Introduction
A series of high-profile ransomware attacks held the world’s attention in 2021, keeping ransomware at the top of threat lists and priorities for cybersecurity teams everywhere. To put all this activity into context and shed some light on the scope and direction of the ransomware landscape, our threat researchers and security consultants created the 2022 Unit 42 Ransomware Threat Report. This report provides the latest insights on established and emerging ransomware groups, payment trends and new techniques that ransomware groups are using to increase their profits, including ransomware-as-a-service and double and multi-extortion capabilities. It also provides some recommendations on security best practices that can help you prevent, detect, respond to and recover from ransomware so that you can minimize the impact and resume business operations.
Key Findings From the 2022 Unit 42 Ransomware Threat Report
The report pulled data from actual incident response cases, as well as dark web forums and the leak sites of ransomware gangs. The following are just a few of the key takeaways from the analysis:
Ransoms Keep Going Up
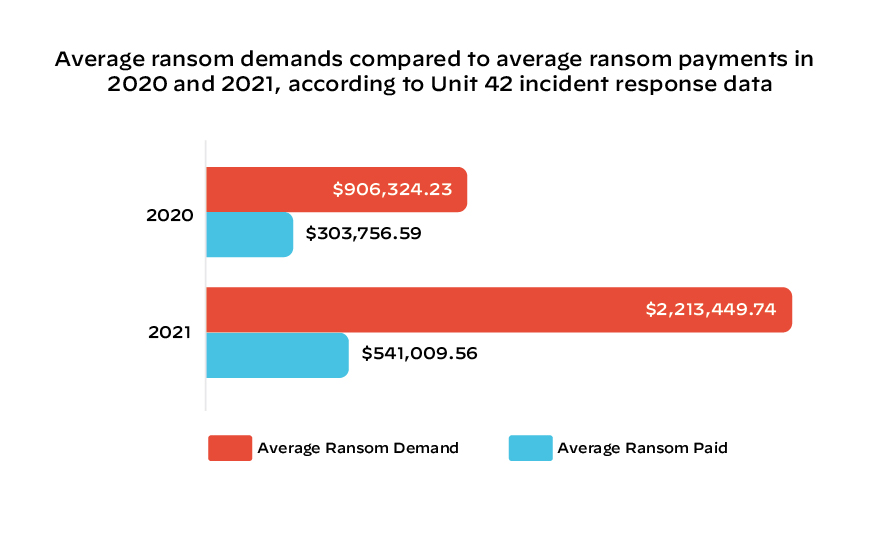
Ransoms – both demands and payments – continue to go up. Among the incident response cases reviewed in 2021, which were predominantly in the U.S., the average ransom demanded was approximately $2.2 million. This represents about a 144% increase from the average demand of $900,000 from the cases analyzed in 2020. The average payment from 2021 cases climbed to $541,010, which was 78% higher than the previous year. While the raw numbers have gone up, it is important to note the payouts tend to be significantly less than initial ransom demands – we calculated actual payments were, on average, 42.42% of the initial ransom amount.
Victim Naming and Shaming Is Fast Becoming Normal
Multi-extortion techniques where attackers not only encrypt the files of an organization, but also name and shame their victims and/or threaten to launch additional attacks (e.g., distributed denial of service DDoS) are increasingly part and parcel of ransomware tactics. In 2021, the names and proof of compromise for 2,566 victims were publicly posted on ransomware leak sites, marking an 85% increase compared to 2020. Ransomware gangs use these tactics to pressure victims to pay more, faster, or both – though the efficacy of the approach depends in part on how sensitive the data they’ve stolen truly is. In 2021, 35 new ransomware groups emerged using double-extortion techniques, which means they demanded a ransom and then informed victims they would publicly expose the data they had stolen if the ransom was not paid.

Ransomware-as-a-Service Continues to Lower the Barrier to Entry
“Entrepreneurial” threat actors are capitalizing on the growing number of cybercriminals who want a piece of the ransomware pie. These criminal entrepreneurs offer ransomware as a service (RaaS) to other criminals, establishing agreements that set the terms for providing actual ransomware to these affiliates, in exchange for a monthly fee or a percentage of ransoms paid. We have seen at least 56 active RaaS groups, some of whom have been operating since 2020, all of whom are lowering the barrier to entry and expanding the reach and negative impact of ransomware.
Recommendations to Improve Ransomware Preparedness
The ideal time to start preparing for a ransomware attack is before it happens. Below are recommendations on best practices organizations can use to reduce the likelihood of a ransomware attack or minimize impact if a successful attack does occur.
Prepare Your Cloud Environments
Given the amount of valuable data in the cloud, it is only a matter of time before we see ransomware groups target cloud environments. However, to launch ransomware attacks in cloud environments, threat actors will likely use new tactics, techniques and procedures (TTPs). This means organizations have a chance to prepare and bolster their defenses – the time is now for organizations to implement identity and access management (IAM) best practices to secure their cloud APIs, as well as harden their cloud workloads from the image down to improve their resilience to ransomware.
Implement a Comprehensive Strategy
While maintaining good general cyber hygiene and implementing security awareness training are foundational starting points, we suggest you also follow these ten steps to reduce the risk and impact of a ransomware attack on your organization:
- Stay educated on the evolving threat landscape to ensure you can spot the latest threats and implement the latest safeguards to protect your organization.
- Analyze the business impact of losing critical data to understand what’s really at risk, including any potential upstream and downstream consequences, to help you prioritize efforts.
- Assess internal and external readiness – including any third parties, partners or supply chain elements that could introduce risks – to help you develop a comprehensive mitigation roadmap.
- Review and test your incident response plan with tabletop exercises and purple team testing simulations to work out kinks and bolster your ability to recover when it matters.
- Implement a Zero Trust strategy to eliminate implicit trust and continuously validate every stage of every digital interaction to make it harder for attackers to operate.
- Identify your exposed assets – anything on the public internet – so you can take steps to reduce your attack surface.
- Prevent known and unknown threats by continuously identifying and blocking exploits, malware, and command-and-control traffic to take away any low hanging fruit from attackers.
- Automate when possible, implementing tools (e.g., security orchestration, automation and response, also known as SOAR) that support the automated remediation of events to speed your ability to respond to and recover from incidents.
- Secure cloud workloads by leveraging best practices and implementing security measures throughout the development lifecycle.
- Reduce response time with retainers – in other words, make incident response experts an extension of your team – to help you create a predictable incident response budget and take faster action to minimize the impact of an attack.
If you think you may be subject to an active ransomware attack or have an urgent matter, get in touch with the Unit 42 Incident Response team or call North America Toll-Free: 866.486.4842 (866.4.UNIT42), EMEA: +31.20.299.3130, APAC: +65.6983.8730, or Japan: +81.50.1790.0200.
Get the full 2022 Unit 42 Ransomware Threat Report for more ransomware insights, trends and recommendation for best practices.
Additional Resources
- 2022 Unit 42 Ransomware Threat Report Webinar
- 2022 Ransomware Trends: Higher Ransom Demands, More Extortion Tactics
- Forrester Ransomware Survival Guide
- Unit 42 Retainer Datasheet












 Get updates from Unit 42
Get updates from Unit 42