This post is also available in: 日本語 (Japanese)
Unit 42 released details about a new spear phishing campaign called FreeMilk that uses a relatively new attack technique that can be highly effective. This is the kind of technique that is likely to be aimed at high value targets. Targets of these attacks are likely to be individuals with access to valuable or sensitive information such as members on a Board of Directors, C-level executives, military and political personnel, or those with compromising information such as journalists or activists. Individuals close to those previously mentioned could also be used as part of the attack campaign such as an executive assistant to a CEO or even friends or family.
How it Works
Phishing attacks are broad, leveraging email messages crafted around common, generalized topics in order to trick recipients into opening an email message and its attachments. Attackers will cast a wide net, with no regard to who the victims are, hoping that a decent percentage of attacks are successful.
Spear phishing, like the name implies, is a more targeted form of phishing which incorporates a theme directly related to the target. Using this approach, victims are more inclined to trust the sender, and open the email message and any attachments resulting in the success of the attack.
FreeMilk is an advanced spear phishing attack campaign that, instead of using a theme to lure targets into downloading a malicious attachment, hijacks an in-progress email conversation.
Simply explained:
- Alice (A) and Bob (B), are having an ongoing email conversation.
- The attacker, Charlie (C) will carry out an attack, likely using some form of credential theft, in order to gain control to Alice’s email account.
- Using Alice’s email account, Charlie sends an email containing a malicious attachment that appears to be relevant to the ongoing email conversation between Alice and Bob.
- Bob receives the email, and thinking it’s from Alice, opens the malicious attachment and the attack is successful.
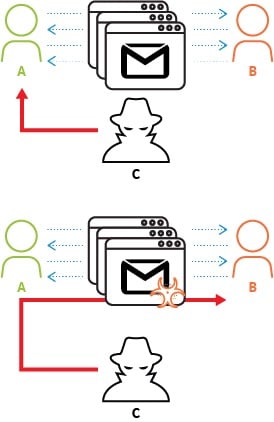
Figure 1 Conversation Hijacking to Deliver Malware
How to Defend Against It
Unit 42 observed this specific attack taking advantage of a vulnerability in Microsoft Office, which has a patch available. To protect against FreeMilk and attacks alike, ensure your systems and devices are updated with the latest operating systems and security patches.
Additionally, multiple layers of security for devices and networks create additional layers of protection to prevent against these types of attacks. For example, multi-factor authentication would prevent an attacker from abusing stolen credentials, hindering their ability to access an email account and successfully complete the FreeMilk attack campaign.











 Get updates from Unit 42
Get updates from Unit 42