Executive Summary
The attacks against cloud-hosted infrastructure are increasing, and the proof is in the analysis of security alert trends. Recent research reveals that organizations saw nearly five times as many daily cloud-based alerts at the end of 2024 compared to the start of the year. This means attackers have significantly intensified their focus on targeting and breaching cloud infrastructure.
These alerts aren’t simply noise. We’ve seen the greatest increases in high severity alerts, meaning indicators of attacks are successfully targeting critical cloud resources as explained in Table 1.
| Cloud Resource | Why It’s Critical |
| Identity and access management (IAM) | Leaked credentials can open the door to an organization’s cloud infrastructure. |
| Storage | Can contain sensitive organizational or customer data. |
| Virtual machines | Often connected to additional internal services, offering lateral movement opportunities to attackers. |
| Containers | Container host exploitation can allow attackers to run malicious containers. |
| Serverless | Serverless functions are designed for singular automated purposes. Remote command line executions should not occur. |
Table 1. Criticality of certain cloud resources.
Of particular note, attackers frequently targeted serverless IAM tokens resulting in remote command-line usage. These are significant because they can be used to gain access to an organization’s larger cloud environment. As part of the increase of cloud alerts, there were three times as many remote command-line access events utilizing identity access and management (IAM) tokens, and credentials that are used by cloud serverless functions.
We also identified other upward trends in alerting:
- An 116% increase in IAM-based “impossible travel event” alerts (i.e., login events from distant geographic areas within a narrow time window)
- A 60% increase in IAM application programming interface (API) requests from outside regions for compute resources (cloud virtual machine)
- A peak 45% increase in the number of cloud snapshot exports during November 2024
- A 305% increase in the number of suspicious downloads of multiple cloud storage objects
Identity is the defense perimeter of cloud infrastructure. Attackers target IAM tokens and credentials as they hold the keys to the cloud kingdom, allowing attackers to move laterally, escalate their permissions and perform additional malicious operations. The rise in the number of access attempts and usage of sensitive IAM service accounts means attackers across the globe have their sights set on cloud resources.
Attackers target cloud storage services as they often contain sensitive data. We saw a notable increase in the number of suspicious cloud storage object downloads and image snapshot exports. Suspicious cloud storage object download alerts trigger when a single IAM-based identity downloads a large number of storage objects within a narrow time window. This can signify malicious operations such as ransomware or extortion. Image snapshots are targeted by attackers as snapshots can contain sensitive data regarding cloud infrastructure and IAM credentials that could allow the attacker to escalate permissions and move laterally within a victim cloud environment.
These examples illustrate the immediate need to protect cloud environments, not solely with foundational cloud security posture management (CSPM) tools, but in cooperation with tools that detect and prevent malicious runtime operations as they occur.
By deploying Cortex Cloud’s runtime cloud security tooling — also called Cloud Detection and Response (CDR) — security teams can identify and prevent malicious events within cloud environments.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | Cloud Cybersecurity Research |
Cloud Attacks at Scale
In a recent Unit 42 post, we published details of a ransomware and extortion campaign that directly targeted exposed environment variable files. The campaign’s threat actor successfully harvested over 90,000 credentials from 110,000 targeted domains. More worryingly, they also harvested nearly 1,200 cloud IAM credentials. These credentials allowed the threat actor to successfully perform extortion attacks against multiple organizations.
This operation highlights an opportunity to discuss the security mechanisms that are in place to protect organizations. Specifically, this allows us to determine how to employ both posture management and runtime monitoring security solutions seamlessly. This allows organizations to build a cloud security defense perimeter that is sufficiently robust, and capable of facing these new waves of attackers.
During the investigation for this article, we discovered that the average total number of cloud alerts experienced by an organization increased by 388% in 2024. These alerts originated from both posture management and runtime monitoring detection operations.
Although alerts with “informational” severity did account for the majority of alerts, it is extremely important to highlight that the most significant change was in the number of high severity alerts. This classification of alert saw an increase of 235% during 2024. Medium and low severity alerts also increased by 21% and 10%, respectively.
