This post is also available in: 日本語 (Japanese)
Executive Summary
It’s no secret that web threats, fueled by sophisticated attackers, continue to increase and do more damage. As part of our regular tracking and observation of trends in web threats, from October 2020 to September 2021, our web threat detection module found around 2,240,000 incidents of malicious landing URLs containing all kinds of web threats, 831,000 of which are unique URLs.
We analyzed these web threats in search of trends in when web threats are more active, which malware families present threats more often, and where in the world web threats appear to be coming from. In many cases, the majority appear to originate from the United States (though we recognize that attackers may use proxy servers to hide their physical locations).
We also take a closer look at the web skimmer. With the popularity of e-commerce websites, web skimmer attacks are being leveraged by more attackers due to the difficulty in detecting them and the ease of deploying them. We will provide insight into how the attack is distributed. We observe that more and more web skimmers are being hosted on the cloud, especially for some web skimmer families.
Palo Alto Networks customers are protected from the web threats discussed here and many others via the Advanced URL Filtering and Threat Prevention cloud-delivered security subscriptions.
| Types of Attacks and Vulnerabilities Covered | Skimmer attacks, formjacking, malware, cryptominers |
| Related Unit 42 Topics | Information stealing, A Closer Look at the Web Skimmer |
Web Threats Detection Analysis
By collecting data from October 2020-September 2021 with Advanced URL Filtering, we detected 2,241,354 incidents of malicious landing URLs containing all kinds of web threats, 831,550 of which are unique URLs.
As shown in Figure 1, web threats were more active from October 2020-January 2021 than at other times during the year. This suggests that attackers, especially those targeting e-commerce websites, might be more active during the holiday shopping season. After January 2021, the number of web threats leveled off, both in total and in terms of unique URLs.
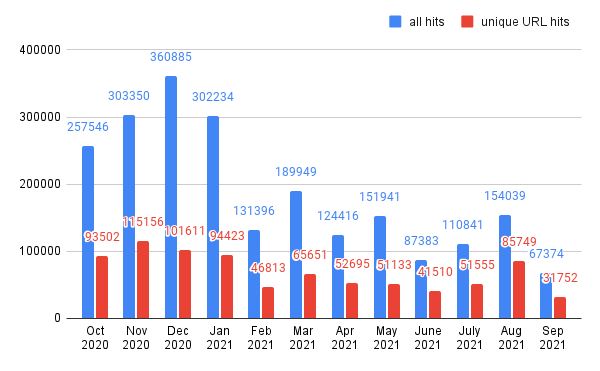
Web Threats Landing URL Analysis
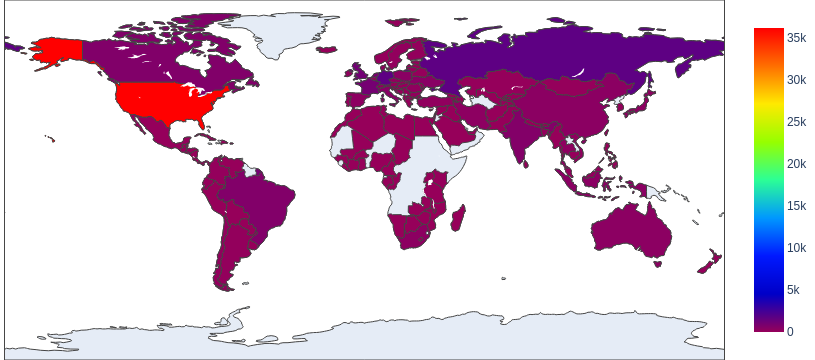
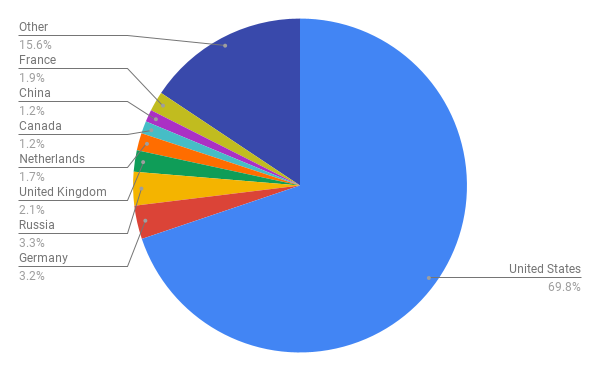
According to our analysis, the previously mentioned 831,550 unique URLs are from 51,985 unique domains. After identifying the geographical locations for these domain names, we found that the majority number of them seem to originate from the United States, followed by Russia and Germany. However, we recognize that the attackers might leverage proxy servers and VPNs located in those countries to hide their actual physical locations.
