This post is also available in: 日本語 (Japanese)
Executive Summary
Today, INTERPOL and The Nigeria Police Force announced the results of Operation Falcon II, joint operations that led to the arrest of 11 Nigerian business email compromise (BEC) actors. Collaborative in its approach, this operation leveraged intelligence and resources from several industry partners combined with law enforcement entities from over six nations in order to map global victims back to a core subset of actors who have historically operated outside of foreign law enforcement jurisdictions.
BEC remains the most common and most costly threat facing our customers. This threat held the top spot for the fifth year in a row on the 2020 FBI Internet Crime Complaint Center (IC3) report. Over half a decade, global losses have ballooned from $360 million in 2016 to a staggering $1.8 billion in 2020. As we eagerly await the release of the 2021 numbers, our telemetry and experience helping clients respond to BEC attacks suggests that last year's global losses will once again set new records.
Despite these massive loss amounts, industry and global law enforcement continue to make considerable strides toward thwarting this activity.
Furthermore, this recent operation was novel in its approach in that it didn’t target the easily identifiable money mules or flashy Instagram influencers who are typically seen benefiting from these schemes. Instead, it focused predominantly on the technical backbone of BEC operations by targeting the actors who possess the skills and knowledge to build and deploy the malware and domain infrastructure used in these schemes. Of the individuals arrested, we track six out of the 11 actors as being SilverTerrier (Nigerian malware) actors who have successfully avoided prosecution for the past half decade due to the complexities of mapping global victims beyond the flow of stolen funds back to the source of malicious network activity.
This blog provides a brief overview of the six actors and provides recommendations to help organizations protect against these threats.
Palo Alto Networks customers are protected against the types of BEC threats discussed in this blog by products including Cortex XDR and the WildFire, Threat Prevention, AutoFocus and Advanced URL Filtering subscription services for the Next-Generation Firewall.

| Operation Falcon II arrests include threat actors tracked as | SilverTerrier |
| Related Unit 42 Topics | cybercrime, business email compromise |
The BEC Threat Actors
Darlington Ndukwu

Aliases: Darlington Opara, Darlington Smith, Darlly Ndu, DN Network, Engr. DN, ask4dn, padarlingtonsmith, darllymoore4u, dnhovercraft2000
Domains: This actor supports several other Nigerian BEC actors, and as such, we found over 1,300 domain registrations sharing some degree of connection to this actor. Of that number, 285 are directly linked with this actor. Most notably, in addition to malware, he operated his own hosting service and name server, both of which supported other actors. These include domains that have historically impersonated banking institutions, government entities and others. Some examples include: annexbanks[.]com, bangkokbnk[.]com, barcklaysplc[.]com, cimbmy[.]com, hsbc-london.co[.]uk, western-union[.]org, americans-airforce[.]com, armymilitary[.]us, fbigov[.]org, immigration-ng[.]com, indonesia-gov[.]com, iowahomelandsecurity[.]com, military-welfare[.]com and unitednatios[.]eu
Malware: ISRStealer, Keybase, Pony, LokiBot, PredatorPain, ISpySoftware
Oldest Activity: 2014
Interesting Notes: This actor is known to have targeted a security researcher by using their name and organization to register a fraudulent domain. More importantly, this actor is also believed to have been arrested in 2018 as part of the FBI’s operation WireWire. Thus, his recent arrest marks one of the first known instances of a Nigerian actor being arrested twice for BEC. It further suggests that his initial prosecution fell short of dissuading continued criminal activity.
Onuegwu Ifeanyi Ephraim

