Last November, Microsoft manually patched a remotely exploitable vulnerability (CVE-2017-11882) in Equation Editor, which is a program that lets you write a mathematical equation into a document. Our Unit 42 research team provided a detailed analysis on this vulnerability here.
Since then, Microsoft has received additional reports from multiple security vendors that turned out to be related to another vulnerability that was successfully exploited after applying Microsoft’s update – Microsoft assigned it as CVE-2018-0802 and released a fix for it in the January 2018 monthly security updates.
The vulnerability is a stack overflow bug when parsing the long font name string in a FONT record, just like CVE-2017-11882. It can be used by attackers to execute code in the security context of the logged-on user.
In this blog, we look at an RTF document which we found in the wild that exploits the new FONT record vulnerability. We first saw this sample on January 3, 2018. This means that attackers were actively exploiting the CVE-2018-0802 in a zero-day attack scenario prior to Microsoft’s patch which was only available on January 9.
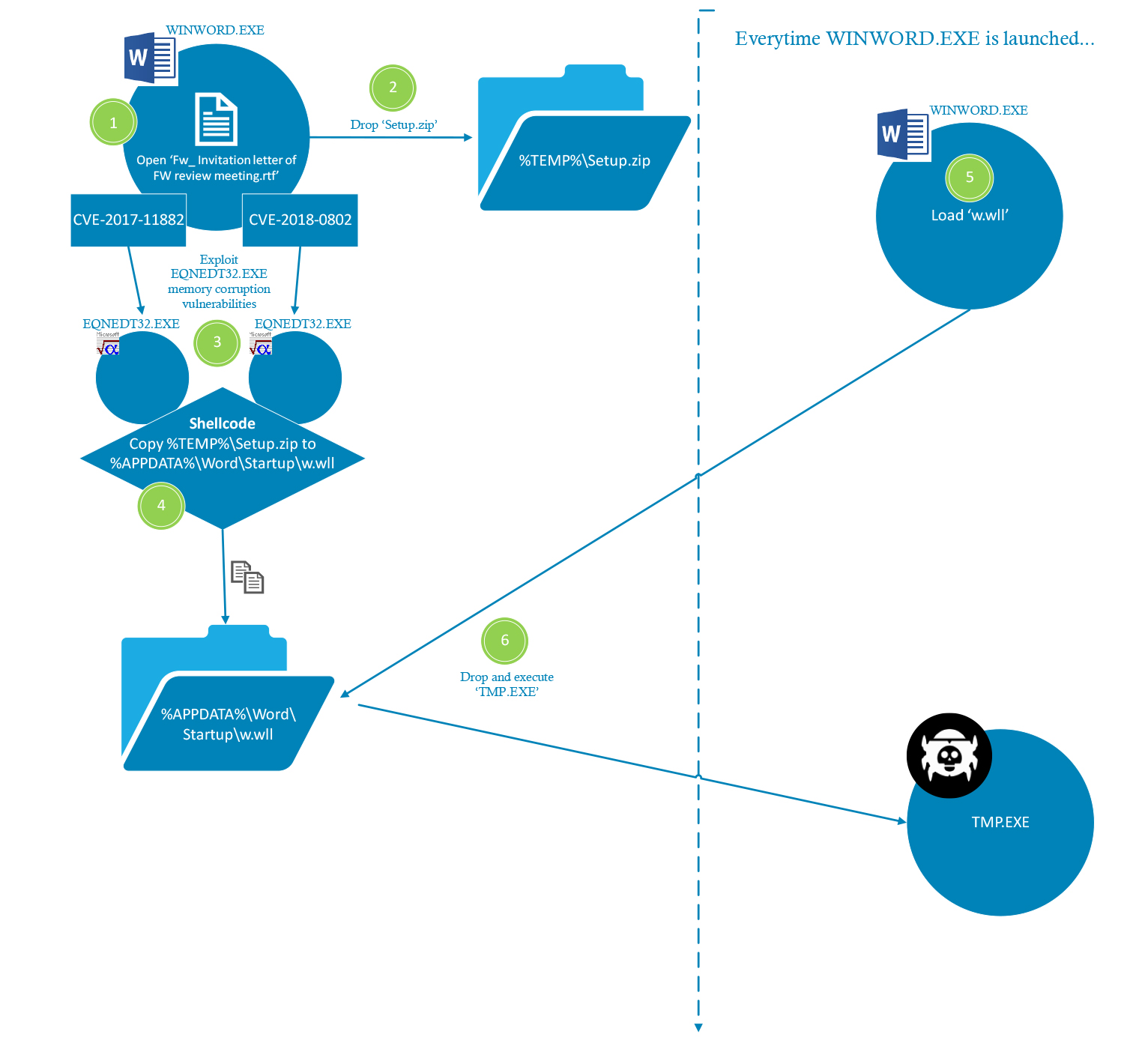
Figure 1 - The attack flow as observed in the malicious sample
In Figure 1 we show the attack flow as observed in the malicious sample. First, the malicious RTF document is opened by the victim. Then, the document uses an embedded ‘package’ to drop a DLL named ‘Setup.zip’ to the disk, under the ‘%TEMP%’ directory. This technique was described in McAfee’s whitepaper.
Secondly, the RTF file contains two embedded equations (parsed by ‘EQNEDT32.exe’) – one for CVE-2017-11882, and another for the Font vulnerability within CVE-2018-0802. This means that the attack will work on a victim’s machine unless they have applied patches for both CVEs.
The equations exploits contain a shellcode that copies the DLL file dropped at the first stage and renames it into ‘%appdata%\Word\Startup\w.wll’. ‘%appdata%\Word\Startup’ is a special directory containing plugin DLLs for Microsoft Word, which are loaded by ‘winword.exe’ each time it is launched. This grants the malware with a persistency capability.
When ‘w.wll’ is loaded into ‘winword.exe’, it drops the actual malware payload (embedded in the DLL) into ‘%programdata%\NetWork\tmp.exe’ and executes it.
How Traps prevents this threat
Palo Alto Networks Traps advanced endpoint protection offers multiple methods of malware and exploit prevention to protect against such complex threats. It first prevents the malicious shellcode running in ‘EQNEDT32.exe’ using Traps exploit prevention capabilities. Secondly, Traps local analysis via machine learning prevents ‘%programdata%/NetWork/tmp.exe’ from executing. Some other samples we have observed in the wild run a command line or PowerShell commands via ‘EQNEDT32.exe’ to execute the malicious intents. Traps prevents these by malware examination flow.
Learn more about how Traps prevents zero-day vulnerabilities and unknown threats.












 Get updates from Unit 42
Get updates from Unit 42