What These Trending Alerts Signify
The changes we observed in the number of alerts align with our 2024 State of Cloud-Native Security Report, which found that 71% of organizations attribute increased vulnerability exposures to accelerated deployments. Furthermore, 45% of those organizations report a rise in advanced persistent threat (APT) attacks over the last year.
A case in point is Microsoft’s recent research on Storm-2077, a China-based cloud threat actor group (CTAG) that employs complex cloud IAM credential harvesting techniques to obtain and to maintain access to victim cloud environments. It quickly becomes apparent that both cloud posture management and runtime security monitoring must function as a single unit to perform adequate protection from the next phase of threats in cloud environments. The Background section below provides additional information on posture management and runtime monitoring detections.
A key mission for cloud defenders is to design and deploy a cloud security platform that will improve detection capabilities. This allows administrators not only to detect misconfigurations and vulnerabilities, but also to collect and analyze the runtime events within cloud environments. Such a platform provides defenders with better visibility and enables quicker response time when dealing with alerts.
While the ability to identify and detect malicious or suspicious cloud events has increased across the industry, so has the complexity of threat actors’ offensive cloud operations. For example, in January 2024, the average cloud environment saw only two alerts for the remote command-line usage of a serverless function IAM token. This stayed consistent throughout the year. However, by December 2024, the average cloud environment saw more than 200 of those same alerts – a worrying signal of increased activity. As shared in the Leaked Environment Variables article, this runtime operation is exactly what occurred during that malicious extortion event.
Further evidence supporting this trend includes the following:
- An 116% rise in impossible travel alerts relating to cloud identities
- A 60% increase in the number of compute workload API calls occurring from outside of that instance’s cloud region
- A 45% increase in the number cloud snapshot exports
- A 305% increase in the number of suspicious downloads of multiple cloud storage objects
Both of these alert findings strongly indicate that the prime objective of CTAGs is targeting, collecting and using a cloud IAM token or credential. This also indicates that attackers will use these tokens or credentials for potentially malicious operations.
Background
Cloud security posture management (CSPM) tools form the foundation of cloud security. Their operations center on guardrail control monitoring to ensure that cloud environments maintain secure configurations and are free from vulnerabilities and misconfigurations.
Posture management monitoring is traditionally based on time-specific security scanning of a cloud environment’s resources and configurations. Alerts are triggered when a new or modified cloud resource appears to pose potential security risks.
For example, an alert will be triggered if an IAM policy is overly permissive and allows access to other cloud resources. It will also be triggered if a cloud compute instance or serverless function contains vulnerabilities or misconfigurations.
Posture management scanning operations are performed on a routine schedule, often hourly or daily. Some CSPM security tools allow for the monitoring of cloud platform auditing logs as well, which can assist in detecting suspicious activity as it occurs within a cloud service platform (CSP). It is critical that organizations configure their CSPM platform to collect the audit logs from their third-party cloud-based software-as-a-service (SaaS) applications to ensure visibility.
CDR tools provide runtime monitoring detections by collecting, identifying and even preventing operations that occur during a particular event. By collecting the logs from cloud compute instances, CSP logging resources and third-party cloud SaaS applications, CDR security tools can identify, alert on and prevent malicious cloud events.
Examples of these operations include the execution of an API request against a cloud platform or cloud application such as:
- Creating new cloud users or service accounts
- Attaching IAM policies to new or established IAM users or roles
- Establishing network connections from a Tor exit node or VPN host
In contrast to posture management tools, runtime monitoring tools continuously monitor the cloud environment and often require a dedicated agent to maintain visibility of the cloud resources. When an agent is installed, cloud runtime monitoring security tools allow for the detection — and even prevention — of malicious cloud operations as they occur.
High Severity Alert Trends
We have observed a clear increase in the number of alerts in 2024, correlating with the rise in attacks on cloud environments.
High severity cloud alerts increased by 235% throughout 2024. The largest single-month spike (281%) occurred in May, and we noted the most substantial increase in these alerts (204%, 247% and 122%) in August, October and December, as shown in Figure 1.