The choropleth map shown in Figure 2 indicates the wide distribution of these domain names across almost every continent, including Africa and Australia. Figure 3 shows the top eight countries where the owners of these domain names appear to be located.
Web Threats Class Analysis
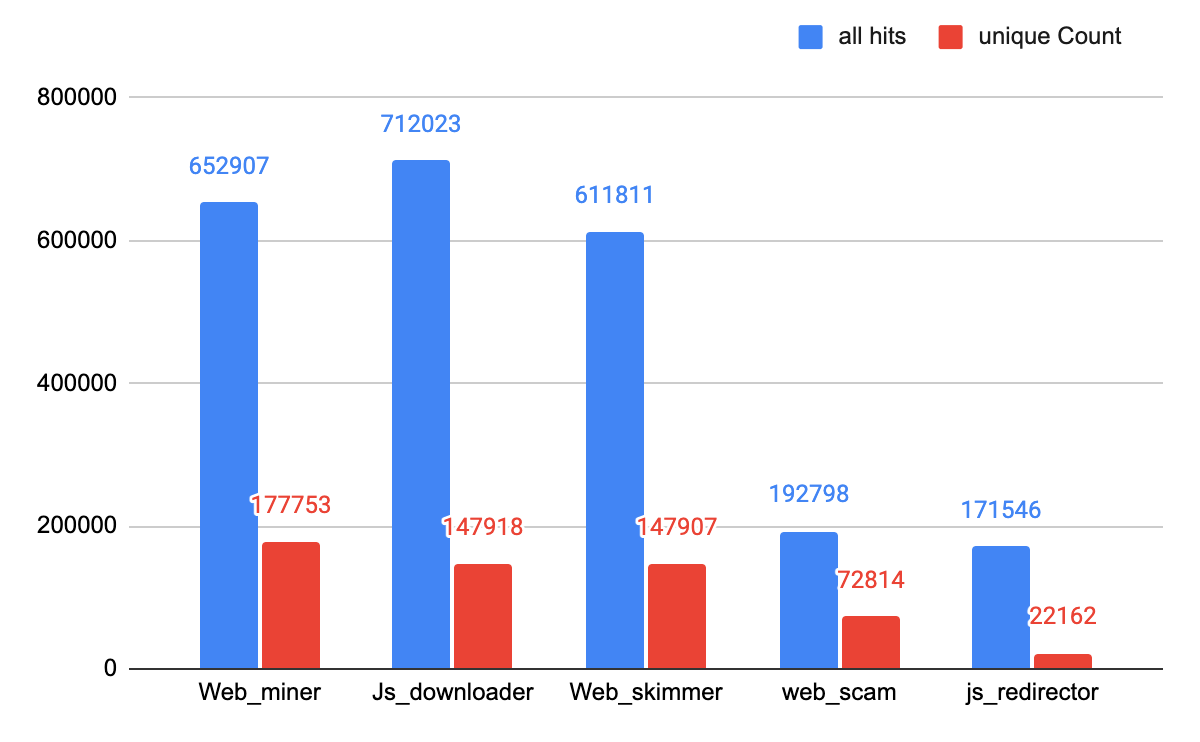
The top five web threats we observed are cryptominers, JS downloaders, web skimmers, web scams and JS redirectors. Here are definitions for each:
- Cryptominers or coinminers are cryptocurrency miners that run in web browsers and consume significant CPU resources, making computer use slow.
- JS downloaders are snippets of JavaScript code that download malicious files from websites remotely to enable further malicious behaviors.
- Web skimmers are snippets of JavaScript code embedded into web pages to steal sensitive user information such as credit card information or personally identifiable information (PII).
- Web scams are fraudulent activity over the internet, often using social engineering techniques to propagate malware infection or cause monetary loss for users.
- JS redirectors are snippets of JavaScript code that are inserted into malicious or hacked websites, and used to redirect the browser to websites unintended by the user.
As shown in Figure 4, JS downloader threats are very active. We also see that many coinminers exist all over the web, though, ironically, some are not working because the dependent coinminer libraries they once used are no longer supported. Web skimmers, which we will highlight in the sections that follow, are some of the most pervasive and severe web threats and third most common among the threats we observed.
Web Threats Malware Family Analysis
Based on our classification of web threats explained in the previous section, we further organized our set of web threats by malware family. The family is important to understanding how threats work since threats in the same family share similar JavaScript code even if the HTML landing pages where they appear have different layouts and styles.
Among the samples we collected, there are 684,276 unique malicious JavaScript snippets from the 2,241,354 HTML pages observed containing web threats from October 2020-September 2021.
