Introduction
Our annual survey of incident data from more than 250 organizations and more than 600 incidents provides a Unit 42 perspective on the current state of security exposures.
Threat actors are increasing their speed, scale and sophistication – and that requires rapid, comprehensive and proactive defense.
The 2024 Unit 42 Incident Response Report presents the data we collected while helping hundreds of organizations defend against threat actors and active attacks. That data provides insight into how organizations can effectively defend their attack surface.
Threat actor tactics evolved noticeably in 2023. Large-scale exploitation of internet-facing vulnerabilities was the initial access vector in 39% of our cases, compared to 28% of cases in 2022. Threat actors continue to steal and use compromised credentials. While we saw phishing less often used to drop malware, it’s still used in many intrusion techniques, including exploiting IT support and password reset processes as well as session token theft.
The past year also featured more “grab-and-go” behavior. A majority of incidents involved threat actors exfiltrating as much data as they could find rather than seeking specific information. This represents an increase and a continued trend toward prioritizing speed and scale above more targeted theft.
Instead of carefully selecting data, attackers are now rapidly collecting as much as possible, exfiltrating it and sorting it out later. Sometimes, data theft is automated, along with vulnerability exploitation. This approach also aligns with attackers’ tendency to exfiltrate data earlier in the attack process than in previous years.
Key Findings From the 2024 Unit 42 Incident Response Report
More-Sophisticated Threat Actors Are Gaining Initial Access Differently
There’s a clear strategy shift among advanced threat actors. It’s illustrated by the changing ways they achieve initial access.
- Over the past year, there has been a discernible rise in the exploitation of software and API vulnerabilities, which have become increasingly favored by attackers. Exploiting these vulnerabilities accounted for 38.60% of the initial access points in 2023, up from 28.20% the year before. This significant increase indicates where attackers are focusing their efforts.