Aliases: Ifemonums, SSGToolz, SSGDomains, Alper Larcin
Domains: This actor also supports several other Nigerian BEC actors. There are over 144 domains registered using this actor's names, aliases and email addresses. Examples of domains used by this actor include: Some examples include: gulf-capital[.]net, owenscorming[.]com, pennssylvania[.]com[.]mx, starwooclhotels[.]com, and us-military-service[.]com. Similarly, domains registered by this actor for use by his associates include: ayamholy[.]com and kabospy[.]com.
Malware: LokiBot, PredatorPain, ISRStealer, Pony, NanoCore, AzoRult, ISpySoftware, Agent Tesla, Keybase
Oldest Activity: 2014
Interesting Notes: This actor has been active for over seven years. Over that time he has sponsored and provided services for several junior actors looking to follow his criminal pursuits. In one BEC forum alone, he is known to have sponsored 30 other actors for access. In November 2020, this actor was arrested along with three associates for his BEC activities. The arrests were part of the first Operation Falcon, which was a joint effort between INTERPOL, The Nigeria Police Force and Group IB. Following his release, this actor quickly returned to his previous schemes and was observed registering the domain covid19-fundservices[.]com in March 2021. With the identification of additional evidence, this actor was arrested once again in December 2021 as part of Operation Falcon II.
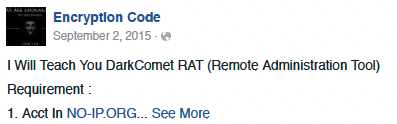
Oyebade Fisayo

Aliases: EncryptionCode, Fyzee, Fyzeeconnect
Domains: This actor supports several other Nigerian BEC actors with roughly 250 domains directly linked to his aliases or email accounts. The majority of these domains have impersonated logistics companies. Some examples include: atlanticexpresslogistics[.]com, clarionsshipping[.]com, dpdexpressuk[.]com, dynamicparceldelivery[.]com and shipatlanticlogistics.co[.]uk.
Malware: ISRStealer, Pony, LuminosityLink, NanoCore, LokiBot, Keybase, Adwind, Agent Tesla, PredatorPain, ImminentMonitor
Oldest Activity: 2015
Interesting Notes: In addition to supporting BEC schemes directly, this actor has historically offered free advice to his Facebook friends on how to use remote access trojans.
Kevin Anyanwu

Aliases: Markens Clothing
Domains: In 2015 this actor registered the domain hsbctelex[.]net. HSBC is one of the largest financial institutions in the world. Telex, on the other hand, is an abbreviation for Telegraphic Transfers, which are used to process international and domestic payments. When registering this domain, the actor used the same phone number that is advertised as being associated with a personal (not business) Facebook page called Markens Clothing.
Malware: We have not identified any malware calling back to domains owned by this actor. However, we believe that this domain was likely used for fraudulent purposes in support of BEC campaigns.
Oldest Activity: 2015
Interesting Notes: This actor is an associate of Onuegbu Ifeanyi Ephraim.
Onukwubiri Ifeanyi Kingsley

Aliases: Soja Rex, Ifeanyi Soja, Soja TMT, Richard Manson
Domains: This actor's email address is directly linked to 20 domain registrations. These include domains that impersonate financial institutions such as PNCFinancial[.]ca and PrimeFCU[.]com. Pivoting on domain registration phone numbers and street addresses reveals an additional 370 fraudulent domains that were likely used by this actor and his associates. For example, his phone number is also linked to five domains that were registered for an individual or alias of Uwe Martin (UweTMT). Two of these domains were qatarairways[.]pw and cokepromo[.]asia.
Malware: Pony, LokiBot
Oldest Activity: 2016
Interesting Notes: This actor is strongly branded as being part of “The Money Team,” abbreviated as TMT. This organization appears to have several legitimate business entities including TMT Cakes and TMT Travel and Tours Limited – the latter of which claims to be Nigeria's leading travel company with deals on visas and scholarships. However, despite the seemingly benign function of these entities, this actor’s fraudulent domain registrations, malware activities and personal associations call into question the true legitimacy of these organizations and his activities. For example, this actor is friends with Onwuka Emmanuel Chidiebere (aka CeeCeeBoss TMT) and Onuegbu Ifeanyi Ephraim (aka SSGToolz), both of whom were arrested by INTERPOL and The Nigeria Police Force in November 2019 for BEC schemes. Additionally, this actor is friends with Darlington Nduku, Markens Clothing and several other BEC actors.
Kennedy Ikechukwu Afurobi

