Today, Palo Alto Networks Unit 42 researchers are announcing details on a new high- severity vulnerability affecting the Google Android platform. Patches for this vulnerability are available as part of the September 2017 Android Security Bulletin. This new vulnerability does NOT affect Android 8.0 Oreo, the latest version; but it does affect all prior versions of Android. There is some malware that exploits some vectors outlined in this article, but Palo Alto Networks Unit 42 is not aware of any active attacks against this particular vulnerability at this time. Since Android 8.0 is a relatively recent release, this means that nearly all Android users should take action today and apply updates that are available to address this vulnerability.
What our researchers have found is a vulnerability that can be used to more easily enable an “overlay attack,” a type of attack that is already known on the Android platform. This type of attack is most likely to be used to get malicious software on the user’s Android device. This type of attack can also be used to give malicious software total control over the device. In a worst-case attack scenario, this vulnerability could be used to render the phone unusable (i.e., a “brick”) or to install any kind of malware including (but not limited to) ransomware or information stealers. In simplest terms, this vulnerability could be used to take control of devices, lock devices and steal information after it is attacked.
An “overlay attack” is an attack where an attacker’s app draws a window over (or “overlays”) other windows and apps running on the device. When done successfully, this can enable an attacker to convince the user he or she is clicking one window when, in fact, he or she is actually clicking another window. In Figure 1, you can see an example where an attacker is making it appear that the user is clicking to install a patch when in fact the user is clicking to grant the Porn Droid malware full administrator permissions on the device.
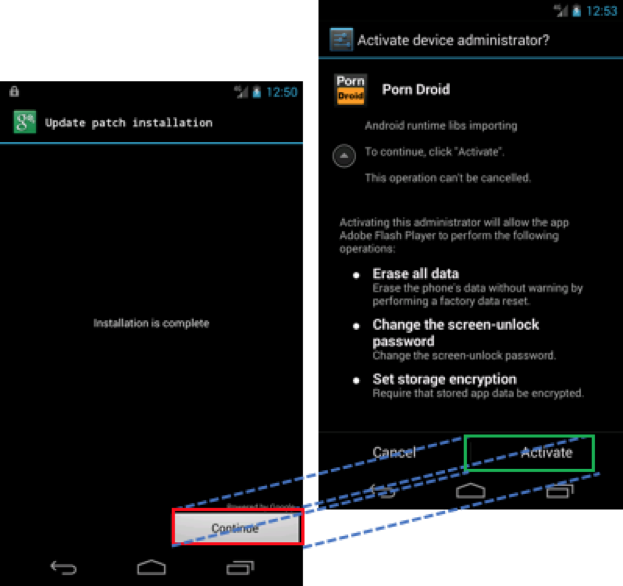
Figure 1: Bogus patch installer overlying malware requesting administrative permissions
You can see how this attack can be used convince users to unwittingly install malware on the device. This can also be used to grant the malware full administrative privileges on the device.
An overlay attack can also be used to create a denial-of-service condition on the device by raising windows on the device that don’t go away. This is precisely the type of approach attackers use with ransomware attacks on mobile devices.
Of course, an overlay attack can be used to accomplish all three of these in a single attack:
- Trick a user into installing malware on their device.
- Trick a user into giving the malware full administrative privileges on the device
- Use the overlay attack to lock up the device and hold it hostage for ransom
Overlay attacks aren’t new; they’ve been discussed before. But until now, based on the latest research in the IEEE Security & Privacy paper, everyone has believed that malicious apps attempting to carry out overlay attacks must overcome two significant hurdles to be successful:
- They must explicitly request the “draw on top” permission from the user when installed.
- They must be installed from Google Play.
These are significant mitigating factors and so overlay attacks haven’t been reckoned a serious threat.
However, our new Unit 42 research shows that there is a way to carry out overlay attacks where these mitigating factors don’t apply. If a malicious app were to utilize this new vulnerability, our researchers have found it could carry out an overlay attack simply by being installed on the device. In particular, this means that malicious apps from websites and app stores other than Google Play can carry out overlay attacks. It’s important to note that apps from websites and app stores other than Google Play form a significant source of Android malware worldwide.
The particular vulnerability in question affects an Android feature known as “Toast.” “Toast” is a type of notification window that “pops” (like toast) on the screen. “Toast” is typically used to display messages and notifications over other apps.
Unlike other window types in Android, Toast doesn’t require the same permissions, and so the mitigating factors that applied to previous overlay attacks don’t apply here. Additionally, our researchers have outlined how it’s possible to create a Toast window that overlays the entire screen, so it’s possible to use Toast to create the functional equivalent of regular app windows.
In light of this latest research, the risk of overlay attacks takes on a greater significance. Fortunately, the latest version of Android is immune from these attacks “out of the box.” However, most people who run Android run versions that are vulnerable. This means that it’s critical for all Android users on versions before 8.0 to get updates for their devices. You can get information on patch and update availability from your mobile carrier or handset maker.
Of course, one of the best protections against malicious apps is to get your Android apps only from Google Play, as the Android Security Team aggressively screens against malicious apps and keeps them out of the store in the first place.












 Get updates from Unit 42
Get updates from Unit 42