It will avoid infecting the following locales: Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine and Uzbekistan. Cerber has been observed attacking databases as well as typical files. Infection methods are varied, including the use of malicious attachments in emails, malicious links, and the use of Exploit Kits. The Cerber malware payload uses a polymorphic model on its distribution servers making it very difficult for signature-based detection approaches to keep up with detecting all variants.
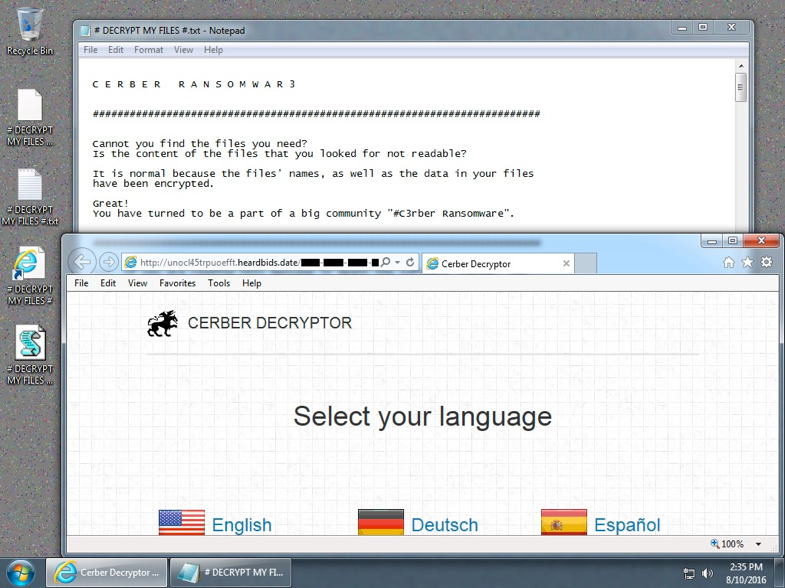
The following Figure shows a typical view of an system infected by Cerber including the ransom notice and support for the victim to get their files decrypted.
Figure 4: Cerber Ransomware infection
 In France, we saw the highest volume of web-browsing sessions in February, followed by the United Kingdom and finally Germany. The majority of this volume in France was due to samples of Spora ransomware. Many ransomware attacks include a try-before-you-buy feature on their pay pages, where you can decrypt one or two files for free as an inducement to trust the crooks. Spora has many options such as: decrypt two files for free; decrypt a selection of files for $30; have the ransomware itself removed for $20; buy “immunity” for $50; and get a full restore for $120. Prices are quite low compared to other families that still charge one Bitcoin, which has almost doubled in value since the start of 2017 and is currently over the $2,000 USD mark. Spora seemed to appear on the ransomware scene earlier this year and since then as risen by hundreds if not thousands of sessions
In France, we saw the highest volume of web-browsing sessions in February, followed by the United Kingdom and finally Germany. The majority of this volume in France was due to samples of Spora ransomware. Many ransomware attacks include a try-before-you-buy feature on their pay pages, where you can decrypt one or two files for free as an inducement to trust the crooks. Spora has many options such as: decrypt two files for free; decrypt a selection of files for $30; have the ransomware itself removed for $20; buy “immunity” for $50; and get a full restore for $120. Prices are quite low compared to other families that still charge one Bitcoin, which has almost doubled in value since the start of 2017 and is currently over the $2,000 USD mark. Spora seemed to appear on the ransomware scene earlier this year and since then as risen by hundreds if not thousands of sessions ![]() per day, indicating that it may be a threat that will be with us for some time. Many of the web-browsing sessions containing Spora ransomware use legitimate-sounding filenames such as “Chrome font v4.11.exe” that purport to be font files or other updates related to the Google Chrome web browser. Many sites hosting the malware appear to be compromised websites and in February, the majority of such sites were education-related, such as “edenhope.vic.edu[.]au/free.php”. The PHP (server side scripting framework used in web development) files often use filenames such as get, free, and info. The targeted industries globally are Higher Education followed by Securities and Investment Services. For the three countries examined, the industry most targeted was Higher Education.
per day, indicating that it may be a threat that will be with us for some time. Many of the web-browsing sessions containing Spora ransomware use legitimate-sounding filenames such as “Chrome font v4.11.exe” that purport to be font files or other updates related to the Google Chrome web browser. Many sites hosting the malware appear to be compromised websites and in February, the majority of such sites were education-related, such as “edenhope.vic.edu[.]au/free.php”. The PHP (server side scripting framework used in web development) files often use filenames such as get, free, and info. The targeted industries globally are Higher Education followed by Securities and Investment Services. For the three countries examined, the industry most targeted was Higher Education.
