Executive Summary
Last week, Microsoft reported that attackers compromised Exchange Mail Servers with the use of four zero-day vulnerabilities. While patches have been released by Microsoft, adversaries are still attacking vulnerable versions of Microsoft Exchange Servers with malicious tools, malware and data exfiltration. Further, Microsoft has confirmed the existence of a ransomware variant leveraging these vulnerabilities, which has been dubbed “DearCry.” It is reasonable to suspect that the ransomware authors were paying homage to an unrelated yet infamous ransomware family, “WannaCry,” which was used as a payload within an orchestrated attack campaign leveraging known Microsoft vulnerabilities to infect victims en masse.
Due to the surge of this malicious activity, we’ve created this threat assessment for overall threat awareness. Full visualization of the techniques observed and their relevant Courses of Action (CoA) can be viewed in the Unit 42 ATOM Viewer.
If you think you may have been impacted, please email crypsis-investigations@paloaltonetworks.com or call (855) 875-4631 to get in touch with the Crypsis Incident Response team.
DearCry Ransomware Overview
DearCry is a new ransomware variant that has been observed exploiting Microsoft Exchange Servers’ ProxyLogon vulnerabilities for initial access. Early reports of the appearance of DearCry ransom notes in tandem with associated Microsoft Exchange Server compromises via ProxyLogon vulnerabilities began to surface on March 9, 2021, and victims in the U.S., Canada and Australia are suspected, according to security researcher Michael Gillespie.
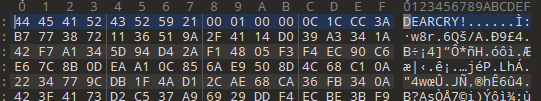
When executed, DearCry ransomware uses AES-256 and RSA-2048 to encrypt victim files, while also modifying file headers to include the string ‘DEARCRY!’ (see Figure 1).
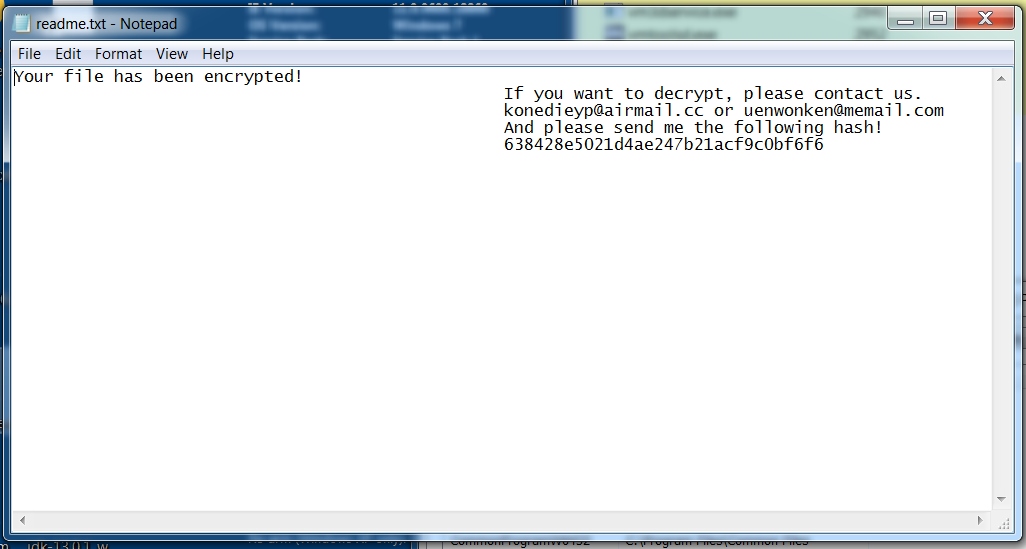
As with a majority of ransomware variants, DearCry deploys a ransom note to the victim’s desktop. However, instead of demanding a fixed ransom amount and including a Bitcoin wallet address, DearCry’s note includes two email addresses that the victim is asked to contact, as well as a request for a provided hash to be sent (see Figure 2).
During its execution, DearCry also runs a service named “msupdate” that is not native to the Windows operating system. This service is later removed when the ransomware finishes its encryption process. Furthermore, all logical drives on the Windows operating system, except for CD-ROM drives, are enumerated on the victim’s system so that the ransomware can begin to encrypt files using an RSA public key.