When classifying these JavaScript snippets into malware families, we looked for similarities in the malicious JavaScript code. If we identified some pieces of malware showing similar code patterns, behaviors or originating from the same attacker, these pieces of malware are grouped into a malware family. Figure 5 shows the numbers of snippets observed for the top 18 malware families we identified. Looking at how the families are grouped, it’s not hard to see that the coinminers and JS downloaders we detected belong to fewer families – but the web skimmers we found show more diversity in code and behavior. Detection for web skimmers can therefore be more difficult – the JavaScript that web skimmers run can be very flexible and easy to obfuscate to escape detection. Because of this, we now take a deeper look into web skimmers and how they are evolving.
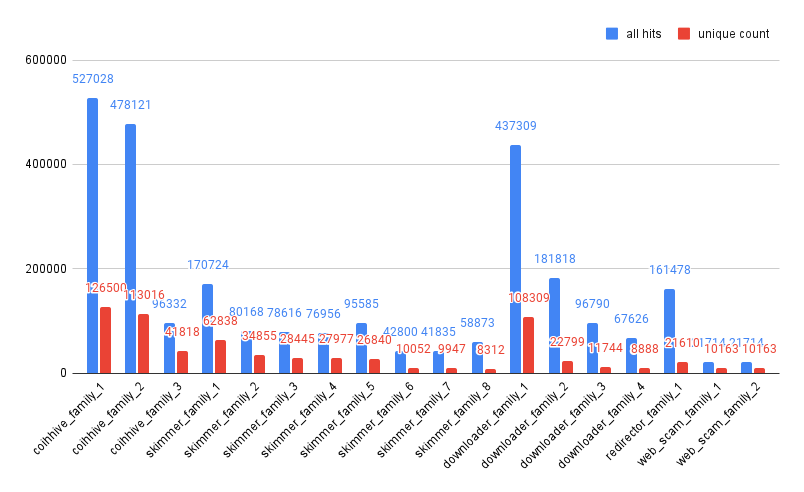
Web Skimmer Detection Analysis
As we mentioned earlier, web skimmers are easy to deploy and hard to detect. Normally, they will intercept sensitive information such as PII, bank card information and so on. Recently, we noticed that more and more web skimmers were deployed on the cloud to make them seem less suspicious. (When deployed on the cloud, their domain names often contain public cloud indicators tied to legitimate companies, which can increase their apparent legitimacy in the eyes of the user.) In the following sections, we will take a closer look at the web skimmer.
Web Skimmer Malware Host Analysis
In web skimmer threats, most URLs hosting malicious JavaScript code usually have different landing URLs – even the malware host URL and the landing URL are typically from different domains. The malware host URL is very important not only to victims – since this is where the attack takes place – but also to researchers because this is where the malicious JavaScript code is injected. In most cases, attackers can fully control the content of the malware host URL.
With Advanced URL Filtering, from October 2020-September 2021, we detected 147,907 unique URLs from 611,811 total URLs where web skimmer malware was injected into the pages. These URLs belong to 6,817 unique domains. After identifying the apparent geographical locations for these domain names, we found that the majority of them seem to also originate from the United States – as we observed for web threats generally. Figure 6 shows the heat map.
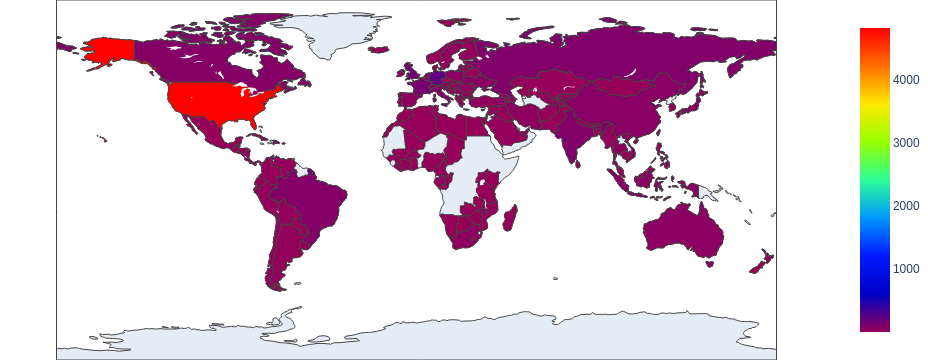
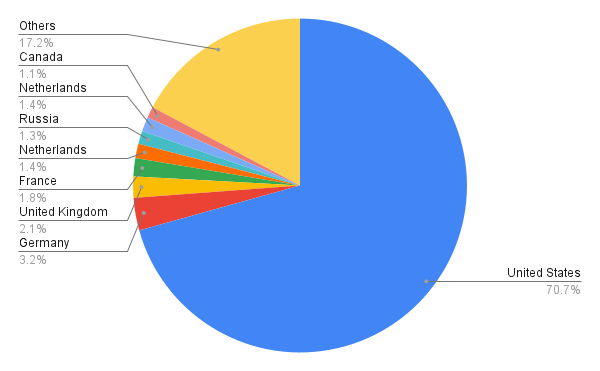
Figure 7 shows the top eight countries where the owners of these domain names appear to be located. In contrast to what we observed for web threats overall – for which the top three countries were the United States, Russia and Germany – the top three host domain countries for web skimmers were the United States, Germany and the United Kingdom. This seems reasonable since most web skimmers target e-commerce websites and these countries have relatively higher consuming capability.