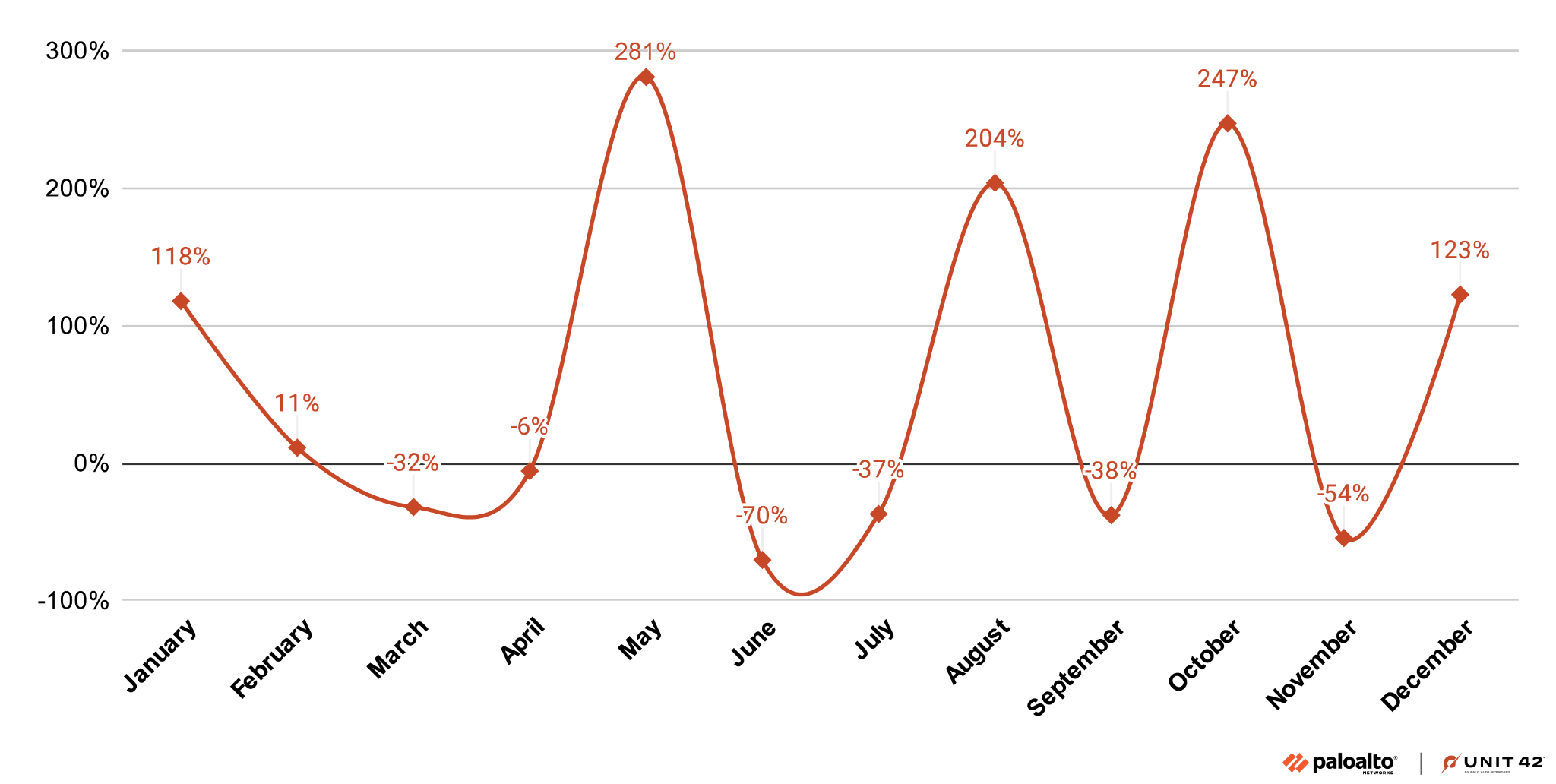
Top 10 High Alerts
A closer look at the top 10 most frequent daily high severity alerts reveals a high number of alerts pertaining solely to runtime-focused events. These alerts are triggered by a singular event or a sequence of connected events. This necessitated near real-time analysis or, in some instances, real-time analysis for detection.