As of March 2021, DearCry ransomware has been seen targeting files with the following file extensions:
.TIF, .TIFF, .PDF, .XLS, .XLSX, .XLTM, .PS, .PPS, .PPT, .PPTX, .DOC, .DOCX, .LOG, .MSG, .RTF, .TEX, .TXT, .CAD, .WPS, .EML, .INI, .CSS, .HTM, .HTML, .XHTML, .JS, .JSP, .PHP, .KEYCHAIN, .PEM, .SQL, .APK, .APP, .BAT, .CGI, .ASPX, .CER, .CFM, .C, .CPP, .GO, .CONFIG, .PL, .PY, .DWG, .XML, .JPG, .BMP, .PNG, .EXE, .DLL, .CAD, .AVI, .H, .CSV, .DAT, .ISO, .PST, .PGD, .7Z, .RAR, .ZIP, .ZIPX, .TAR, .PDB, .BIN, .DB, .MDB, .MDF, .BAK, .LOG, .EDB, .STM, .DBF, .ORA, .GPG, .EDB, .MFS
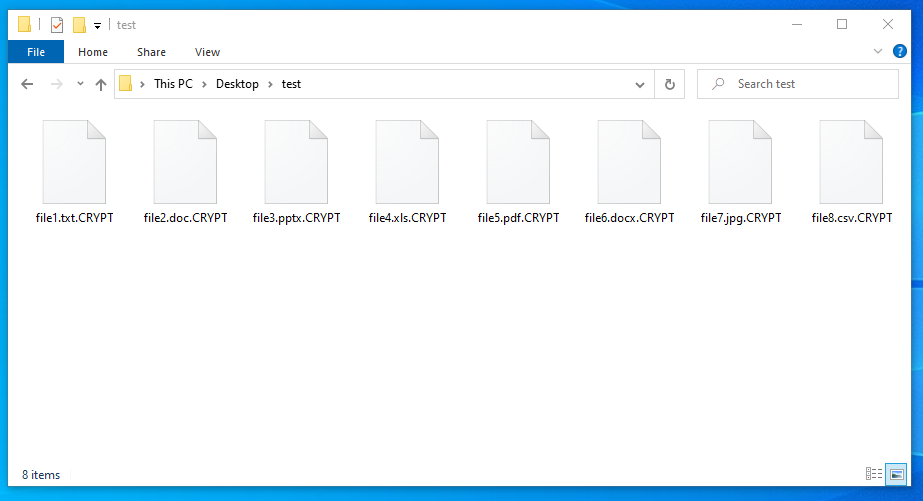
At the time of this writing, all attributed samples leverage the .CRYPT extension for infected files.
Courses of Action
This section documents the relevant tactics, techniques and procedures ( TTPs) used by DearCry and maps them directly to Palo Alto Networks product(s) and service(s). It also further instructs customers how to ensure their devices are configured correctly.
| Product / Service | Course of Action |
|
Initial Access |
|
|
Exploit Public-Facing Application [T1190] |
|
| NGFW | Ensure application security policies exist when allowing traffic from an untrusted zone to a more trusted zone |
| Ensure 'Service setting of ANY' in a security policy allowing traffic does not exist | |
| Ensure 'Security Policy' denying any/all traffic to/from IP addresses on Trusted Threat Intelligence Sources Exists | |
| Threat Prevention† | Ensure a Vulnerability Protection Profile is set to block attacks against critical and high vulnerabilities, and set to default on medium, low and informational vulnerabilities |
| Ensure a secure Vulnerability Protection Profile is applied to all security rules allowing traffic | |
| Deploy Content Pack 8380, which detects the four Microsoft Exchange zero-day vulnerabilities | |
| WildFire† | Ensure that WildFire file size upload limits are maximized |
| Ensure forwarding is enabled for all applications and file types in WildFire file blocking profiles | |
| Ensure a WildFire Analysis profile is enabled for all security policies | |
| Ensure forwarding of decrypted content to WildFire is enabled | |
| Ensure all WildFire session information settings are enabled | |
| Ensure alerts are enabled for malicious files detected by WildFire | |
| Ensure 'WildFire Update Schedule' is set to download and install updates every minute | |
| Cortex XSOAR | Deploy XSOAR Playbook - Isolate Endpoint |
|
Defense Evasion, Discovery, Impact |
|
|
Disable or Modify Tools [T1562.001], File and Directory Discovery [T1083], Data Encrypted for Impact [T1486], Service Stop [T1489] |
|
| Cortex XDR | Enable Anti-Exploit Protection |
| Enable Anti-Malware Protection | |
| Look for the following BIOCs alerts to detect activity*:
Cortex XDR Agent - Behavioral Threat Detected Cortex XDR Analytics - Multiple Discovery Commands |
|
| Cortex XSOAR | Deploy XSOAR Playbook - Ransomware Manual |
Table 1. Courses of Action for DearCry.
†These capabilities are part of the NGFW security subscriptions service.
* These analytic detectors will trigger automatically for Cortex XDR Pro customers.
Conclusion
DearCry is a new ransomware leveraging ProxyLogon vulnerabilities from Microsoft Exchange Servers. Furthermore, it is a perfect example of how threat actors can impact the threat landscape by taking advantage of newly disclosed vulnerabilities to make a quick profit. We strongly advise immediately updating all Microsoft Exchange Servers to the latest available patched versions released by Microsoft.
Palo Alto Networks customers are protected across our product ecosystem, with protections deployed in the following products and subscriptions:
- Next-Generation Firewall
- Security subscriptions: Threat Prevention (Deploy Content Pack 8380 which detects the four zero-day vulnerabilities) and URL Filtering.
- Cortex XDR
- Cortex XSOAR
- WildFire
It is imperative for customers to employ best practices in order to ensure Palo Alto Networks products are configured in a manner best suited for your protection.
Indicators associated with this Threat Assessment are available on GitHub, have been published to the Unit 42 TAXII feed and are viewable via the ATOM Viewer.
In addition to the above courses of action, AutoFocus customers can review additional activity by using the tag: DearCry.
Additional Resources
- March 2021 Exchange Server Security Updates for older Cumulative Updates of Exchange Server
- WCry/WanaCry ransomware technical analysis
- Threat Assessment: Active Exploitation of Four Zero-Day Vulnerabilities in Microsoft Exchange Server
- Remediation Steps for the Microsoft Exchange Server Vulnerabilities
- Microsoft Exchange Server Attack Timeline
Palo Alto Networks has shared our findings, including file samples and indicators of compromise, in this report with our fellow Cyber Threat Alliance members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. For more information on the Cyber Threat Alliance, visit www.cyberthreatalliance.org.












 Get updates from Unit 42
Get updates from Unit 42