- At the same time, previously compromised credentials are also growing as an initial access vector. Compromised credential use has grown from 12.90% to 20.50% during the same time frame. And if we look back two years, it’s more than five times as prevalent as in 2021. Marketplaces for stolen credentials remain vibrant, despite coordinated takedown efforts between law enforcement and private industry.
- Phishing is decreasing… sort of. From a one-third share of initial access incidents in 2022, phishing has dropped to just 17% in 2023. This reduction signals a possible de-prioritization of phishing as cybercriminals adapt to more technologically advanced – and perhaps more efficient – infiltration methods.
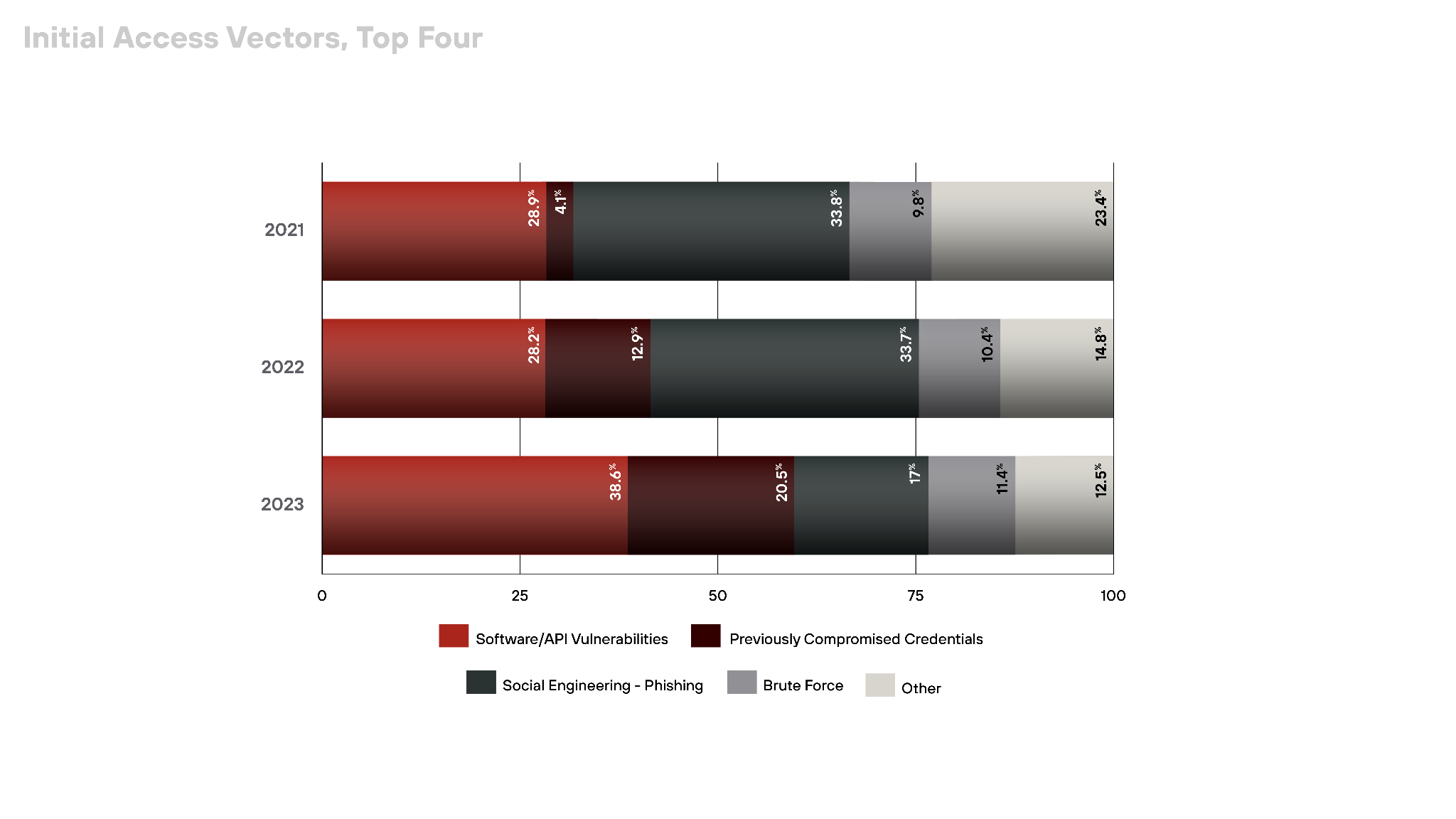
Our observations lead us to believe these are strategic changes, particularly for more advanced threat actors. They are moving away from traditional and interactive phishing campaigns to less noticeable and possibly automated methods of exploiting system weaknesses and pre-existing credential leaks.
This trend suggests that defenders should now prioritize detecting and remediating software vulnerabilities and securing credential management processes to mitigate these rising threats.
Threat Actors Grab Data Indiscriminately
Threat actors are stealing data less discriminately. An overwhelming majority of incidents involved indiscriminate data theft, where specific data targeting seemed less attractive to the attackers.
In 93% of incidents, threat actors took data indiscriminately rather than searching for specific data. This is up from 2022, when 81% of cases involved non-targeted data theft. In 2021, it was even lower: 67%
This surge points to a growing trend among cybercriminals who appear to be casting a wider net, gathering any data they can access rather than expending effort to locate and extract particular datasets.
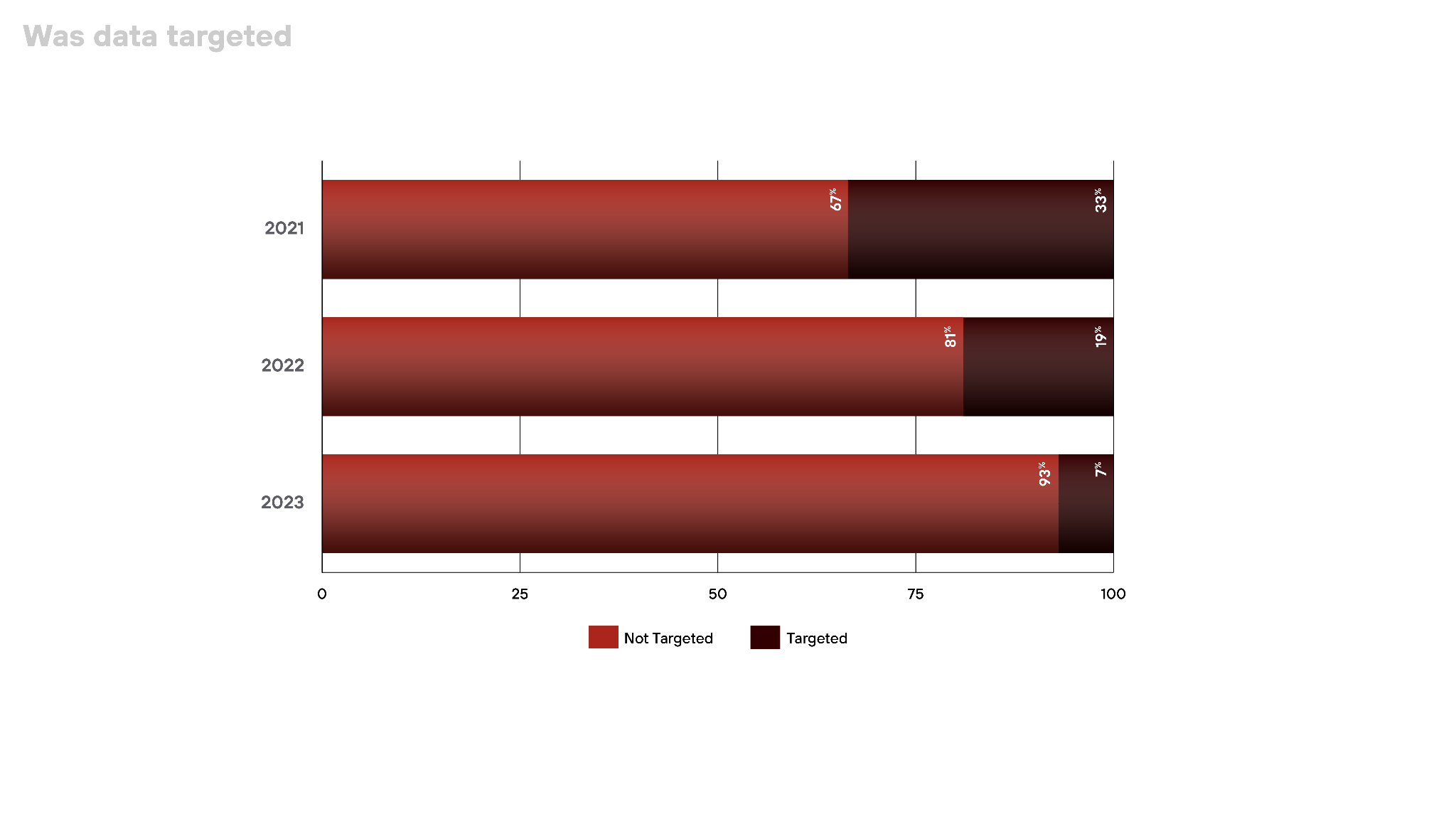
This shift could be due to a variety of factors. Attackers know the sheer volume of an organization’s data could reveal lucrative targets when taken in bulk. They are also likely to use automated tools that harvest data indiscriminately.