Table 2 below shows that the remote command-line usage of the serverless IAM tokens is an event that requires real-time log analysis to detect and potentially to prevent. Conversely, the most frequent high severity alert, “cloud storage delete protection disabled,” can be detected and mitigated with a CSPM tool.
| Alert Name | Runtime or Posture Control | Average Daily Count |
| Remote command line usage of serverless token | Runtime | 24.68 |
| An identity performed a suspicious download of multiple cloud storage objects | Runtime | 21.09 |
| Cloud Storage Delete Protection Disabled | Posture and Runtime | 20.19 |
| Abnormal Allocation of compute resources in a high number of regions | Posture and Runtime | 11.11 |
| A Kubernetes node service account was used outside the cluster from non-cloud IP | Posture | 11 |
| Abnormal Suspicious allocation of compute resources in multiple regions | Posture and Runtime | 10 |
| Multiple cloud snapshots export | Runtime | 9.33 |
| Remote command line usage of serverless role | Runtime | 7.79 |
| Unusual allocation of multiple cloud compute resources | Posture and Runtime | 7.73 |
| Abnormal Unusual allocation of compute resources in multiple regions | Posture and Runtime | 6.42 |
Table 2. High severity alerting by average occurrence.
To ensure the protection of cloud storage objects within a storage container whose delete protection has been disabled, we highly recommend deploying a CDR tool. These tools can detect and prevent any cloud storage objects from being deleted as a result of a ”protection disabled” event.
Other notable high severity alerts include multiple cloud snapshot exports and suspicious usage of a service account IAM. Both of these are key indicators of malicious activity within a cloud environment.
Examples of malicious operations that could trigger several of these alerts are cloud-focused extortion or ransomware events. These types of events can only be leveraged by first disabling cloud storage protections, such as delete protection and automatic backups. Once these protections are removed, malicious actors can delete or exfiltrate cloud storage container objects, increasing the likelihood of a successful extortion operation.
Some of these high severity alerts could also be triggered by the compromise of exposed or vulnerable serverless or compute instance resources. Specifically in terms of the remote command-line usage of a serverless IAM token, serverless functions are designed to operate autonomously and independently.
Remote or unauthorized usage of a serverless function's IAM token indicates compromise and potential lateral movement within the cloud environment. The same type of event could indicate the malicious usage of a service account IAM token. Given that service account IAM tokens are typically intended for a single purpose, any abnormal usage of that token should be considered suspicious.
Medium Severity Alert Trends
Unlike the end-of-year high severity alert spike, we saw a sustained spike in medium severity alerts mid-2024. This spike included an initial 186% and subsequent 24% increase, before a downward trend through December, as Figure 2 shows.
