In October 2014, Malwarebytes identified a campaign based on thousands of compromised websites that kicked off an infection chain to Angler exploit kit (EK). It was named "EITest" campaign, because "EITest" was a variable consistently found in injected scripts across all of the compromised websites. Malwarebytes noted some changes in this campaign in 2015 and 2016.
Like others in the cybersecurity threat research community, we have been tracking the EITest campaign. This blog post focuses on network traffic and how indicators have changed over time.
The Evolution of EITest
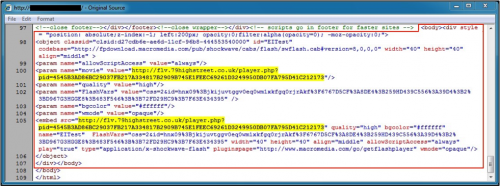
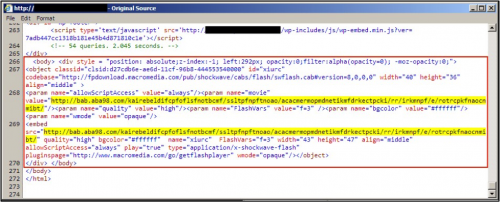
We first saw traffic related to this campaign in September 2014. Since then, patterns for injected script in the compromised websites have remained consistent. Only the URLs and variable names have changed.
Figure 1: Injected script from the EITest campaign in September 2014.
Figure 2: Injected script from the EITest campaign in March 2016.
The EITest gate occasionally changes IP addresses, but since January 2016, this campaign used the 85.93.0.0/24 block. So far this year, the TLD for these domains has most often been .tk, but other TLDs are also used. Below is a list with the date, IP address, and domain we have seen for the EITest gate URL
- 2014-09-22: 148.251.56[.]156 - flv.79highstreet.co[.]uk
- 2014-10-02: 148.251.56[.]156 - fix-mo[.]tk
- 2015-06-08: 194.15.126[.]7 - joans[.]ga
- 2015-11-10: 31.184.192[.]206 - ymest[.]ml
- 2015-12-04: 31.184.192[.]206 - vecexeze[.]tk
- 2016-01-19: 85.93.0[.]32 - feedero[.]tk
- 2016-01-25: 85.93.0[.]32 - www.bobibo[.]tk
- 2016-01-26: 85.93.0[.]32 - en.robertkuzma[.]com
- 2016-02-03: 85.93.0[.]32 - vyetbr[.]tk
- 2016-02-10: 85.93.0[.]32 - dofned[.]tk
- 2016-02-15: 85.93.0[.]32 - zeboms[.]tk
- 2016-02-18: 85.93.0[.]32 - 14s.syte4[.]com
- 2016-03-04: 85.93.0[.]33 - vovevy[.]tk
- 2016-03-07: 85.93.0[.]33 - nixsys[.]tk
- 2016-03-09: 85.93.0[.]33 - mvcvideo[.]tk
- 2016-03-14: 85.93.0[.]33 - bab.aba98[.]com
- 2016-03-29: 85.93.0[.]34 - folesd[.]tk
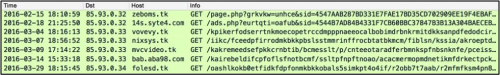
When we first noticed the EITest gate in September 2014, the URL format was: [domain]/player.php?pid=[long hexadecimal string]. Sometime in 2015, player.php switched to [random word].php and ?pid changed to ?sid. By mid-February 2016, the EITest gate URL experienced more drastic changes. See figure 3 for details.
Figure 3: Changes in EITest gate URLs since 2016-02-15.
Flash File for Redirection
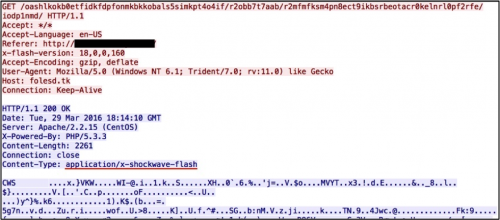
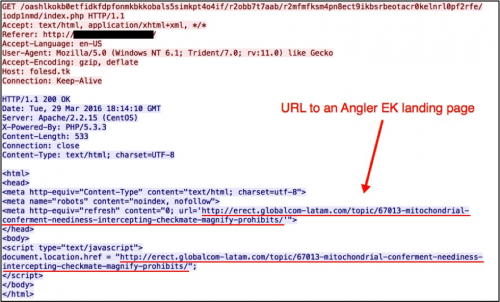
The EITest gate URL continues to return a Flash file that redirects traffic to Angler EK. This gate URL always generates two HTTP GET requests. The first request retrieves the Flash file and the second request returns script pointing to an Angler EK landing page.
Figure 4: First HTTP GET request to EITest gate returns a Flash file.
Figure 5: Second HTTP GET request to EITest gate returns script pointing to Angler EK.
Differences in Angler EK Used by This Campaign
Angler EK used by this campaign is somewhat different than Angler EK for other actors. Campaigns like pseudo-Darkleech tend to distribute ransomware like CryptoWall or TeslaCrypt. However, the group behind EITest pushes a variety of malware. Below are examples of the Angler EK caused by the EITest campaign and the associated malware.
- 2014-09-22: Vawtrak
- 2014-10-02: Pushdo.s
- 2015-06-08: Vawtrak
- 2015-11-10: Tinba
- 2015-12-04: TeslaCrypt
- 2016-01-19: Bedep and Kovter.B
- 2016-01-25: Fareit/Pony and Pusdo.s
- 2016-01-26: Bedep and TeslaCrypt
- 2016-02-03: HydraCrypt
- 2016-02-10: Ursnif variant
- 2016-02-15: TeslaCrypt
- 2016-02-18: TeslaCrypt
- 2016-03-03: TeslaCrypt
- 2016-03-04: dropper, possible Andromeda
- 2016-03-07: dropper, undetermined
- 2016-03-09: TeslaCrypt
- 2016-03-14: Zeus variant
- 2016-03-29: Bedep and possible Neutrino/Andromeda malware
Conclusion
The EITest campaign has been active since at least September 2014. Patterns of injected scripts sent by the websites compromised in this campaign have remained fairly static. However, the gate URL has evolved considerably since the campaign first started. The EITest gate leads to Angler EK and delivers a variety of malware. This campaign is not limited to ransomware like other campaigns that use Angler EK.
Palo Alto Networks customers are protected from the EITest campaign through our next-generation security platform. Associated domains have been flagged as malicious in Threat Prevention, and WildFire classifies the Flash files used in this campaign as malicious.












 Get updates from Unit 42
Get updates from Unit 42