Aliases: Chidi Ibeh, Big Boss
Domains: This actor is associated with 97 domains, including wemacreditb[.]com, orionshippingx[.]com and fdralgrantagency[.]com.
Malware: Pony, PredatorPain, Azorult
Oldest Activity: 2014
Interesting Notes: According to his social media accounts, his favorite quotes come from the Bible, Ralph W. Emerson and Niccolò Machiavelli. This actor is also friends with Onwuka Emmanuel Chidiebere (aka CeeCeeBoss TMT), who was arrested by INTERPOL and the Nigeria Police Force in November 2019 for BEC schemes.
Protections and Mitigations
The best defense against BEC campaigns is a security posture that favors prevention. We recommend that organizations implement preventative practices including:
- Review network security policies, focusing on the types of files (portable executables, documents with macros, etc.) that employees can download and open on devices attached to company networks. Additionally, as a best practice, URL filtering rules should be established to restrict access by default to the following categories of domains: Newly Registered, Insufficient Content, Dynamic DNS, Parked and Malware.
- Routinely review mail server configurations, employee mail settings and connection logs. Focus efforts on identifying employee mail-forwarding rules and identifying foreign or abnormal connections to mail servers. When possible, consider implementing geo-IP blocking. For example, small local businesses do not need to allow logon attempts from foreign countries where they have no employees.
- Conduct employee training. Routine cyberthreat awareness training is one component; however, organizations should also consider tailored training focused on their sales and finance components. Such training should require all wire transfer requests to be validated using verified and established points of contact for suppliers, vendors and partners.
- Conduct tabletop exercises and rehearsal investigations with the intent of determining sources of evidence, as well as gaps in the types of evidence needed, and establishing reporting points of contact for the appropriate authorities. Additionally, rehearsals should validate familiarity with the financial fraud kill chain and make clear that staff know which personnel are responsible for enacting it.
- Conduct compromise assessments on an annual or more frequent basis to test organizational controls and validate that there is no unauthorized activity occurring in the environment. By reviewing mailbox rules and user login patterns on a regular basis, these assessments can verify that controls are functioning as expected and that unwanted behaviors are being effectively blocked throughout the environment.
Finally, for Palo Alto Networks customers, our products and services provide several capabilities designed to thwart BEC attempts, including:
 |
Cortex XDR protects endpoints from all malware, exploits and fileless attacks associated with SilverTerrier actors. |
 |
WildFire® cloud-based threat analysis service accurately identifies samples associated with information stealers, RATs and document packaging techniques used by these actors. |
 |
Threat Prevention provides protection against the known client and server-side vulnerability exploits, malware and command and control infrastructure used by these actors. |
 |
Advanced URL Filtering identifies all phishing and malware domains associated with these actors and proactively flags new infrastructure associated with these actors before it is weaponized. |
 |
Users of AutoFocus™ contextual threat intelligence service can view malware associated with these attacks using the SilverTerrier tag. |
Conclusion
While BEC schemes remain the most profitable and widespread form of cybercrime on the internet, private/public collaborative efforts continue to make tremendous strides in combating these threats on a global scale. The most recent joint operations championed by The Nigeria Police Force and INTERPOL serve as an inspiring example. These operations drew on insights and collaboration from multiple industry partners and law enforcement entities from more than six nations in order to achieve positive outcomes. Those outcomes include disruption of BEC networks within Nigeria, improved international coordination and most importantly, the arrest of 11 actors, who for the better half of a decade have avoided prosecution while providing the technical expertise, malware and malicious domains used in countless BEC campaigns.
Palo Alto Networks was the first cybersecurity company to sign a partnership agreement with INTERPOL in 2017. This agreement served as the foundation for our collaborative efforts in combating criminal trends in cyberspace and other cyberthreats globally. Since then the partnership has continued to evolve, and today Palo Alto Networks remains a proud contributing member of INTERPOL's Gateway program.
Additional Resources
2021 - Interpol Operation Falcon II
2021 – Credential Harvesting at Scale Without Malware
2020 - Interpol Operation Falcon
2020 – SilverTerrier: New COVID-19 Themed Business Email Compromise Schemes
2019 – SilverTerrier: 2019 Nigerian Business Email Compromise Update
2018 – SilverTerrier: 2018 Nigerian Business Email Compromise Update
2017 – SilverTerrier: The Rise of Nigerian Business Email Compromise
2016 – SilverTerrier: The Next Evolution in Nigerian Cybercrime
2014 – 419 Evolution
Mitre: SilverTerrier Group
Unit 42 - Business Email Compromise - Response Services
Unit 42 - Business Email Compromise - Readiness Assessment
*Image at the top of post is an arrest photo provided by INTERPOL.











 Get updates from Unit 42
Get updates from Unit 42