Web Skimmer Trends Analysis
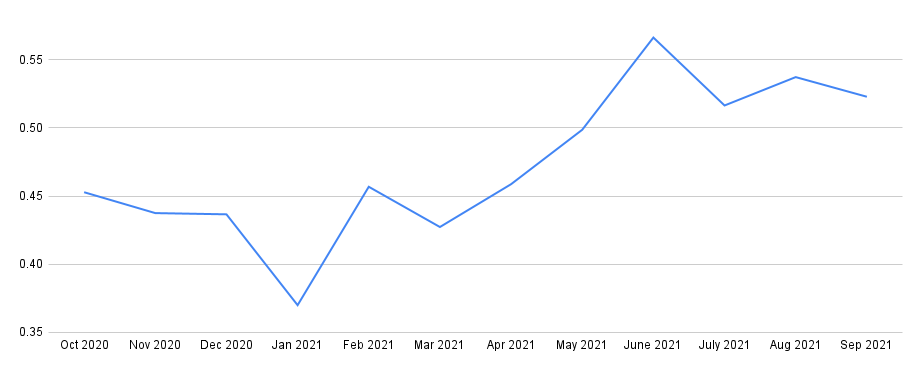
With e-commerce booming, sophisticated attackers choose to leverage the web skimmer to collect users’ sensitive information. In addition, they increasingly choose to deploy web skimmers in the cloud, especially for some web skimmer families – a practice that can make these pages appear more legitimate to normal users. As Figure 8 shows, we can see the ratio for web skimmers hosted on the cloud is very high for certain families – for example, for web skimmer family 5, almost half of web skimmers are hosted in the cloud. Moreover, the rate for that family grew over 50% from May to September.
Web Skimmer Case Study
Among the web skimmer attacks we observed, we identified an interesting case: a web skimmer campaign which leverages a cloud video platform to distribute its malicious JavaScript code to more than 100 real estate sites. For further details, please refer to, “A New Web Skimmer Campaign Targets Real Estate Websites Through Attacking Cloud Video Distribution Supply Chain,” which provides deep insights on how attacks’ vectors are deployed through code analysis.
Conclusion
The web threats analyzed in this blog indicate that the most prevalent web threats are cryptominers, JS downloaders, web skimmers, web scams and JS redirectors.
While many of the most common web threats come from a few malware families that share common characteristics, web skimmers stand out for the diversity of their code and behavior. Furthermore, it is worth noting that some web skimmer families are increasingly focused on taking advantage of cloud hosting – in some cases, more than 50% of the malicious JavaScript code we observed was hosted on the cloud.
The prevalence of web threats emphasizes the need for website administrators to patch all systems, components and web plugins and implement security best practices, which will help to minimize the likelihood of compromised systems.
While cybercriminals continue to seek opportunities for malicious cyber activities, Palo Alto Networks customers are protected from the web threat attacks discussed here and many others via the Advanced URL Filtering and Threat Prevention cloud-delivered security subscriptions.
We also recommend the following actions:
- Continuously update your Next-Generation Firewalls with the latest Palo Alto Networks Threat Prevention content.
- Run a Best Practice Assessment to improve your security posture.
If you think you may be experiencing an active breach, the Unit 42 Incident Response team can help. Please email unit42-investigations@paloaltonetworks.com or call (866) 486-4842 – (866) 4-UNIT42 – for U.S. toll free, (31-20) 299-3130 in EMEA or (65) 6983-8730 in JAPAC. The Unit 42 Incident Response team is available 24/7/365.
Acknowledgements
We would like to thank Billy Melicher, Alex Starov, Jun Javier Wang, Laura Novak and Erica Naone for their help with the blog.











 Get updates from Unit 42
Get updates from Unit 42