Unit 42 researchers have been following the Shamoon 2 attacks closely since November 2016. To date, Shamoon 2 has unfolded in three separate attack waves on November 11, 2016, November 29, 2016, and January 23, 2017.
Based on our newest research, we can answer a question that many have had about these attacks: how is Shamoon 2 able to enter an organization’s network and spread so widely? The answer is simple: credential theft.
Credential theft has been known to be a key part of the Shamoon 2 attacks. What our research is showing that’s new is how the attackers use the credentials once they’ve breached the network. And from this we can see how credential theft is the keystone of Shamoon 2 attacks; if an organization can prevent credential theft, the Shamoon 2 attacks can’t succeed.
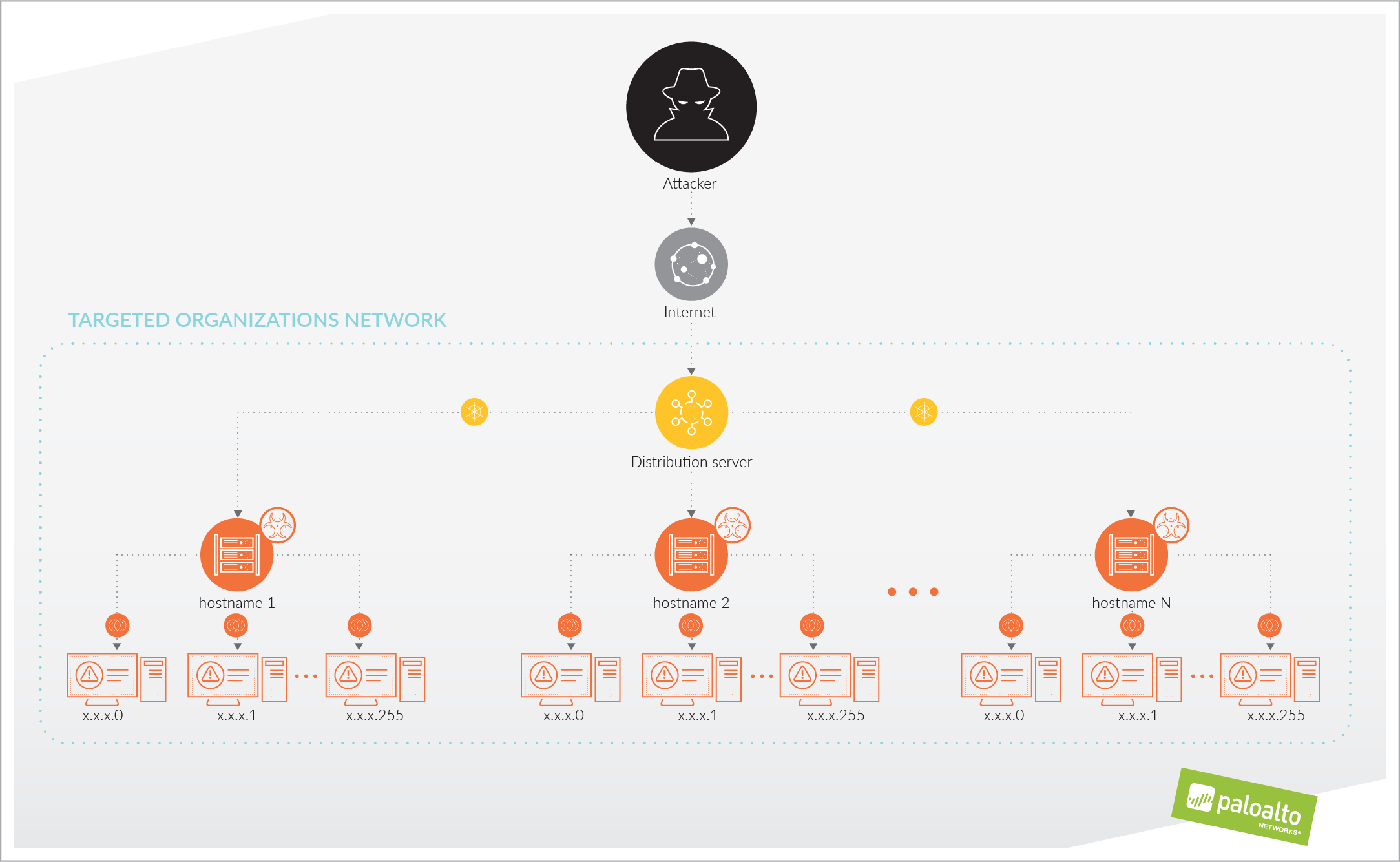
In our research, we’re able to outline that Shamoon 2 enters and spreads through an organization in three stages:
- Shamoon 2 attackers access and compromise a single system in the network, using Remote Desktop Protocol (RDP) with stolen, legitimate credentials. This becomes their distribution server: they download their tools and malware to this system.