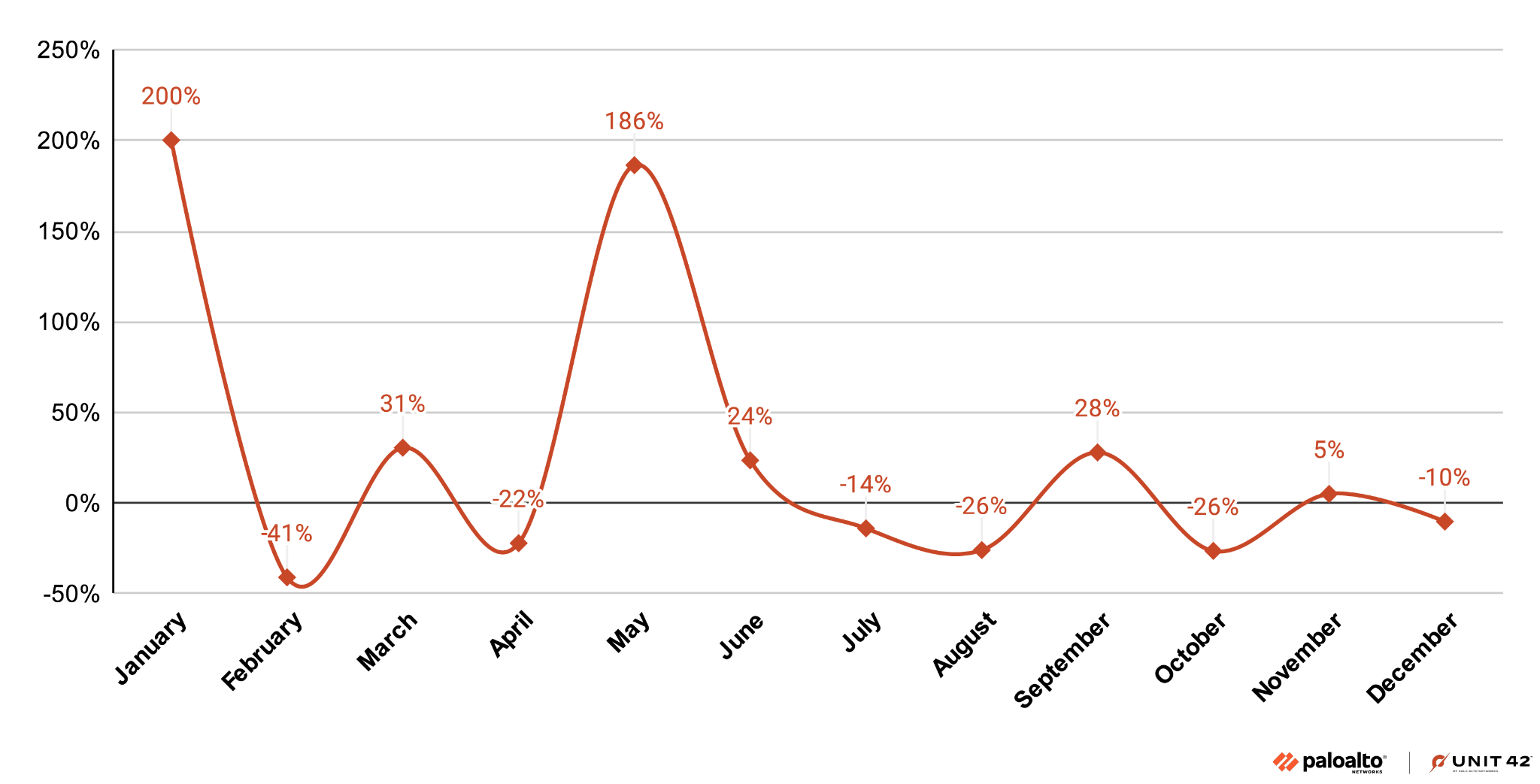
Top 10 Medium Alerts
The top 10 medium severity alerts, shown in Table 3 below, differ from the top 10 high severity alerts listed in Table 2 above. The key difference is that for all but one of the top 10 medium severity alerts, the events can only be detected by performing some form of runtime protection analytics.
The “unusual high-volume data transfer” event can be triggered using traditional CSPM detections of cloud resources. However, like the high severity “cloud storage delete protection disabled” event discussed above, a CDR tool would be better able to detect this unusual volume transfer event as it was occurring. It could also identify the types of files and their cloud storage file or directory locations. These details provide security teams with the most desired resources to perform their jobs: time, and knowledge.
| Alert Name | Runtime or Posture Control | Average Daily Count |
| An IAM identity attempted multiple actions on resources that were denied | Runtime | 80 |
| A compute-attached identity executed API calls outside the instance's region | Runtime | 36.32 |
| Attempted cloud application access from unusual tenant | Runtime | 21.69 |
| An identity performed a suspicious download of multiple cloud storage objects from multiple buckets | Runtime | 18.66 |
| Impossible travel by a cloud compute identity | Runtime | 18.65 |
| Unusual storage high-volume data transfer | Runtime | 15 |
| Kubernetes service account activity outside the cluster from non-cloud IP | Runtime | 12.15 |
| A cloud application performed multiple actions that were denied | Runtime | 12.02 |
| Multiple cloud snapshots export | Runtime | 10 |
| Suspicious identity downloaded multiple objects from a backup storage bucket | Runtime | 9.68 |
Table 3. Medium severity alerting by average occurrence.
