In March of this year, Unit 42 investigated the SamSa actors that were attacking the healthcare industry with targeted ransomware. With this group being active for roughly one year, we decided to revisit this threat to determine what, if any, changes had been made to their toolset. In doing so, we discovered that it’s been a very profitable year for SamSa, with an estimated $450,000 in ransom payments from samples we have identified. This blog serves to discuss changes made by this group and the SamSa malware family since we last discussed them.
Updates to Malware Toolset
In the past 12 months, Unit 42 has collected and analyzed 60 unique samples that have been identified as belonging to the SamSa malware family. SamSa has a very small number of samples overall when compared to more common ransomware families such as Locky, Cerber, and CryptoMix. This is simply a byproduct of the targeted nature of SamSa, which targets specific organizations instead of a wide number of Internet users.
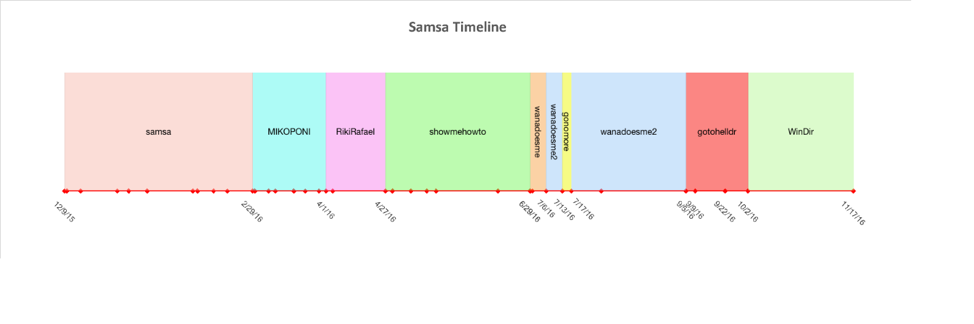
During the past 12 months, a number of changes were made by the authors to make analysis and reverse-engineering more difficult. While we classify all of these samples as “SamSa,” the attackers have used various names to identify their projects. The following chart shows the various internal .NET project names used by SamSa from December 2015 until November of 2016.
Figure 1 Versions of SamSa Ransomware over time
The following list of internal .NET project names were witnessed, in order:
- samsam
- MIKOPONI
- RikiRafael
- showmehowto
- wanadoesme
- wanadoesme2
- gonomore
- gotohelldr
- WinDir
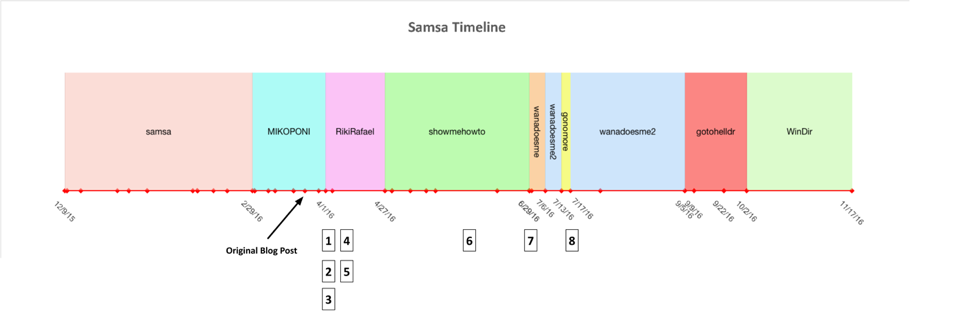
The majority of the name changes took place after April of this year. When discussing changes made internally to the code base, we witnessed the following events since we last discussed SamSa:
Figure 2 SamSa modifications over time
- A number of internal .NET name changes, starting with RikiRafael.
- A number of changes to the encrypted filename extensions used after encryption took place.
- Changes to the format of the encrypted file header.
- Modifications to the dropped helper HTML file that informs the victim of what has occurred.