This has multiple implications for cybersecurity efforts:
- It suggests that traditional defenses focused on protecting highly sensitive data must be complemented by strategies that assume all data could be at risk.
- A “grab everything” attacker mentality underscores the importance of early and robust detection capabilities that can recognize large-scale exfiltration attempts, often the first clear sign of a breach.
- This shift in cyberthreat behavior necessitates a quicker response to detections and alerts and a continuous reassessment of security measures, as the sheer amount of data compromised complicates impact analysis and the notification process.
Considering these shifting threat dynamics, reviewing and strengthening existing security strategies is essential for defenders to effectively counter the advanced tactics of contemporary attackers.
Recommendations for Defenders
In light of the data from our 2024 Unit 42 Incident Response Report, a few recommendations we regularly make rise to the top.
Get Visibility Across Your External and Internal Attack Surface
Organizations should enhance visibility into their external and internal environments to keep pace with the expanding attack surface. That visibility should include understanding the cloud landscape, where frequent changes introduce new risks, and especially securing remote desktop protocol (RDP), which can amplify the threat of ransomware if exposed. Creating this visibility requires a robust combination of asset discovery, vulnerability scanning and adopting comprehensive multifactor authentication (MFA).
Emphasize continuous assessment and improvement of defenses, particularly in cloud services, where the dynamic nature of the technology can lead to frequent exposure to threats.
Close Critical Protection Gaps with Principles of Zero Trust
The Zero Trust model, advocating for a “never trust, always verify” approach, is the approach we most often recommend to our clients.
Organizations should strengthen user authentication with comprehensive MFA and explore passwordless technologies to reduce the effectiveness of credential stealing. Ensuring that users have access only to the resources necessary for their roles limits the potential for unauthorized access and lateral movement within the network.
This strategic approach requires continuous validation of security protocols and user privileges, paired with rigorous education on authentication best practices and session management.
How Palo Alto Networks and Unit 42 Can Help
Get the 2024 Unit 42 Incident Response Report for more incident response insights, trends, predictions and recommendations for best practices.
Palo Alto Networks customers can take advantage of Cortex Xpanse; an active attack surface management solution that can help discover, learn about, and respond to risks in exposed systems and services. Customers also receive protection against the specific vulnerabilities discussed in this post through Cortex XDR, Cortex XSIAM, Cloud-Delivered Security Services (CDSS) and other products. Additionally, Prisma Access is a cloud-delivered networking and security service with features like malware blocking and more.
If you think you may have been impacted by a cyber incident or have specific concerns about any of the vulnerabilities discussed here, please contact Unit 42 to connect with a team member. The Unit 42 Incident Response team is available 24/7/365. If you have cyber insurance, you can request Unit 42 by name. You can also take preventative steps by requesting any of our cyber risk management services.
Our world-renowned incident response team and security consulting experts will guide you with an intelligence-driven approach before, during, and after an incident. By partnering with us, you'll gain strategic guidance for bolstering your defenses and safeguarding your organization.
Additional Resources
- Ransomware Retrospective 2024: Unit 42 Leak Site Analysis — Palo Alto Networks
- 2023 Attack Surface Threat Report — Palo Alto Networks
- 2023 Unit 42 Ransomware and Extortion Report — Palo Alto Networks
- 2022 Incident Response Report — Palo Alto Networks
Updated Feb. 22, 2024, at 4:00 p.m. PT to add Threat Vector podcast.
Updated Sept. 24, 2024, at 6:35 a.m. PT to add Prisma Cloud protection information.












 Get updates from Unit 42
Get updates from Unit 42