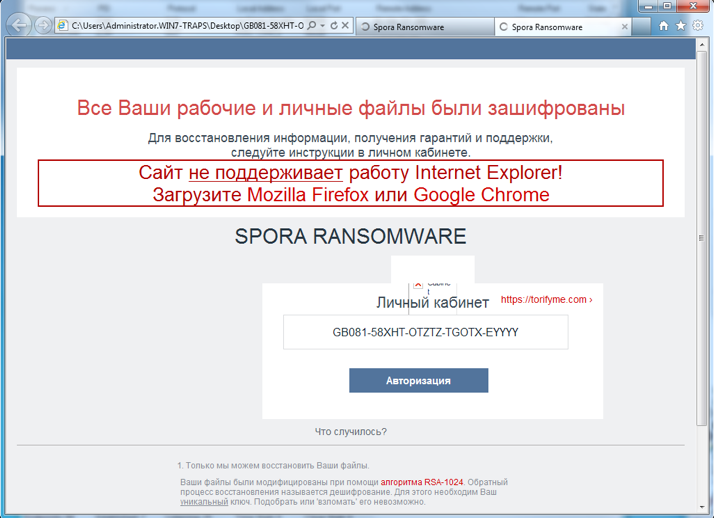
Figure 5 shows a typical view of a system infected by Spora, showing the ransom notice and support details for the victim.
Figure 5: Spora Ransomware infection
FTP as a malware delivery mechanism also deserves a mention as the activity remains quite high. This behavior has been ongoing for quite some time now, primarily due to the PhotoMiner malware I discussed in my last blog covering the EMEA region.
Threats
Country Specific
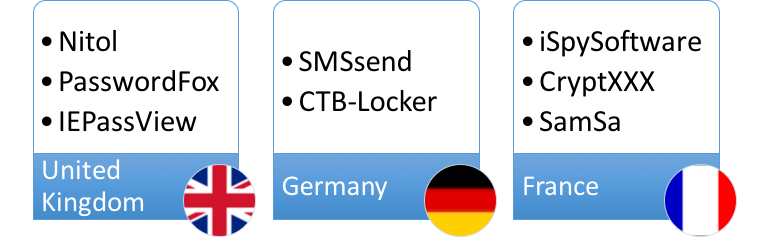
We can see further anomalies between the different countries, as Figure 6 below highlights. Despite the vast majority of malware families being common across all three countries and globally, there are some malware families, only in observed in one country. The following section describes each of these unique threats per country and shows their global trends for the last six months in the form of sparkline charts highlighting each malware’s peak and trend over the extended period.
Figure 6: Unique malware families, by Country, February 2017
Starting with the United Kingdom and the Nitol Trojan, which we have seen quite consistently over the past six ![]() months, showing a spike of high volume towards the end of last year and slightly higher volume of traffic over the last two months. Nitol is a family of Trojans that perform DDoS (Distributed Denial of Service) attacks, allow remote access, download, and run additional files, and perform a number of other malicious activities on the victim host. In February, this malware was seen only in the Higher Education sector in the UK being downloaded with the filename “vip.exe”.
months, showing a spike of high volume towards the end of last year and slightly higher volume of traffic over the last two months. Nitol is a family of Trojans that perform DDoS (Distributed Denial of Service) attacks, allow remote access, download, and run additional files, and perform a number of other malicious activities on the victim host. In February, this malware was seen only in the Higher Education sector in the UK being downloaded with the filename “vip.exe”.