- Attackers execute commands on the distribution server to connect to specific, named systems on the network, using the stolen, legitimate credentials, and infect them with the Disttrack malware.
- The Disttrack malware will execute on those named systems the attacker has successfully infected. The Disttrack malware will attempt to connect to and spread itself to up to 256 IP addresses on its local network. Any systems successfully infected in this stage will also attempt to infect up to 256 IP addresses on their local networks.
These stages are outlined in the image below.
And that credential theft is a key element in each stage:
- Attackers must have valid credentials to gain access via RDP to the system they will use as their distribution server in Stage 1.
- Once on the distribution server, the attackers must be able to execute their tools and scripts in an account that has valid credentials for them to successfully connect to and control the named hosts in Stage 2.
- The Disttrack malware itself must have valid, stolen credentials embedded within it to spread itself in Stage 3.
It’s also worth noting that credentials are a keystone issue in Shamoon 2 wave 2 too: we saw evidence of targeting an organization’s virtual desktop infrastructure (VDI) solutions with default credentials. While not stolen credentials, the effect is the same: attackers can use those credentials to abuse otherwise legitimate access and privileges to carry out their attacks.
At this time, we do not have research that explains definitively how the Shamoon 2 attackers have obtained these credentials. We do believe there is evidence suggestive of a connection between Shamoon 2 and the Magic Hound campaign, which could indicate these two attack campaigns could have worked in conjunction with each other to execute the Shamoon 2 attacks.
We also believe the presence of specific, valid named hosts from the network used in Stage 2 shows they were obtained directly from Active Directory on a domain controller. This is also suggestive of access to the network through legitimate, stolen credentials. In one sample we examined, we found a total of 844 hostnames.
This also helps to set context for how widely Disttrack can attempt to spread: 844 systems, each attempting to spread to 256, means that from one distribution server, Shamoon 2 attackers could potentially try to spread Disttrack to 216,064 systems; and that’s not counting if any of those infected systems, in turn, attempts to spread to an additional 256 systems.
Shamoon 2 attacks are very targeted to a specific region. But it would be a mistake to write-off the threat that Shamoon 2 demonstrates. Shamoon 2 attackers are using a rudimentary, but effective, distribution system of their own making. The power of their attack doesn’t lie in the tools they use but in their ability to obtain and abuse legitimate credentials.
This underscores why credential theft is something that organizations should prioritize as a top threat and take steps to understand it and prevent it. We’ve recently published a new Unit 42 white paper on credential theft that we encourage you to read.
To help customers take steps to better understand and protect against this threat, we’ve posted information in our article PAN-OS Configuration Recommendations to Protect Against Shamoon 2 located in our Threat and Vulnerability Articles section on our Live Community. You can also join in the discussion in our “About Threat and Vulnerability Discussions” on the Live Community.
Ignite ’17 Security Conference: Vancouver, BC June 12–15, 2017
Ignite ’17 Security Conference is a live, four-day conference designed for today’s security professionals. Hear from innovators and experts, gain real-world skills through hands-on sessions and interactive workshops, and find out how breach prevention is changing the security industry. Visit the Ignite website for more information on tracks, workshops and marquee sessions.












 Get updates from Unit 42
Get updates from Unit 42