Several of the alerts listed in Table 3 could indicate that malicious actors are targeting cloud resources such as Kubernetes service accounts outside of the cluster or from a non-cloud IP address. These two alerts in particular might indicate that the Kubernetes cluster authentication tokens have been compromised, as service account IAM tokens are designed for a singular purpose. Any operation using these credentials from outside of the cluster — or outside of the known cloud environment — should be considered suspicious activity and should be mitigated.
Another alert that is important to highlight is exporting multiple cloud snapshots. While there can be a legitimate use case for this type of event — such as the deployment of snapshots or an external backup — threat actors also export snapshots. Cloud snapshots can contain sensitive information, making them a common target of malicious operations.
What Organizations Can Do
There are several steps that organizations can implement to better protect themselves against malicious cloud operations:
- Implement effective CDR runtime monitoring
- Deploy a CDR cloud security for all of your cloud environments
- Ensure that all mission-critical cloud endpoints have runtime enabled agents to detect compute and container runtime operations
- Ensure runtime cloud audit log monitoring is available from your CSP providers
- Ensure that your integrated cloud SaaS applications collect:
- Identity providers (IdP)
- CI/CD integrations
- Source code repositories
- Ticketing platforms
- Place limits on CSP regions in which compute and serverless functions are allowed to operate
- It is common practice for threat actors to create cloud resources within foreign CSP regions to perform a basic form of operation obfuscation
- Identify and prevent IAM service accounts from performing operations outside of their intended functions
- Following least-privilege architecture design for IAM credentials can greatly assist in combating lateral movement and privilege escalation operations if an IAM credential is compromised
- Ensure that cloud storage versioning and encryption are in place for all cloud storage containers
- Versioning and encryption are free configurations for every cloud storage container from each of the three major cloud service providers
- These two features also significantly increase the difficulties that threat actors will encounter when trying to steal your valuable, sensitive information
If in doubt, remember that CDR runtime monitoring defenses must be present to effectively combat the majority of threats faced by cloud environments.
Conclusion
CDR runtime monitoring is a critical aspect of maintaining a secure-cloud, hybrid-cloud and multi-cloud environment. As the trending high and medium severity alert data discussed in this article demonstrate, there was a 388% increase in the average number of alerts that cloud environments witnessed during 2024.
A significant number of these alerts are the direct result of the detection of runtime operations, which cannot be detected with posture management (CSPM) tools alone. CDR tools provide cloud runtime detection capabilities, enabling the detection of malicious events occurring on cloud compute instances, container hosts or serverless functions.
Given the increasing threats targeting cloud environments, the only real defense for these environments is to require cloud-based agents for publicly exposed and critical cloud endpoints, CSP audit logging and cloud third-party SaaS applications. Using a CDR analytics tool allows defenders to collect, detect and prevent the execution of malicious operations that can affect any of these resources. The combination of runtime monitoring, analysis and response for cloud resource event logging is essential to ensure that malicious operations are not allowed to function within cloud environments.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team, or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
References
- Leaked Environment Variables Allow Large-Scale Extortion Operation in Cloud Environments – Unit 42, Palo Alto Networks
- 2024 State of Cloud Native Security Report – Palo Alto Networks
- Microsoft shares latest intelligence on North Korean and Chinese threat actors at CYBERWARCON – Threat Intelligence blog, Microsoft
- What Is CSPM? | Cloud Security Posture Management Explained – Cyberpedia, Palo Alto Networks
- What Is CDR (Cloud Detection and Response)? – Cyberpedia, Palo Alto Networks
- Definition of Identity and Access Management (IAM) – Gartner Information Technology Glossary












 Get updates from Unit 42
Get updates from Unit 42