The next threats only seen in the United Kingdom were PasswordFox and IEPassView both of which are command-line utilities allowing for the extraction of usernames and passwords saved in Firefox and Internet Explorer, respectively. Both utilities are developed by NirSoft as stand-alone tools to help with password recovery but as with such things, others find more nefarious uses for them.
Trends over the extended time period highlight a very similar pattern of volume globally between IEPassView![]() and PasswordFox
and PasswordFox ![]()
Despite sharing similar peaks, including the highest peak for both Trojans in the month of February itself, IEPassView has a higher average number of sessions per day at 7.5 compared to PasswordFox’s daily average of 3. IEPassView also accounts for almost three times the total volume during the extended time period compared to PasswordFox, indicating that targeting stored credentials in Internet Explorer may yield better results for the threat actors.
Session information reported in AutoFocus indicates that the attacks seen in February were targeting Senior lecturers and Professors at Universities in the United Kingdom using spear phishing emails with leading subject lines such as “RE:Bank payment receipt” and attached malware using file names such as “payment receipt order_February.scr”. All SMTP sessions originated from Nigeria with a mixture of sender email addresses including a potentially compromised business email address from a hotel chain based in the Middle East. AutoFocus does not relate these attacks to those detailed in our SilverTerrier white paper, however the objective of stealing credentials and information from victims is on par with other attacks originating from that region of Africa.
In Germany, two of the four top malware families observed are Android based, which is something not seen in previous threat reports produced over the last six to nine months.
Android/SMSsend is a malicious mobile application that, once installed to your mobile device, reaps profit by silently sending SMS messages to premium-rate phone numbers increasing the bill from your provider.AutoFocus sessions indicate that some of the SMSsend samples seen were not being used in a malicious manner but instead uploaded to the internet to specialist websites that aid with the de-compilation of the Android app’s Dalvik byte code into source code. Given the source of these sessions – Higher Education – it’s highly likely the samples were being analyzed by students or faculty. Other sessions however do indicate potentially real cases of the malware being downloaded over web-browsing applications from sites that could be 3rd party app stores with less security restrictions.
Alternatively, these malware samples could have been delivered from compromised or other malicious websites where if a victim browsed the site from and Android devices a drive-by-download would occur. The app would then be automatically downloaded to the user’s device but not be installed automatically unless an exploit of some sort was used in conjunction. Often times, when the threat actor has no such exploit available they will rely on social engineering to lure the user into installing the app.
The sessions show Securities and Investment Services and High-Tech industries as those having the most SMSsend activity using file names such “FreeCola1.apk”. The trend for this malware globally over the extended time period shows a general decline since 6 months ago but clearly activity ![]() persists.
persists.

The CTB-Locker family of ransomware is similar to the CryptoLocker family of ransomware as well as many other ransomware families. It encrypts files with specific extensions using a key retrieved from a server, requests ransom in Bitcoin and also uses the Tor network to further protect its operators’ identity and infrastructure. Globally the trend for CTB-Locker has been downward in ![]() the last six months, since the peak of activity about three months ago, and generally speaking we currently see approximately only fifteen sessions on average each day.
the last six months, since the peak of activity about three months ago, and generally speaking we currently see approximately only fifteen sessions on average each day.
In Germany, the POP3 email sessions of CTB-Locker were primarily observed in the Hospitality sector, originating from Italy and using sender email addresses purporting to be from Telecom Italia or SDA (an Italian express courier company) with appropriate subject lines such as Fattura TIM linea Fissa - Gennaio 2016 scadenza 01/14/2016 (Invoice TIM Fixed Line – January 2016 deadline) and Partenza spedizione (Shipping Departure) respectively. Filenames of attached executables followed suite and used double extensions such as “.pdf.exe”, which is a highly suspect behavior.
Meanwhile, in France, some of the unique malware families seen included an off the shelf keylogger – iSpySoftware – which is marketed to unsophisticated actors as a way to harvest credentials and other sensitive information from victims.
All SMTP sessions seen in February targeted the Higher Education sector and originated from China and Thailand. Globally there has been a slight resurgence![]() in volume of late but nothing compared to the scale seen three months ago and prior.
in volume of late but nothing compared to the scale seen three months ago and prior.