- Different temporary folder names used to hold SamSa while it is running.
- Encryption of embedded strings using the AES-128 algorithm.
- Internal PDB debug strings obfuscated.
- Internal PDB debug strings removed altogether.
Profits
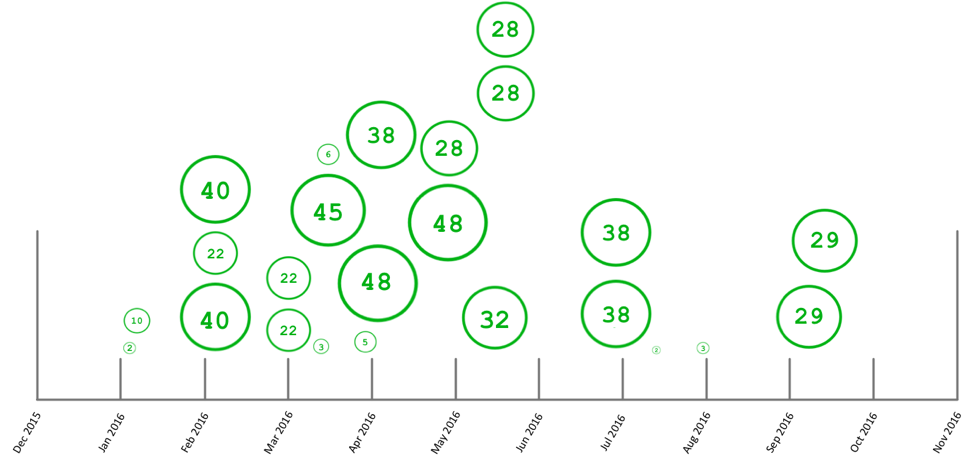
When we originally discussed SamSa, there were confirmed profits of $70,000 for the threat actors, with estimates by other researchers as high as $115,000. Unlike most ransomware, SamSa ransomware executables often contain the Bitcoin Wallet address victims are supposed to use to pay the ransom. Since March 24th 2016, we’ve witnessed 24 unique SamSa samples containing 19 unique Bitcoin (BTC) addresses. This allows us to monitor the blockchain for transfers to those wallets and identify ransom payments. In one unusual case, we saw a version of SamSa where the BTC address was input as a second argument, preventing us from seeing what payment, if any, was received by the actors. This not only makes tracking monetary payments extremely difficult, but also is yet another example of how the SamSa actors take a very targeted approach to their victims, generating unique data for each victim they infect.
Of those 19 unique BTC addresses we observed since March 24th, 14 of these have received payments totaling roughly 394 BTC. Prior to March 24, 2016, we observed roughly 213 BTC received, giving us a total of 607 BTC received by the SamSa actors. Using today’s current BTC rate of $744.43, this allows us to estimate that the attackers have obtained roughly $450,000 since their operations began. It’s important to also note that there are likely a number of samples that exist, which we were unable to obtain, causing the actual figure to likely be much higher. A visual of the money obtained by the SamSa actors can be seen in the following figure:
Figure 3 SamSa BTC profits over time
As we can see, there is a large gap in between June and September of 2016. This is most likely due to the sample set used during research, as there were only a few samples obtained in recent months.
Conclusion
In the past year, the SamSa actors have showed no sign in stopping their attacks. They’ve successfully compromised a number of organizations, and continue to reap significant rewards for their efforts. In the past year alone, they’ve collected an estimated $450,000 from their scam. As the group continues to make money, it is unlikely we shall see them stop in the near future. Palo Alto Networks customers are protected from this threat via the following ways:
- All malware is classified as malicious in WildFire.
- Domains used by SamSa have been flagged as malicious in Threat Prevention.
- AutoFocus users can track this family using the SamSa tag.
A full list of indicators of compromise (IOCs) related to SamSa can be found here.












 Get updates from Unit 42
Get updates from Unit 42