 Another malware family unique to France during February was CryptXXX. The group behind this project is the same as those driving
Another malware family unique to France during February was CryptXXX. The group behind this project is the same as those driving ![]() the legacy Reveton ransomware operations and is closely tied to Angler and Bedep operations. This malware has also been on a decline globally since five to six months ago and on average is seen in less than ten sessions per day. The number of sessions in France was low – less than twenty for the month of February.
the legacy Reveton ransomware operations and is closely tied to Angler and Bedep operations. This malware has also been on a decline globally since five to six months ago and on average is seen in less than ten sessions per day. The number of sessions in France was low – less than twenty for the month of February.
Another ransomware family seen exclusively in France in February was SamSa, also know as mokoponi. SamSa is different from most ransomware families in that it tends to target entire organizations versus individual endpoints. Instead of the indiscriminate methods used by most other contemporary ransomware families, leveraging mass malspam or phishing campaigns, SamSa attackers infiltrate the victim's network using network-based exploits or stolen credentials, and proceeds to install SamSa manually on individual hosts. SamSa will encrypt files using a provided RSA public key and demand either a large sum of Bitcoin in exchange for the recovery key to all victimized machines, or a small Bitcoin fee per infected machine.
Much of the activity ![]() in the last six months surrounding SamSa happened two to three months prior to February where session volume peaked at over a hundred sessions per. Recently in February there has been a small uptick in activity.
in the last six months surrounding SamSa happened two to three months prior to February where session volume peaked at over a hundred sessions per. Recently in February there has been a small uptick in activity.
Malicious Behaviours
As mentioned in my last blog on EMEA threat trends, malicious behaviours can be a powerful way of discovering new threats or suspicious applications in the network. The reason being that many malicious behaviours span across multiple malware families of the same type or even different types of malware, such as ransomware or a credential stealing Trojans. Persistence mechanisms, evasion techniques, or communicating channels often times common between malware families. In this next section, we will investigate some of the most prevalent behaviours that were on the rise in the three studied countries in February as well as globally over the five months prior.
![]() HttpNoUserAgent identifies applications that create HTTP connections but omit or use a blank user-agent. Typically, legitimate applications will include a user-agent value in HTTP requests to identify themselves to the receiving application. HTTP requests without the user-agent header, or with a blank user agent value, are may be suspect. This AutoFocus tag identifies these suspect samples, which have been continuously on the rise globally. Global session averages close to twenty thousand sessions per day.
HttpNoUserAgent identifies applications that create HTTP connections but omit or use a blank user-agent. Typically, legitimate applications will include a user-agent value in HTTP requests to identify themselves to the receiving application. HTTP requests without the user-agent header, or with a blank user agent value, are may be suspect. This AutoFocus tag identifies these suspect samples, which have been continuously on the rise globally. Global session averages close to twenty thousand sessions per day.
With digital currency values soaring, performing nefarious activities related to mining digital currency using victim CPU cycles or simply by stealing digital wallets through targeted credential theft are popular avenues for threat actors for financial gain. The AccessDigitalCurrency tag in AutoFocus reports applications seen in our Wildfire analyzer attempting to interact with known digital currencies, such as Bitcoin, Litecoin, and others. Malware will often seek out wallets for various digital currencies with the intent of stealing this data.
Globally, this type of malware as been on the rise as indicated by this sparkline. ![]()
Image File Execution Options (IFEO) are used by developers for debugging applications on Windows. Malware will often check if debuggers are running when they infect a system as it may be an indication that someone is monitoring the system behaviour. This AutoFocus tag however is indicative of an application to setup itself up as a debugger for the system. The Windows operating system then enumerates application names and, when they run, launch the debugger (in this case the malware) at the same time. This provides the malware persistence on the system in case of reboot or application closure.
Globally the volume ![]() of applications conducting this behaviour has averaged in the hundreds of sessions per day but in January and February this spiked to thousands and, in quite a few cases, in to the tens of thousands of sessions per day.
of applications conducting this behaviour has averaged in the hundreds of sessions per day but in January and February this spiked to thousands and, in quite a few cases, in to the tens of thousands of sessions per day.
Malicious Word documents often use VBA (Visual Basic for Application) macros to launch PowerShell scripts to perform malicious activity such as downloading payloads from the internet. This AutoFocus tag highlights when this behaviour is seen during WildFire analysis.
Globally, the volume ![]() of samples conducting this behaviour is on the rise with some of the greatest volume to date being seen in February, where daily session numbers came close to breaking the one hundred thousand sessions per day mark. On the 20th February the session volume exceeded that, with over one hundred and twenty five thousand sessions. Given the earlier discussion about email-based malspam and phishing campaigns being so prevalent, it’s hardly any wonder this behaviour is growing so quickly as many attacks prefer weaponized Word and Excel documents that launch PowerShell.
of samples conducting this behaviour is on the rise with some of the greatest volume to date being seen in February, where daily session numbers came close to breaking the one hundred thousand sessions per day mark. On the 20th February the session volume exceeded that, with over one hundred and twenty five thousand sessions. Given the earlier discussion about email-based malspam and phishing campaigns being so prevalent, it’s hardly any wonder this behaviour is growing so quickly as many attacks prefer weaponized Word and Excel documents that launch PowerShell.
 Indicates where samples request a shortened URL provided by one of the many URL shortening services, which is leveraged often by malware to disguise potentially malicious web requests. In the six months prior to February the malware that typically had this behaviour appeared to be Adware related. The volume of sessions
Indicates where samples request a shortened URL provided by one of the many URL shortening services, which is leveraged often by malware to disguise potentially malicious web requests. In the six months prior to February the malware that typically had this behaviour appeared to be Adware related. The volume of sessions ![]() peaked about two to three months ago but since then, session the volume has been quite consistent.
peaked about two to three months ago but since then, session the volume has been quite consistent.
Conclusion
EMEA is a socially and economically diverse region with many interesting assets whether they be citizen data, financial information, or natural resources and, as such, is a target for cyber criminals the world over.
It’s probably no surprise to see ransomware as a prevalent malware crossing all borders into all countries as this malware is really victim-agnostic. Any data on any computer in any country is a viable target. We saw a slight change with one family, Spora, which made an appearance over the web-browsing application as opposed to the typical method of malspam over smtp.
Clearly information-stealing malware, such as Pony and tools, such as PasswordFox and IEPassView, are prevalent in countries that have a more service-based economy that manage and process plenty of user data and personally identifiable information (PII).
Cyber Hygiene
The threat landscape is vast and can be complex but you can minimize your risk of infection and enhance the overall health of your network by following some basic cyber hygiene habits:
Patch systems and applications wherever (and as soon as) possible. Alternatively, focus on other security solutions, such as exploit prevention technology to protect those systems and applications from attack or to help manage patching cycles to suit your requirements. Prioritize patching based on known exploits or in-the-wild-attacks. Segment those unpatched/unpatchable devices in the network with additional access controls based on users or application communication to minimize the risk of exploitation. Perform regular vulnerability scans of systems and review changes to spot new devices or changes in active vulnerabilities.
Change the file association for JavaScript to be opened using notepad (or something else benign) rather than the Windows Scripting Host or other shell capable of executing malcode. This can be done per PC or enterprise-wide using Group Policy. This will prevent many JavaScript-based threats from running in the context of weaponized documents.
Educate users and employees of the security risks faced by your organization and perform regular training and reminders about these and how they can help the effort. Provide a platform for users to learn about the risks and to report incidents to security-related staff. Create a culture whereby such reporting is important and valued. Monitor effectiveness of training for the purposes of gap analysis and creating dialogue between security teams and users.
Register for Ignite ’17 Security Conference
Vancouver, BC June 12–15, 2017
Ignite ’17 Security Conference is a live, four-day conference designed for today’s security professionals. Hear from innovators and experts, gain real-world skills through hands-on sessions and interactive workshops, and find out how breach prevention is changing the security industry. Visit the Ignite website for more information on tracks, workshops and marquee sessions.



















 Get updates from Unit 42
Get updates from Unit 42